Embed presentation
Downloaded 52 times


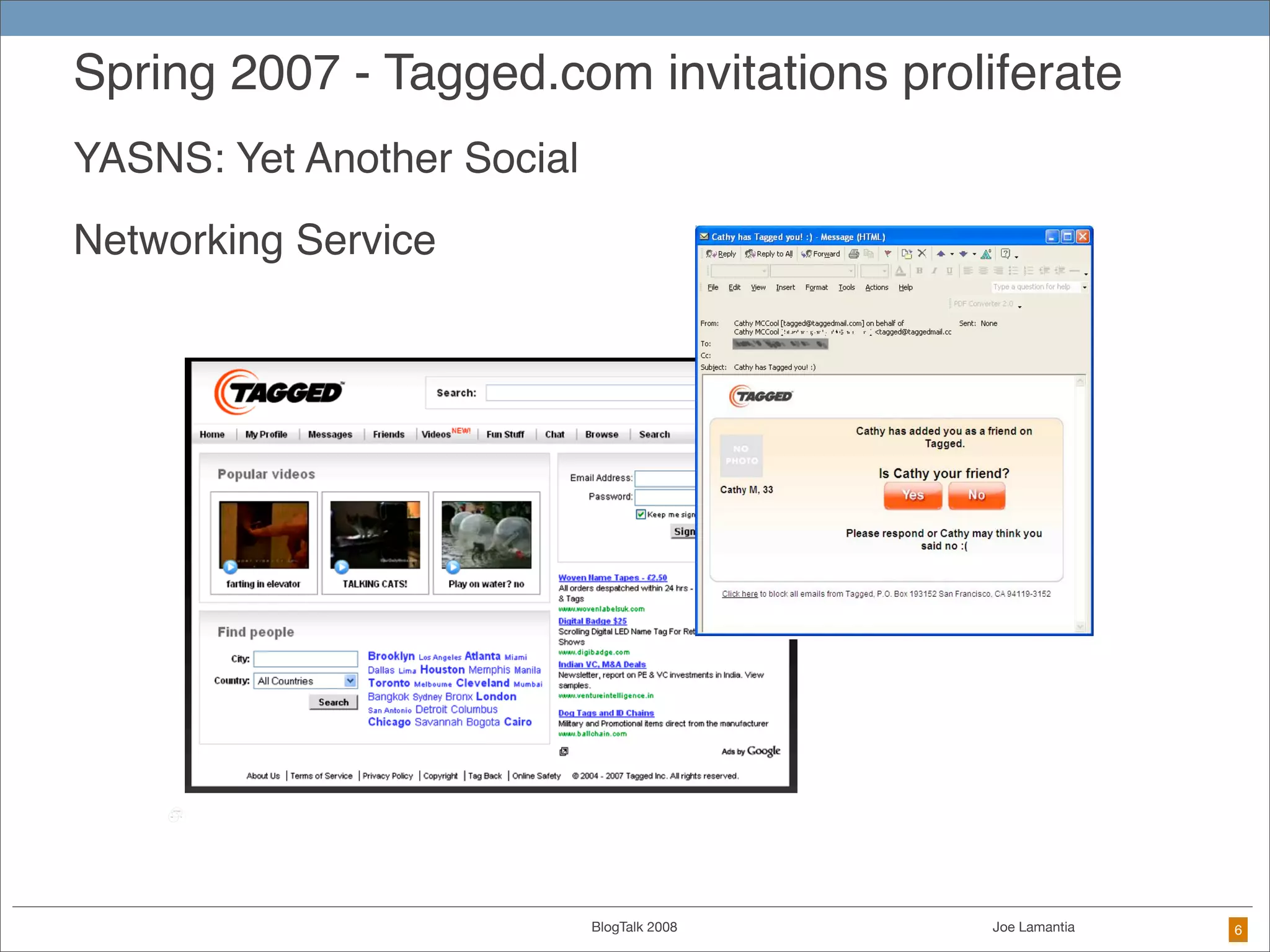
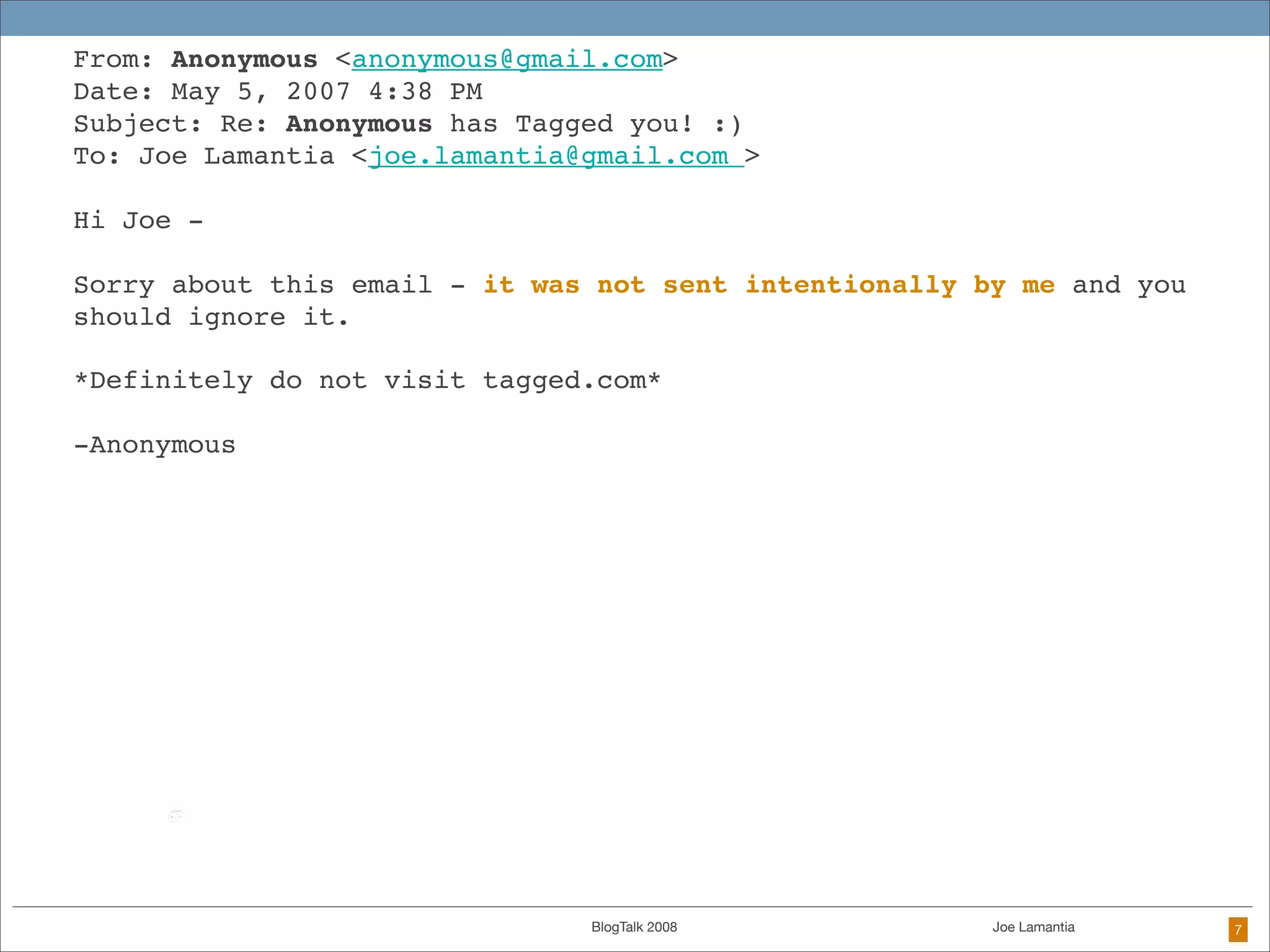
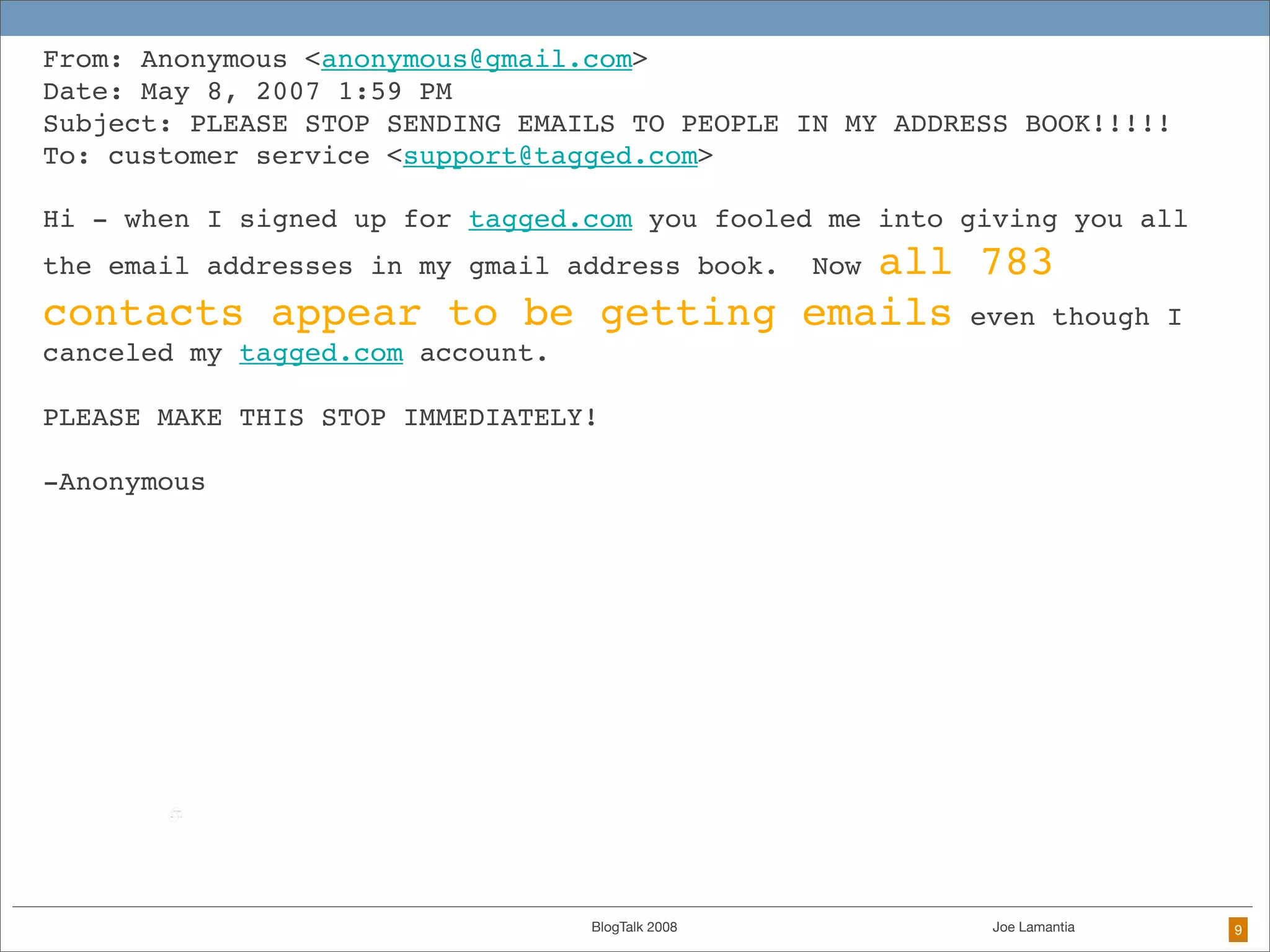
