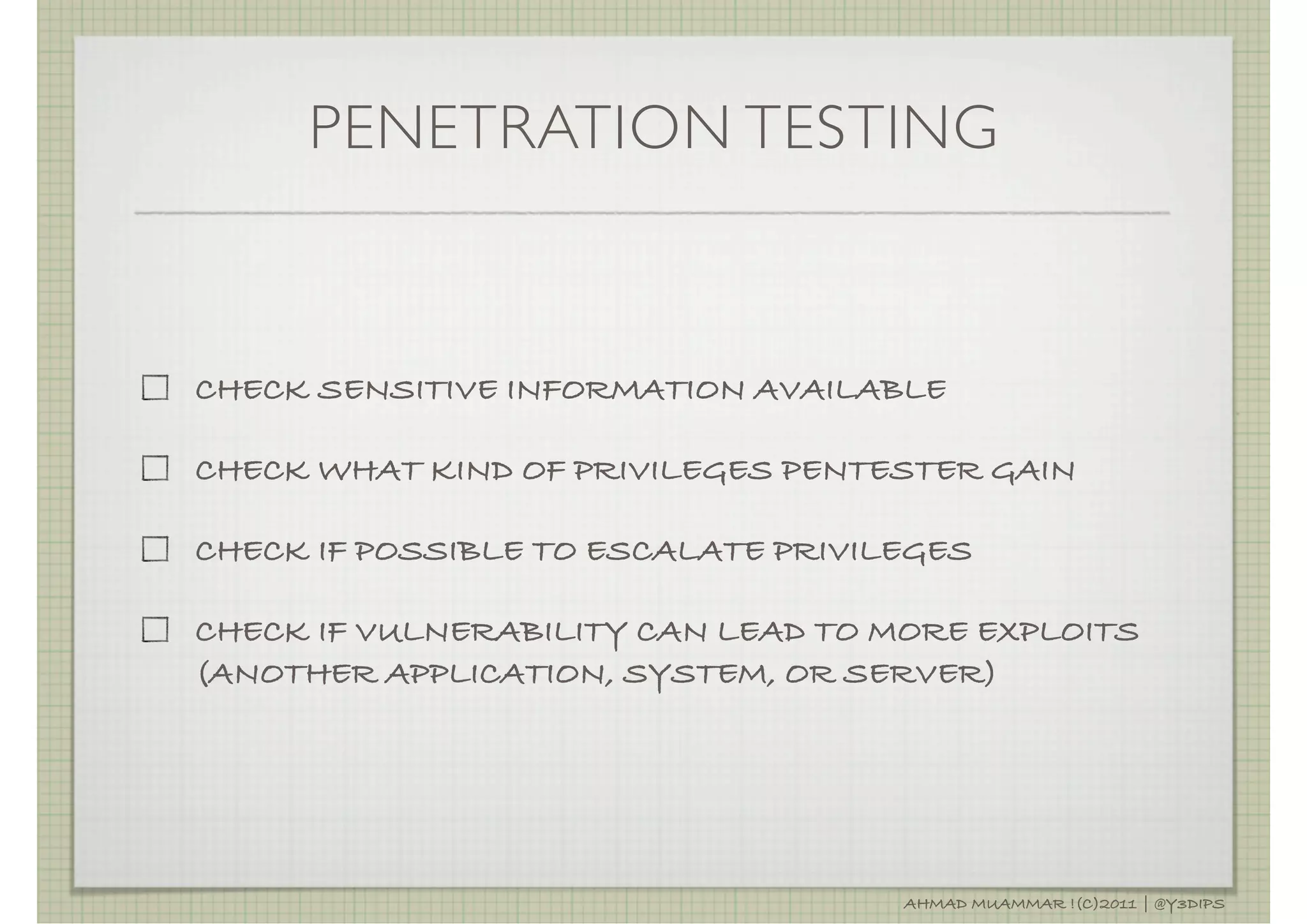
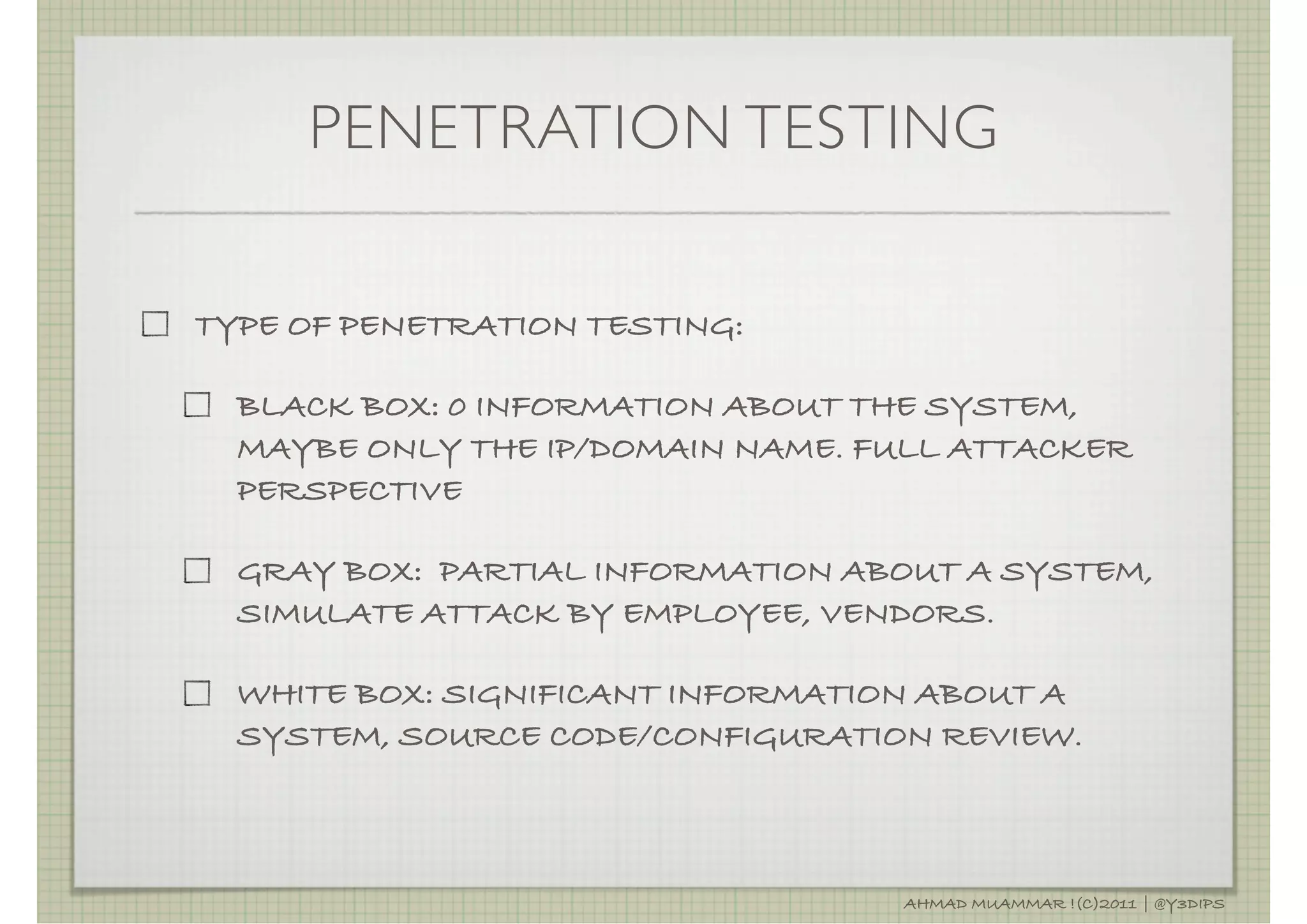
