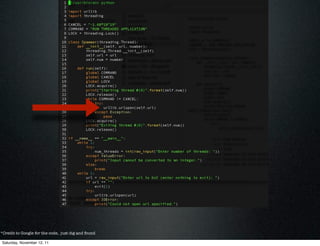
This document discusses layer 7 denial of service attacks and mitigation techniques. It describes how layer 7 attacks target application layer protocols like HTTP and FTP to overwhelm servers. The document then provides an example of an HTTP flood attack against a website and the steps taken to analyze logs and implement mitigation like rate limiting, timeouts, and firewall rules. Effective mitigation requires identifying attacks, hardening servers, and contacting authorities.