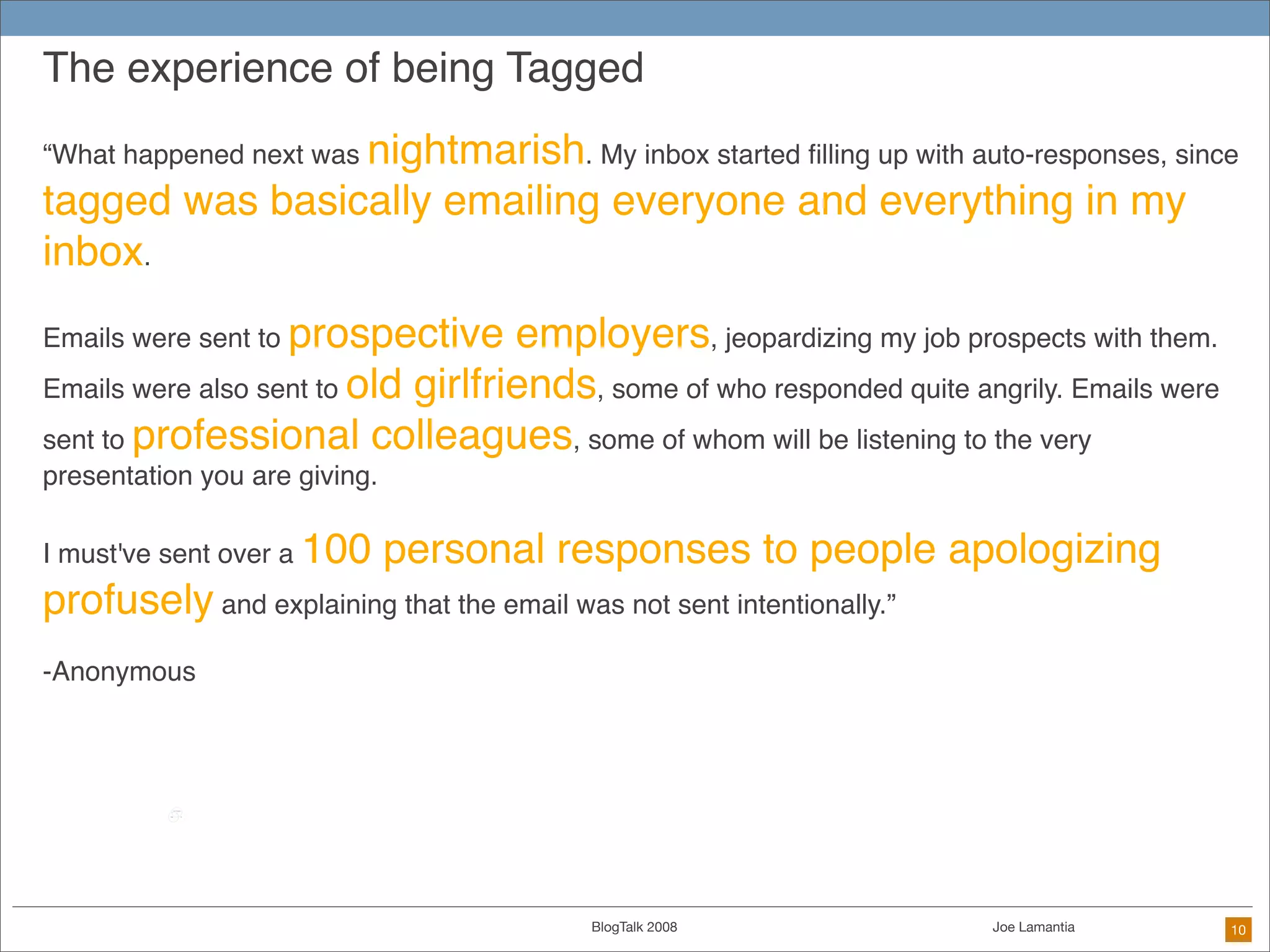
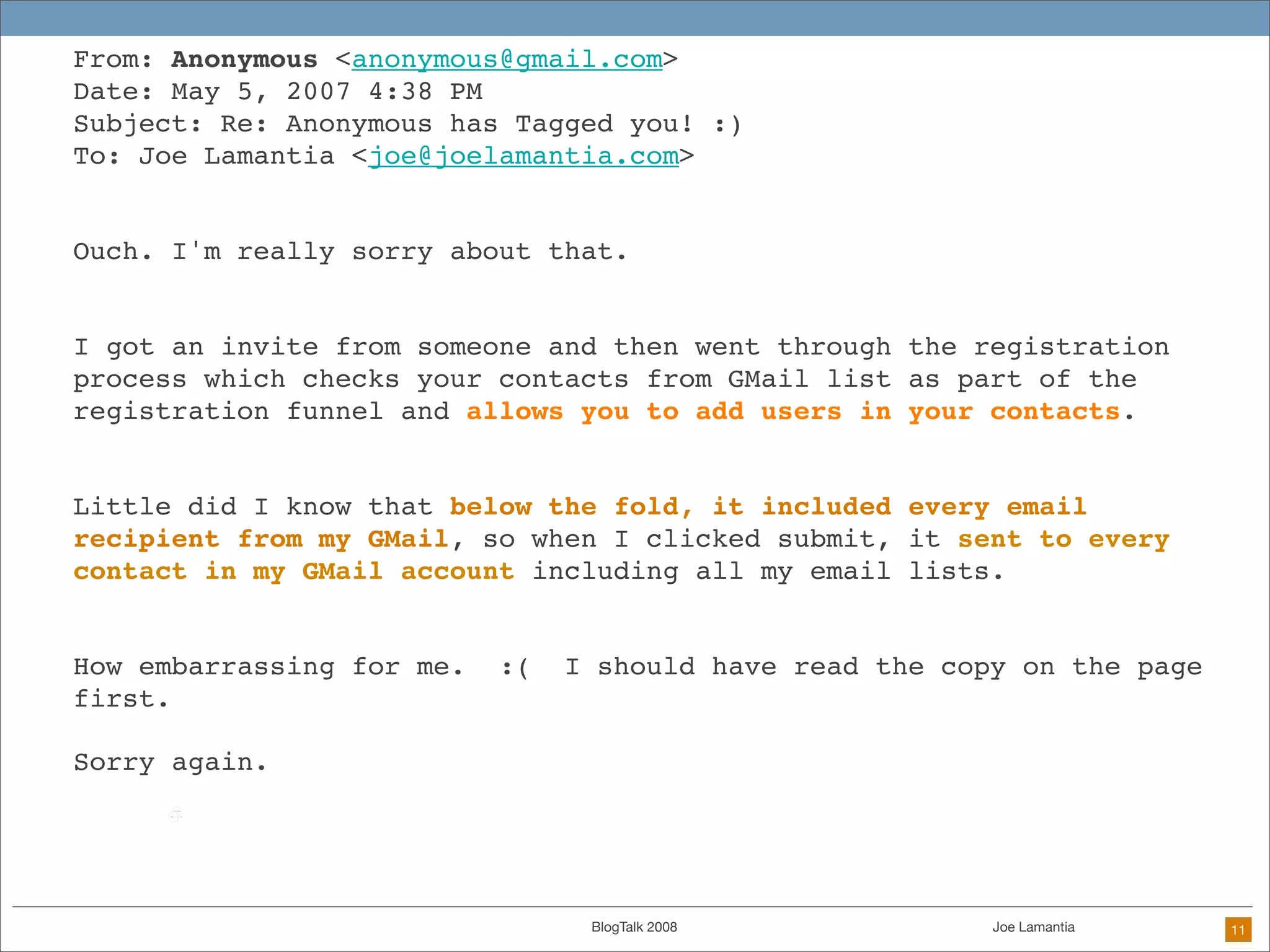

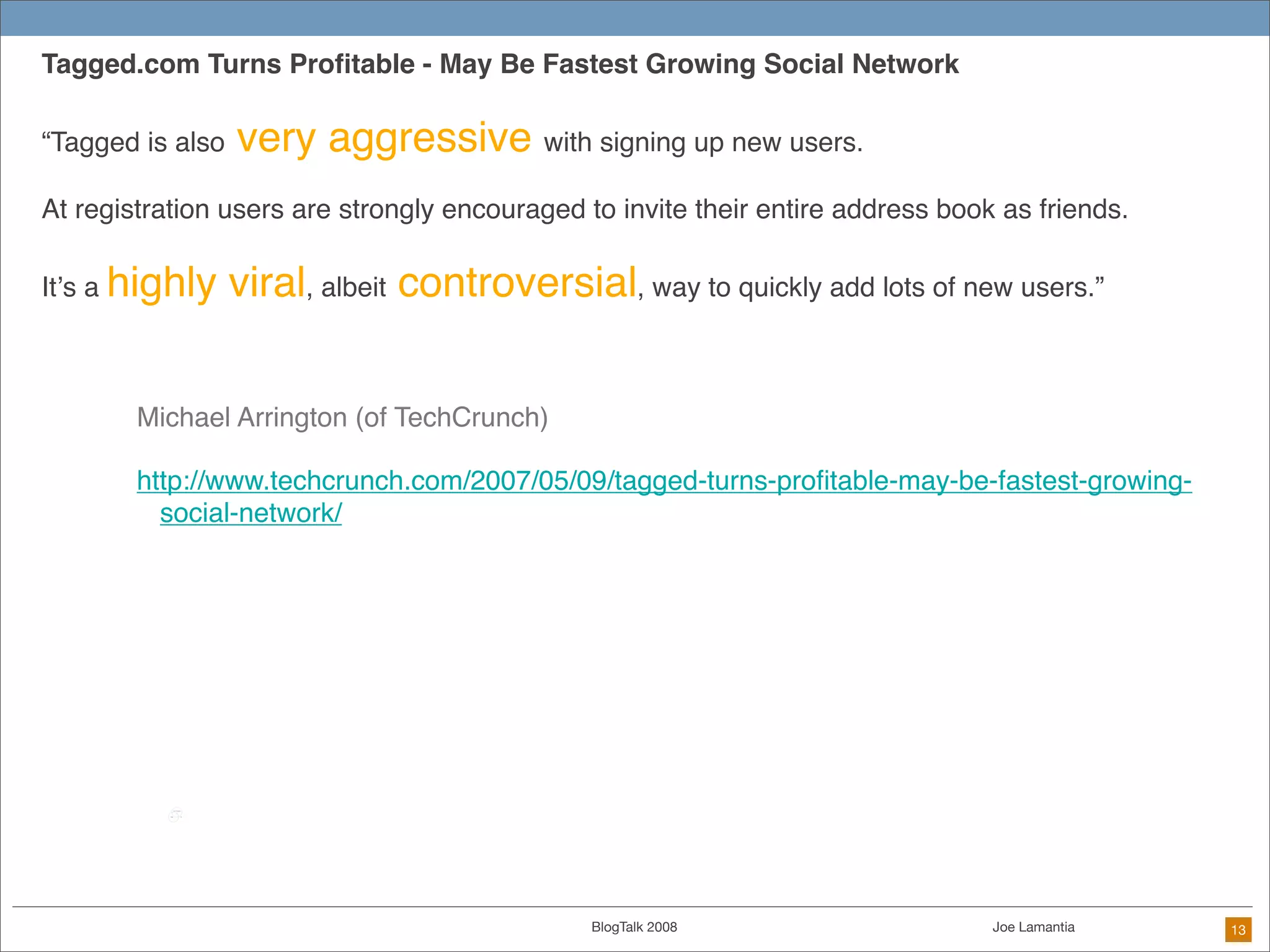
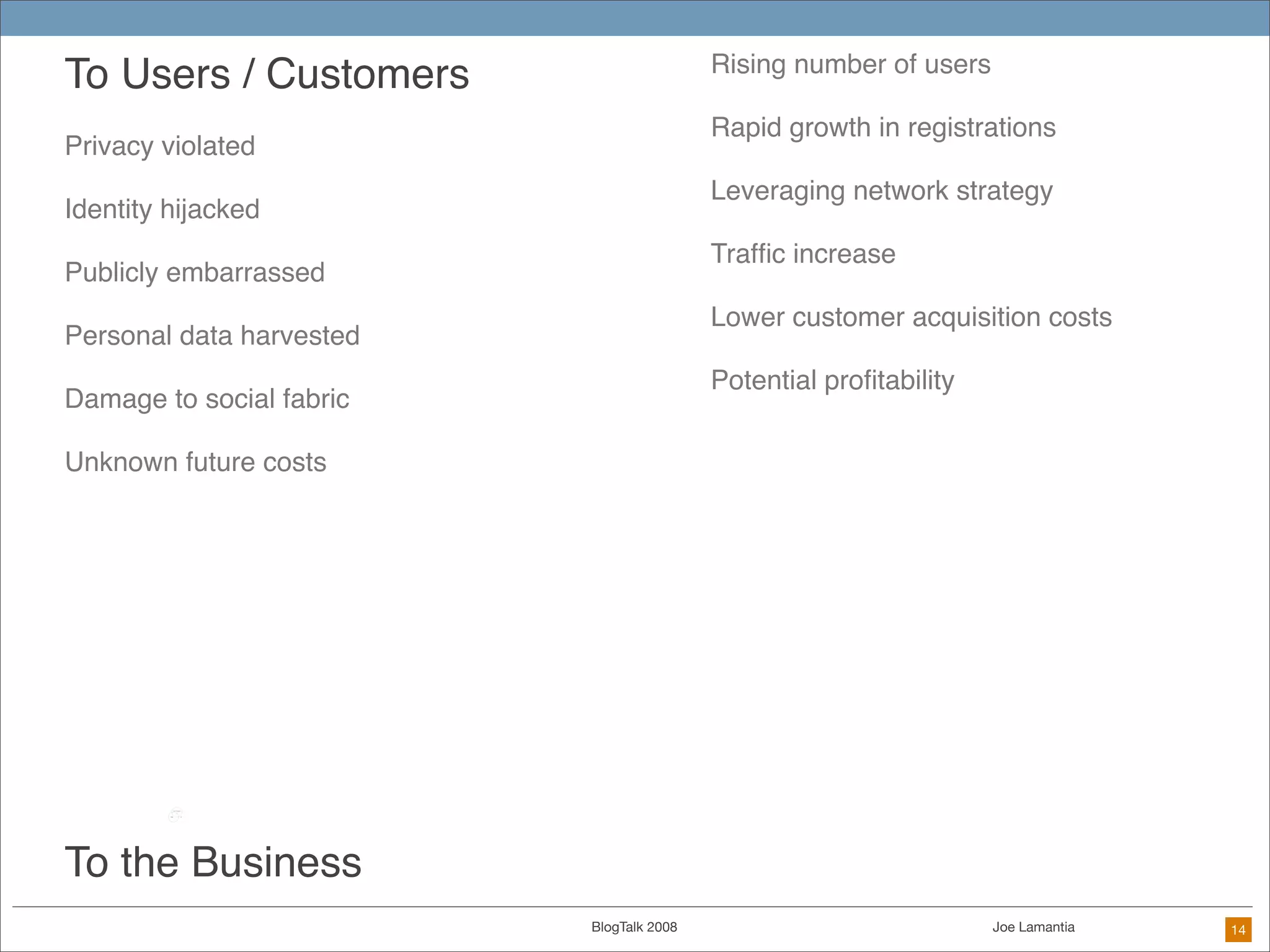

