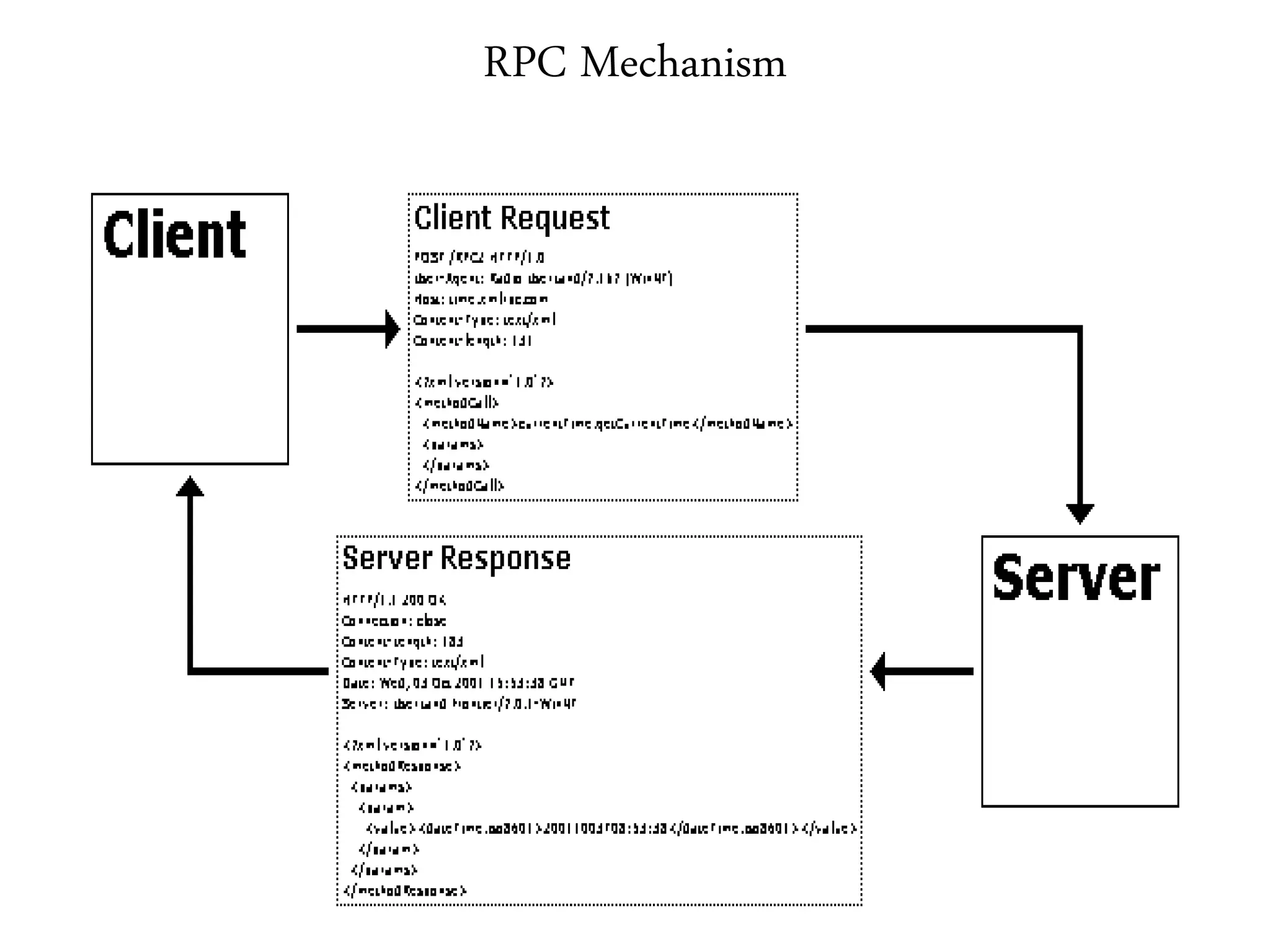
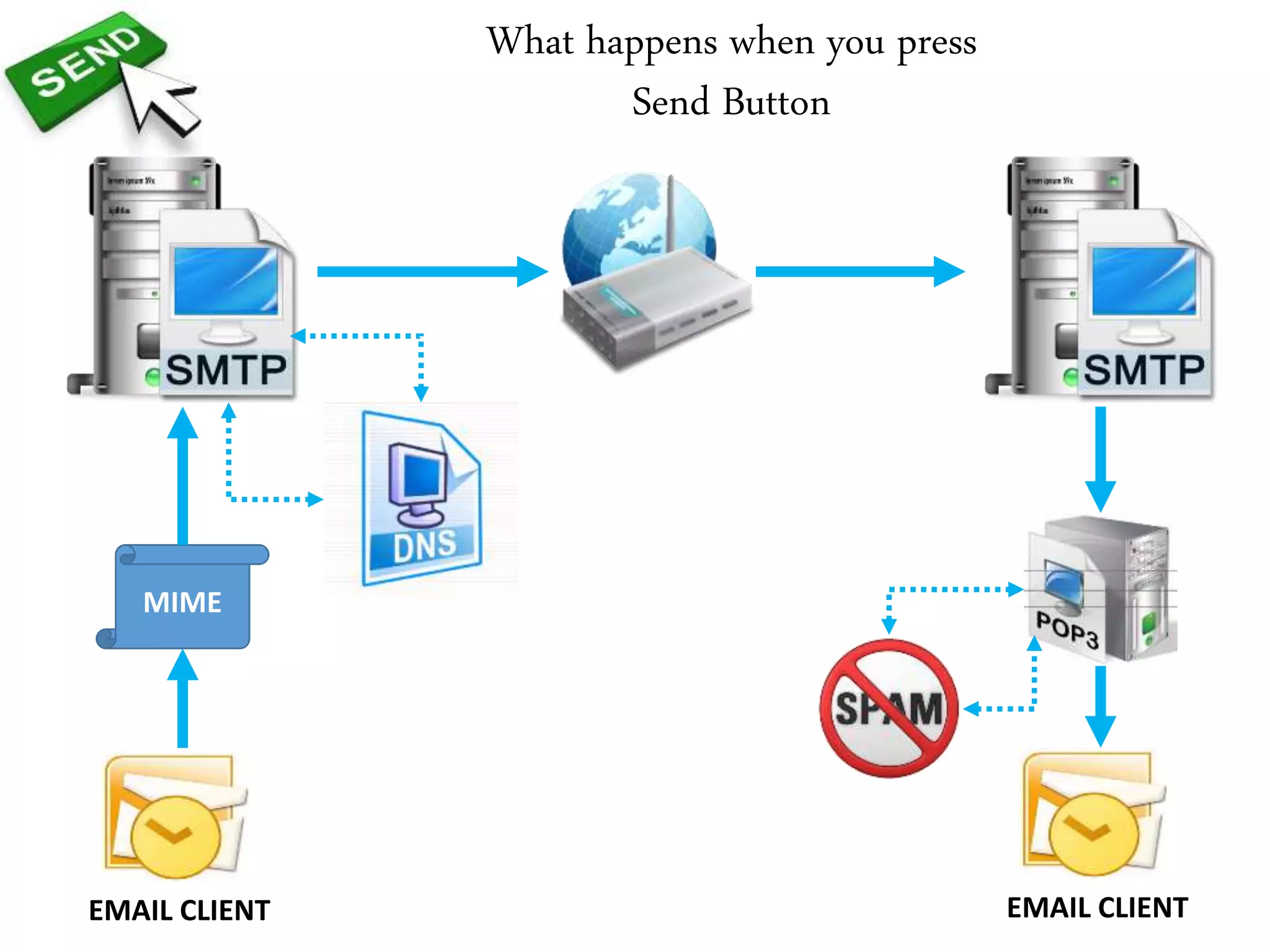
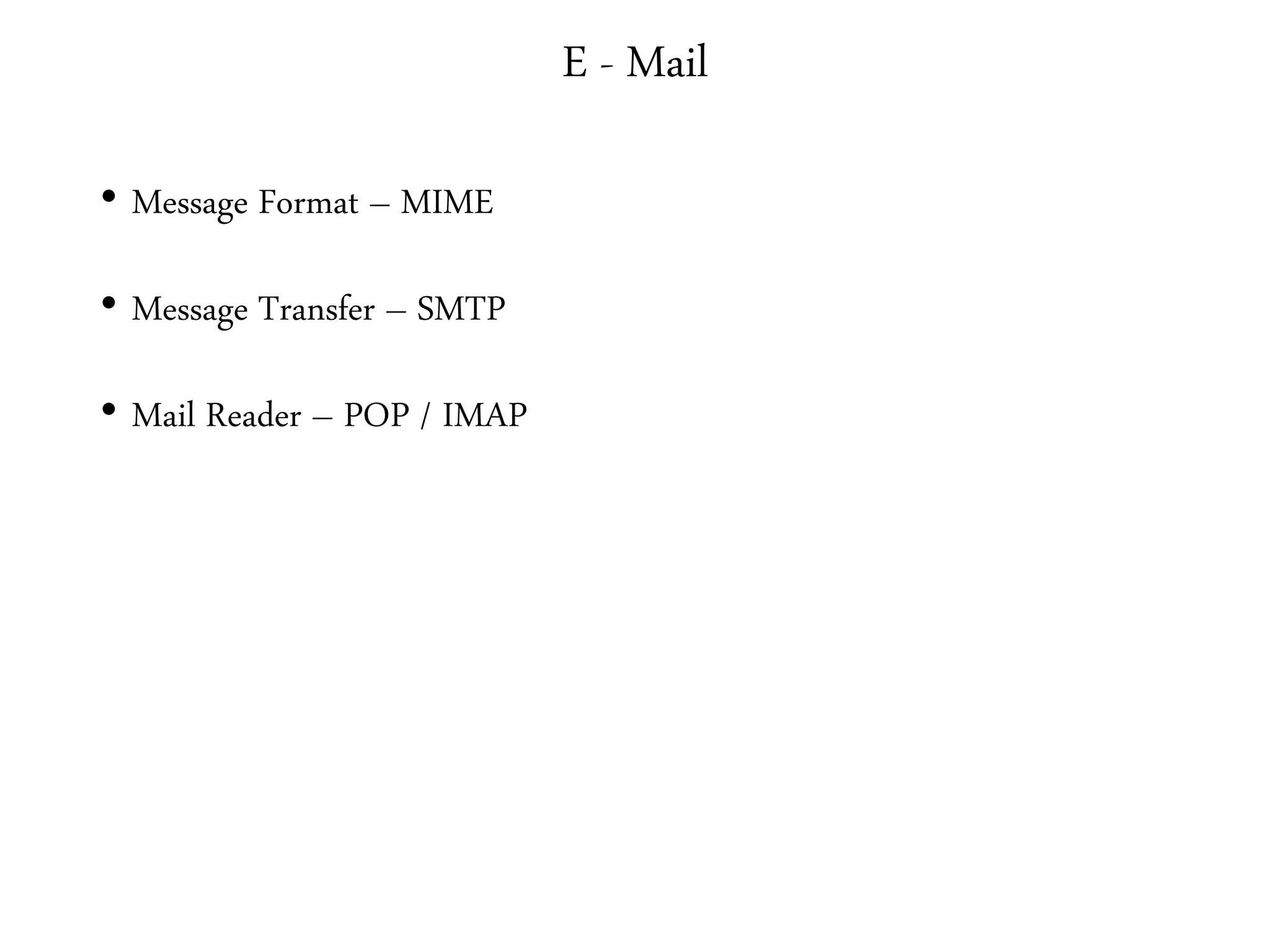
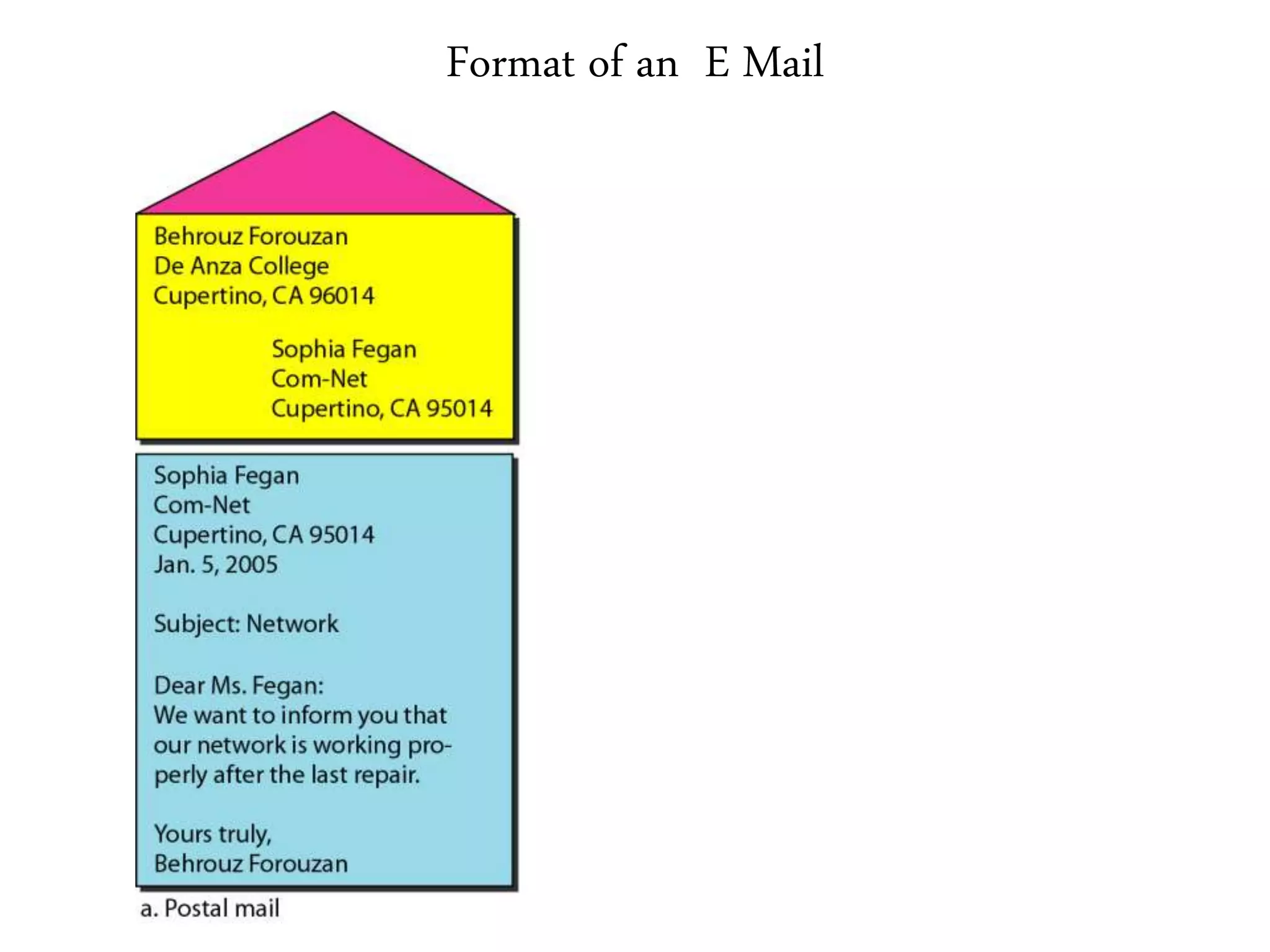
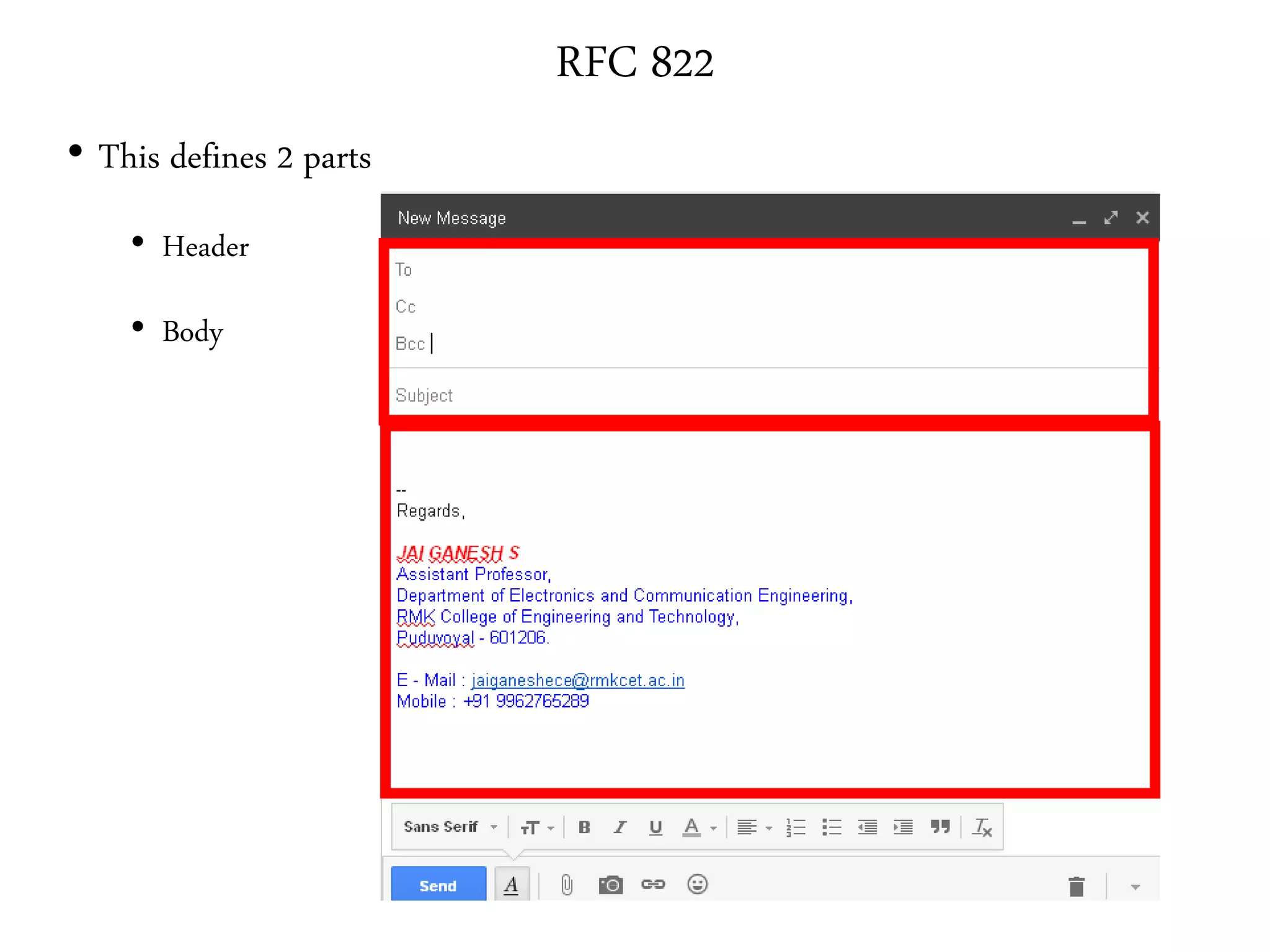
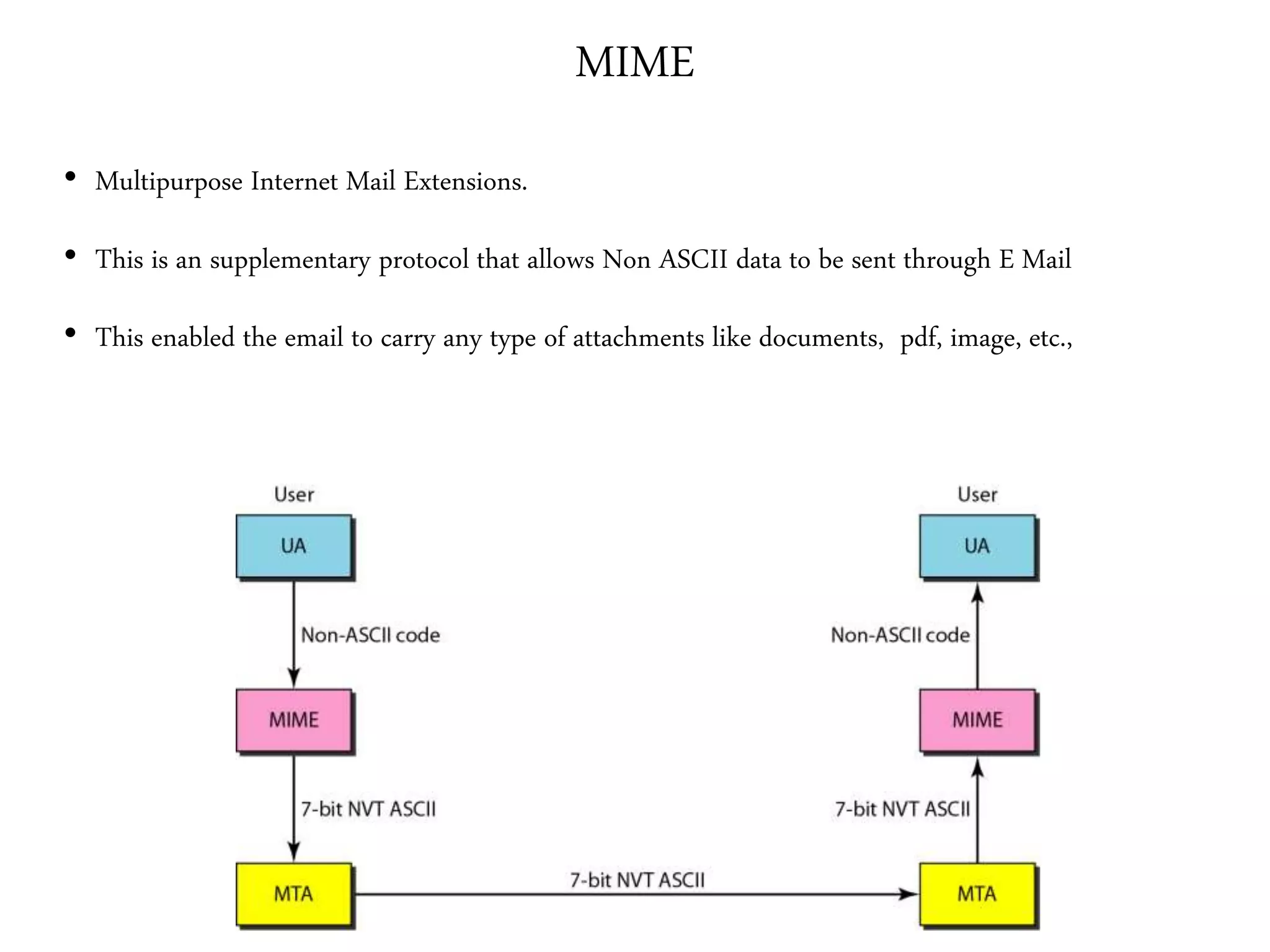