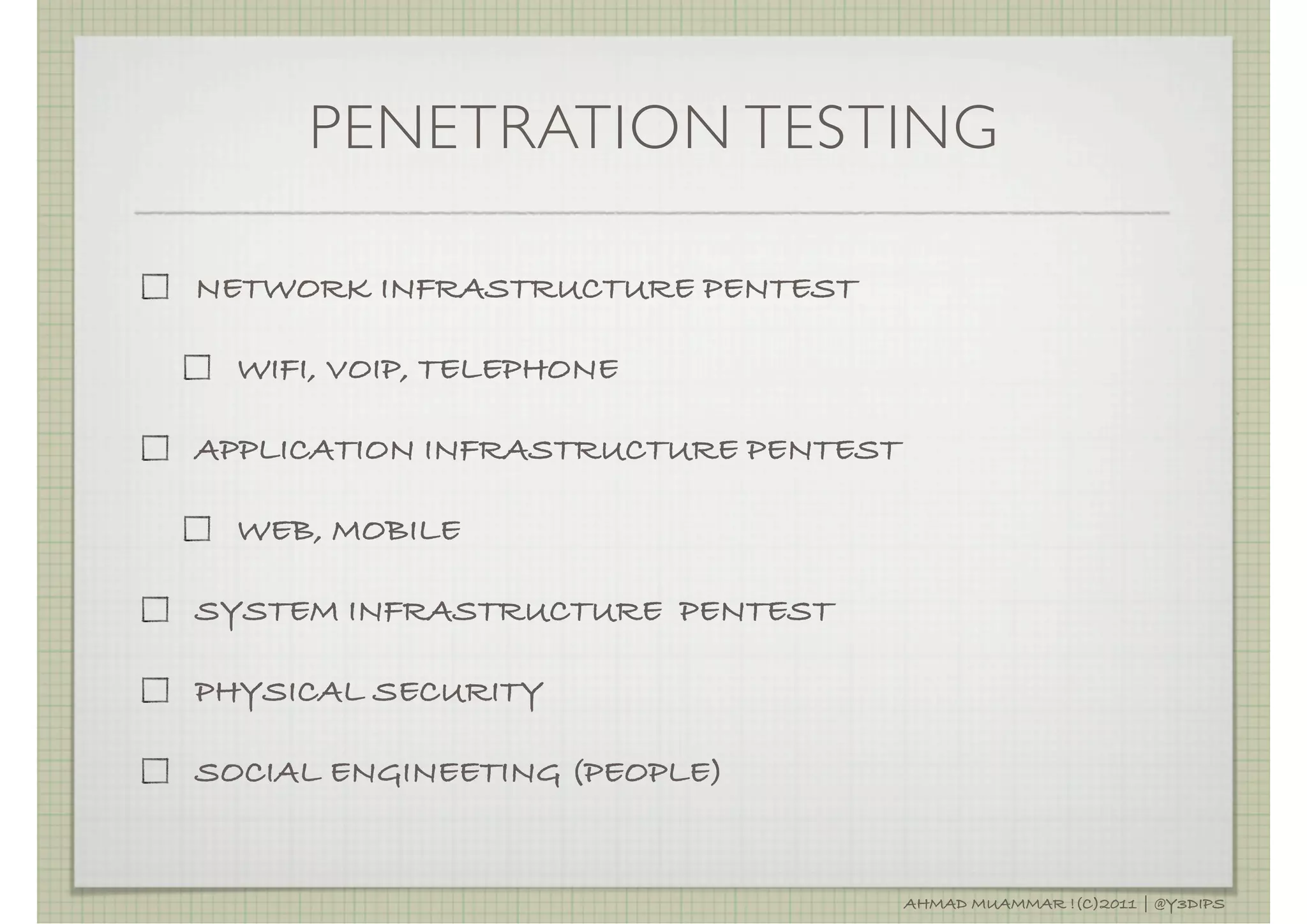
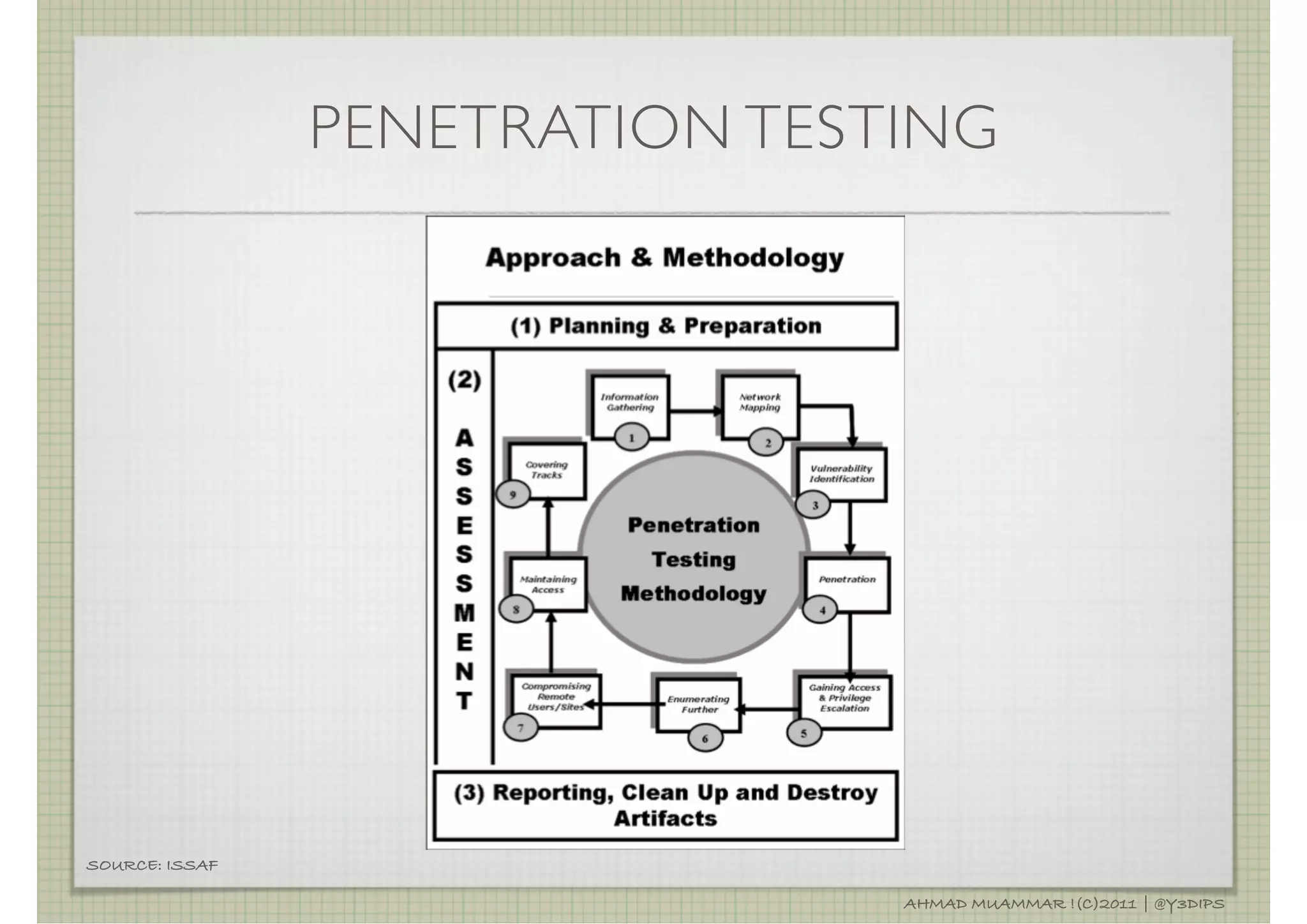
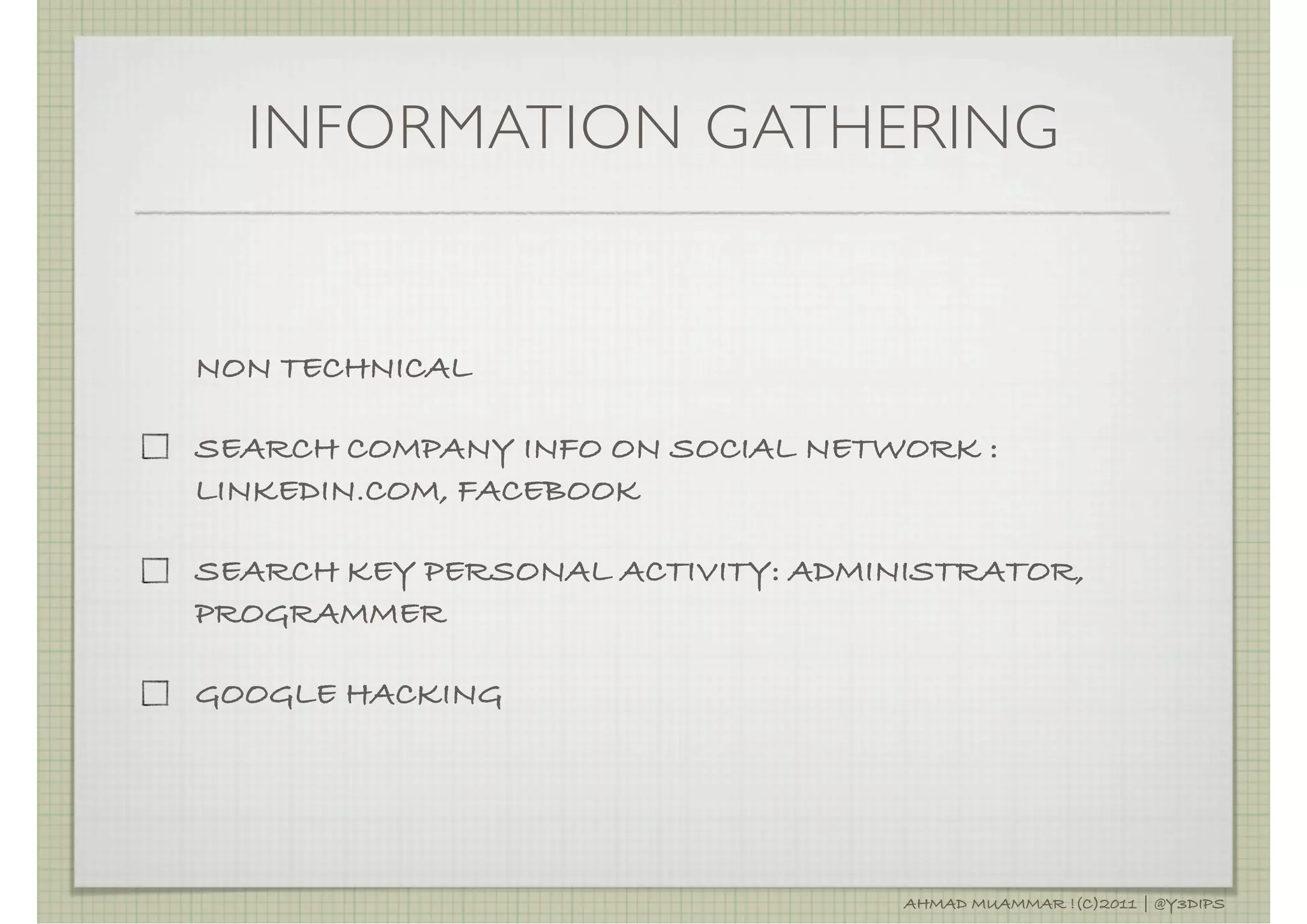