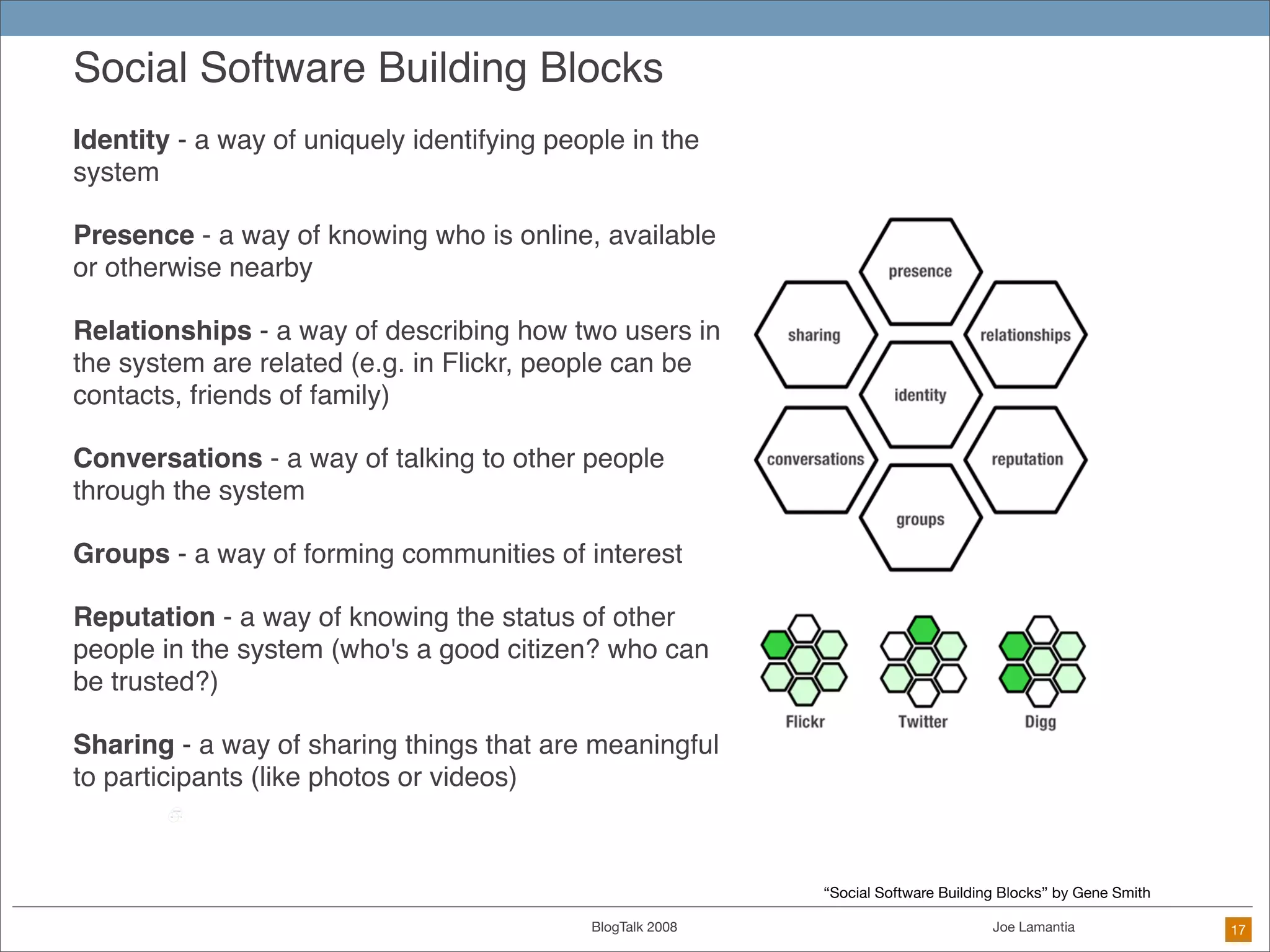
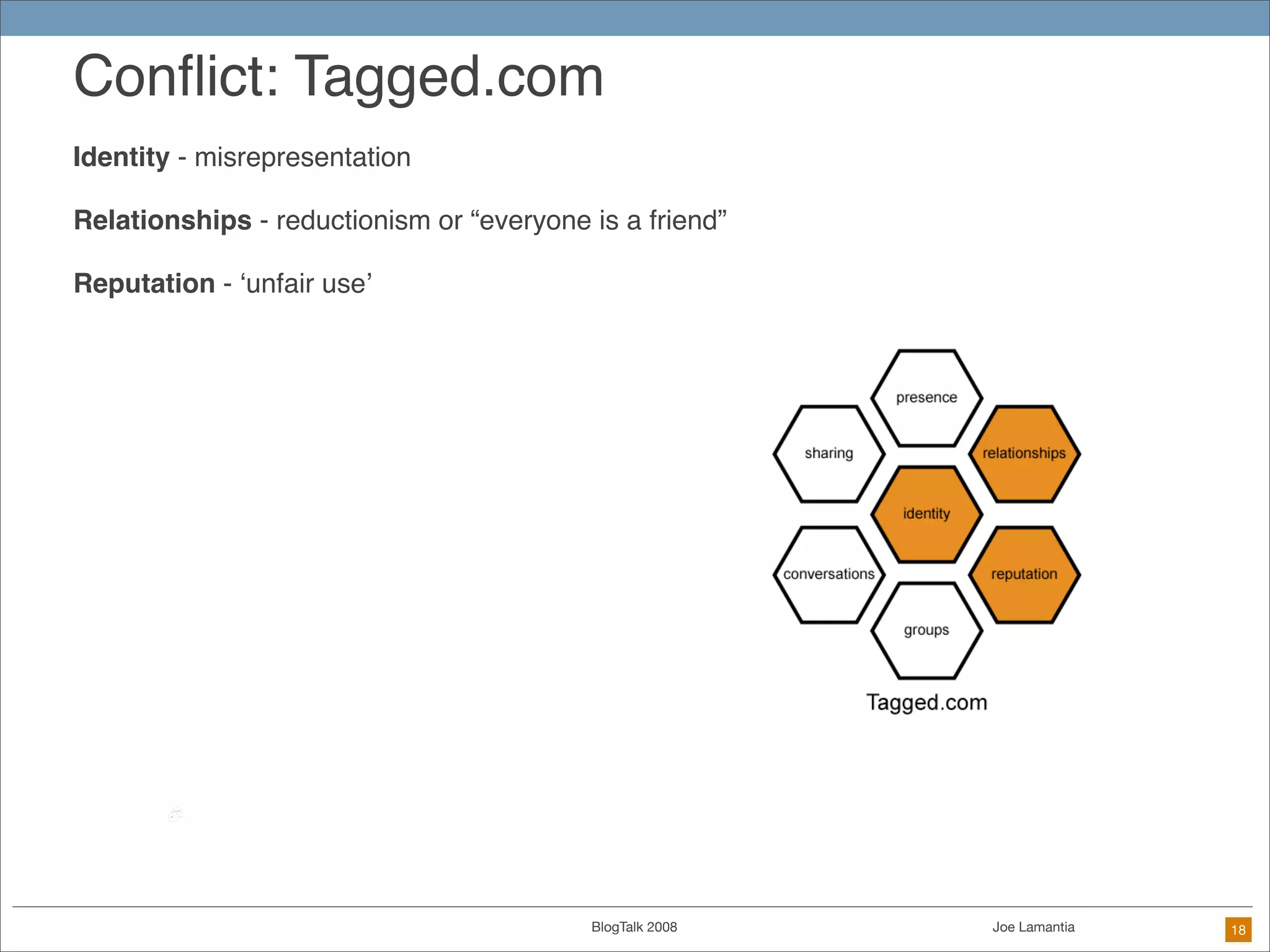

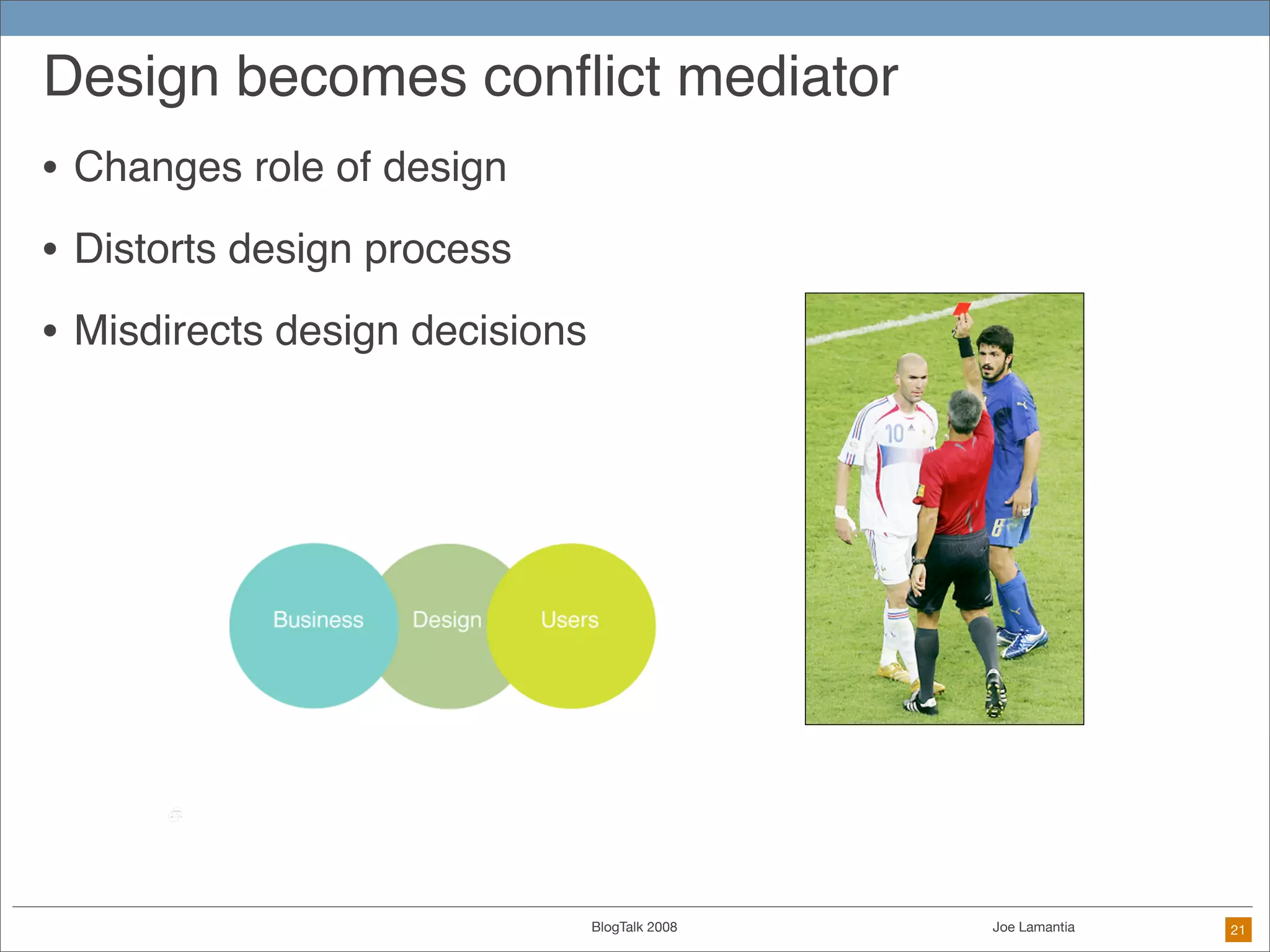


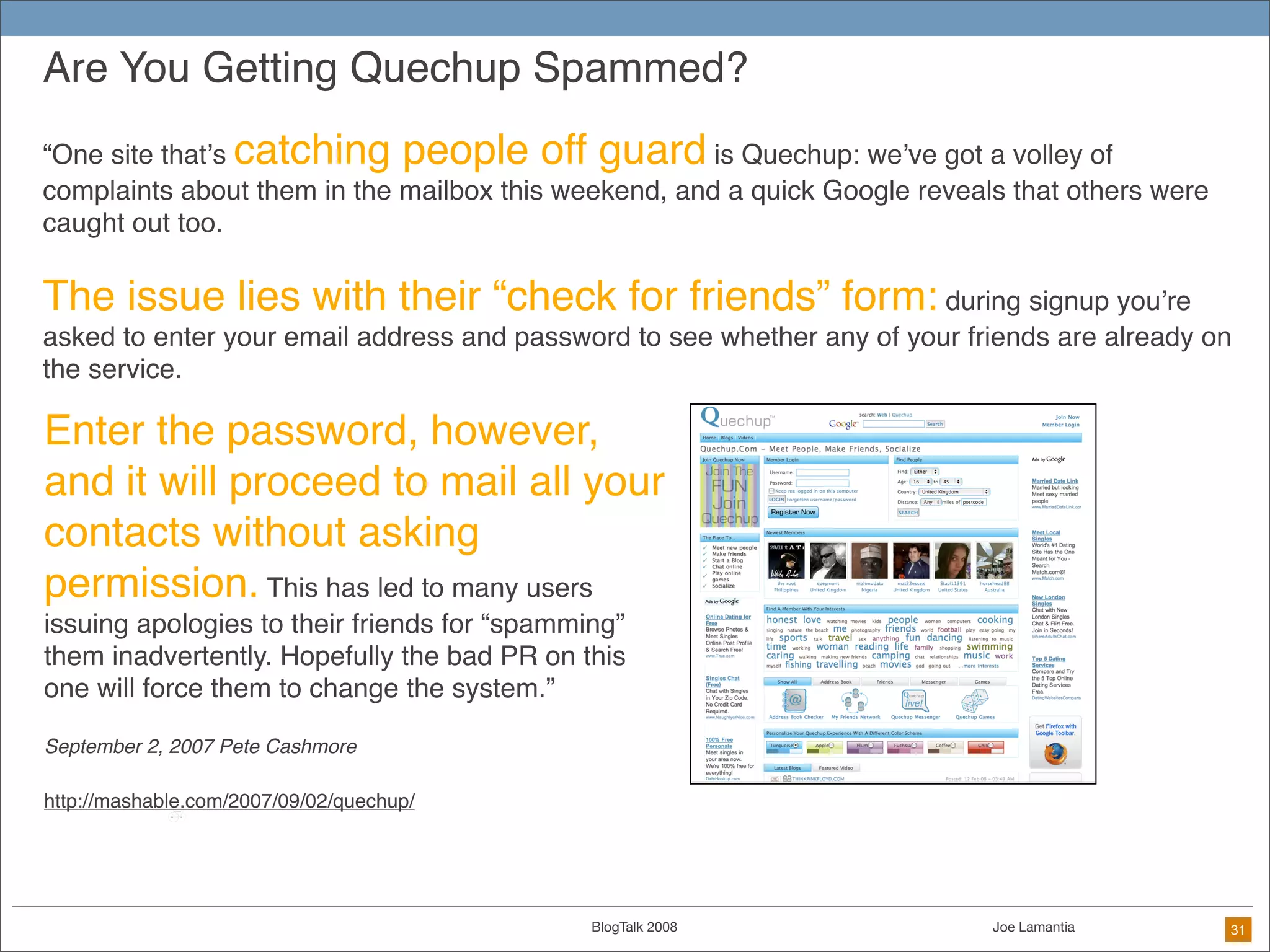