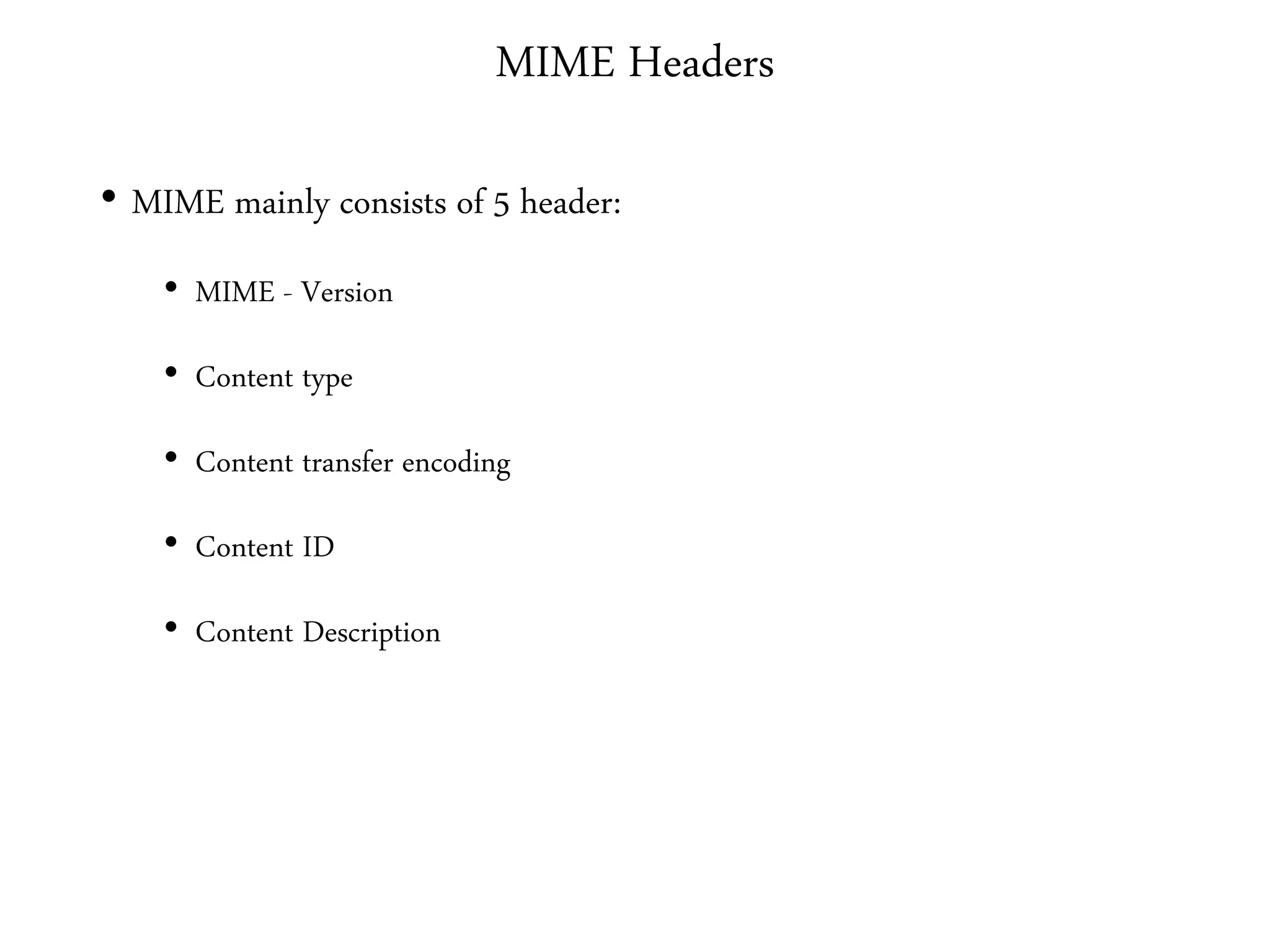
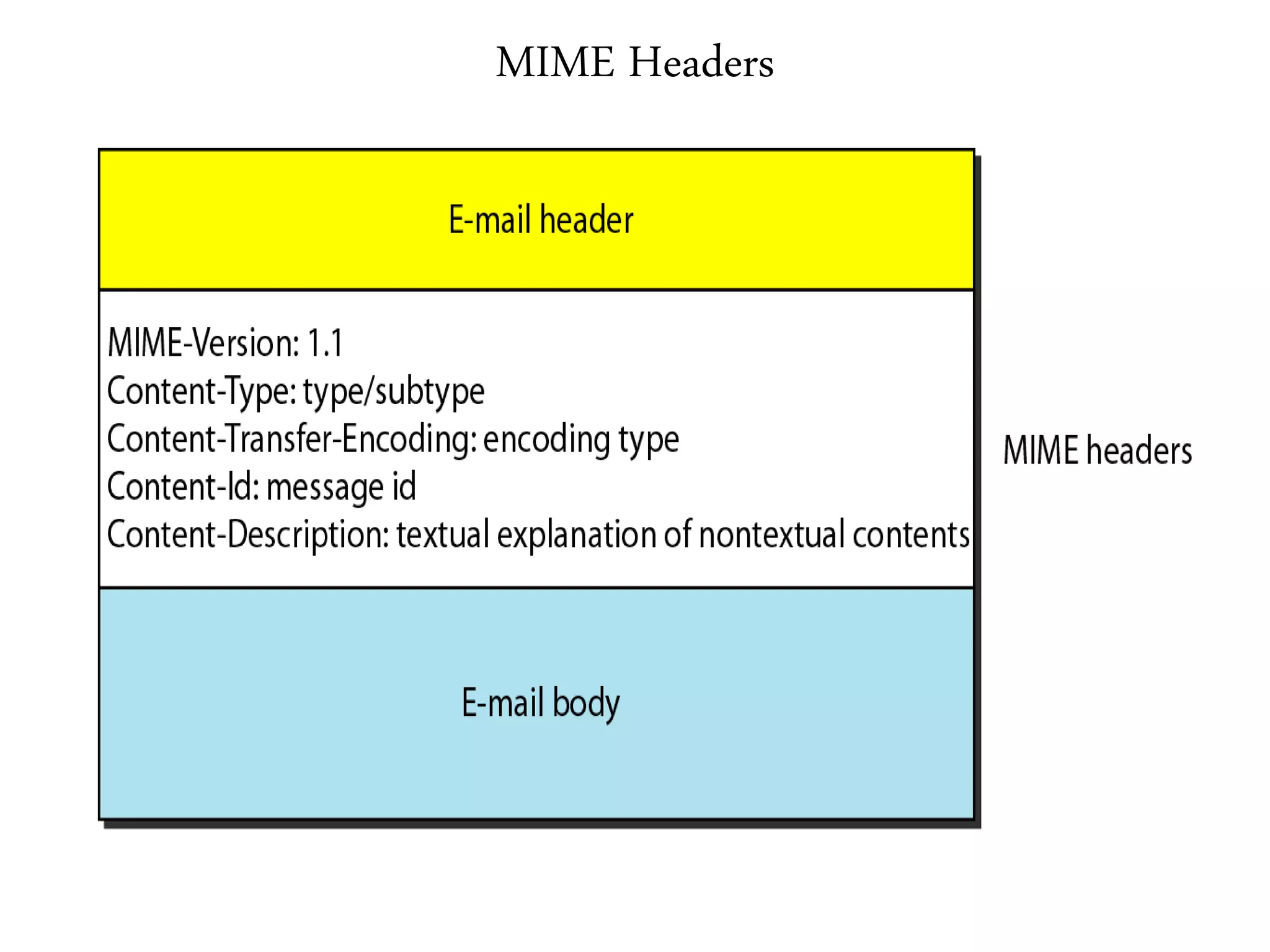
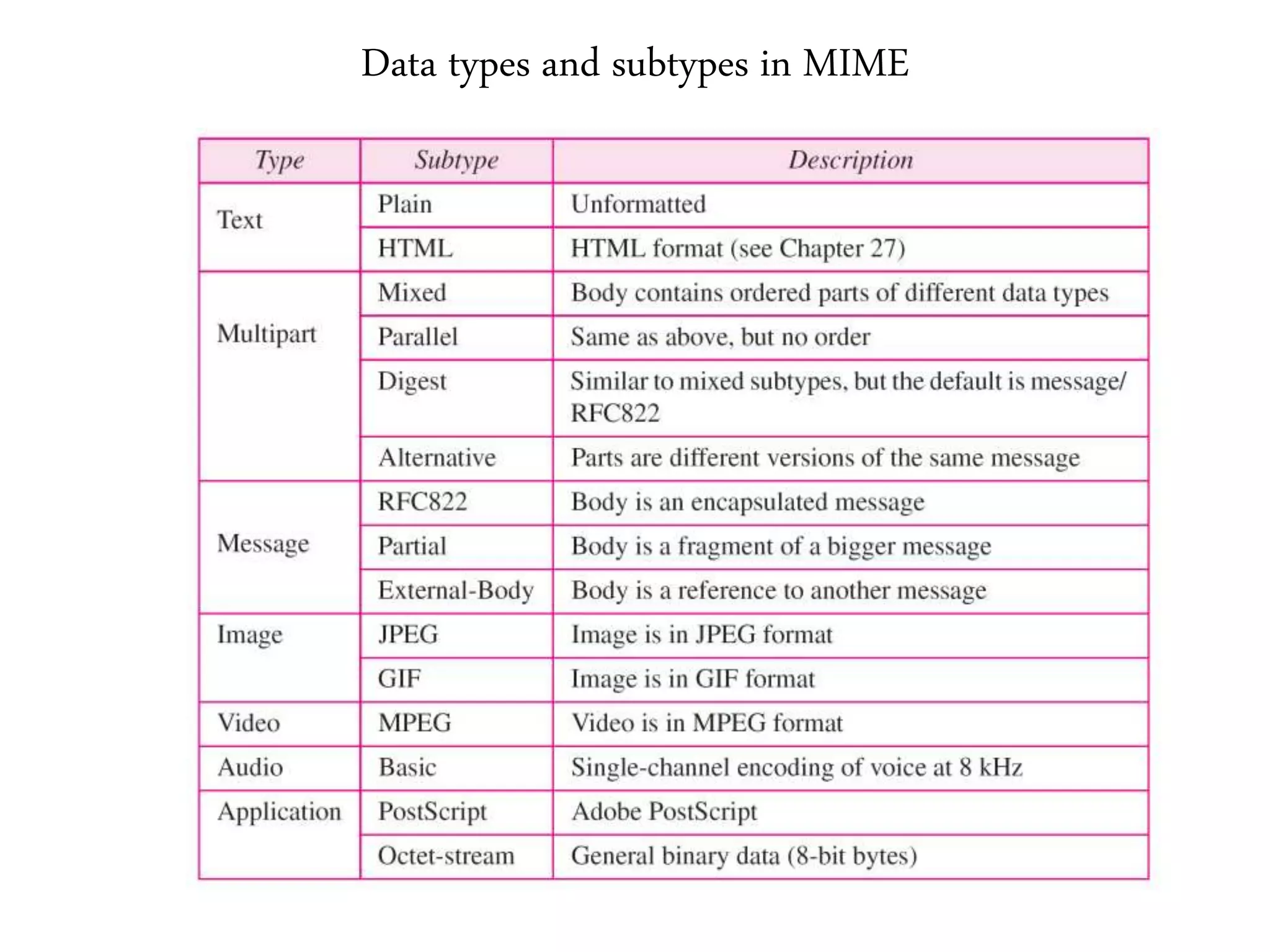
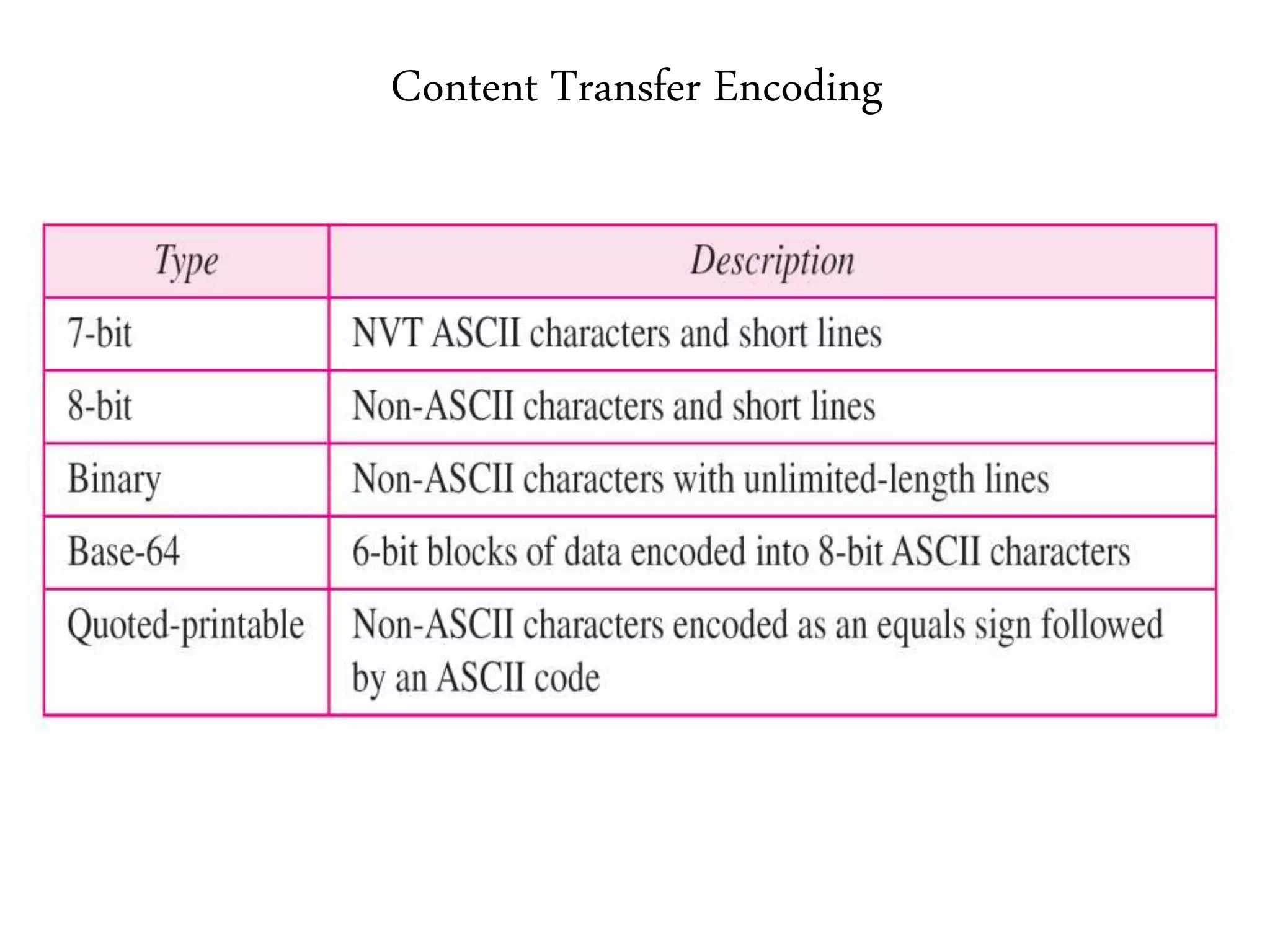
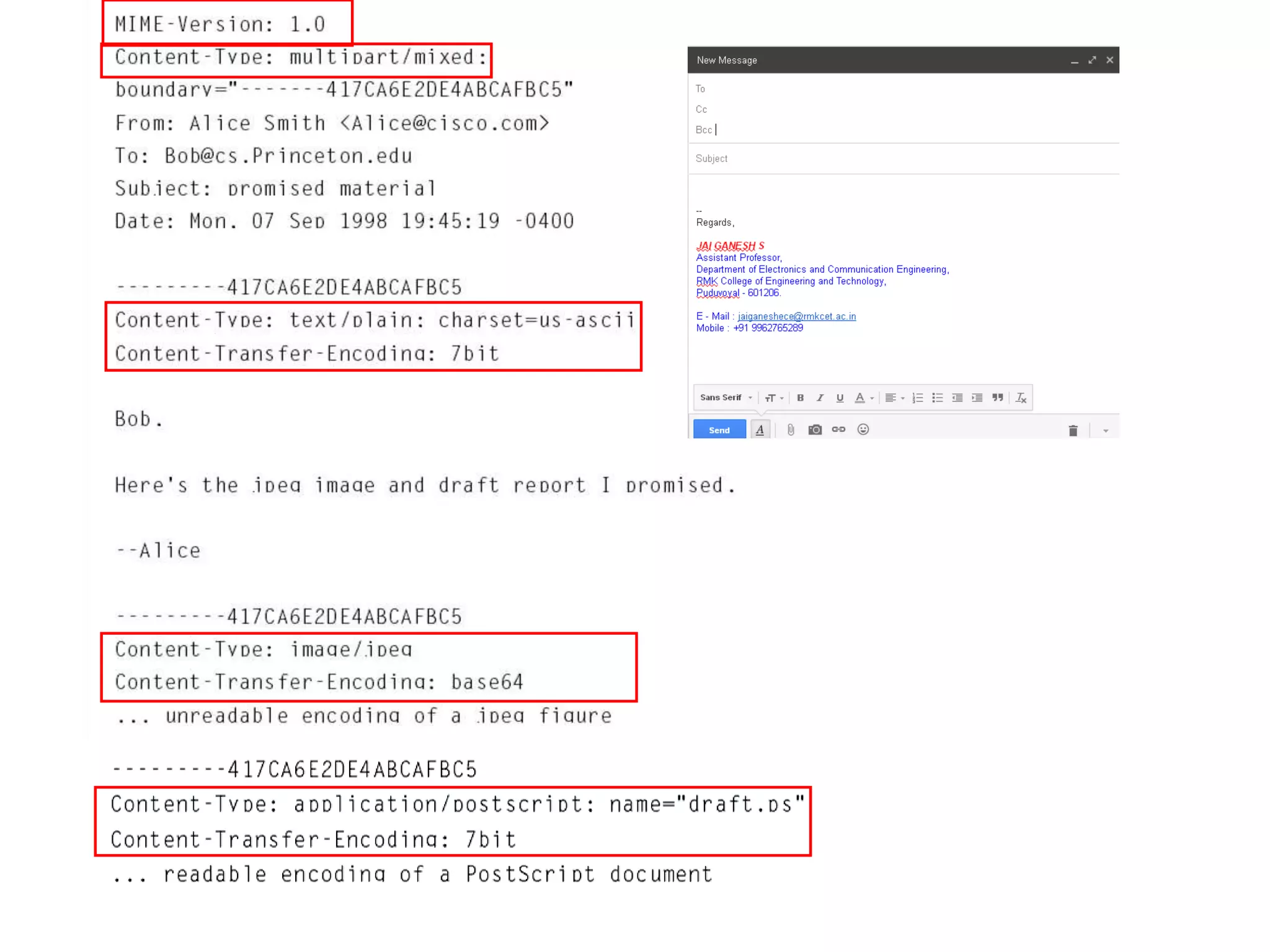
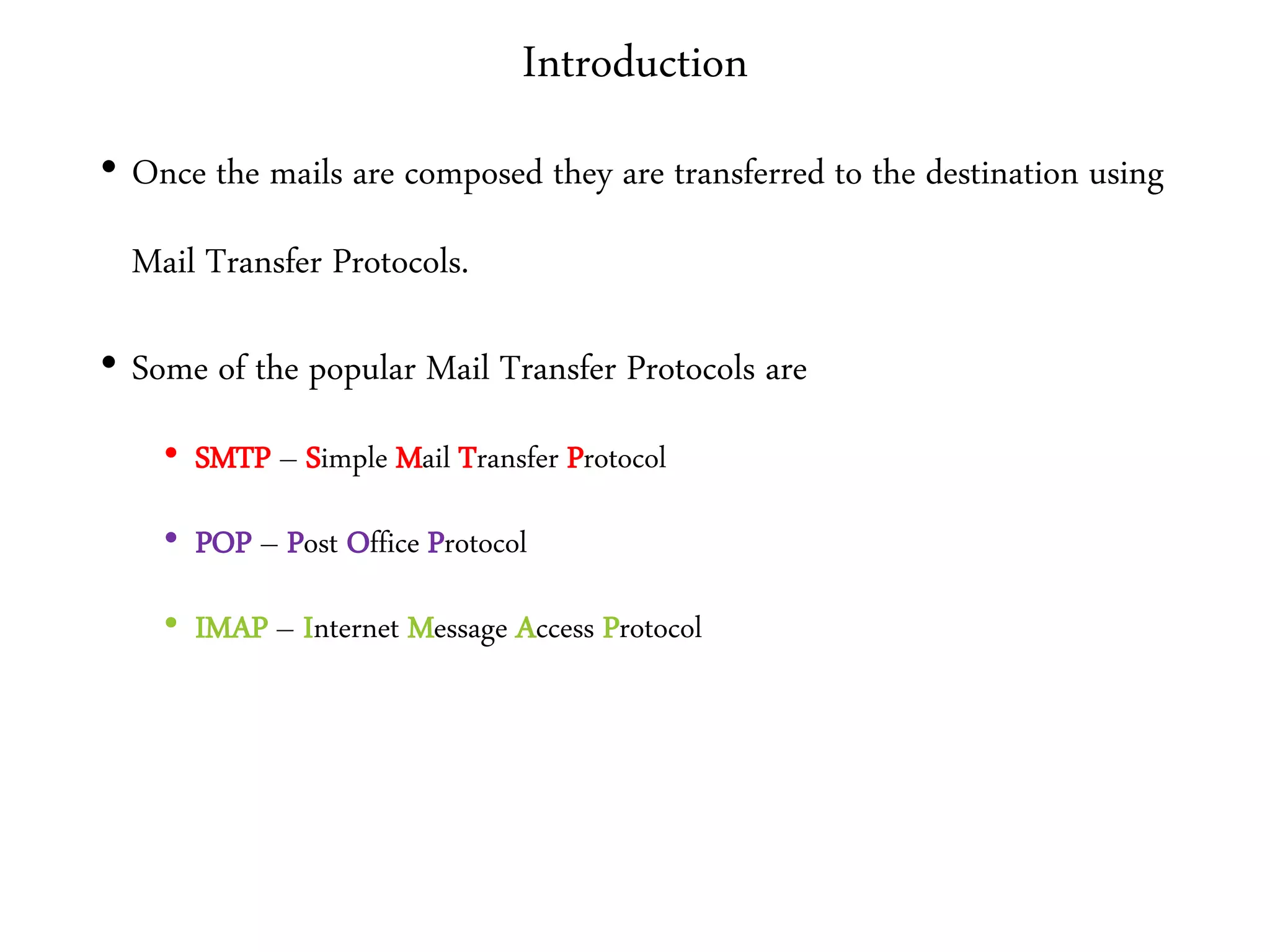
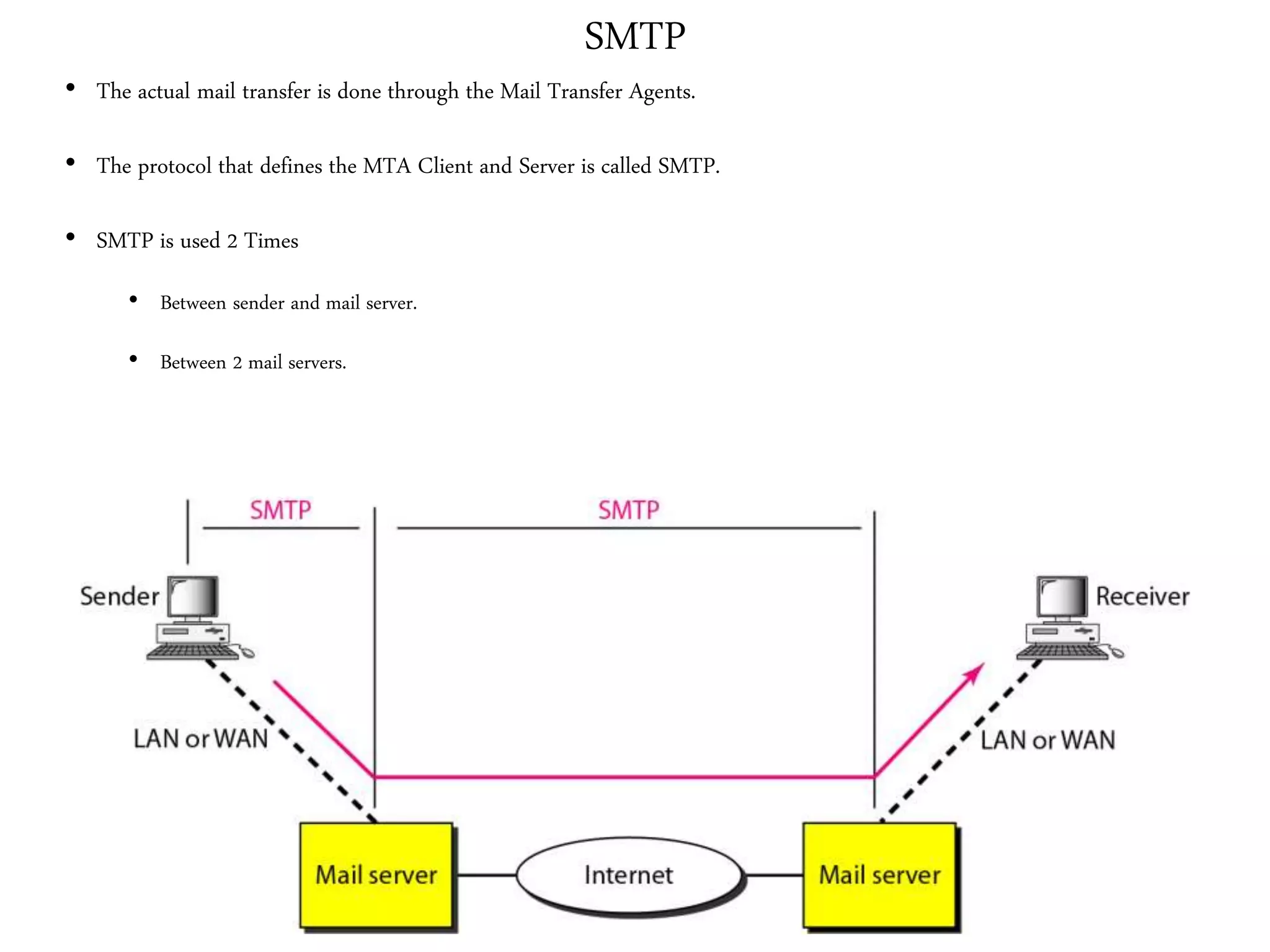