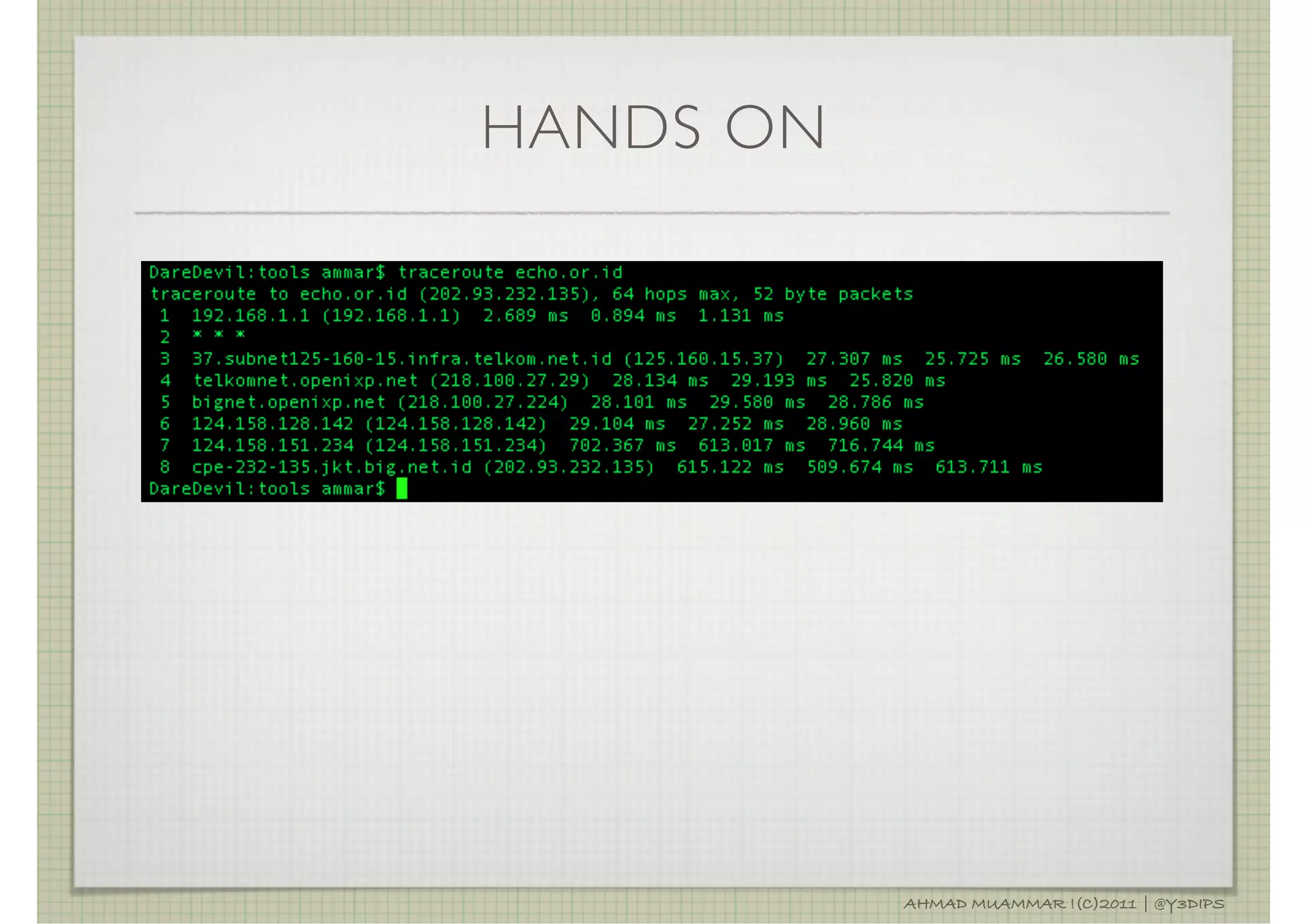
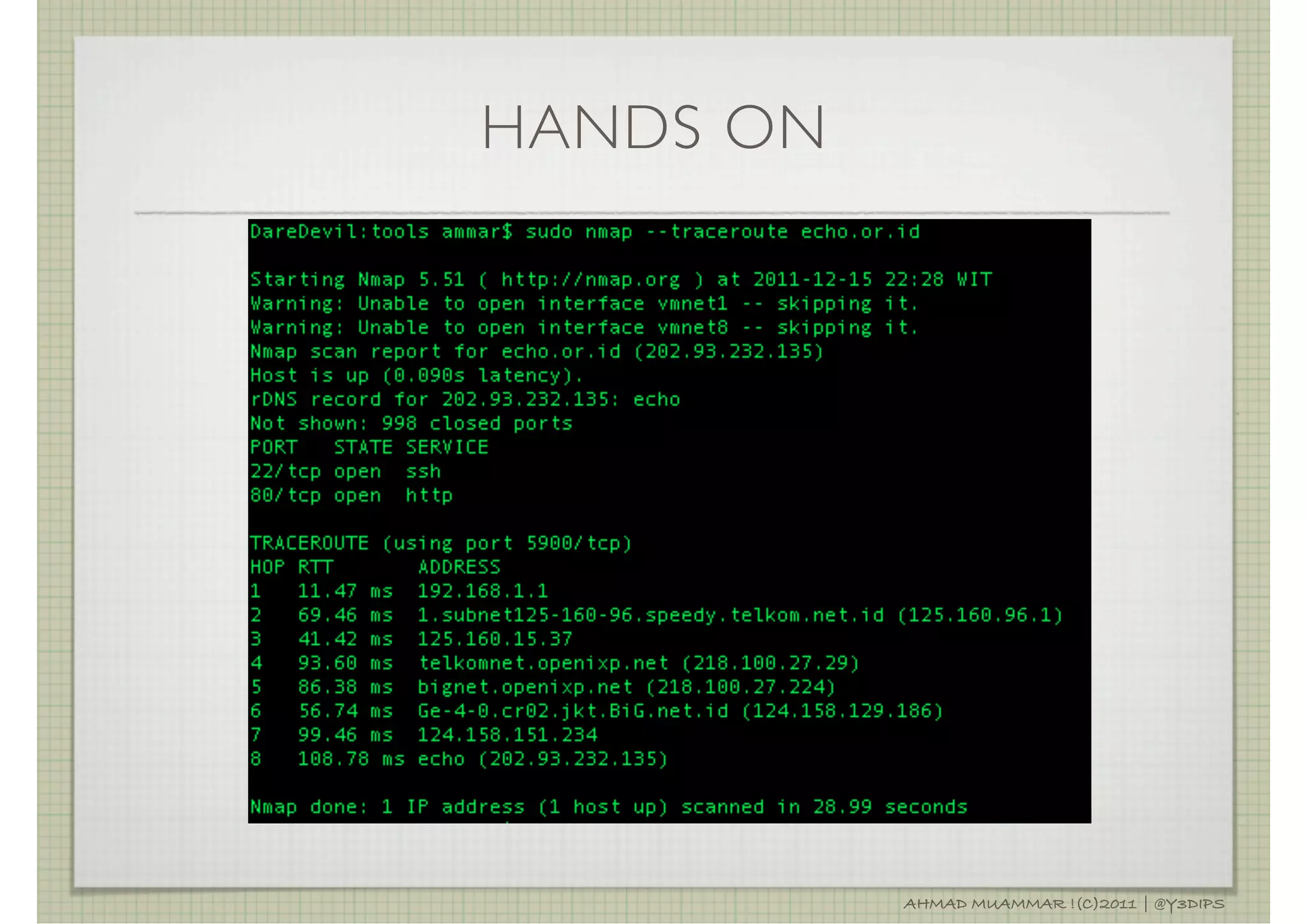