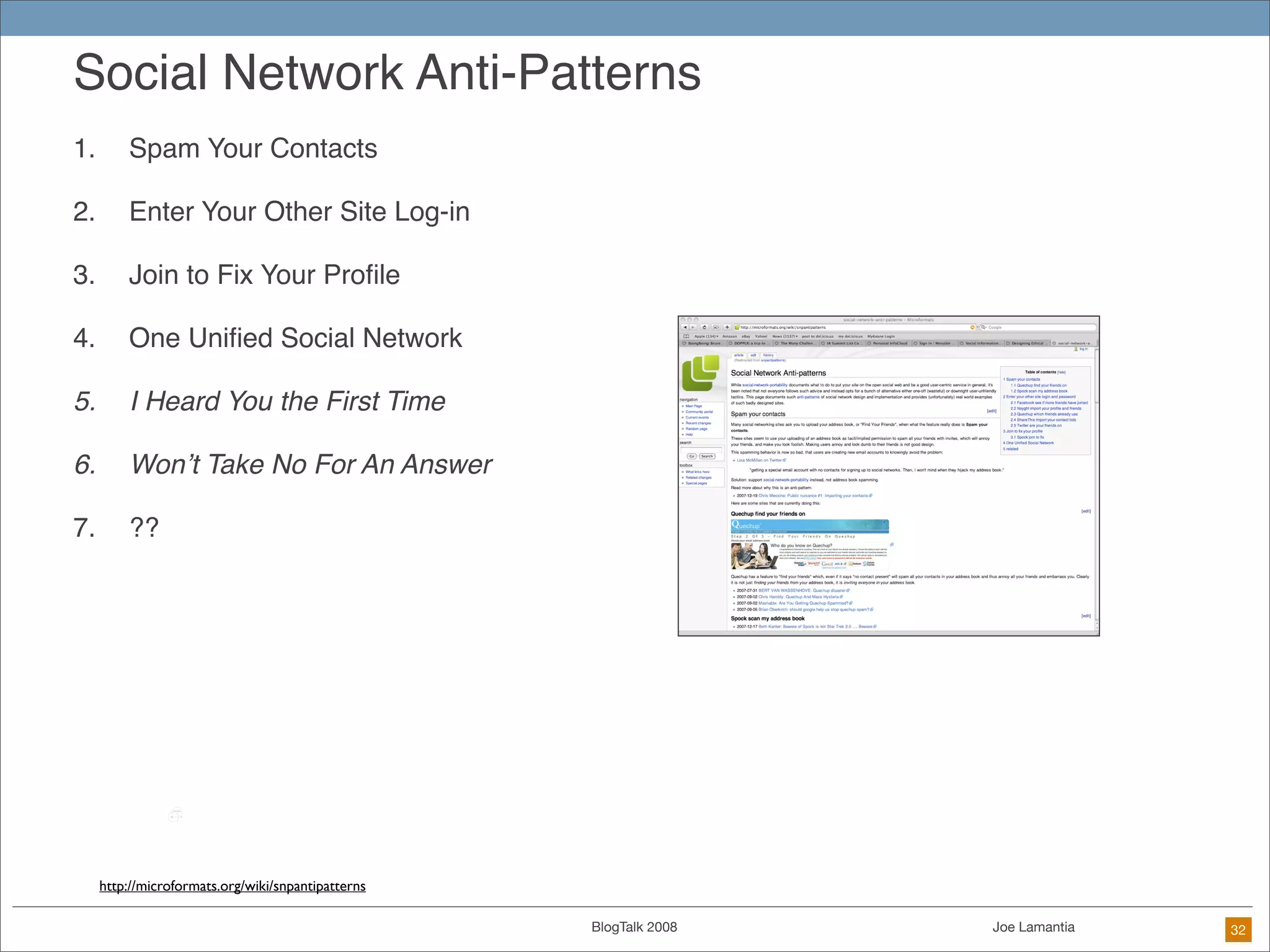
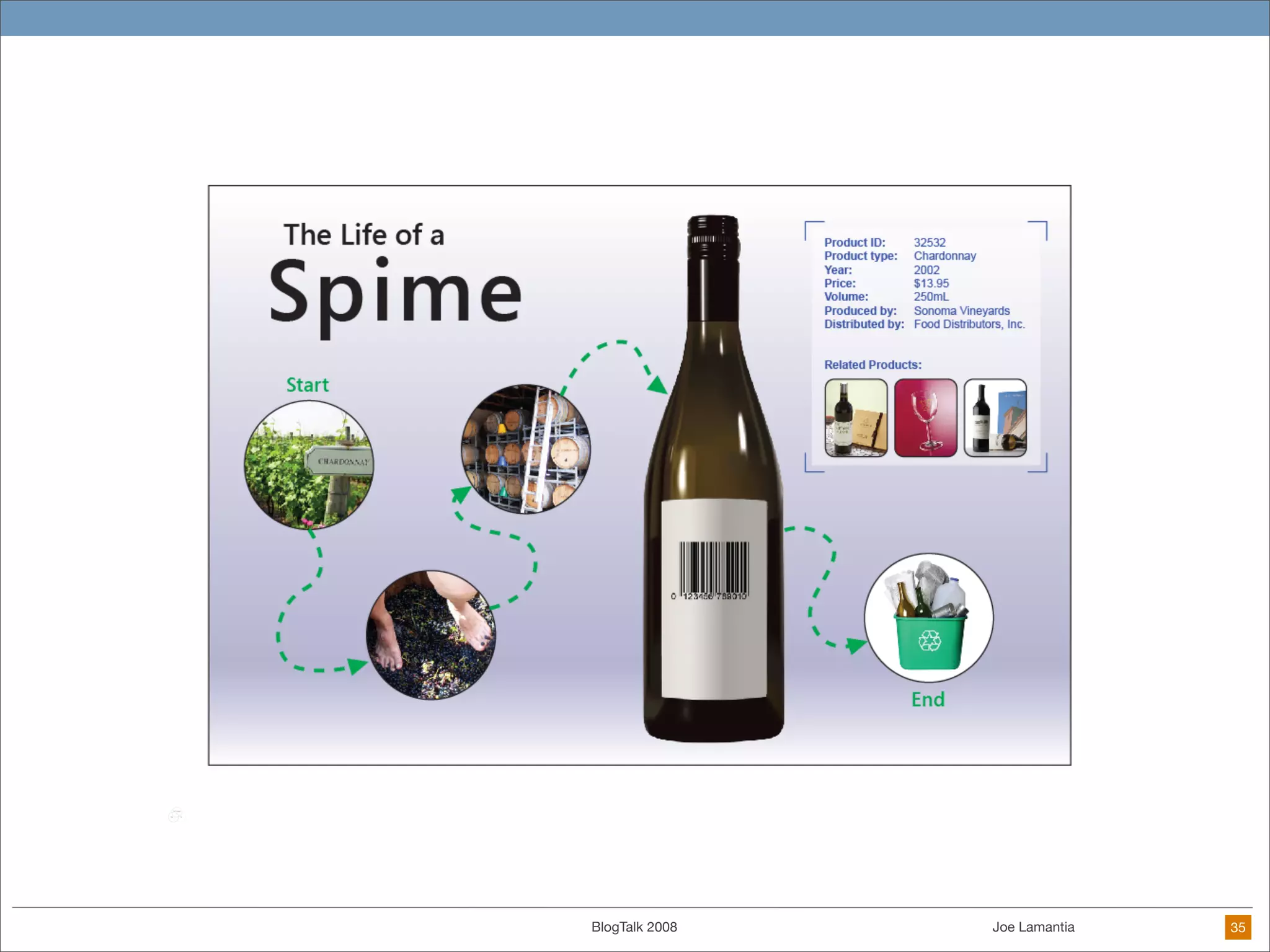
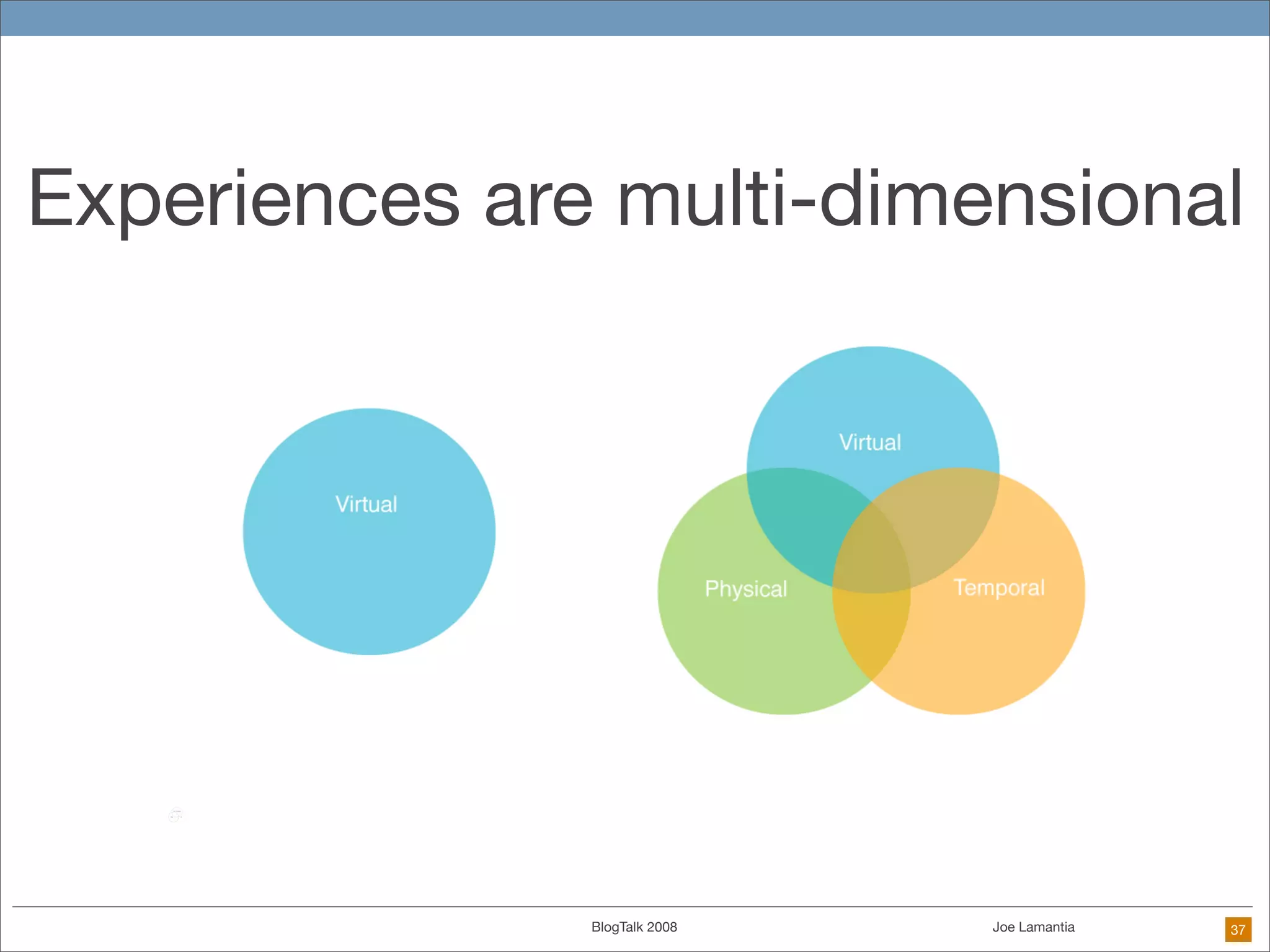
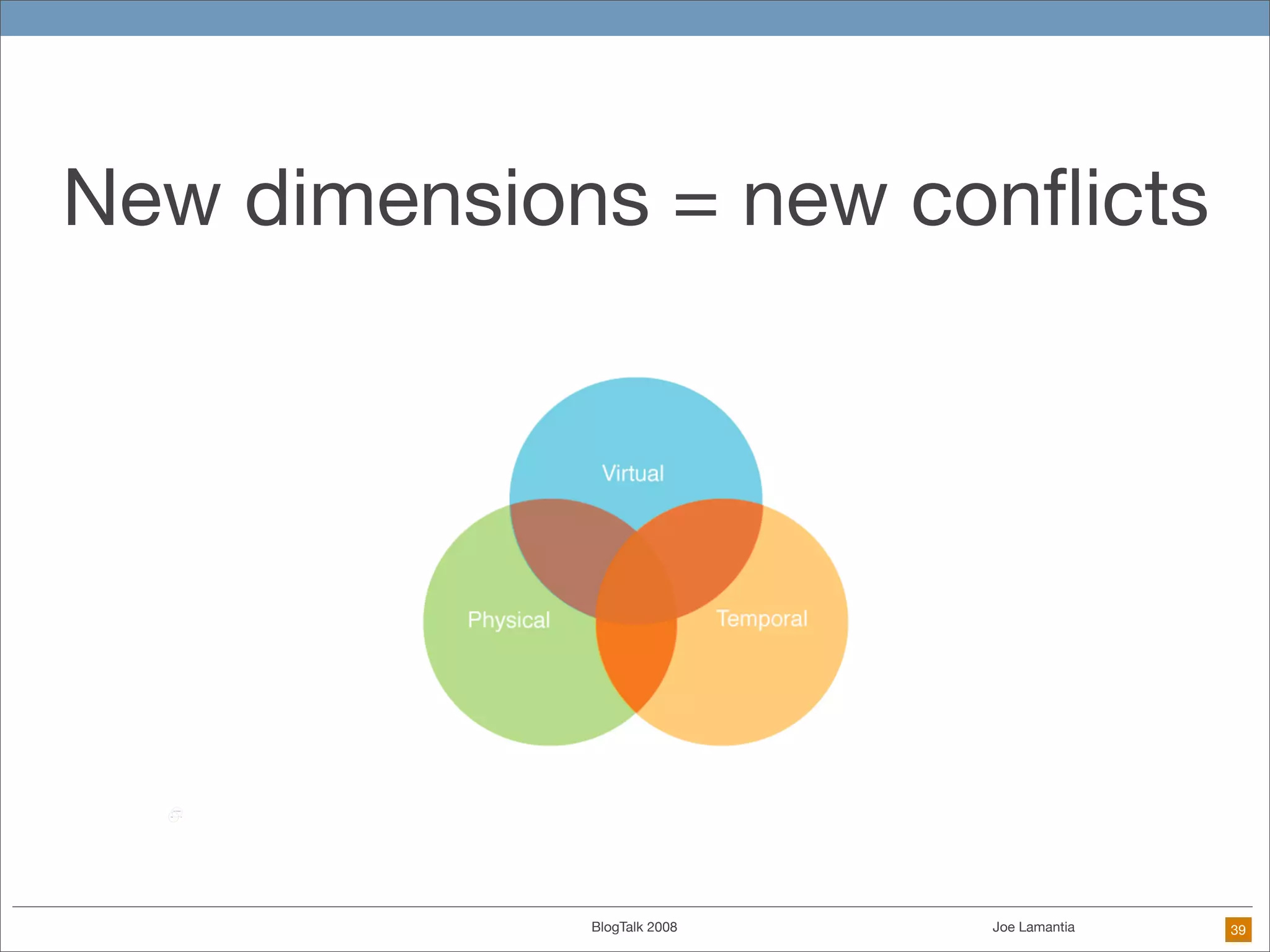