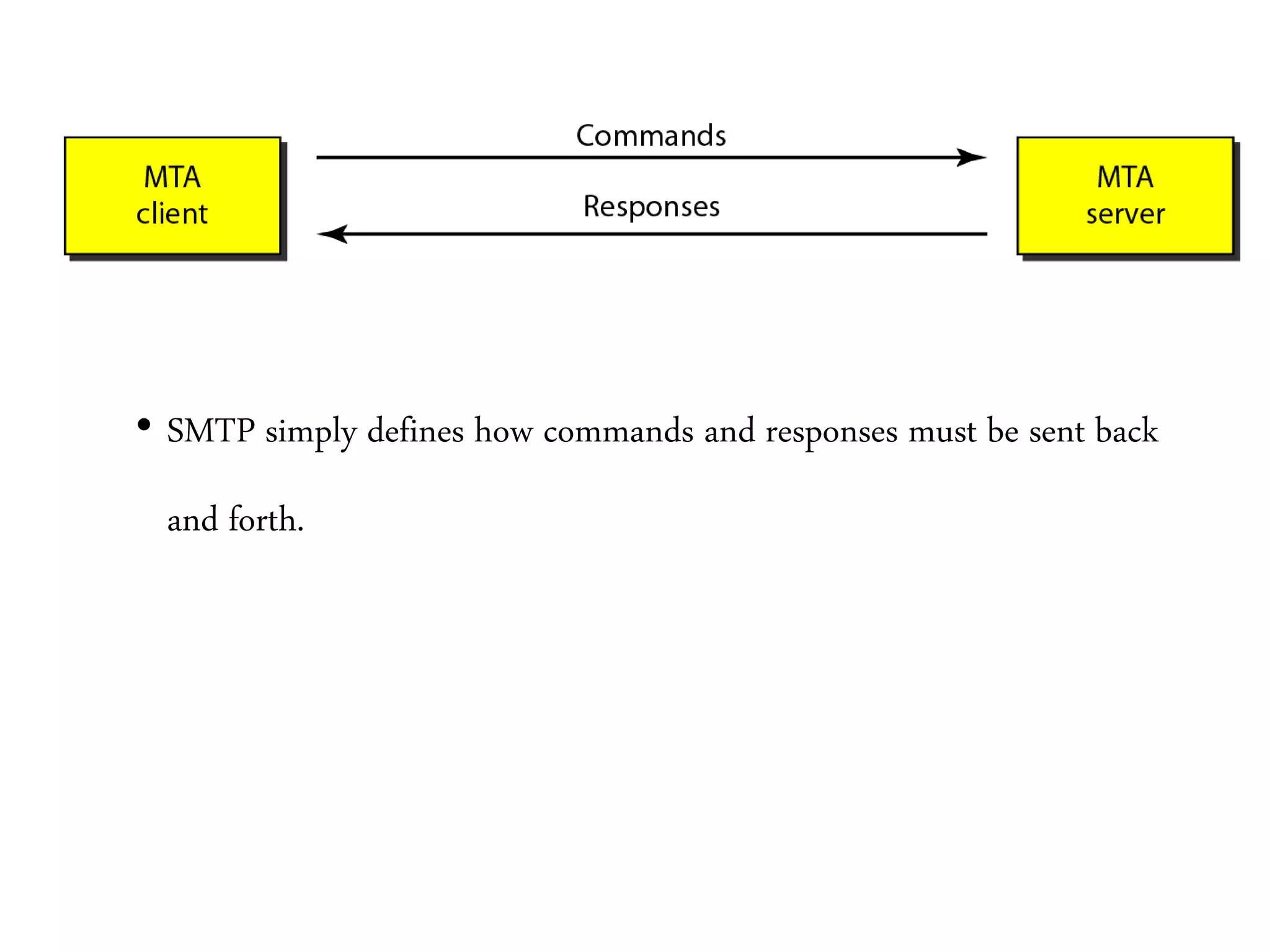
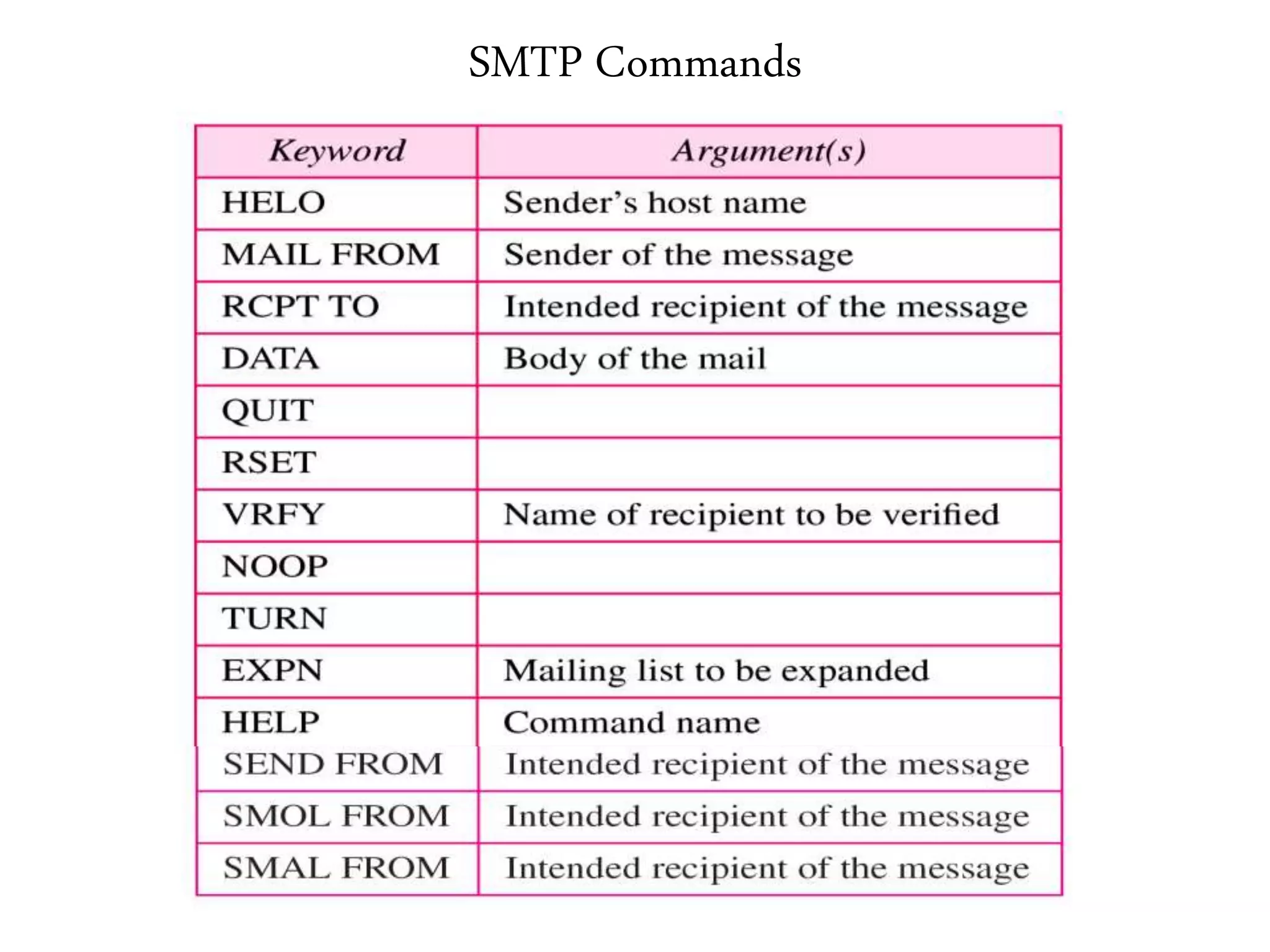
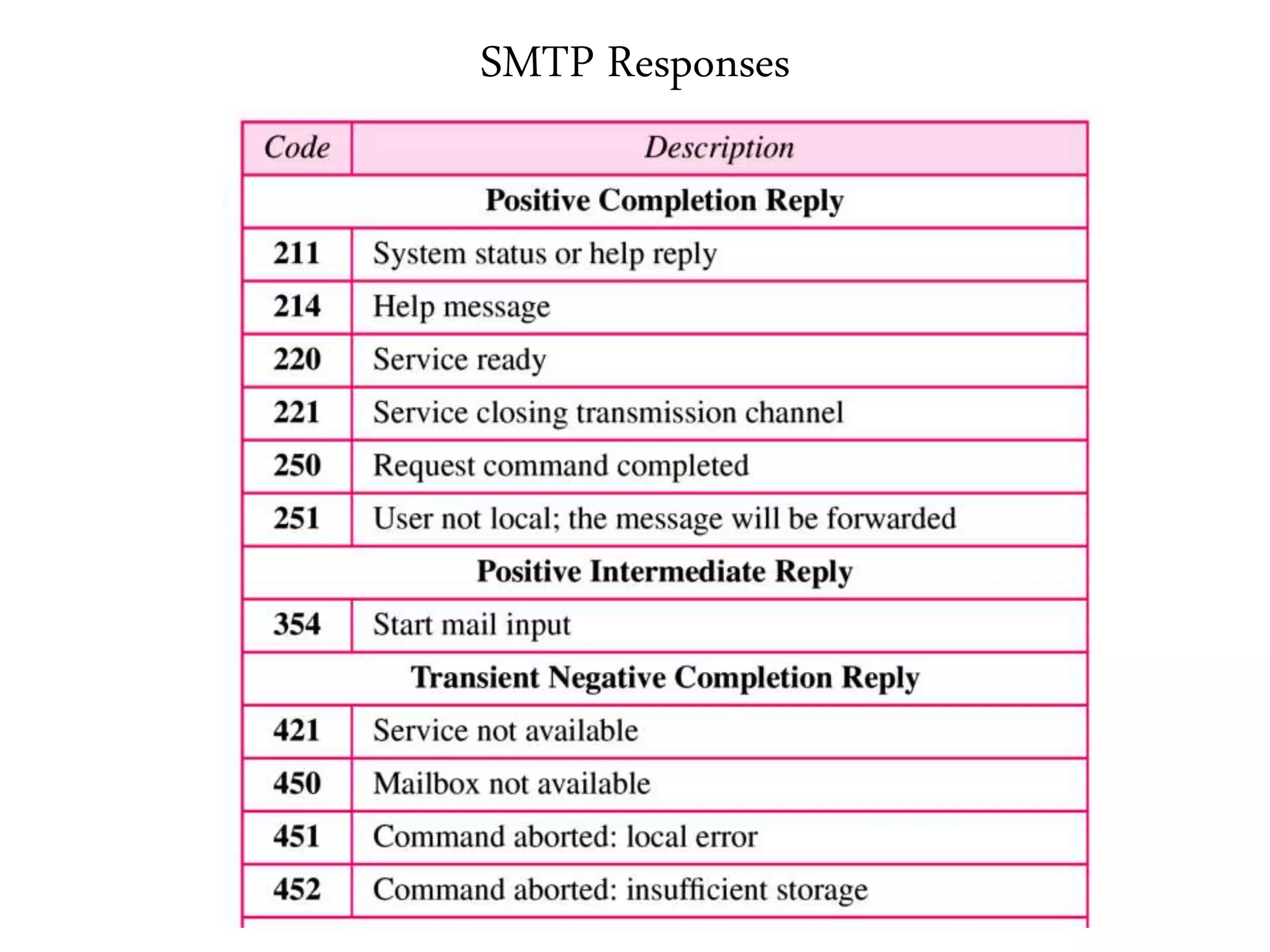
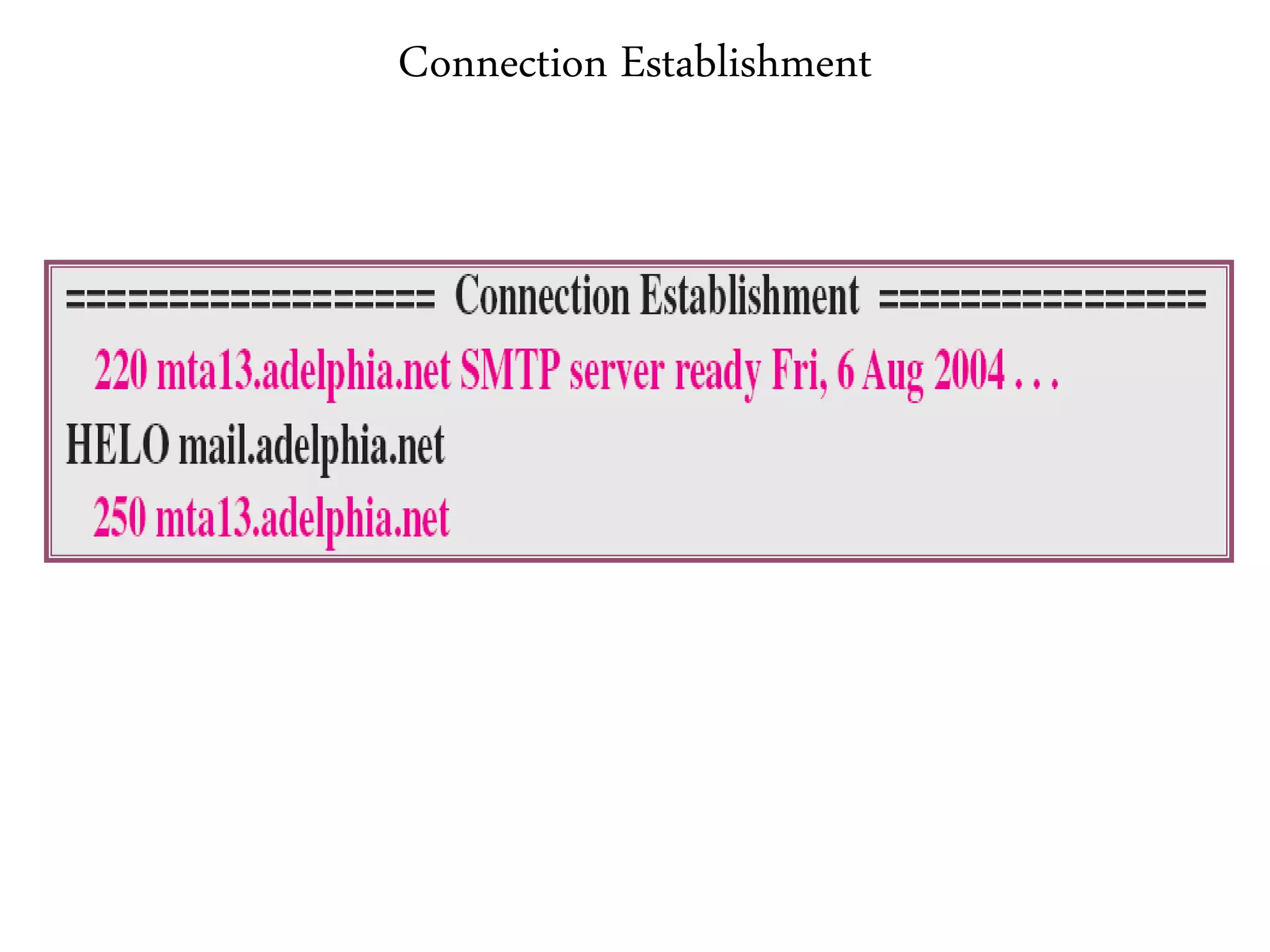
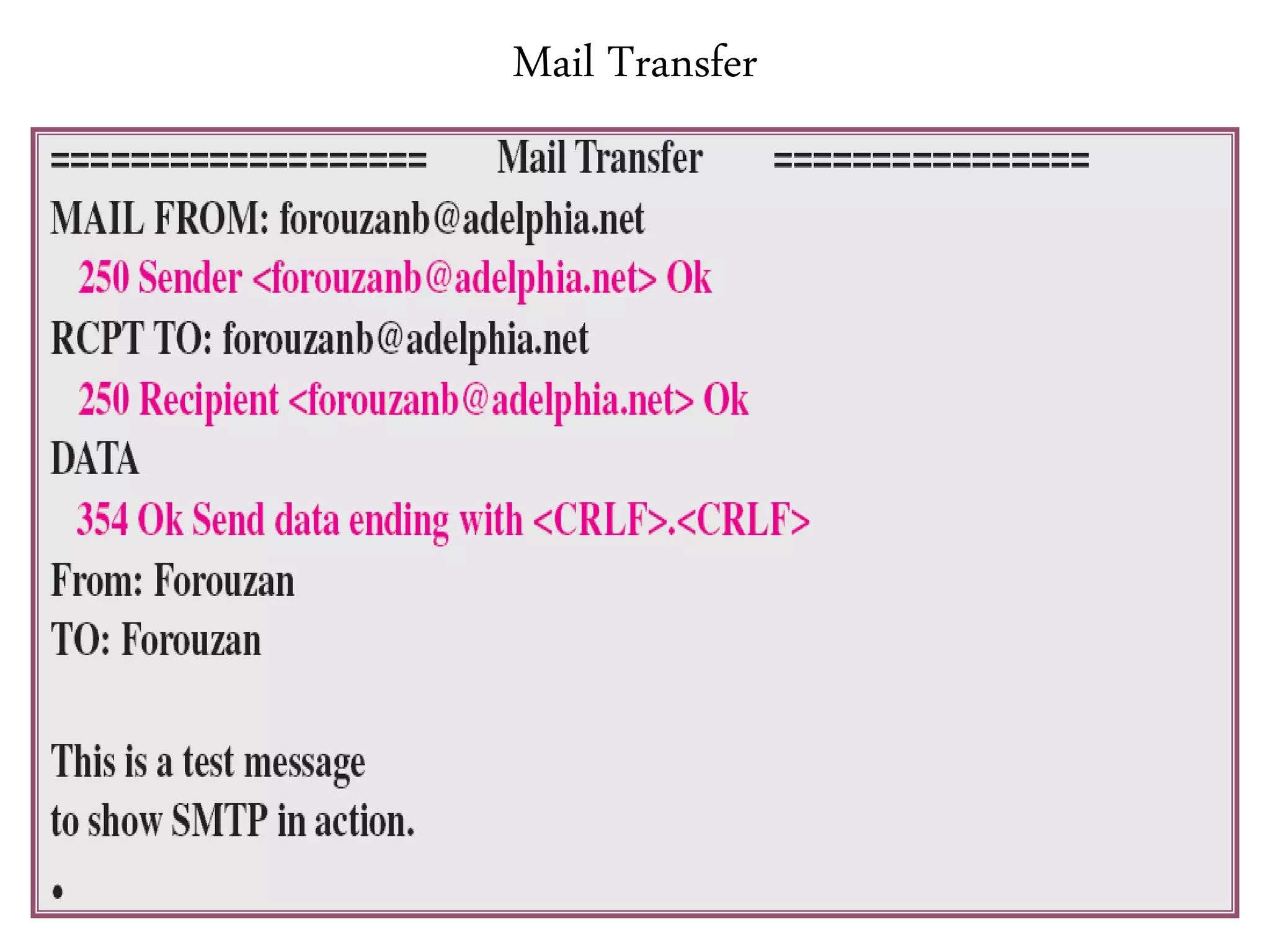
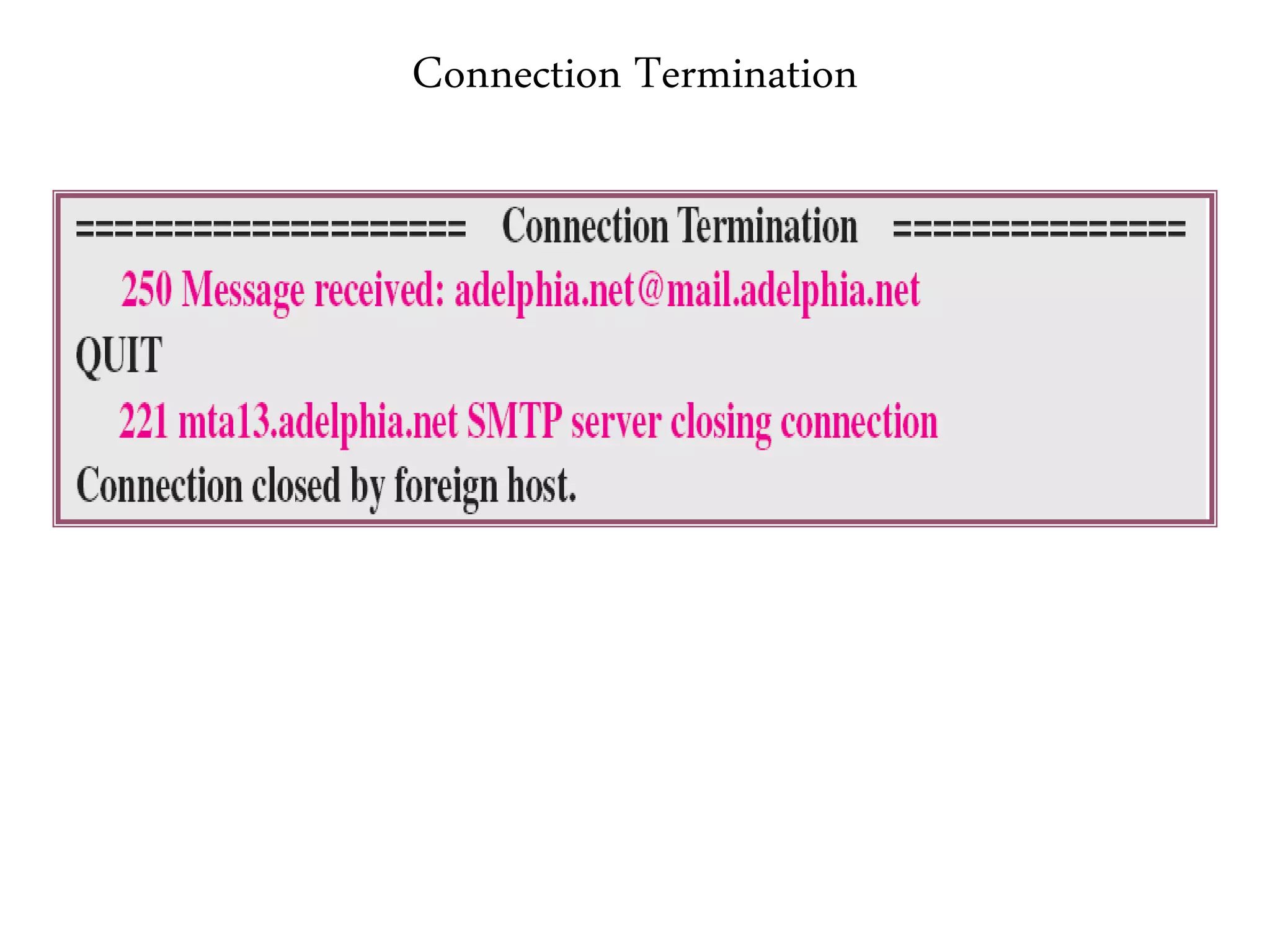