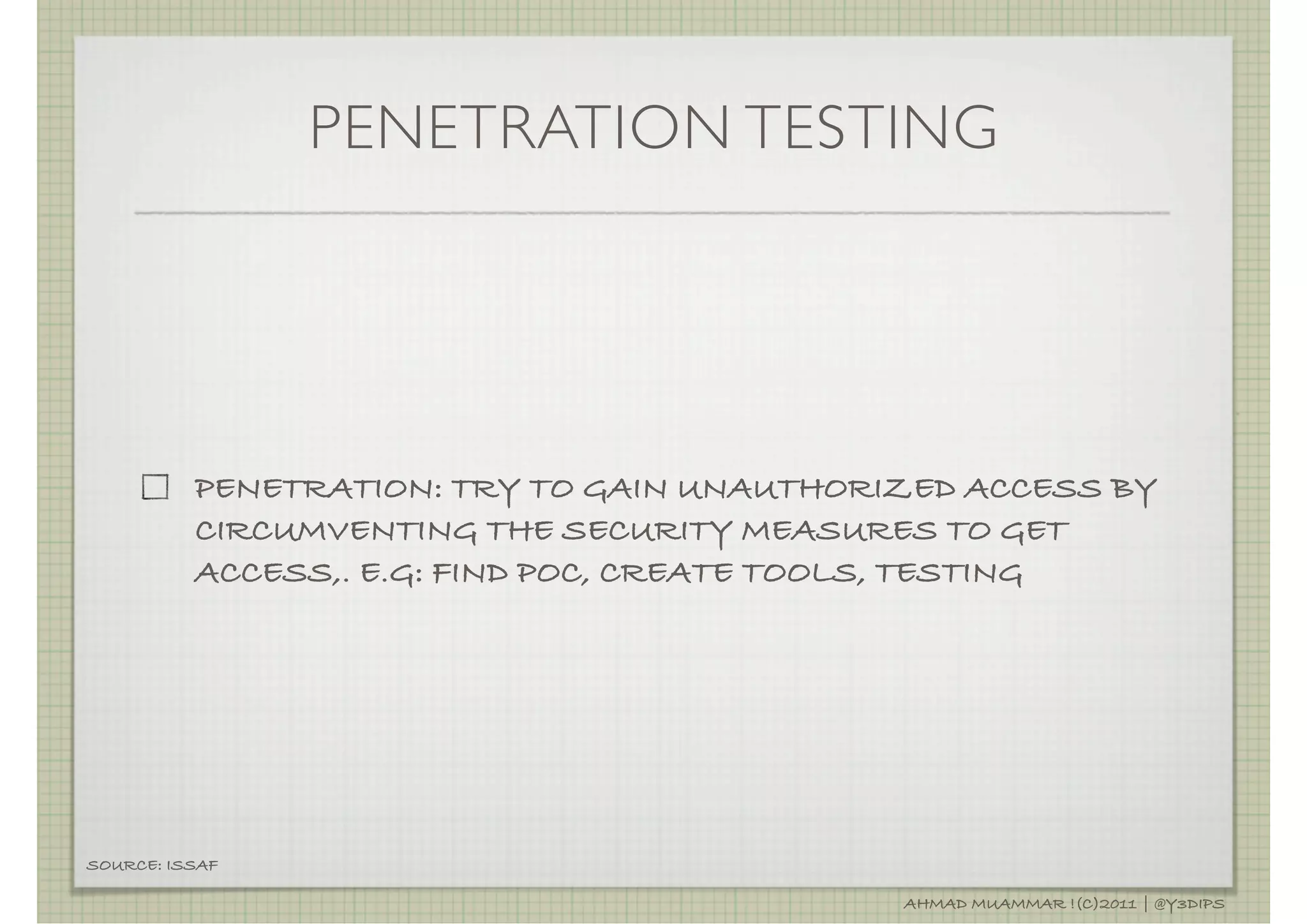
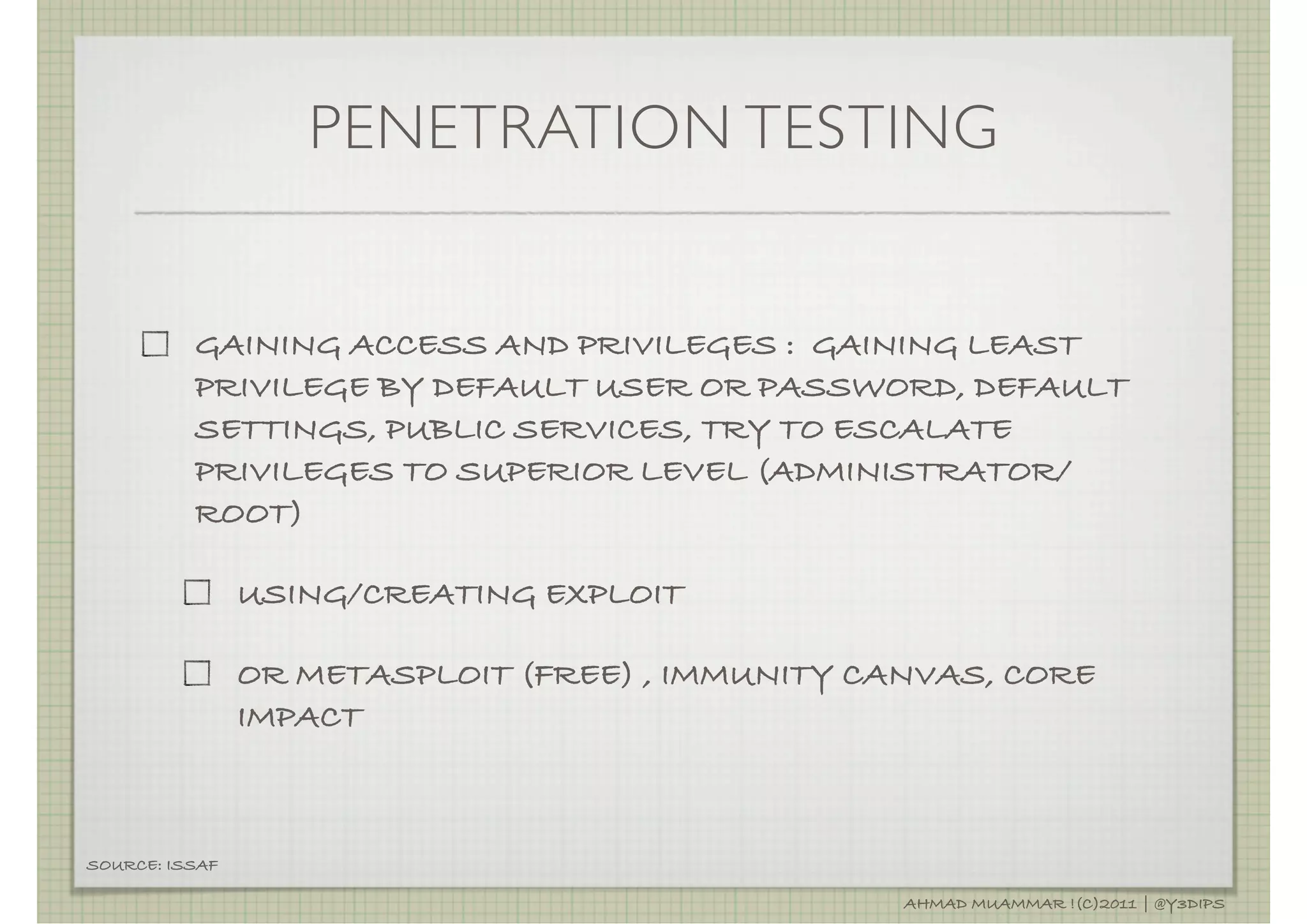
The document discusses penetration testing and related security concepts. It covers topics like vulnerability assessment, security audits, the differences between penetration testing and other assessments, common penetration testing methodologies, and the standard phases of information gathering, network mapping, vulnerability identification, exploitation, privilege escalation, maintaining access and covering tracks.