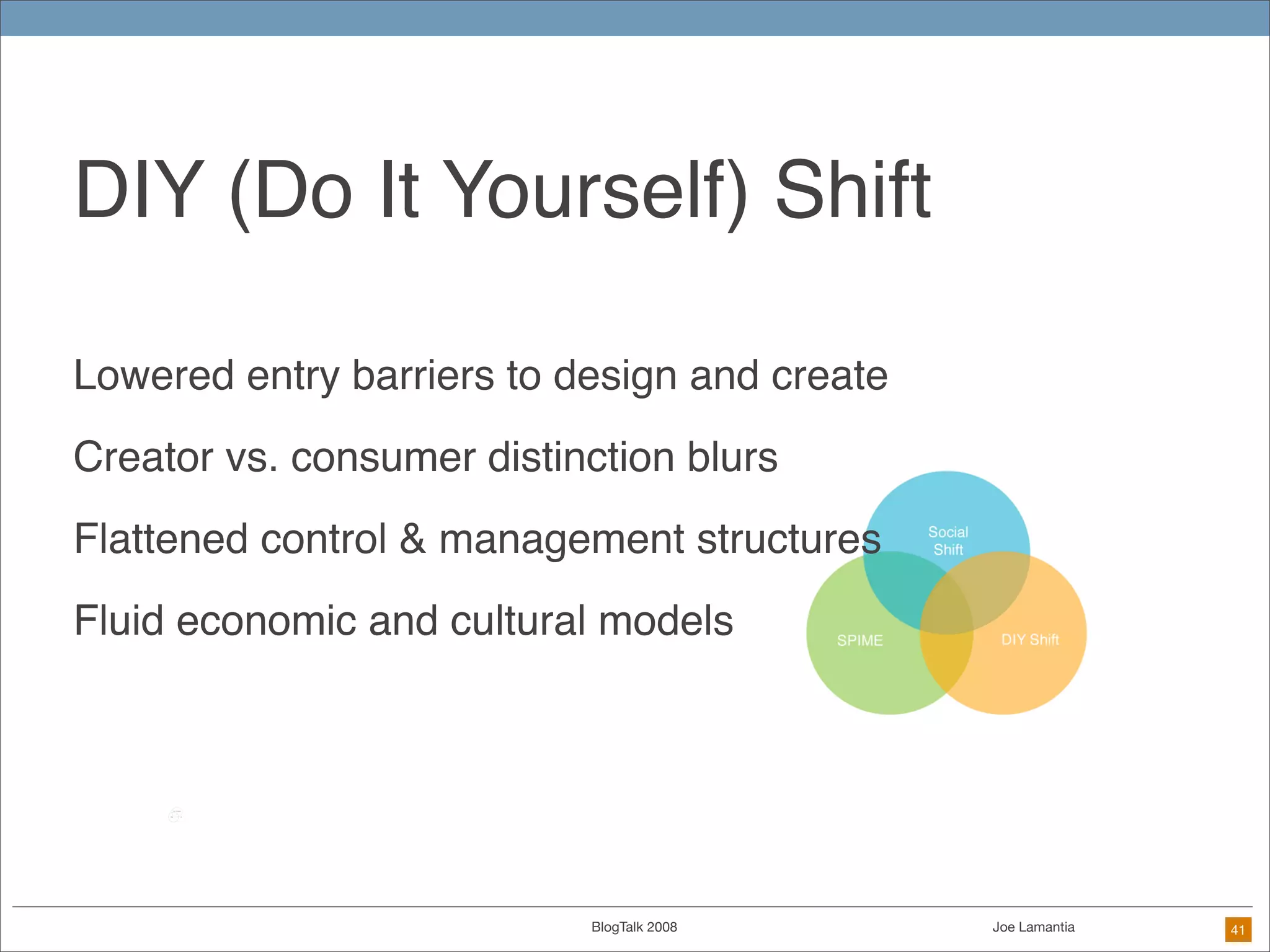

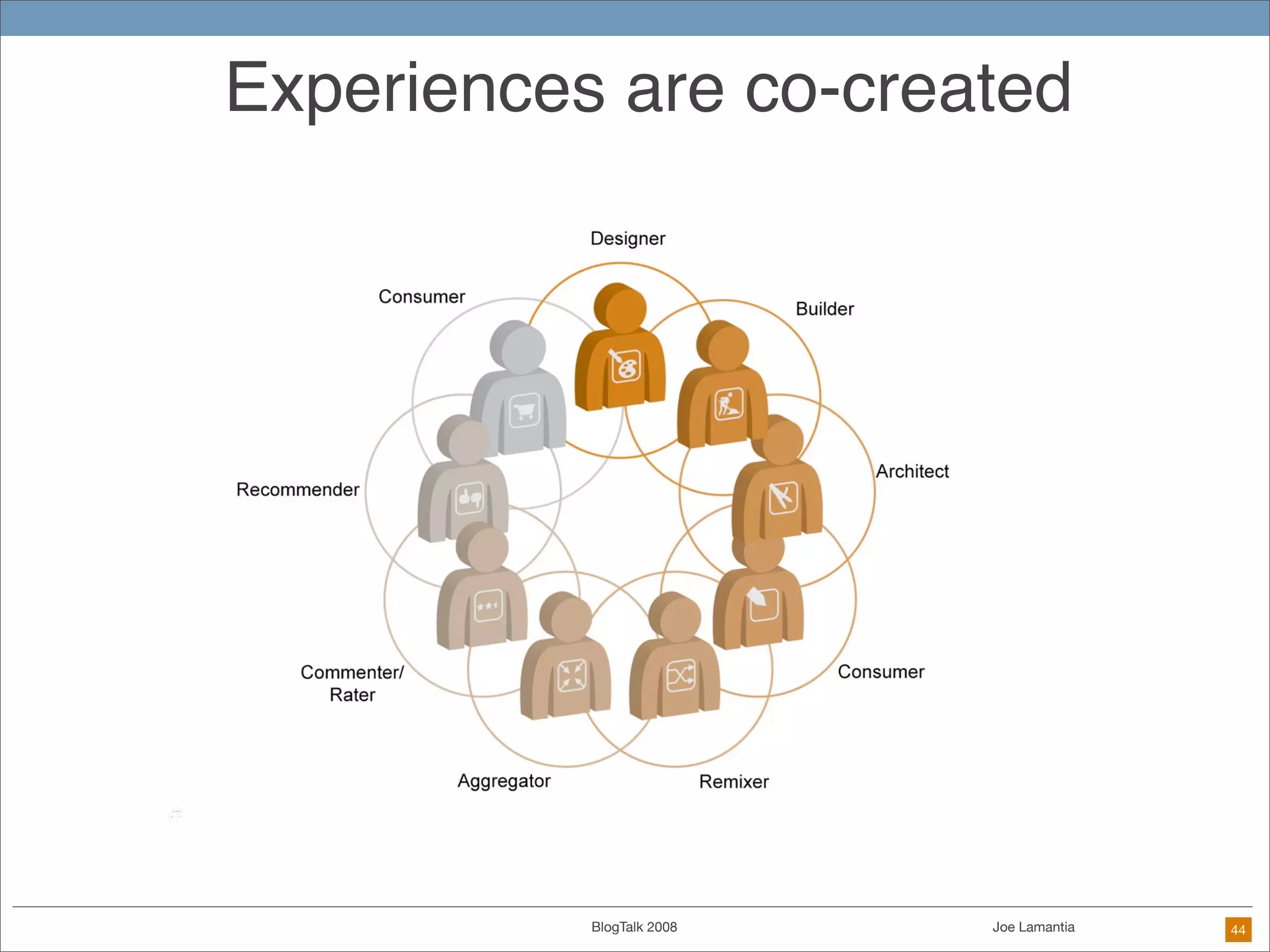
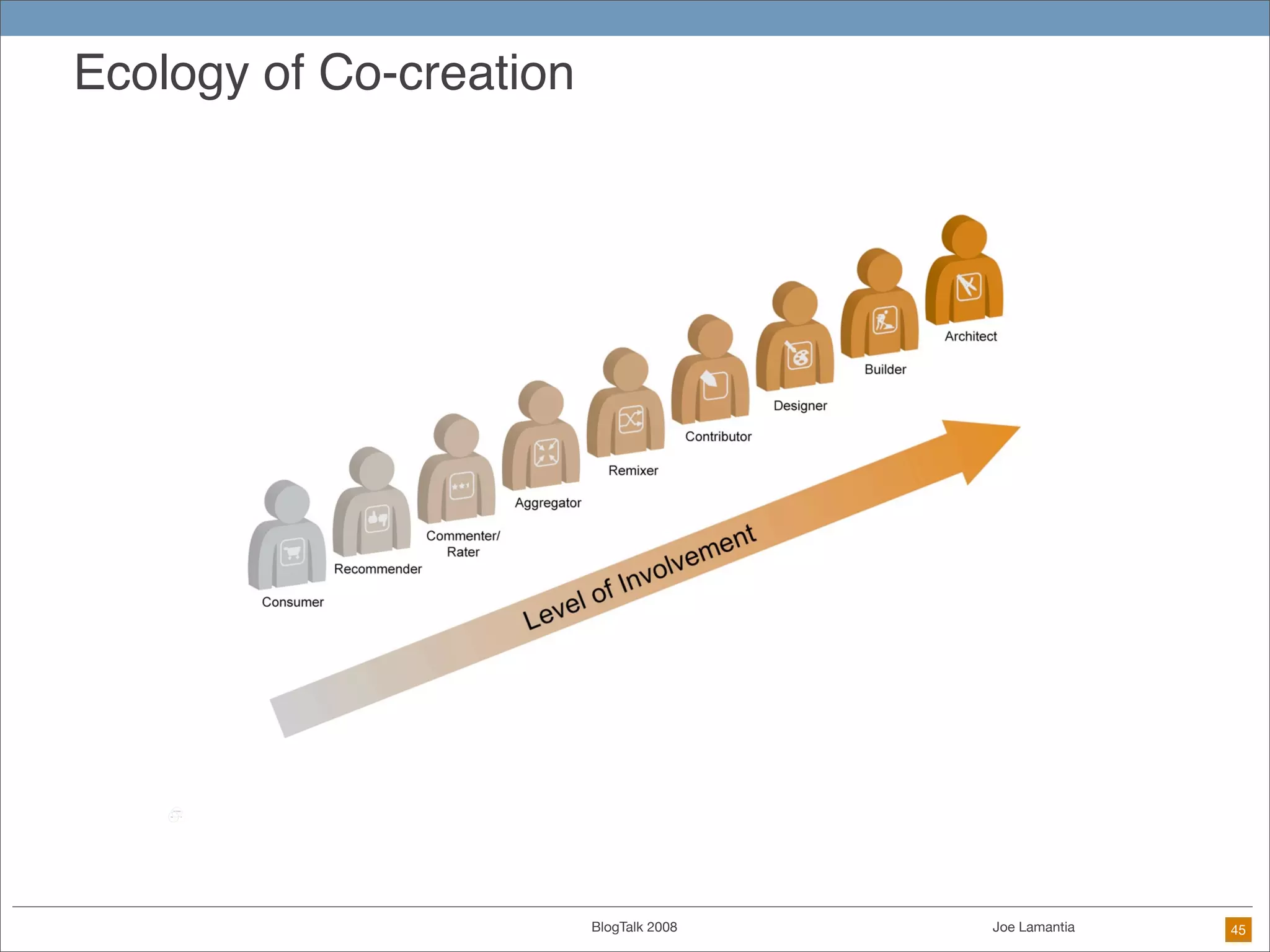
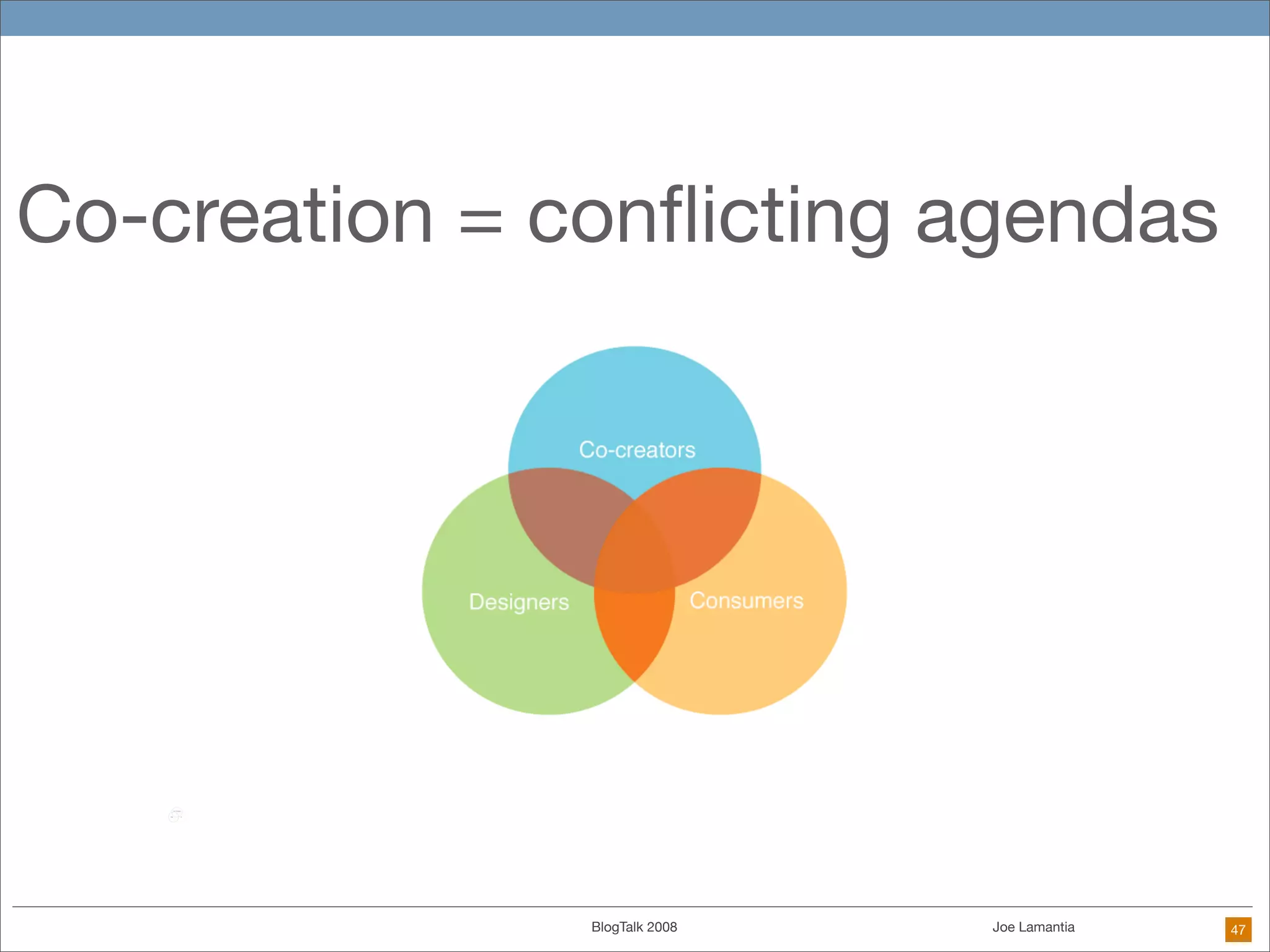