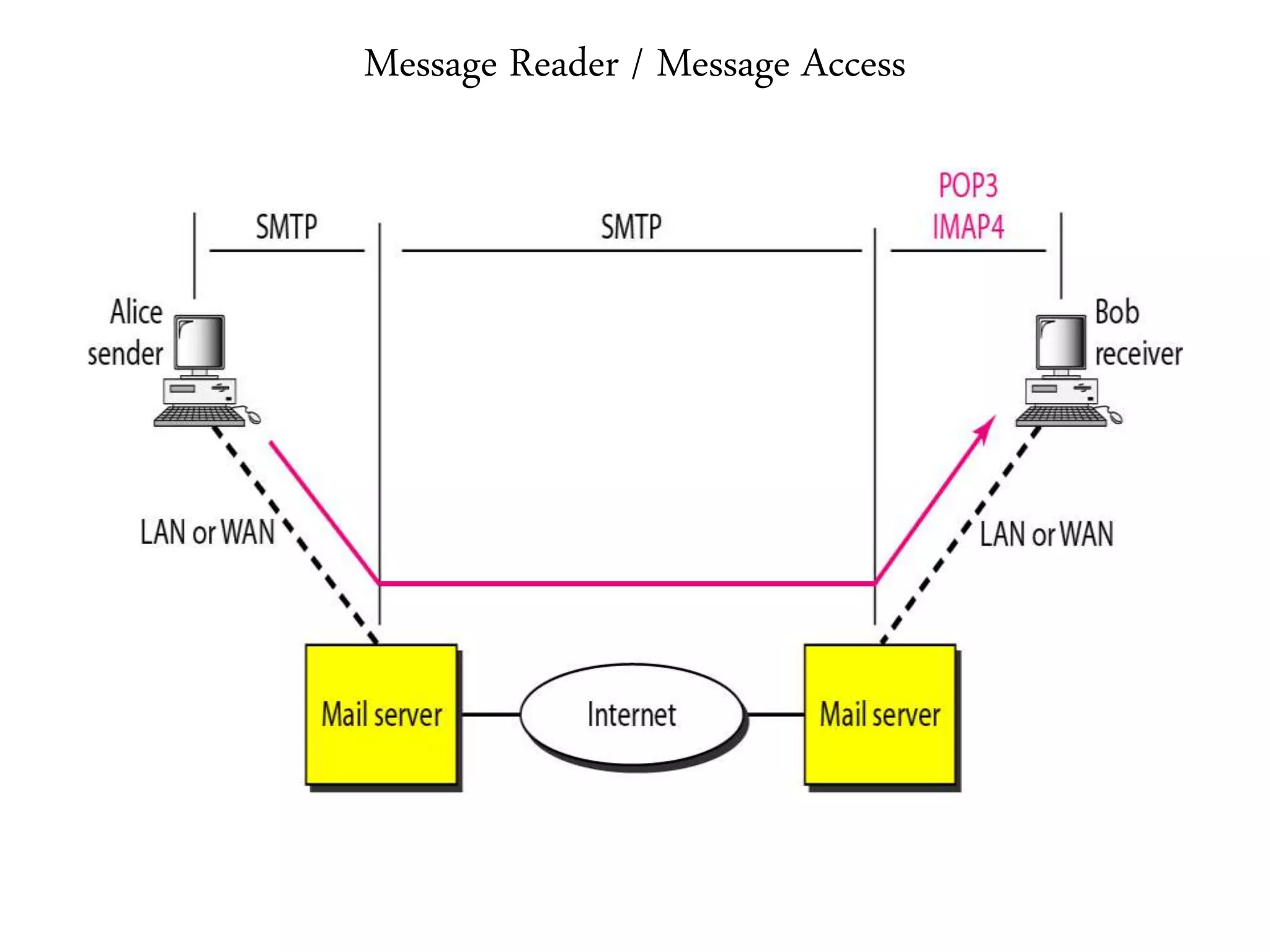
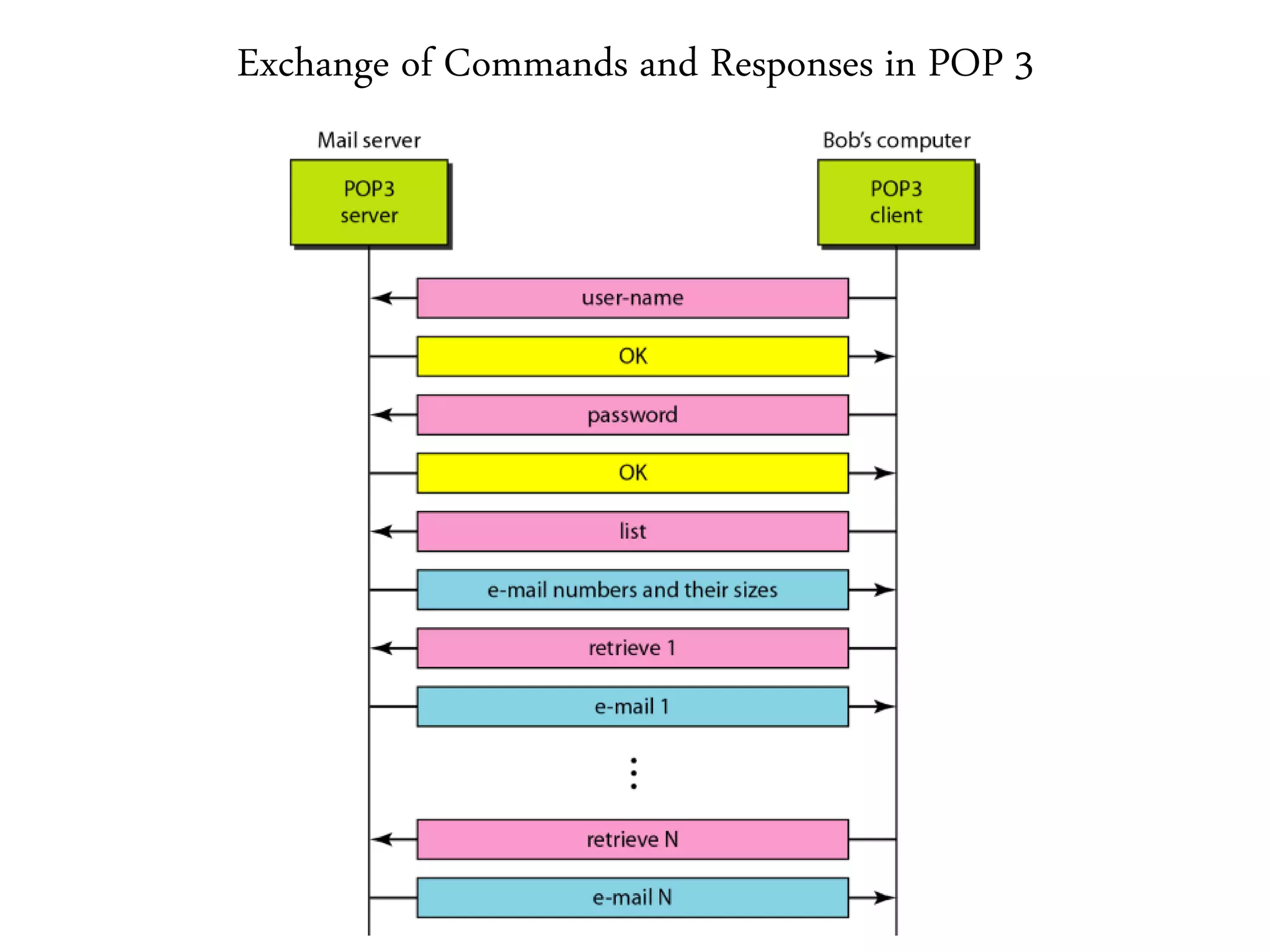
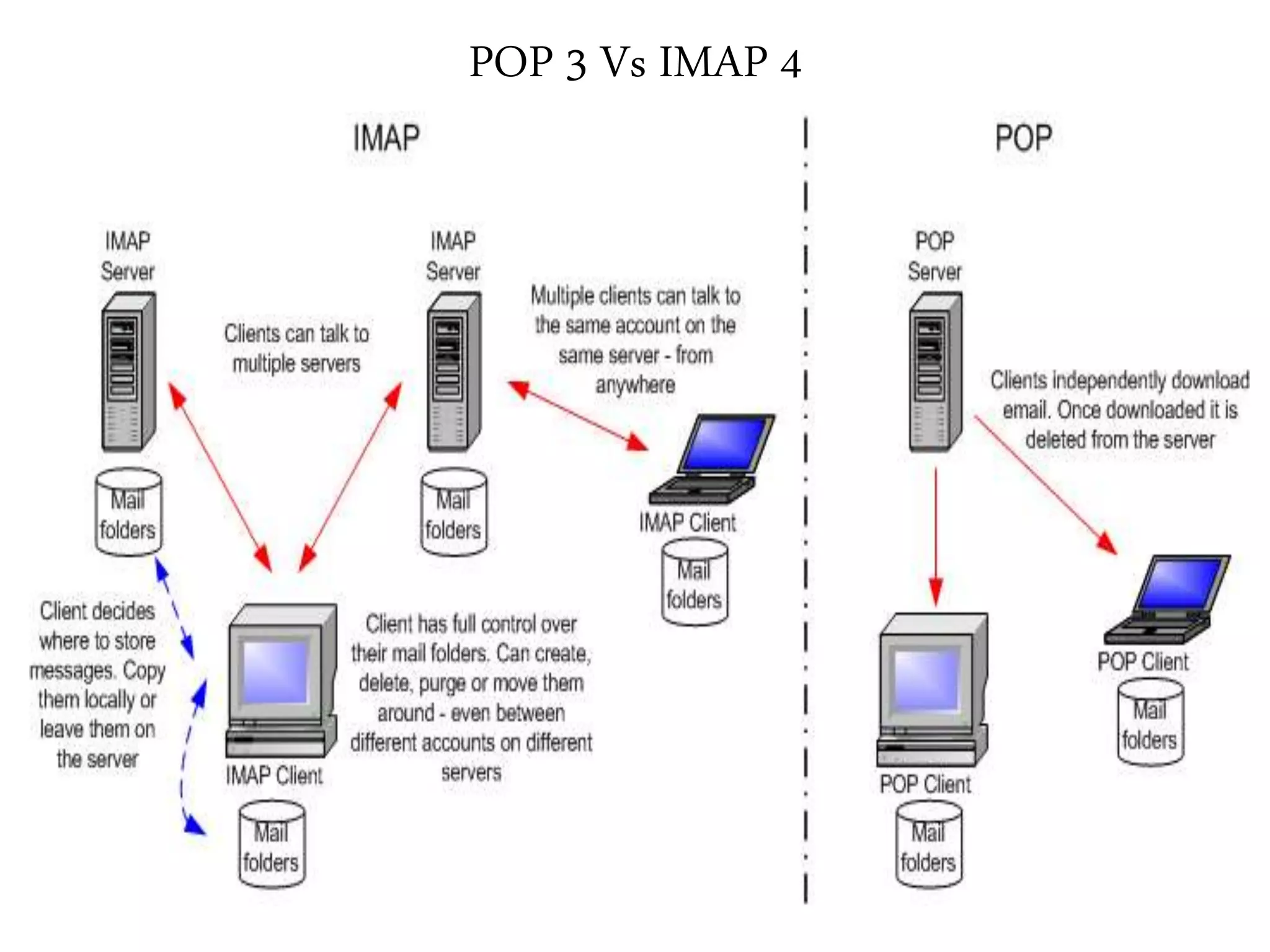
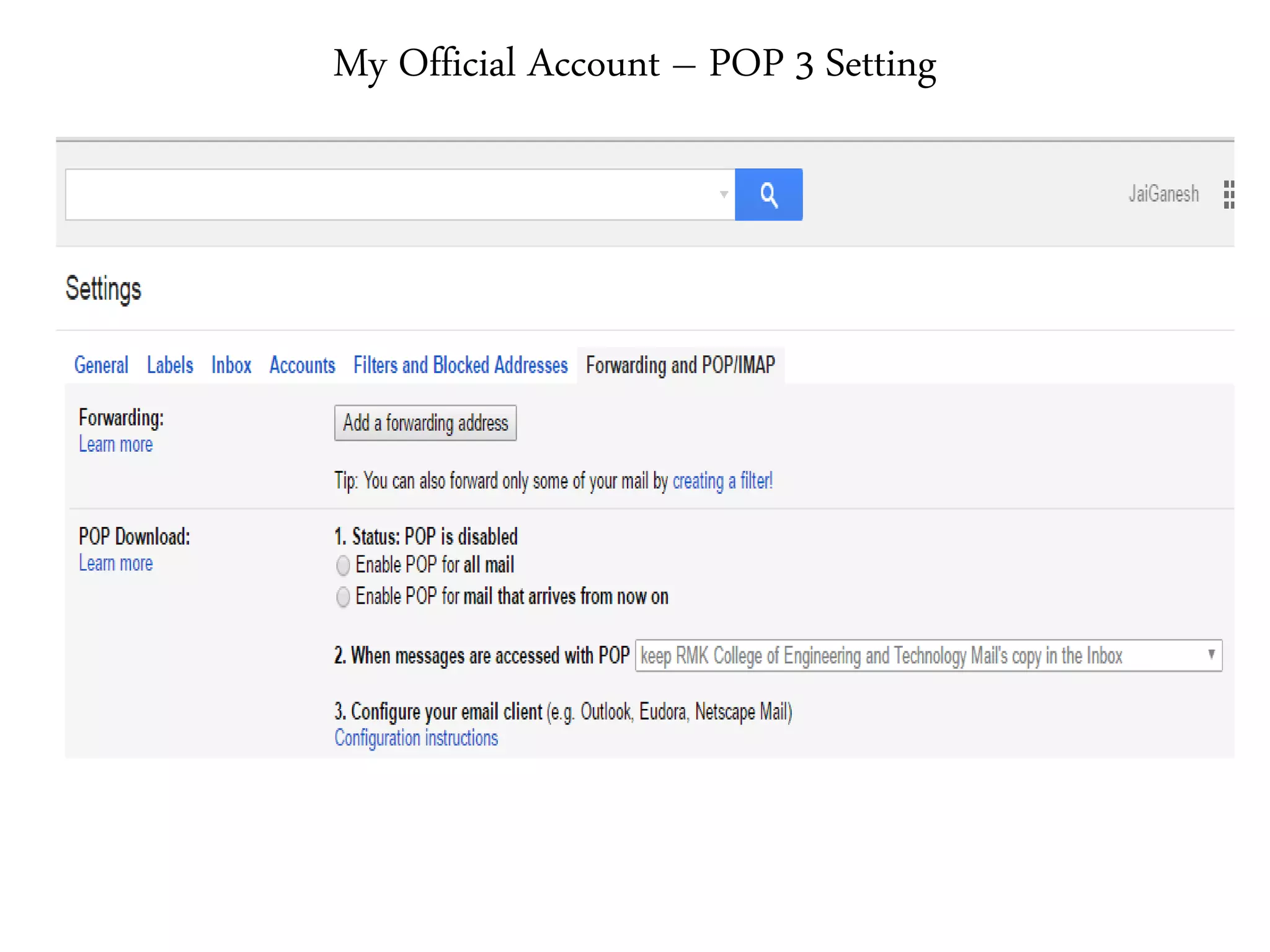
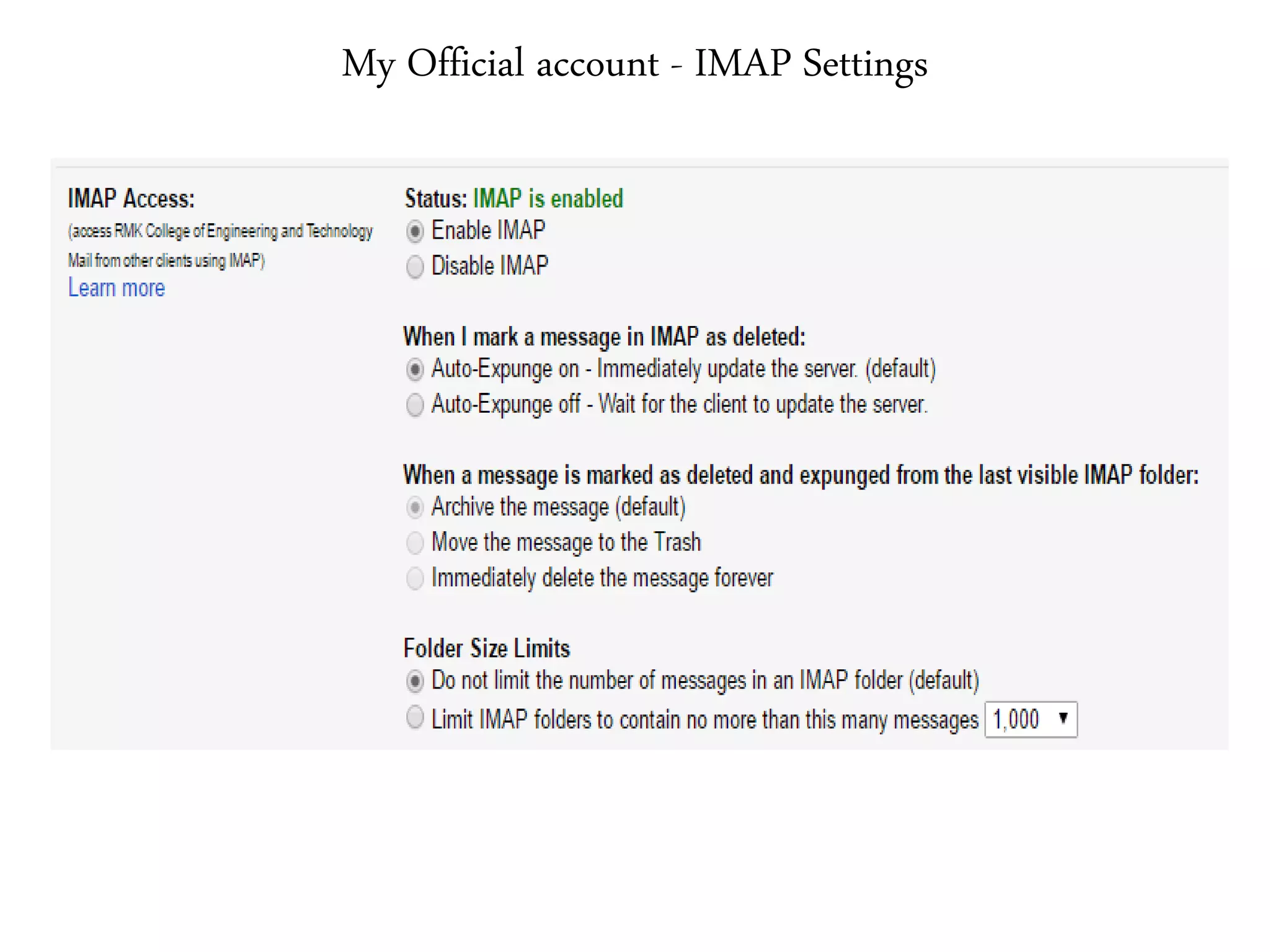
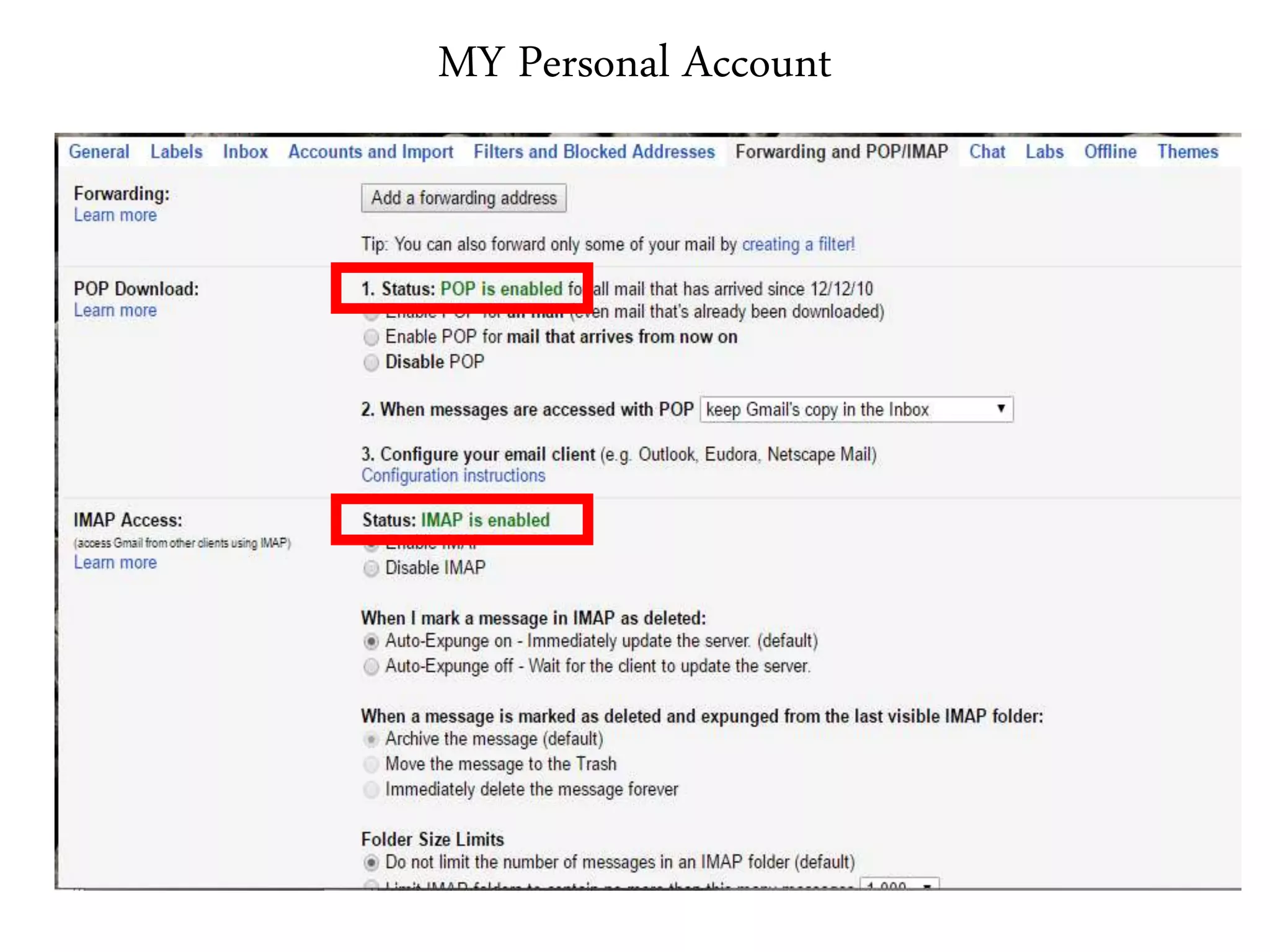
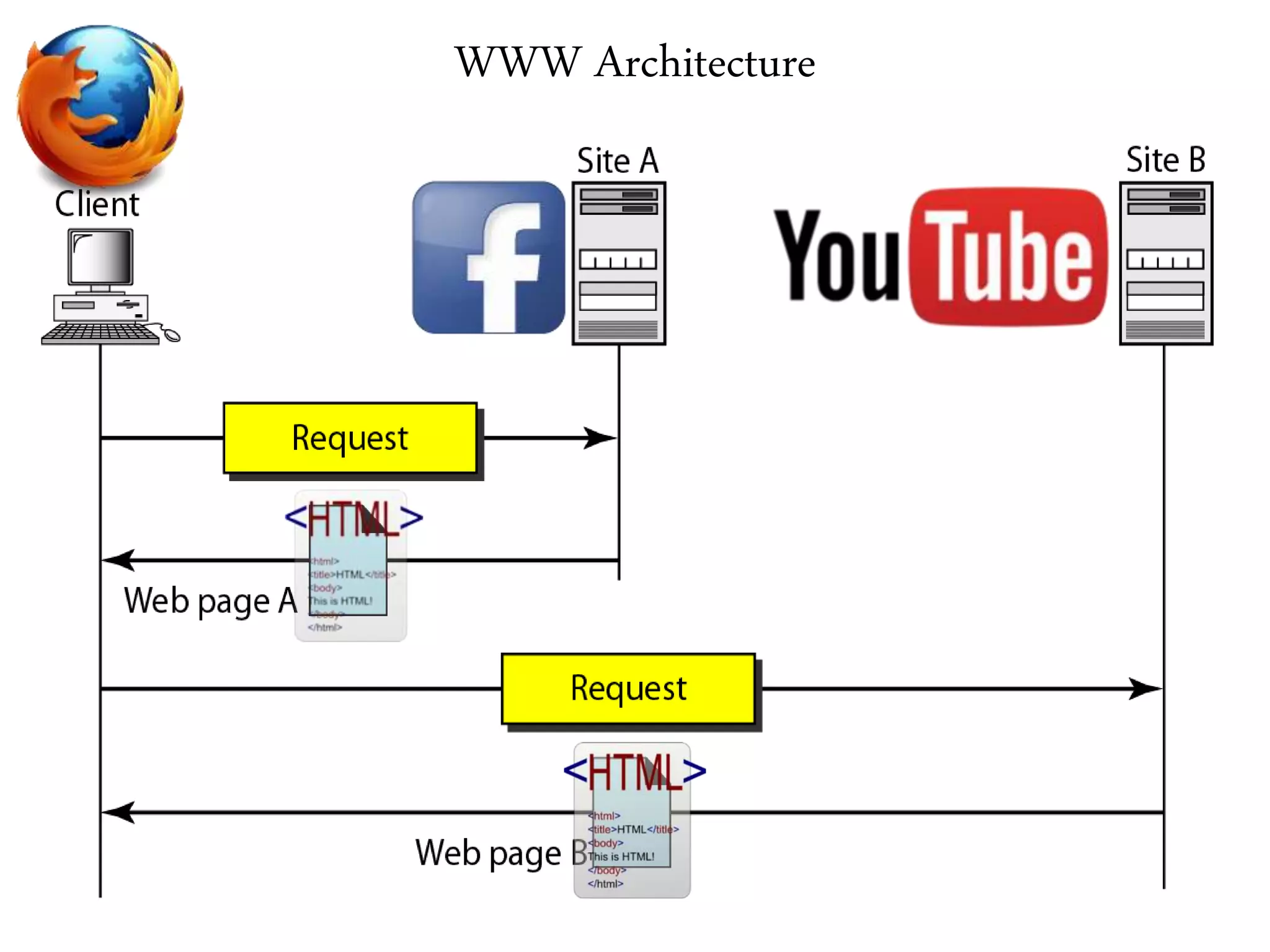
