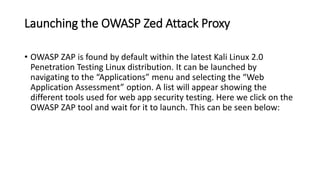
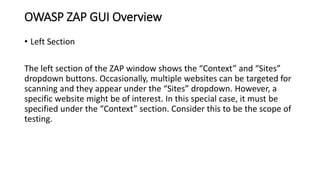
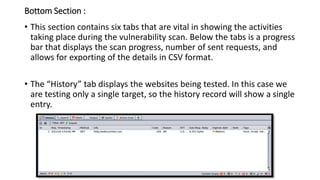
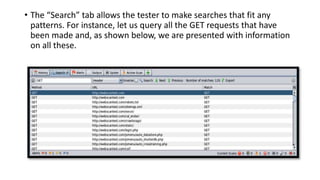
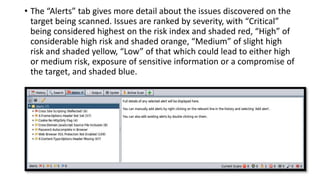
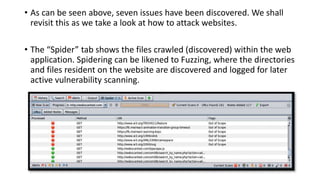
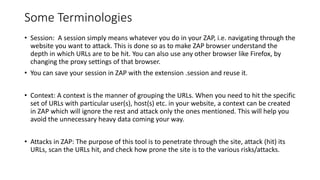
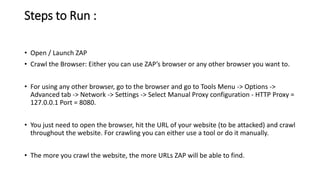
The document provides information on OWASP ZAP, a free and open source web application security testing tool. It discusses what ZAP is, why it is a good choice for security testing, its key features which include an intercepting proxy, scanners, spiders, and fuzzing. It then describes how to launch and use ZAP, covering its graphical user interface, attacking websites by spidering, scanning and reviewing alerts. Key terms like session and context are also explained. Steps to run a scan are outlined, including crawling the site, creating a session and context, attacking with spider and active scans, and reviewing scan results. Finally, the difference between active and passive scans is summarized.