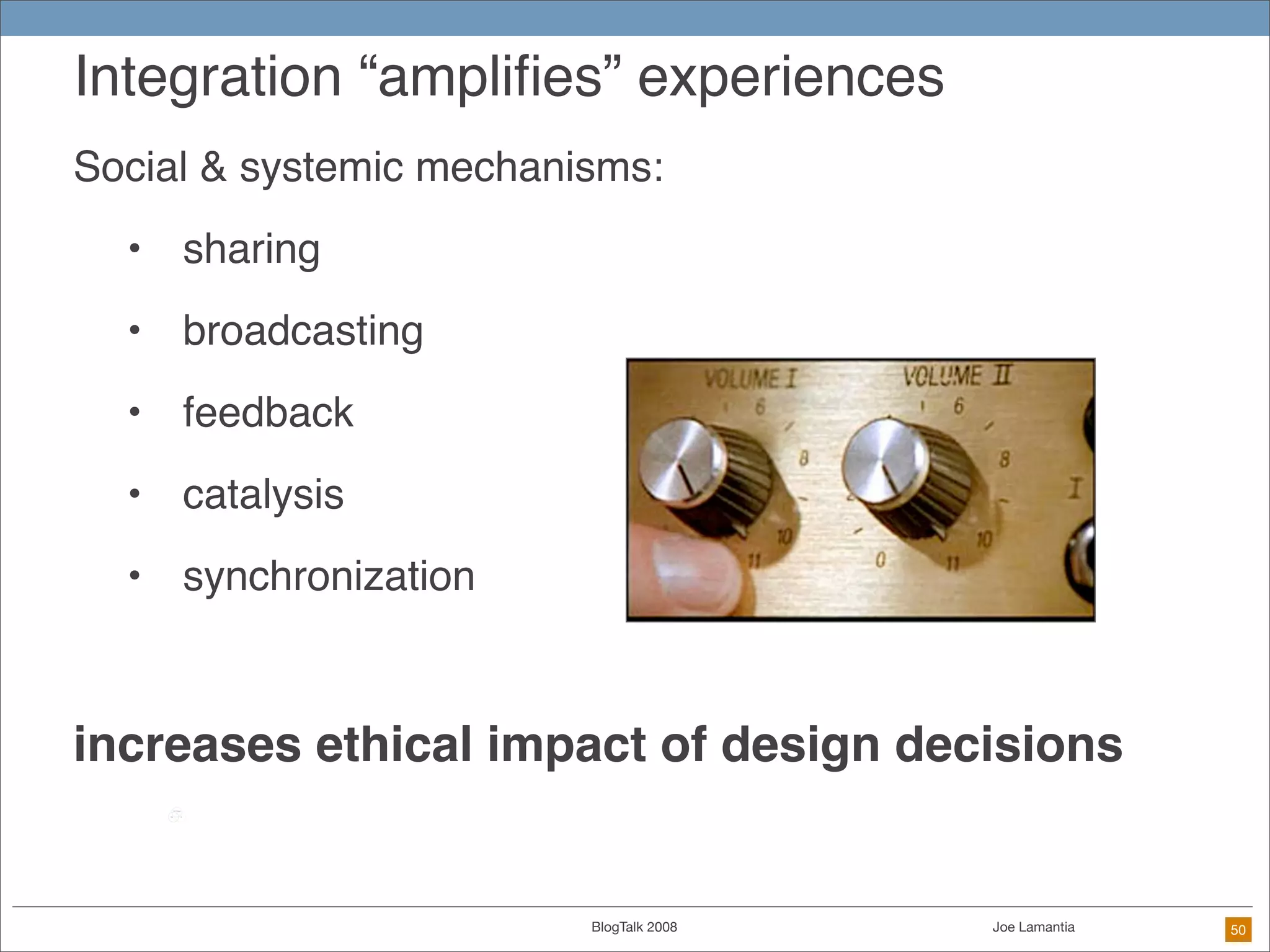
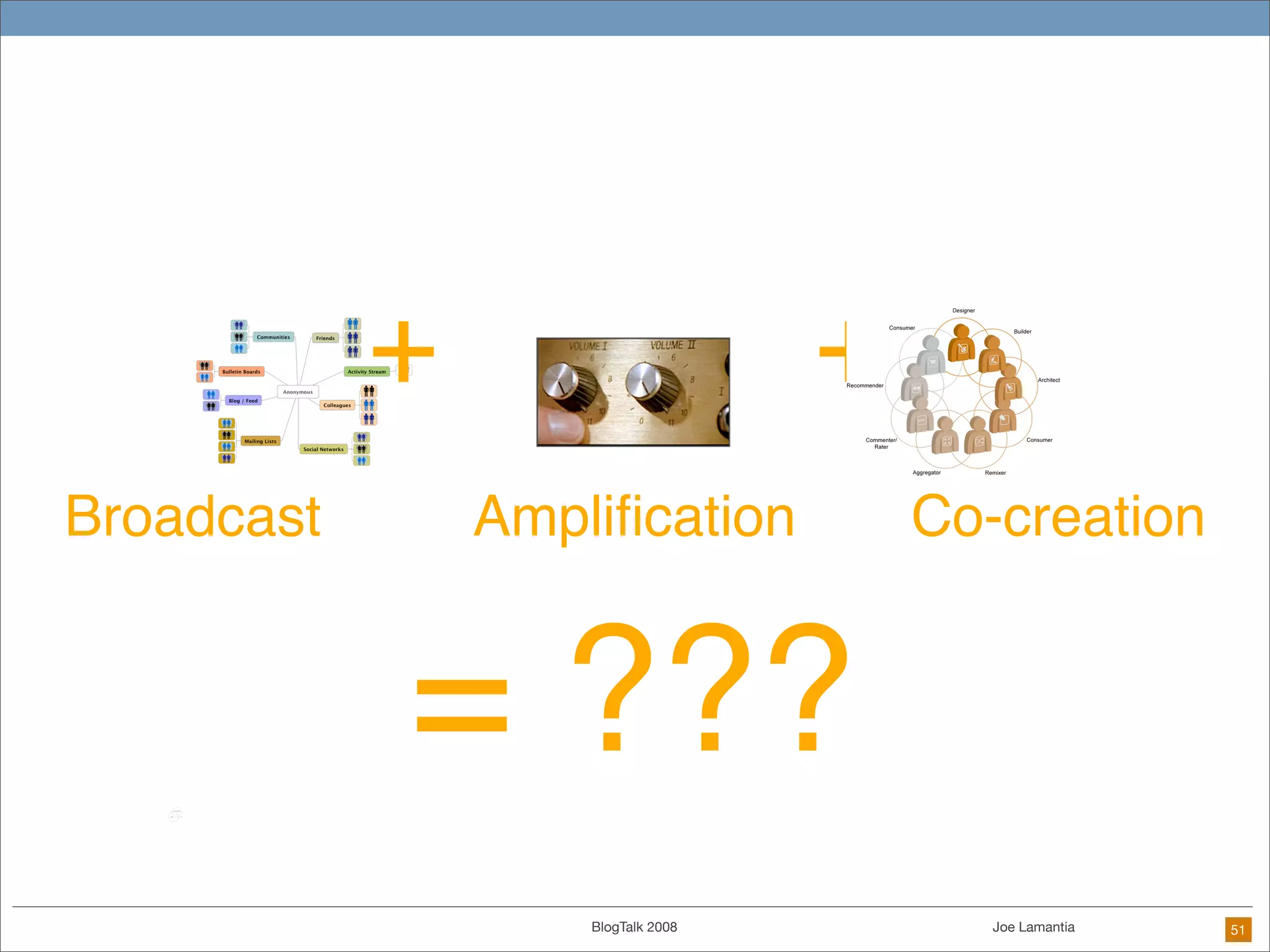
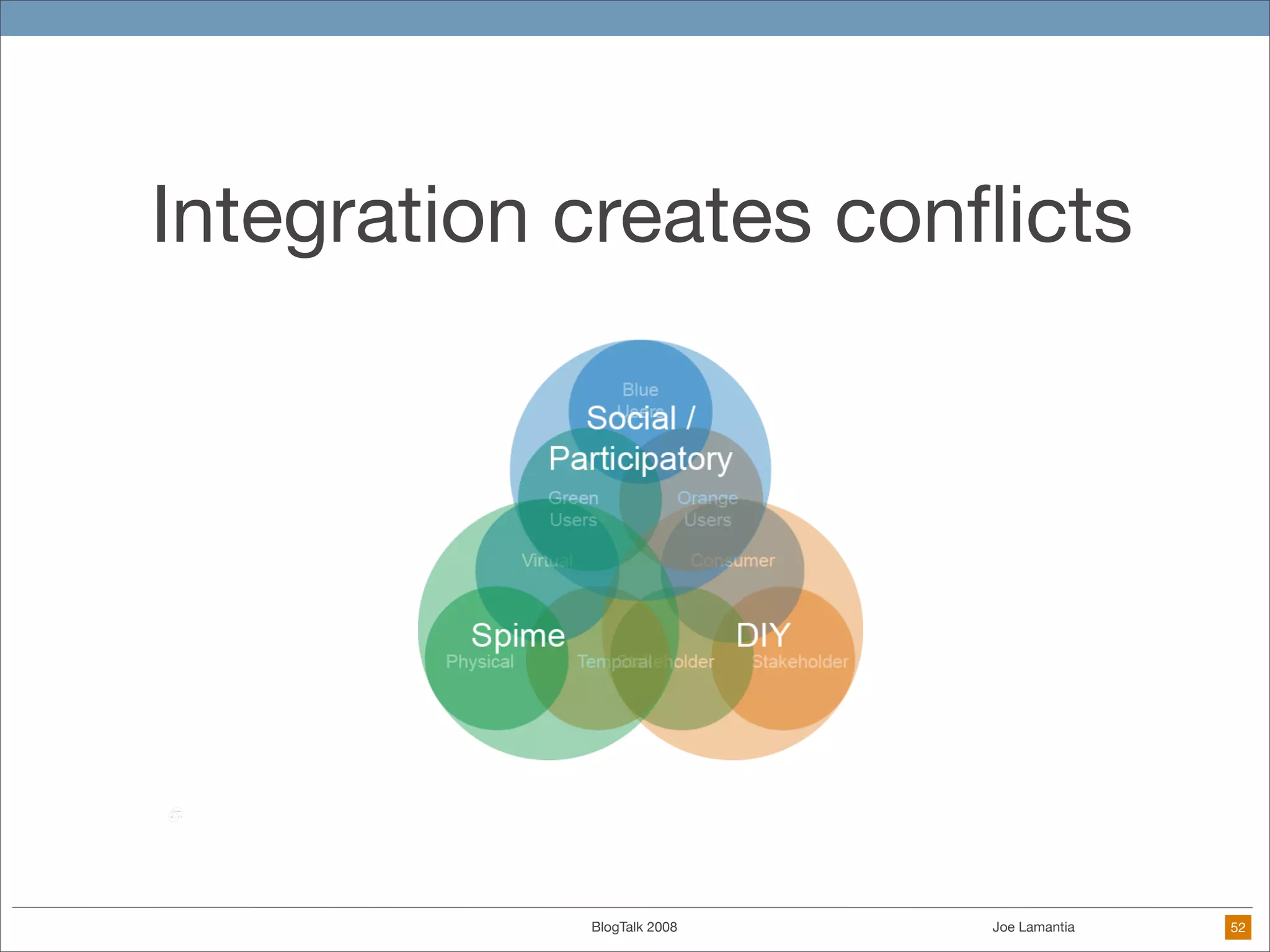

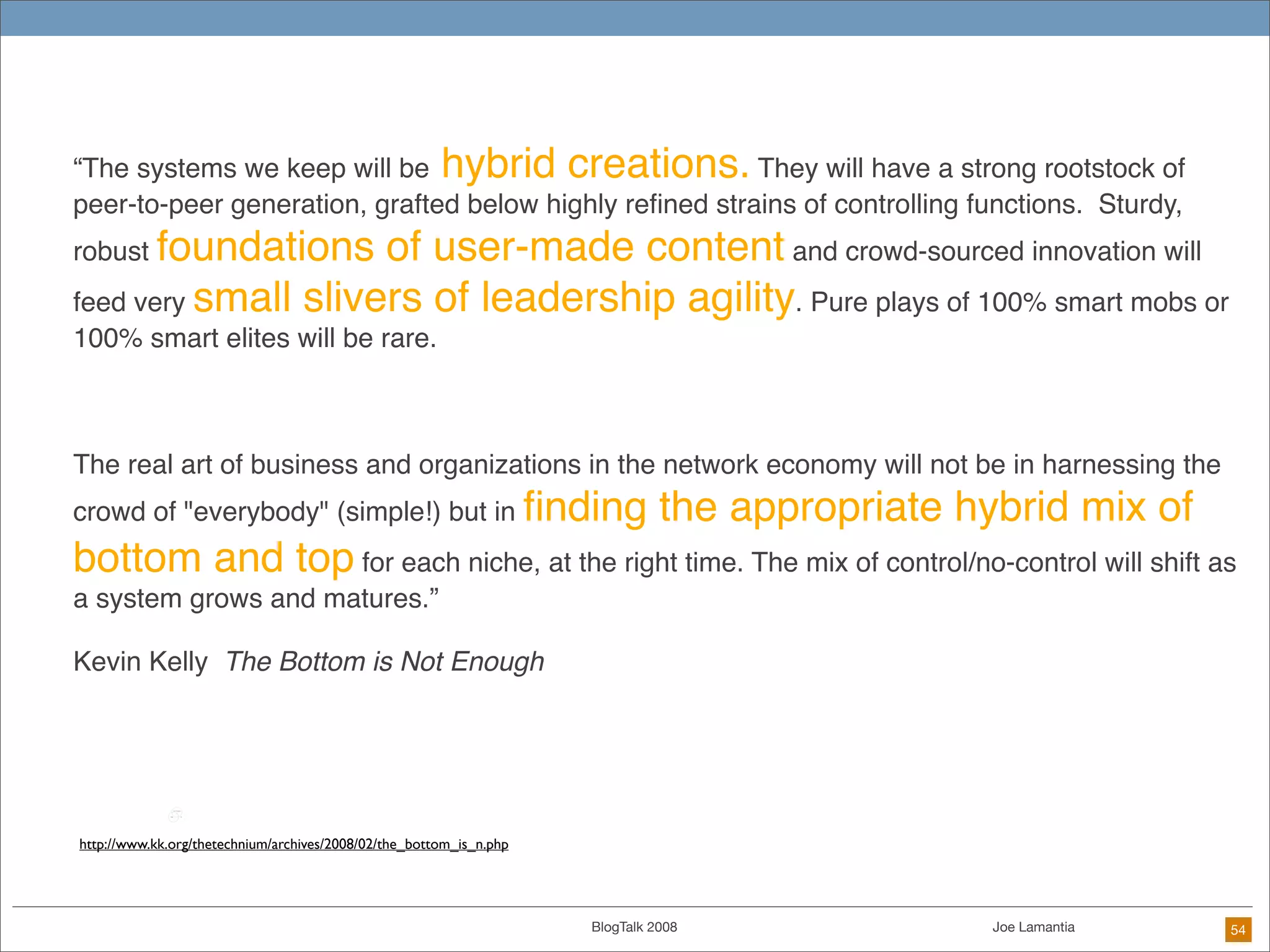