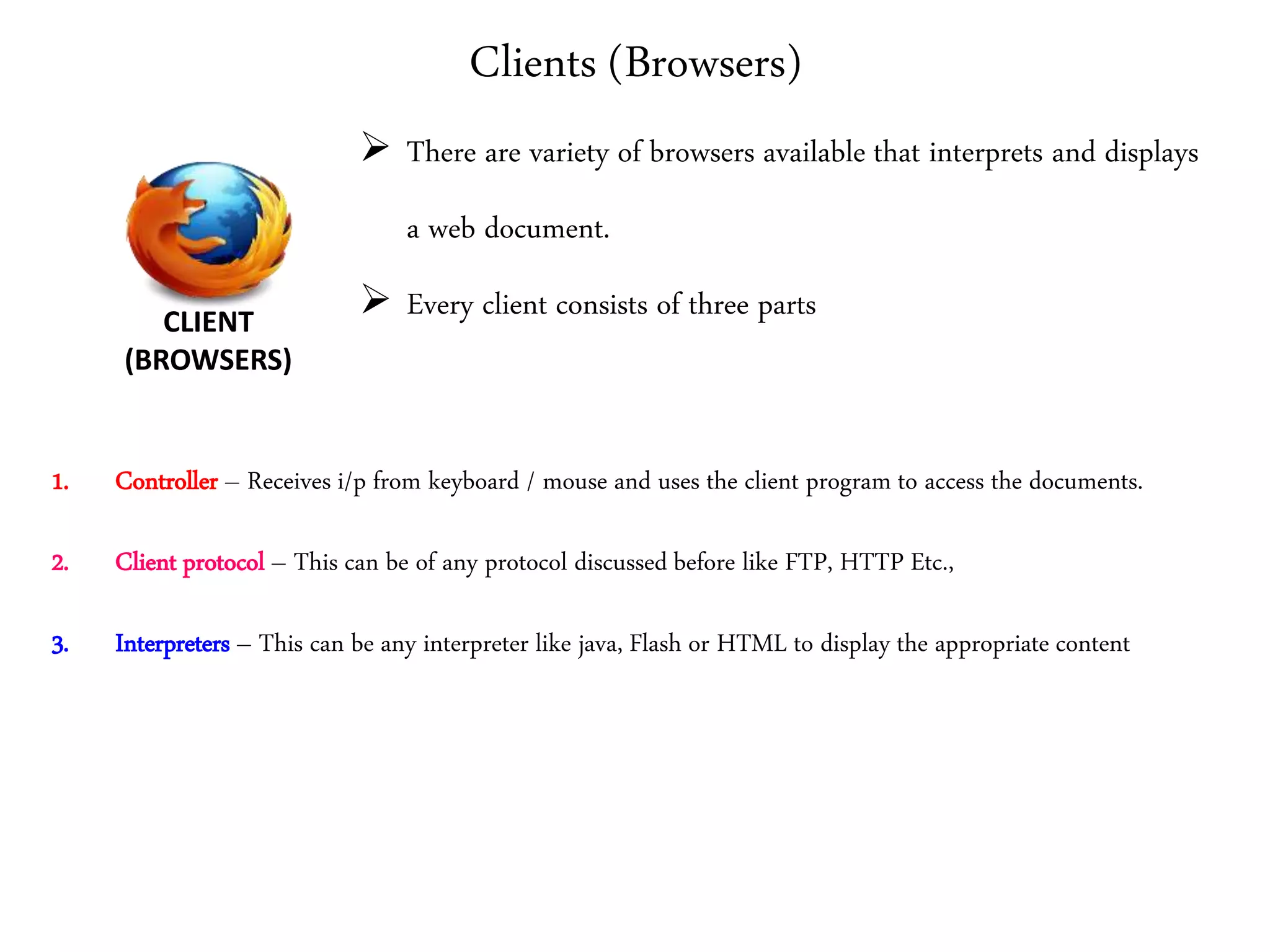
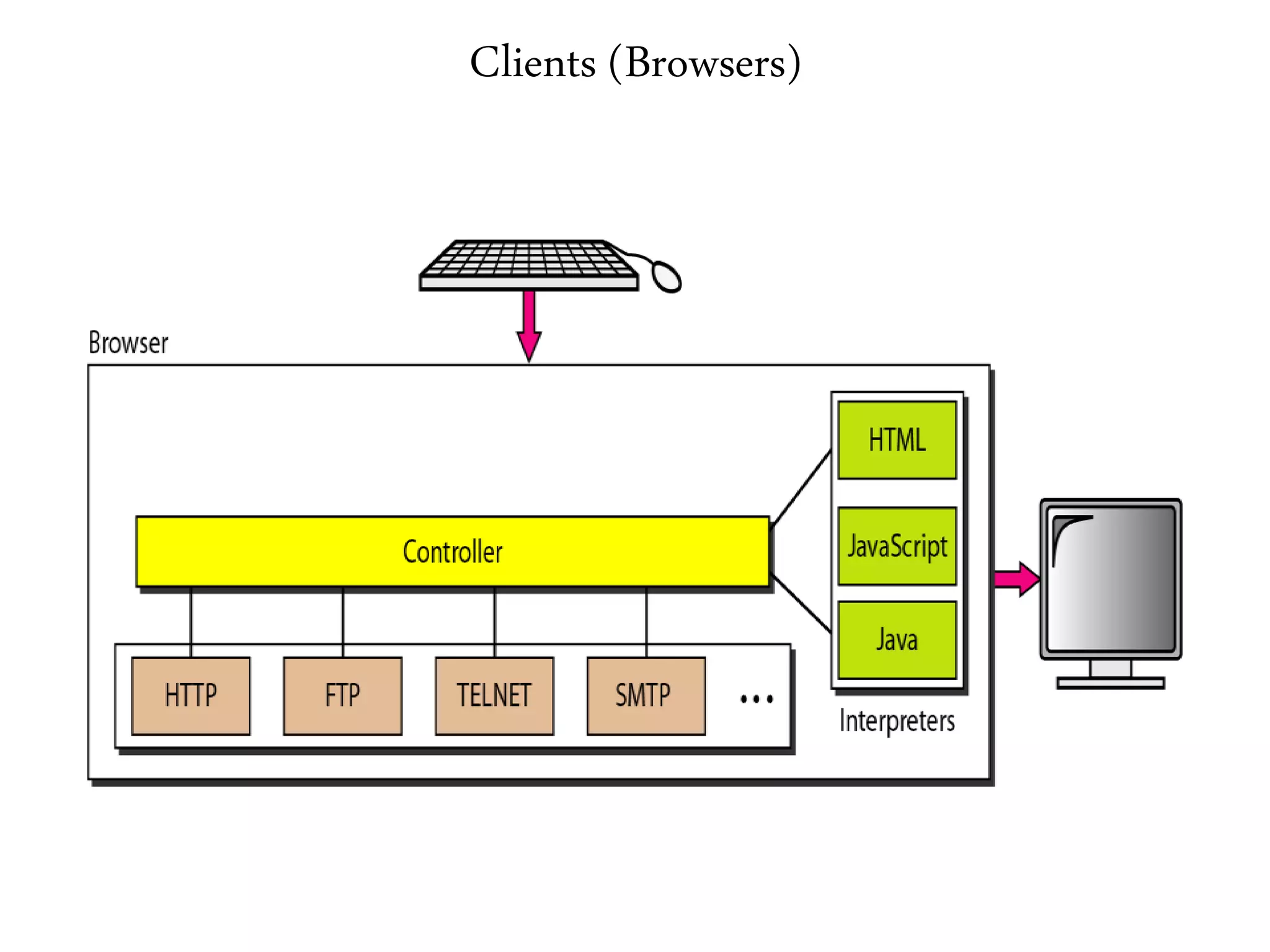
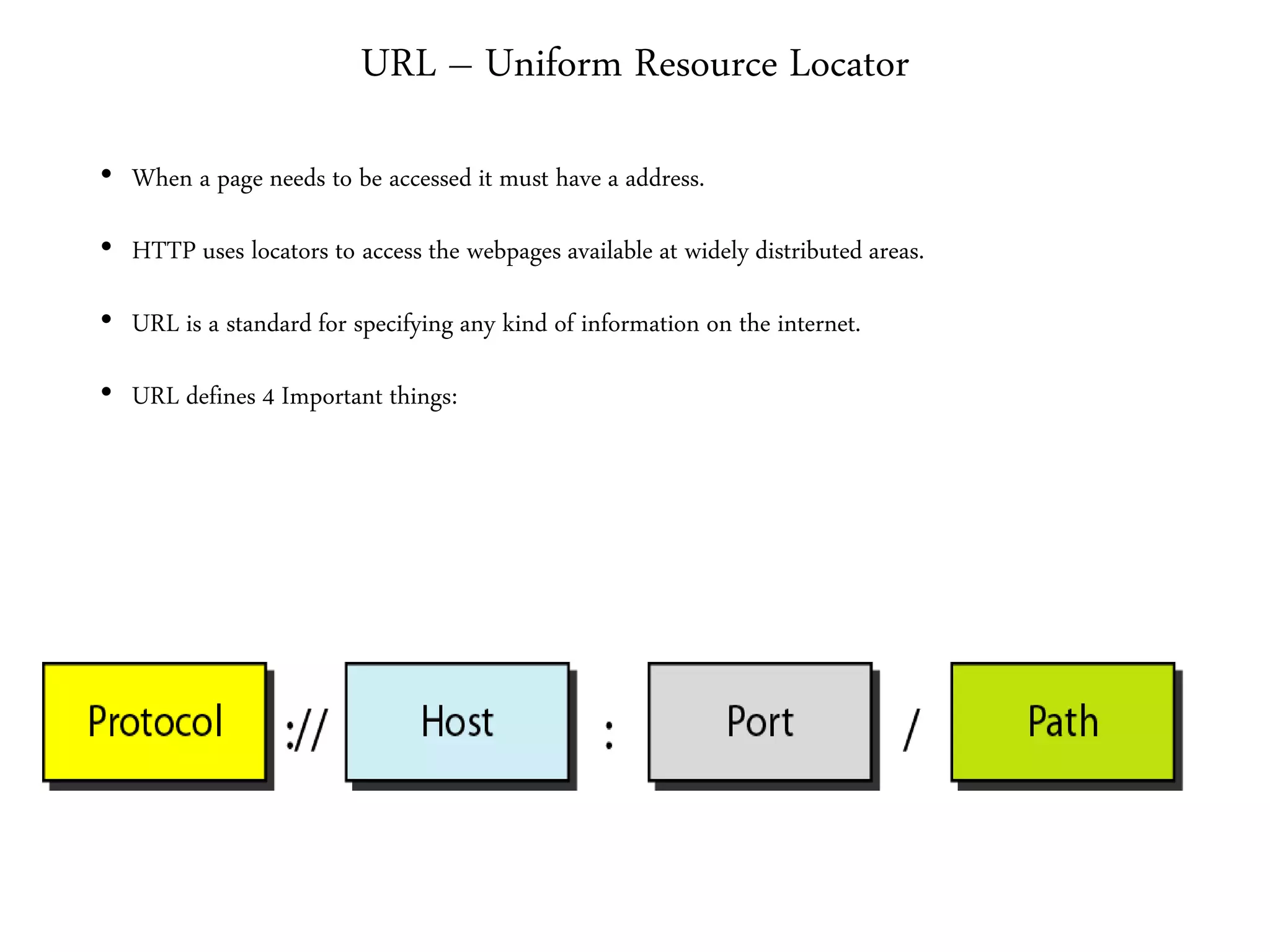
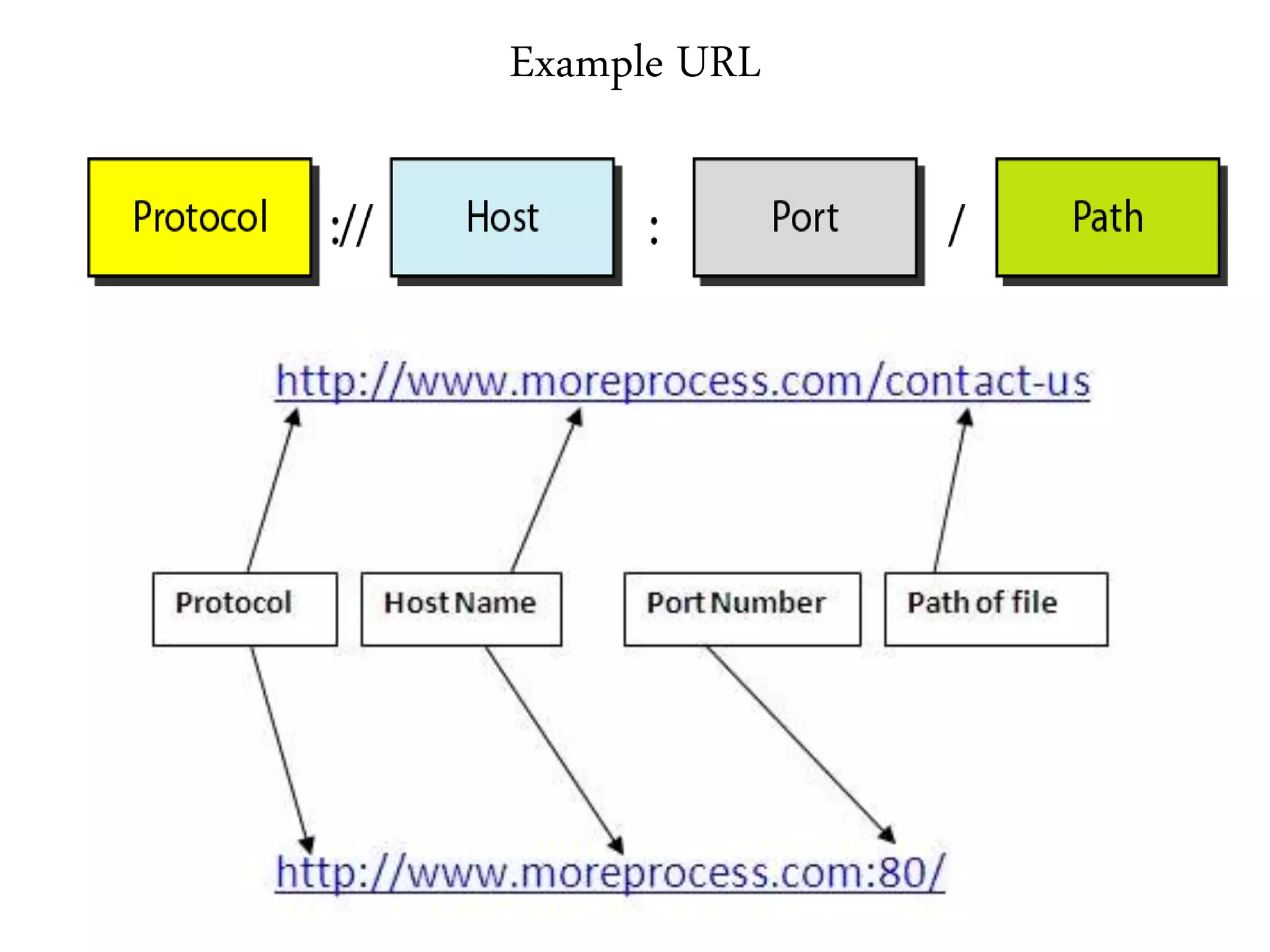
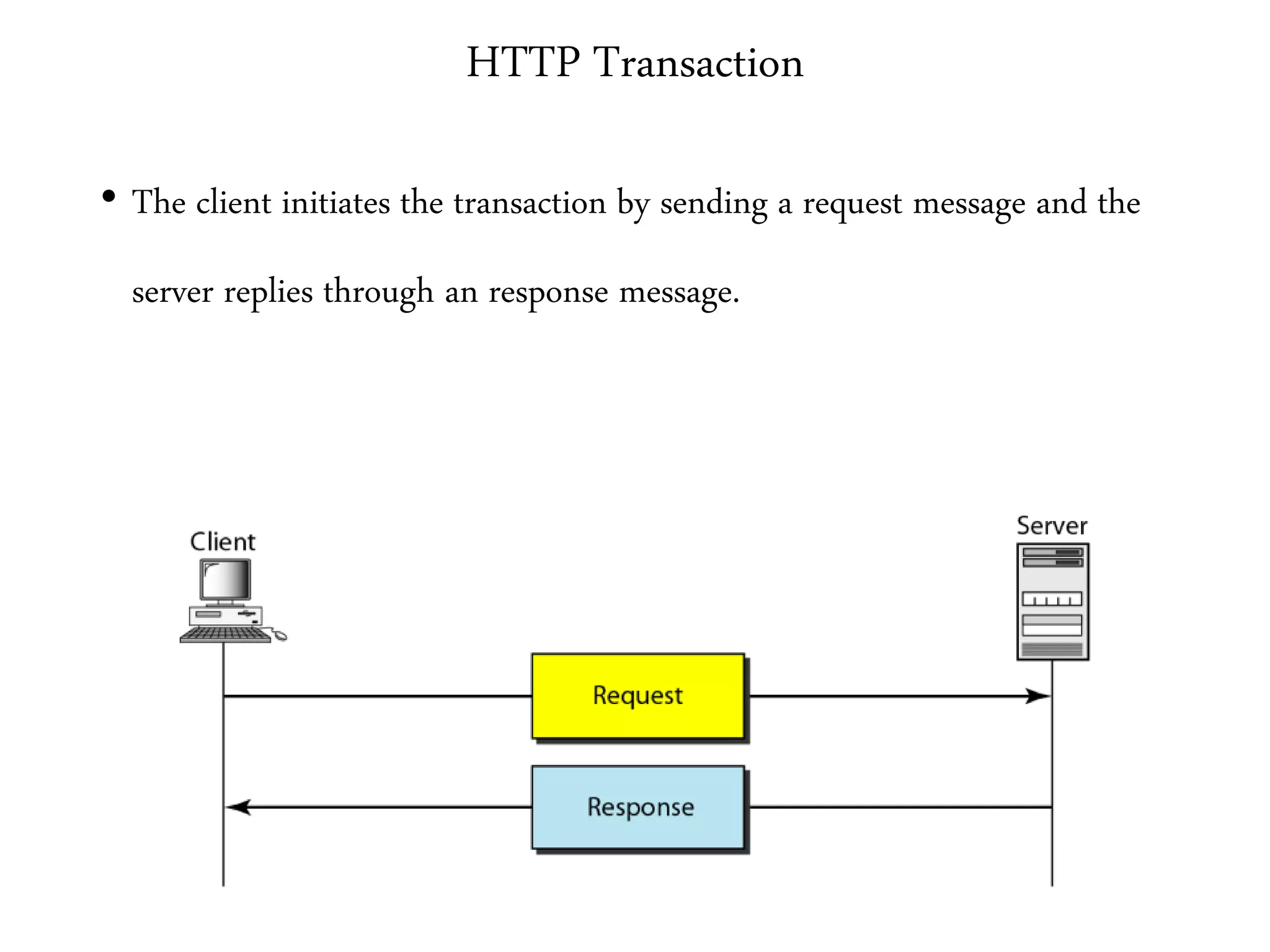
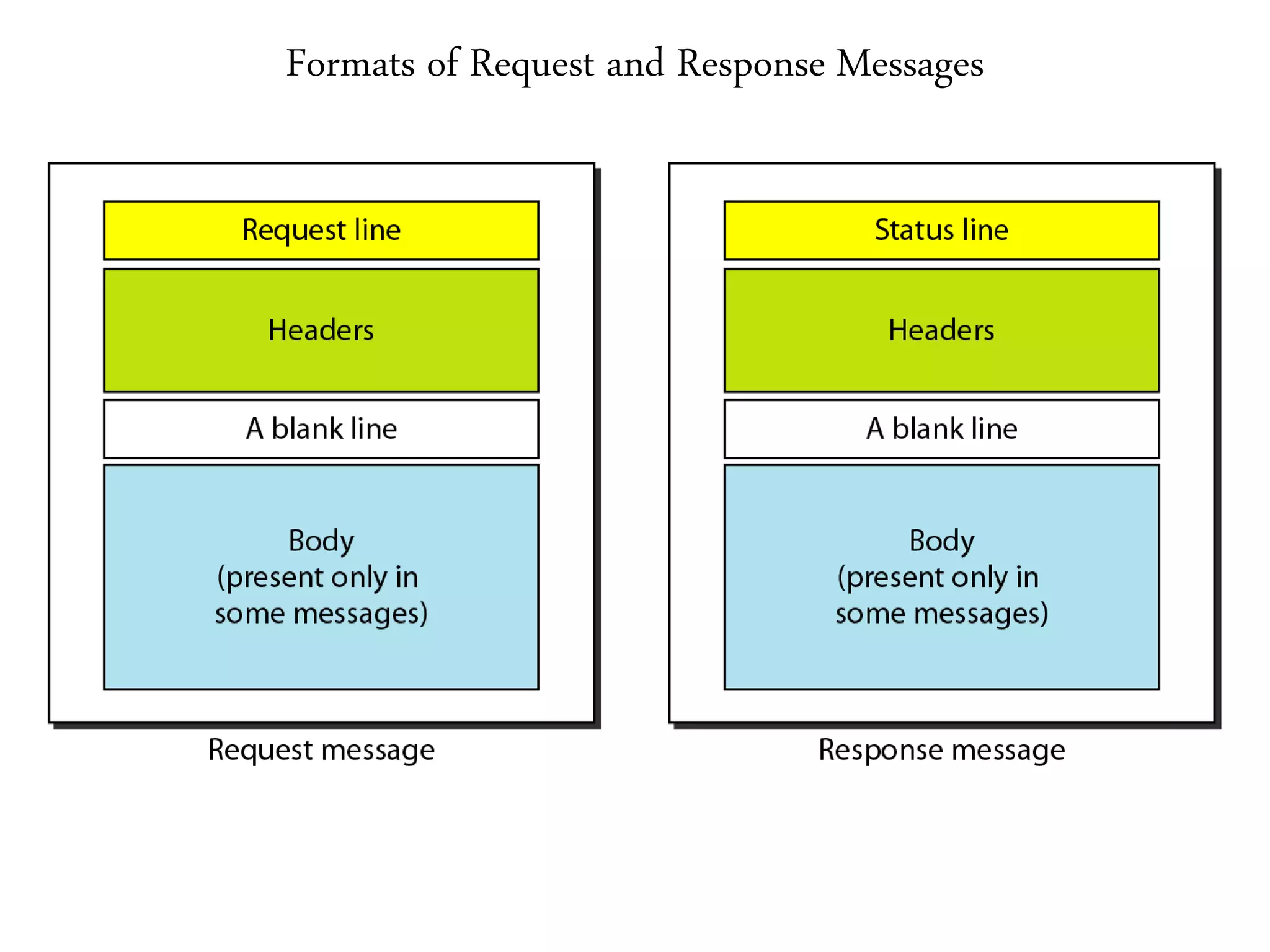