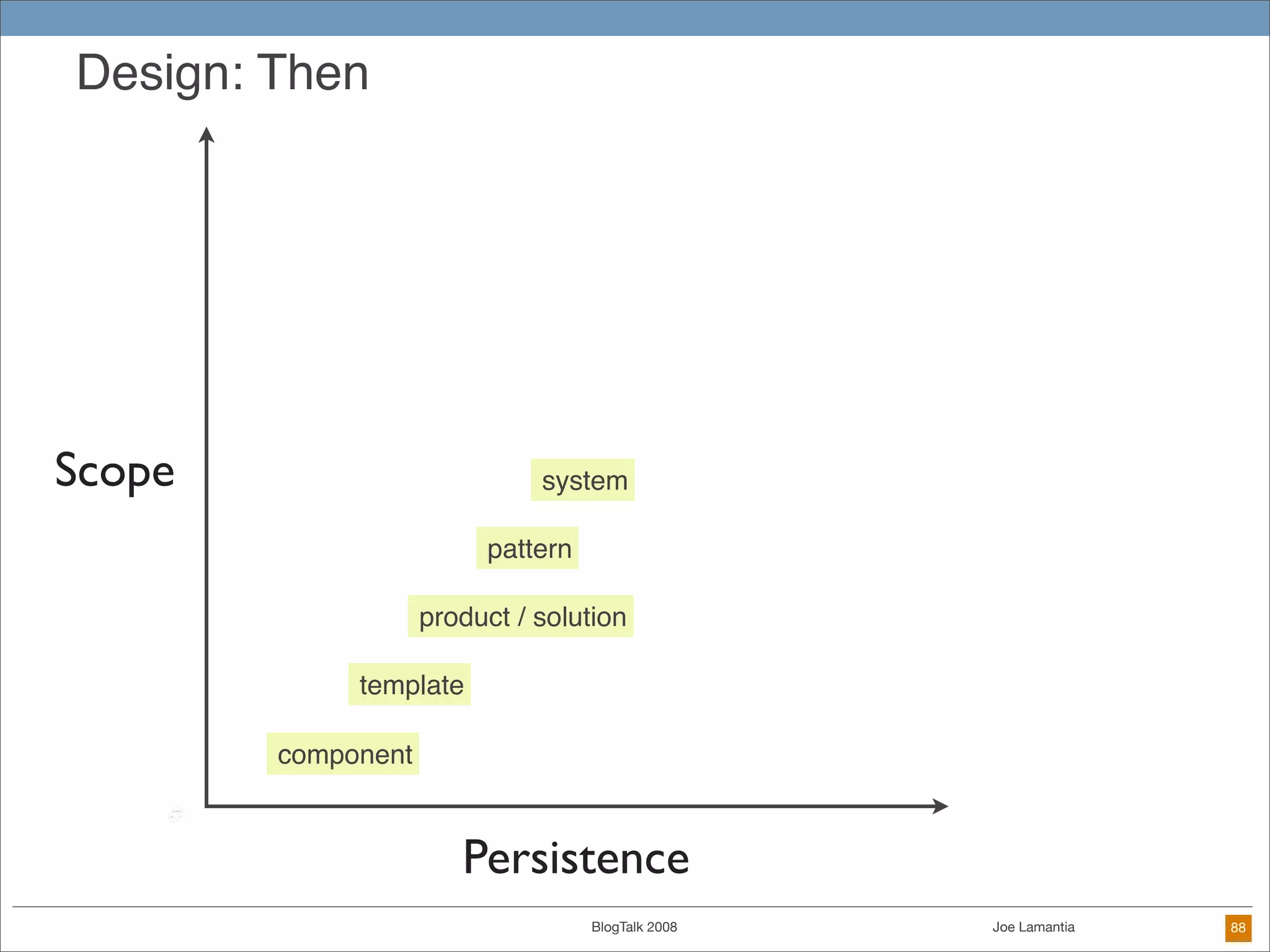
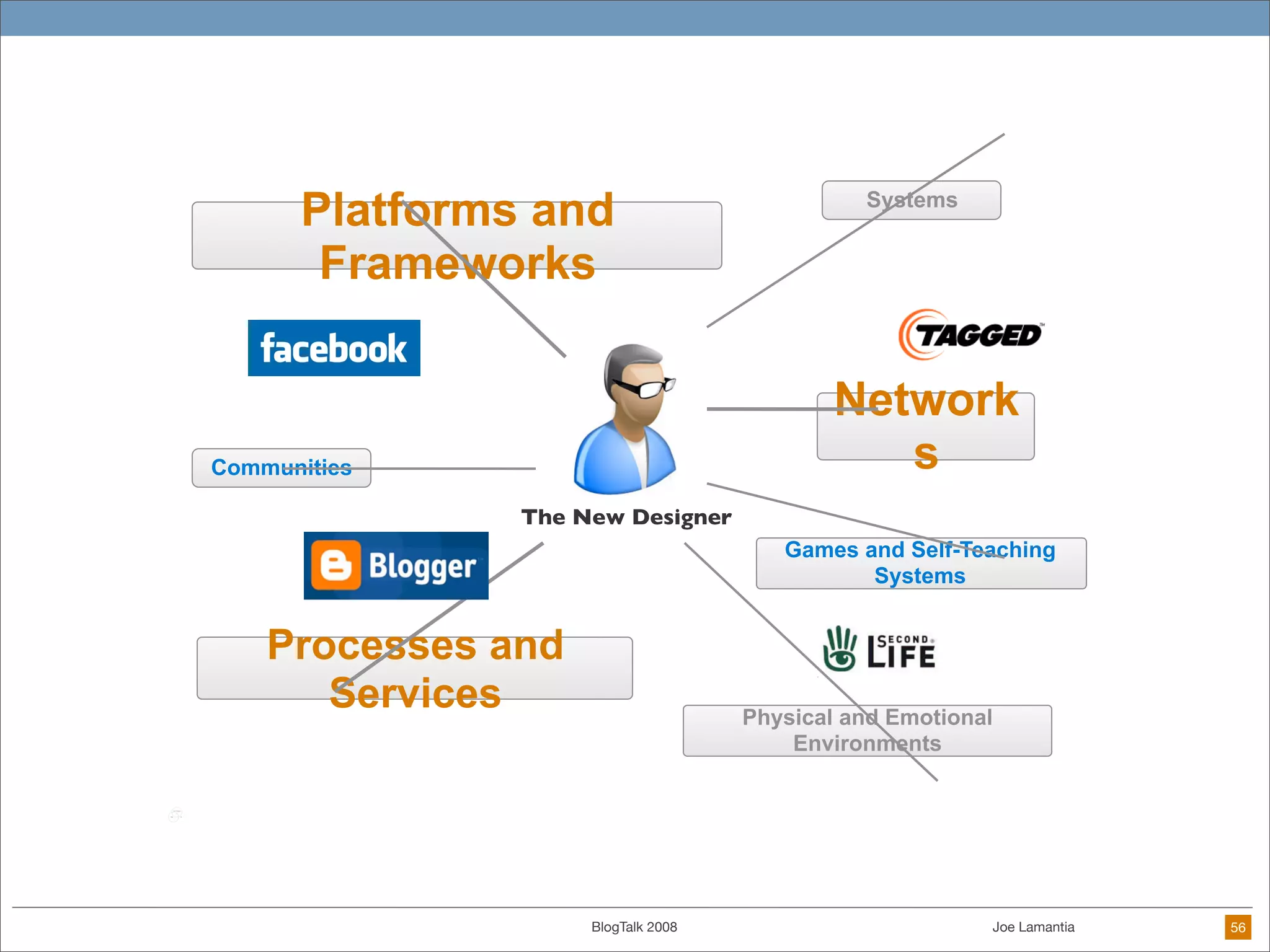
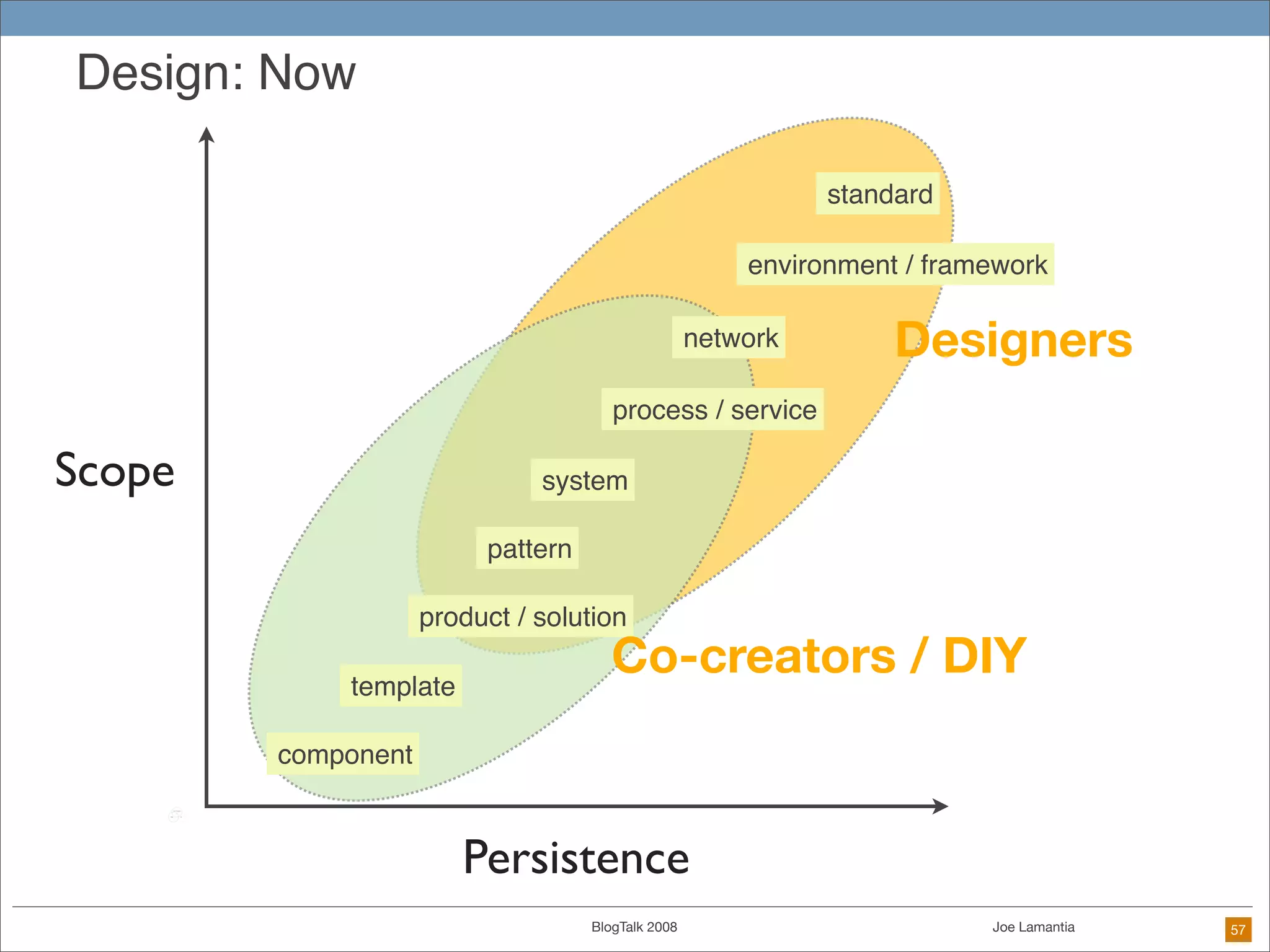
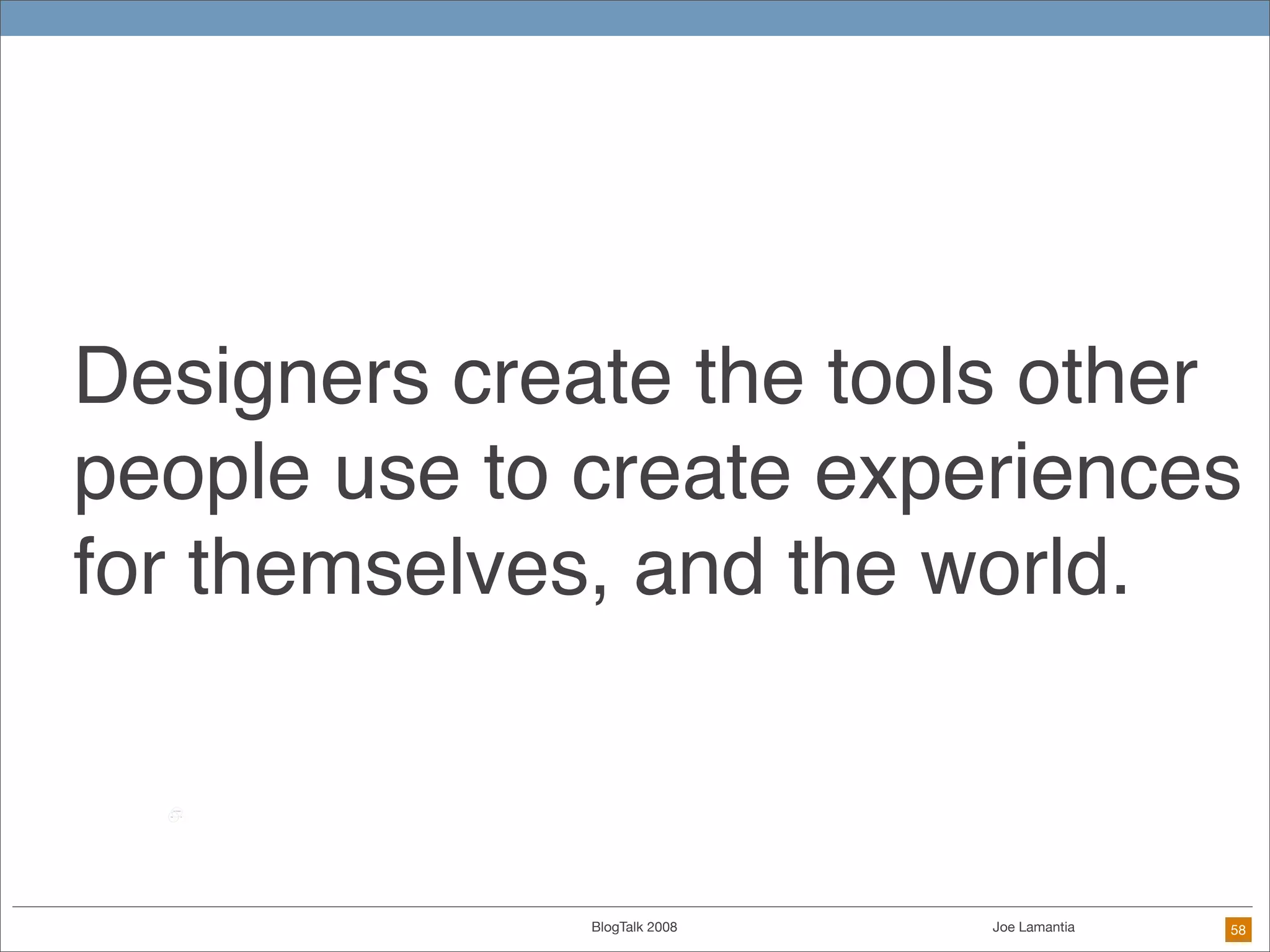