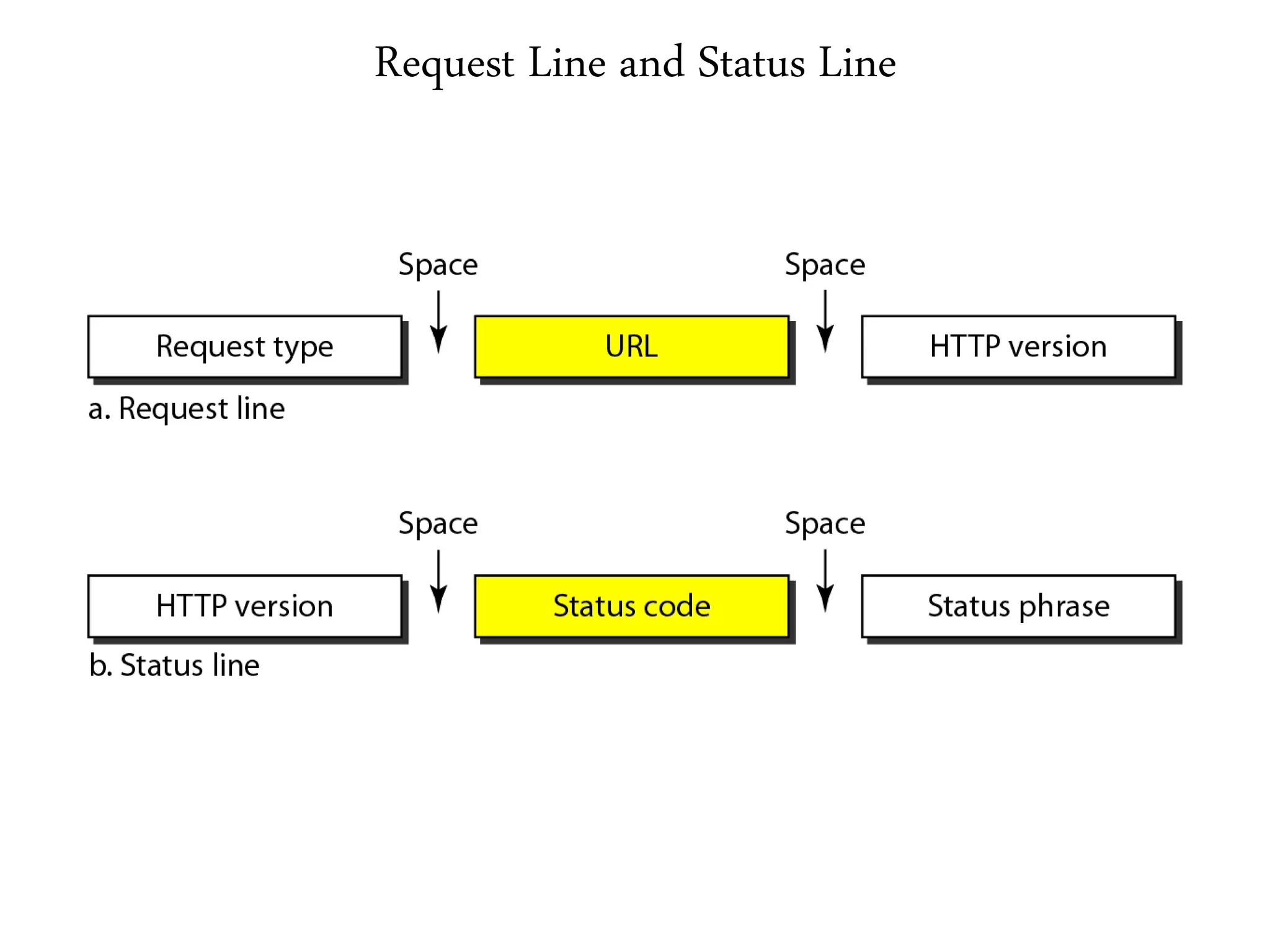
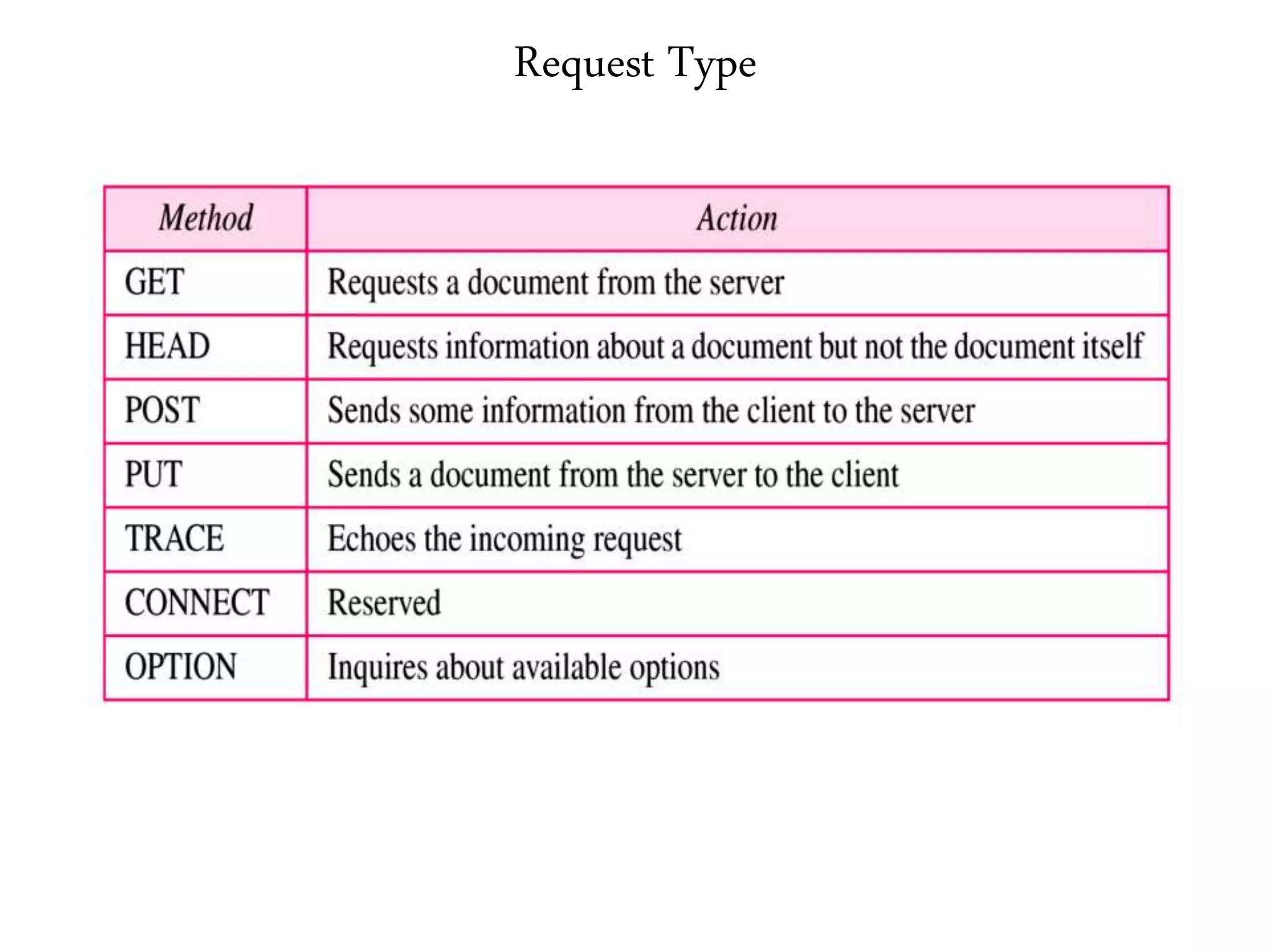
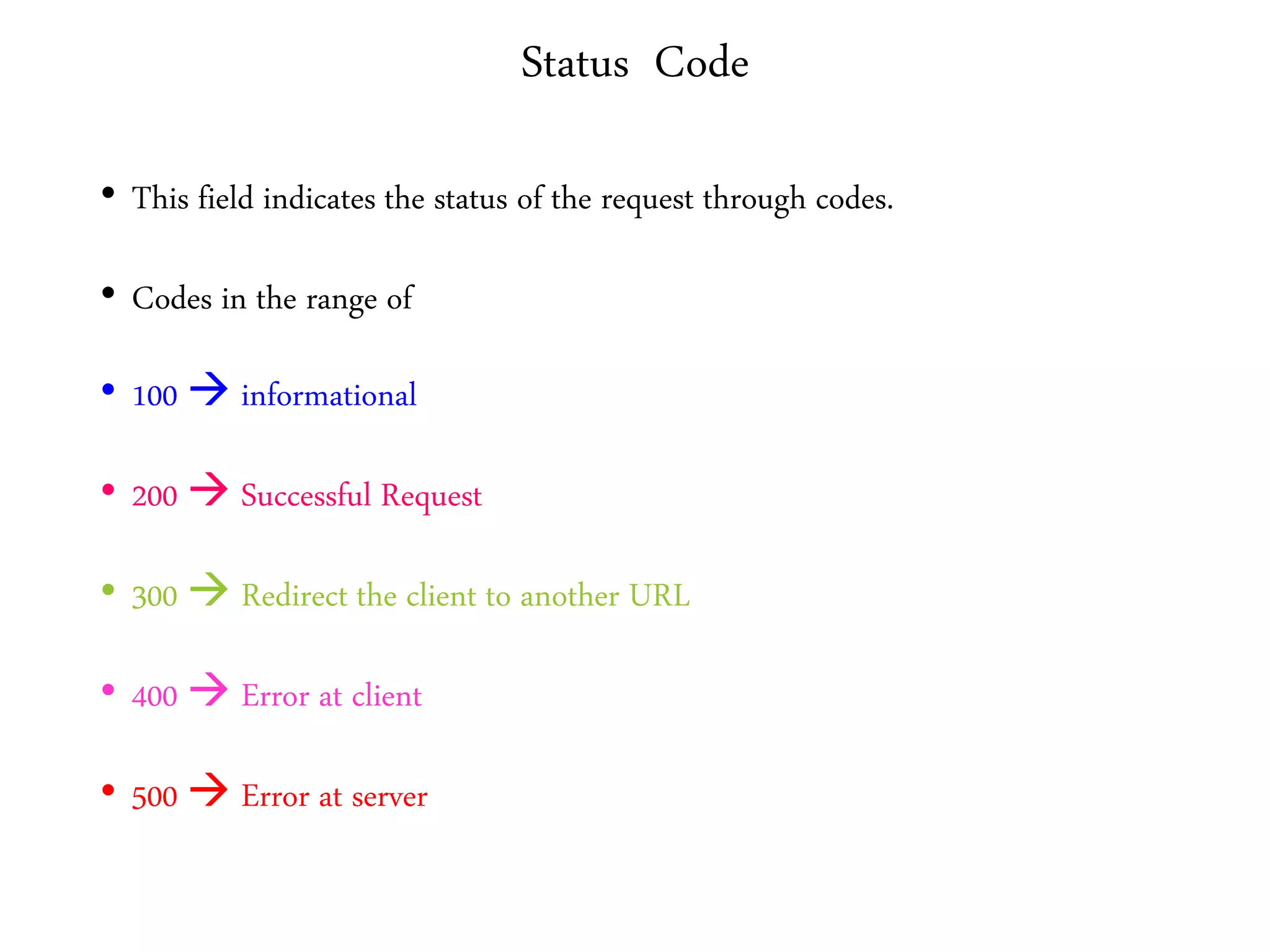
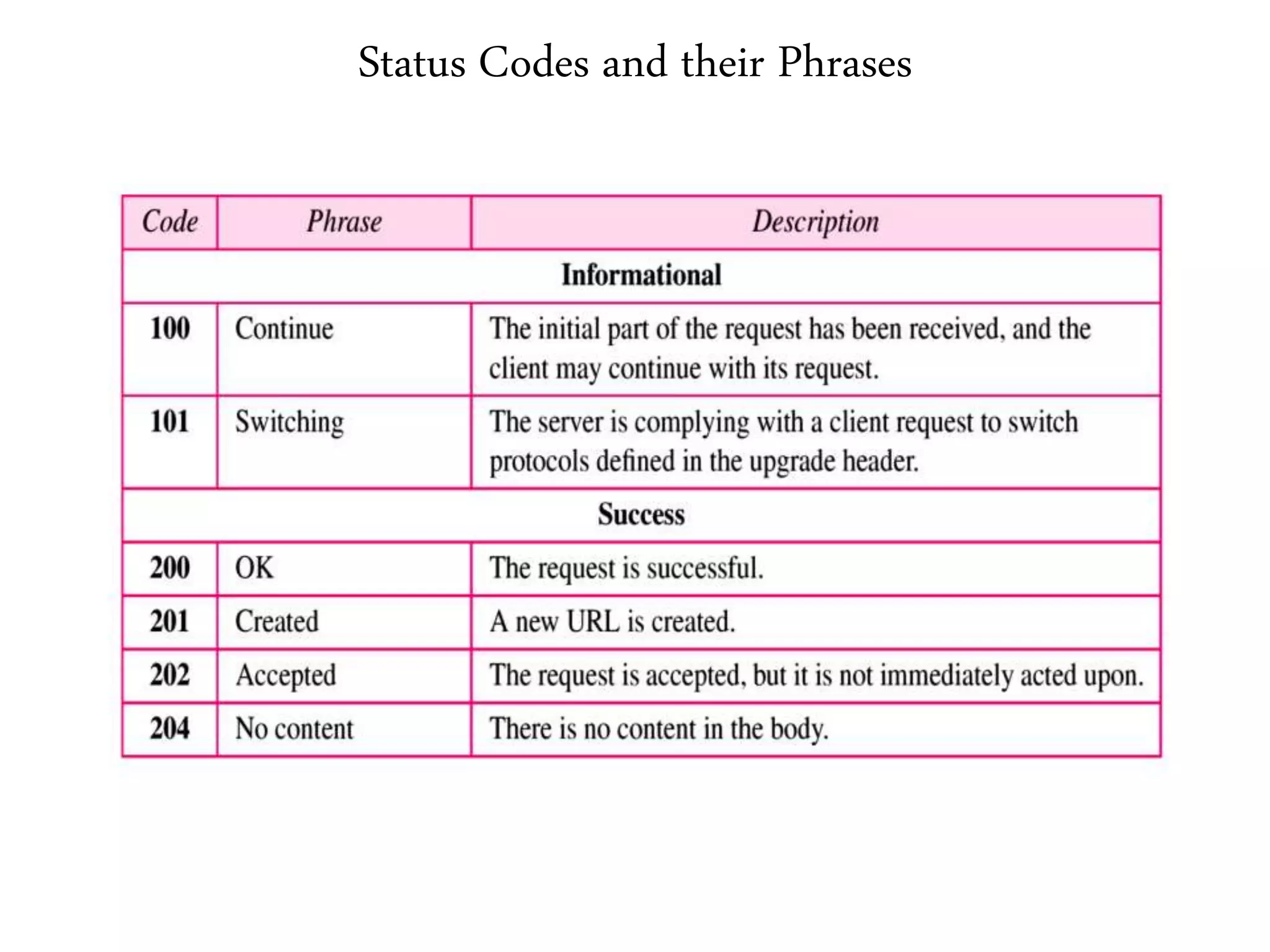
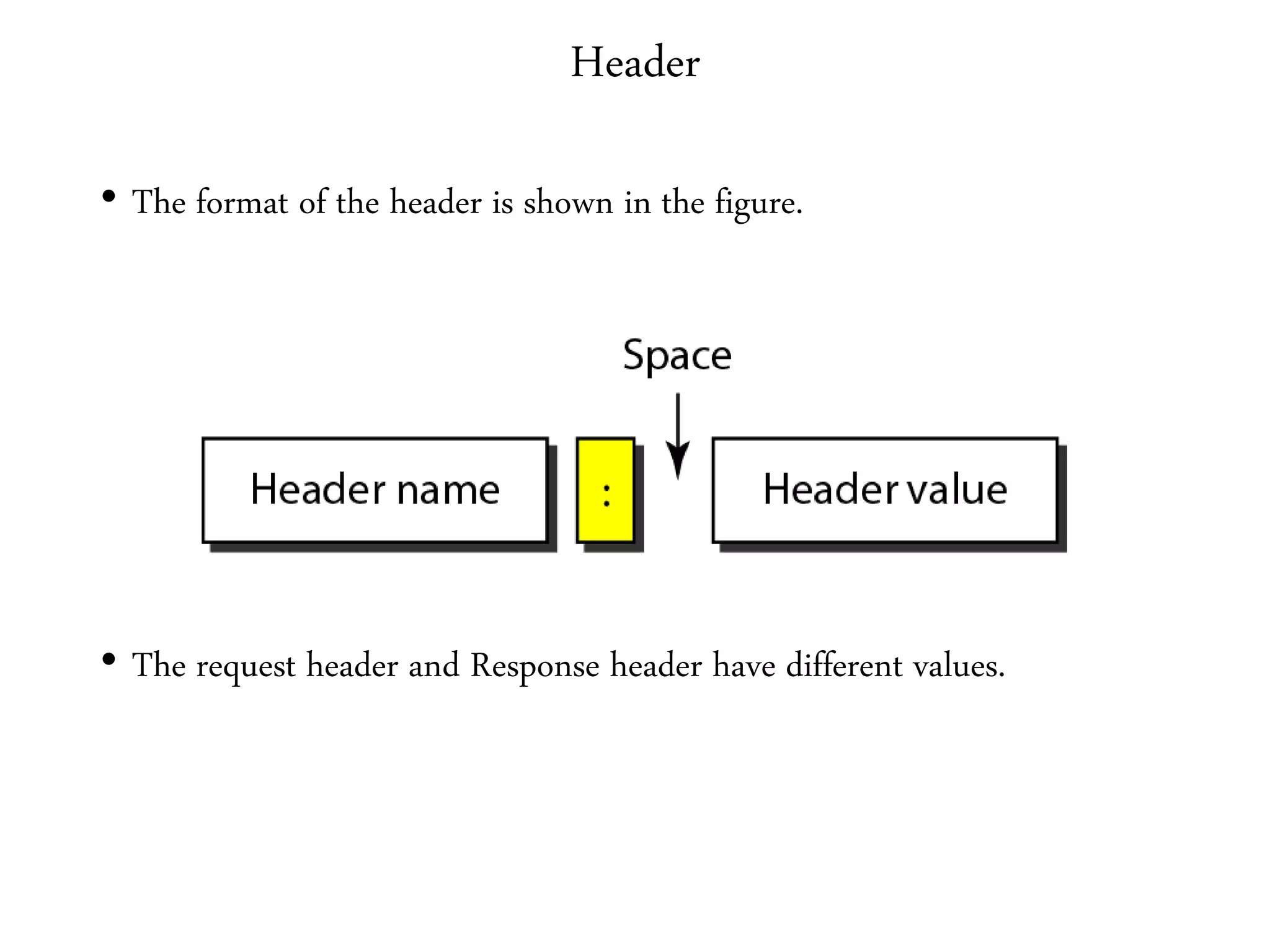
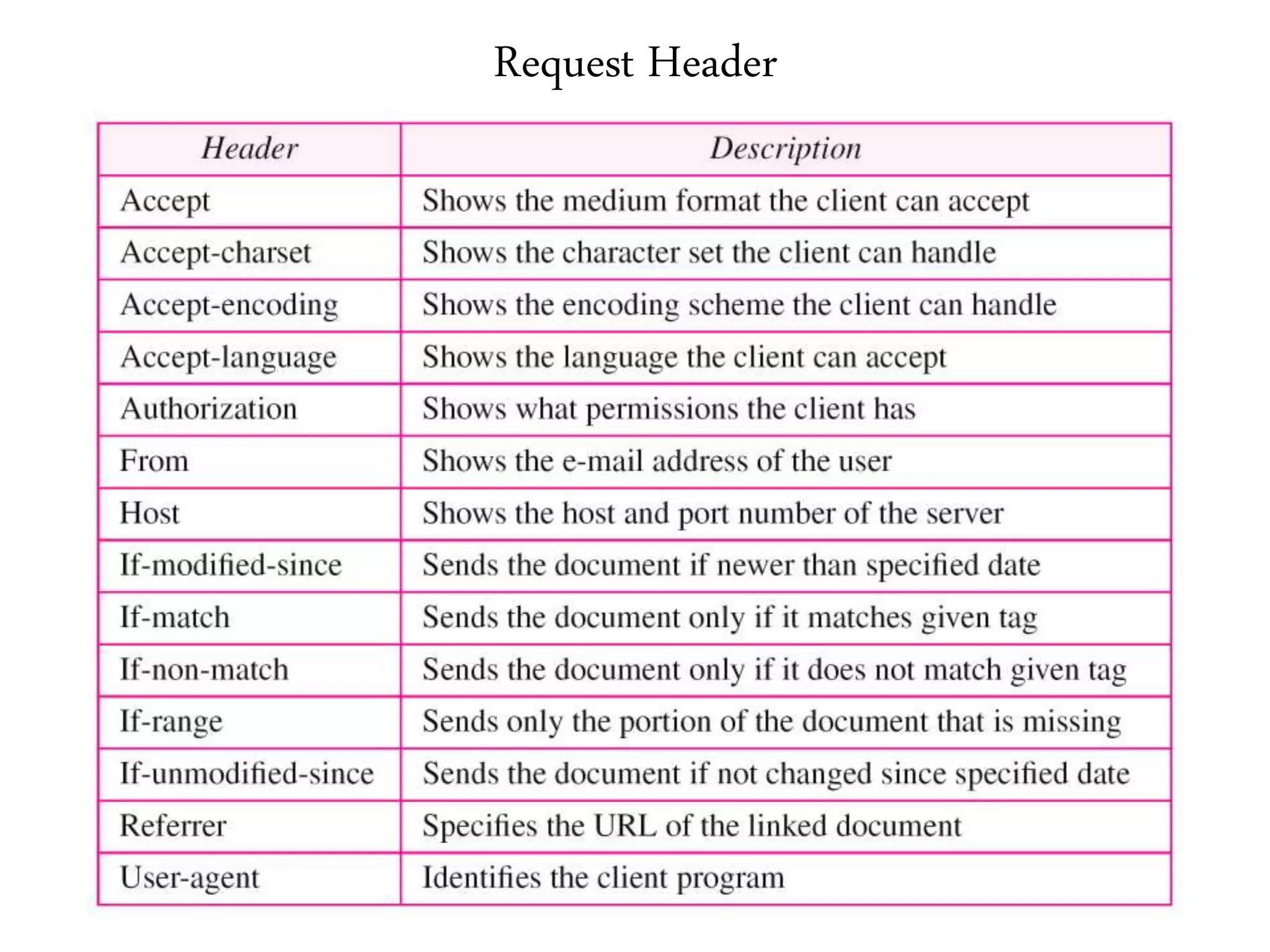
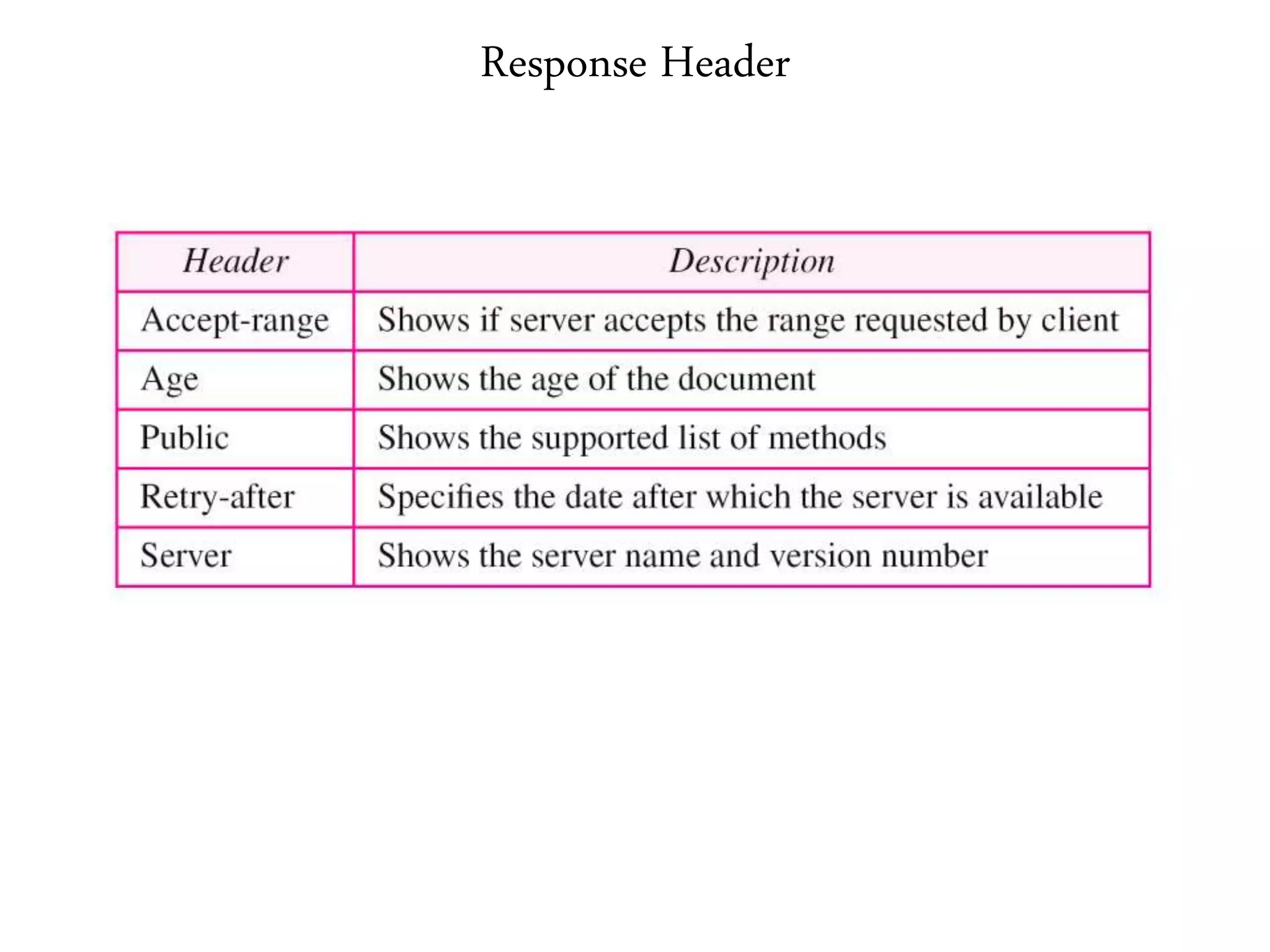
This document provides an overview of various application layer protocols including electronic mail (SMTP, POP3, IMAP), HTTP, web services, DNS, and SNMP. It discusses the distinction between application programs and protocols, how protocols implement remote procedure calls, and that protocols have companion protocols that define message formats. Specific protocols covered in more detail include SMTP for mail transfer, POP3 and IMAP for mail access, HTTP for web access, and the general functions of DNS and SNMP in networks.