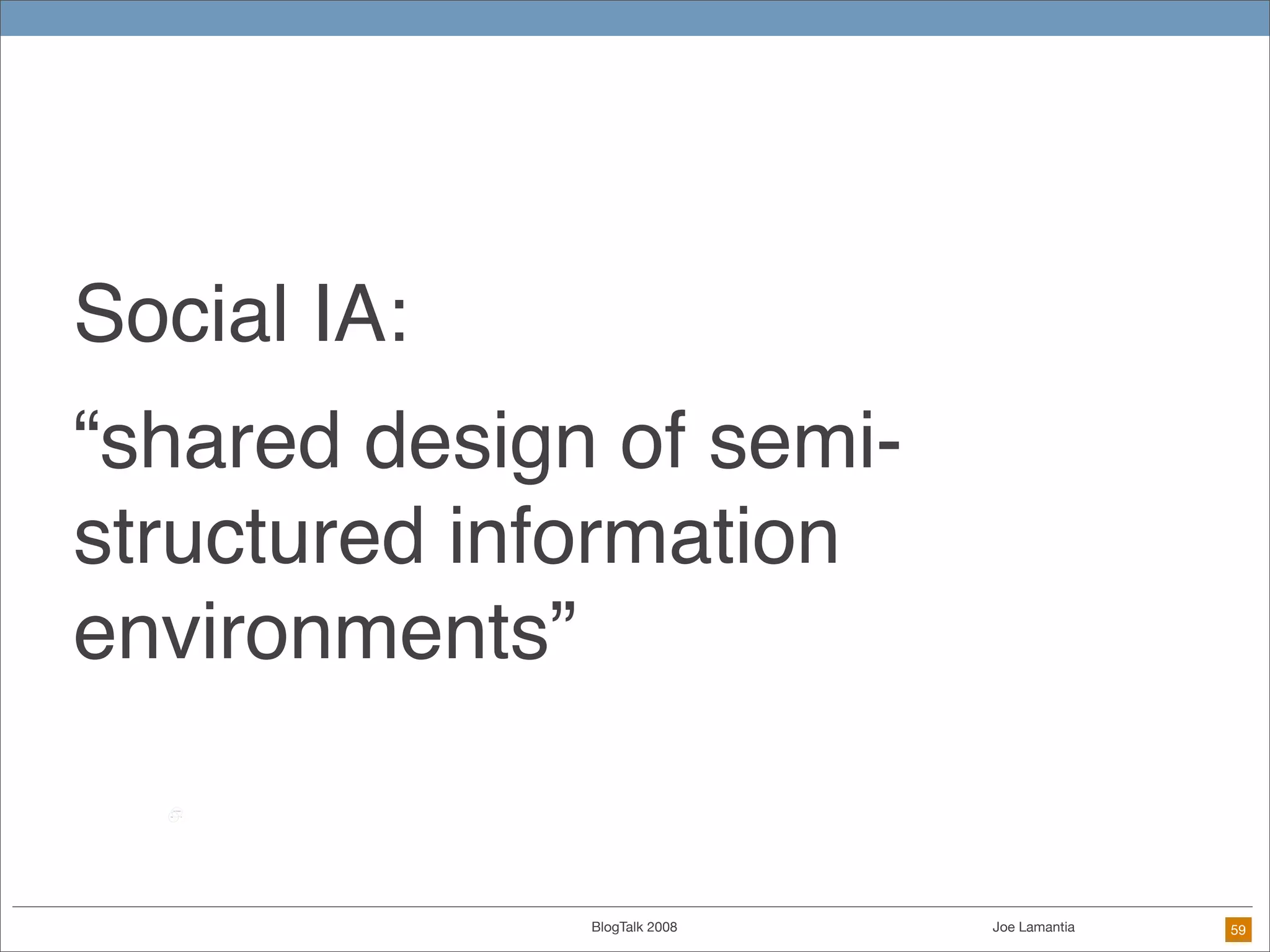
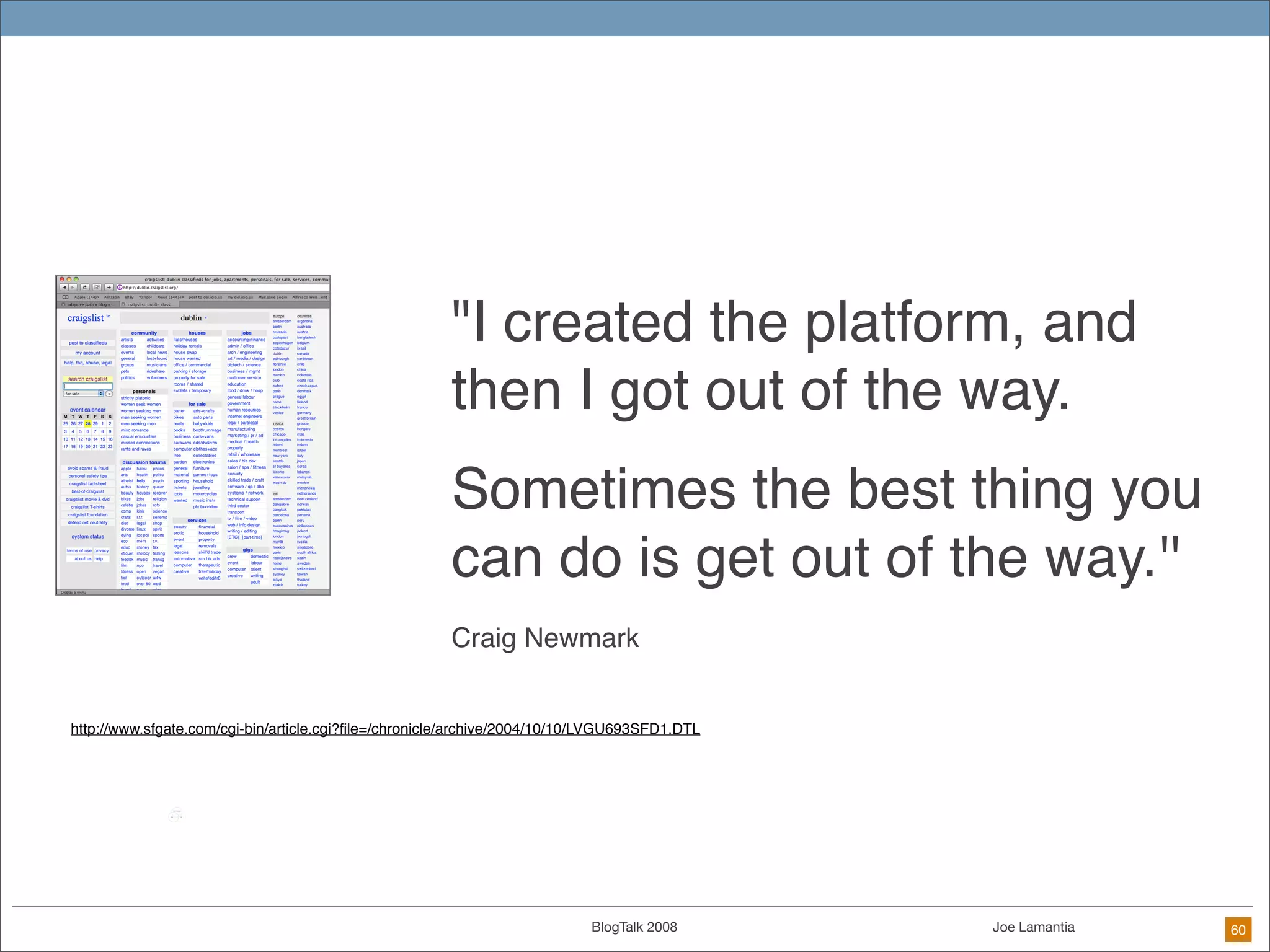






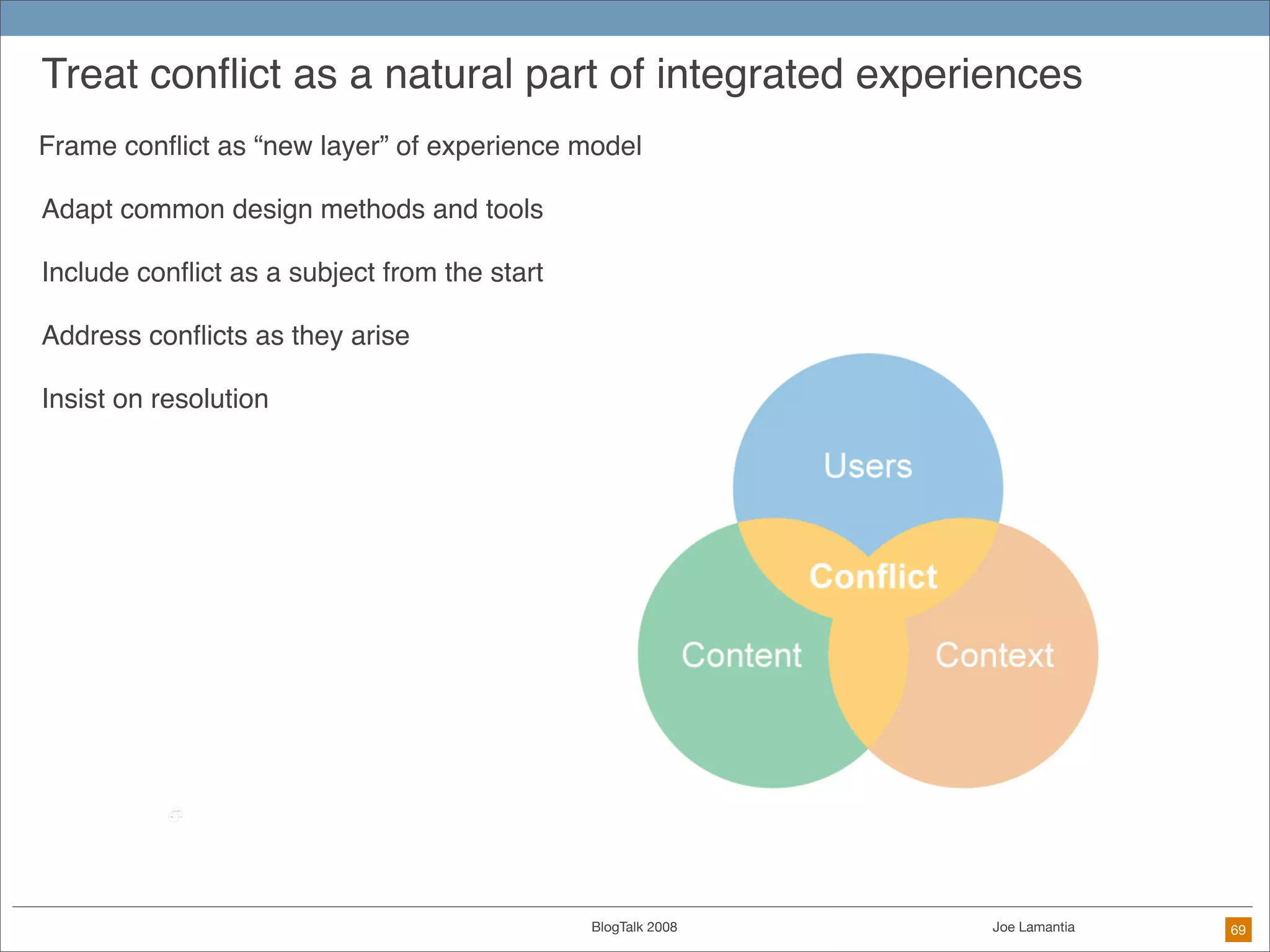

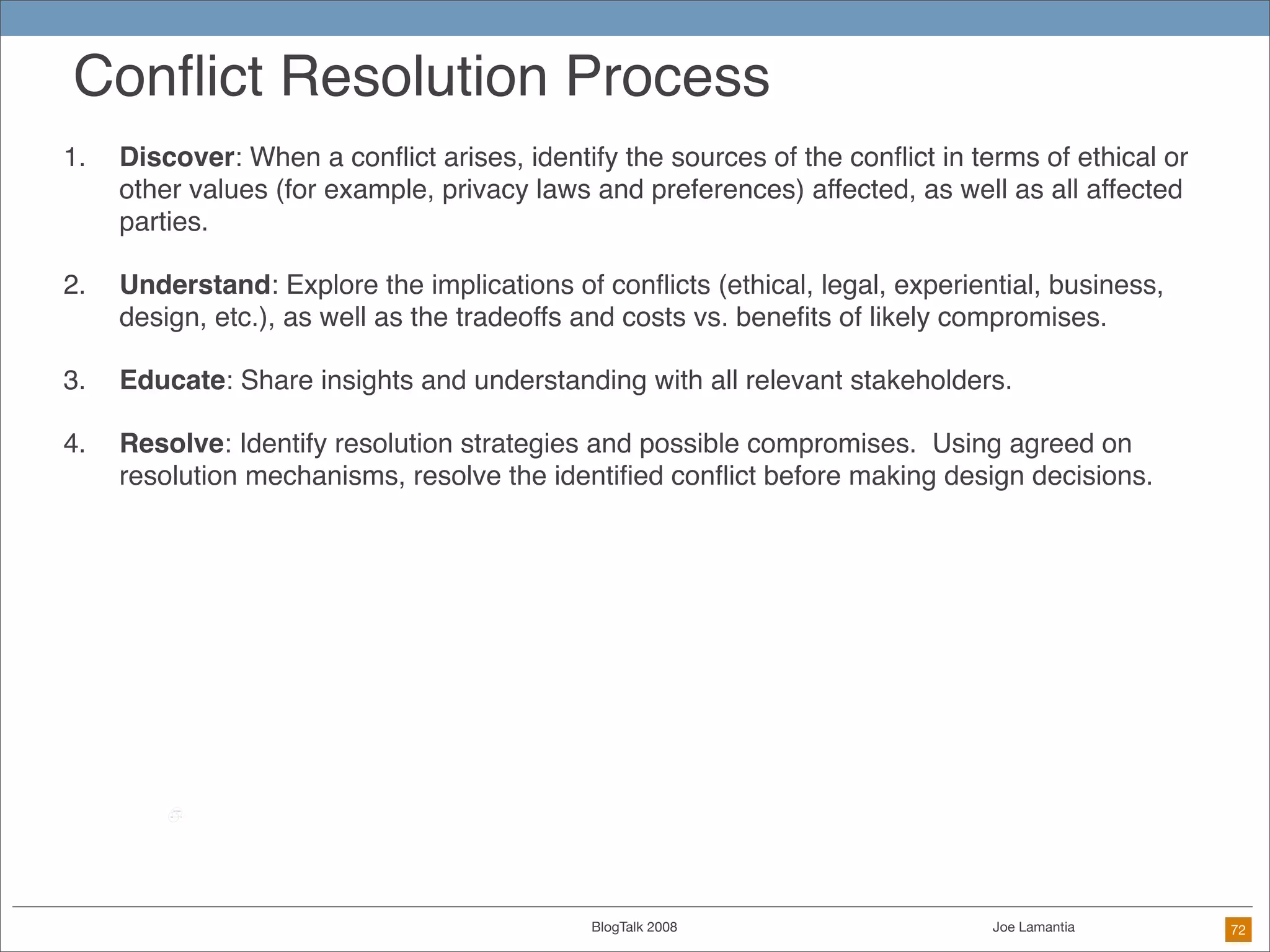
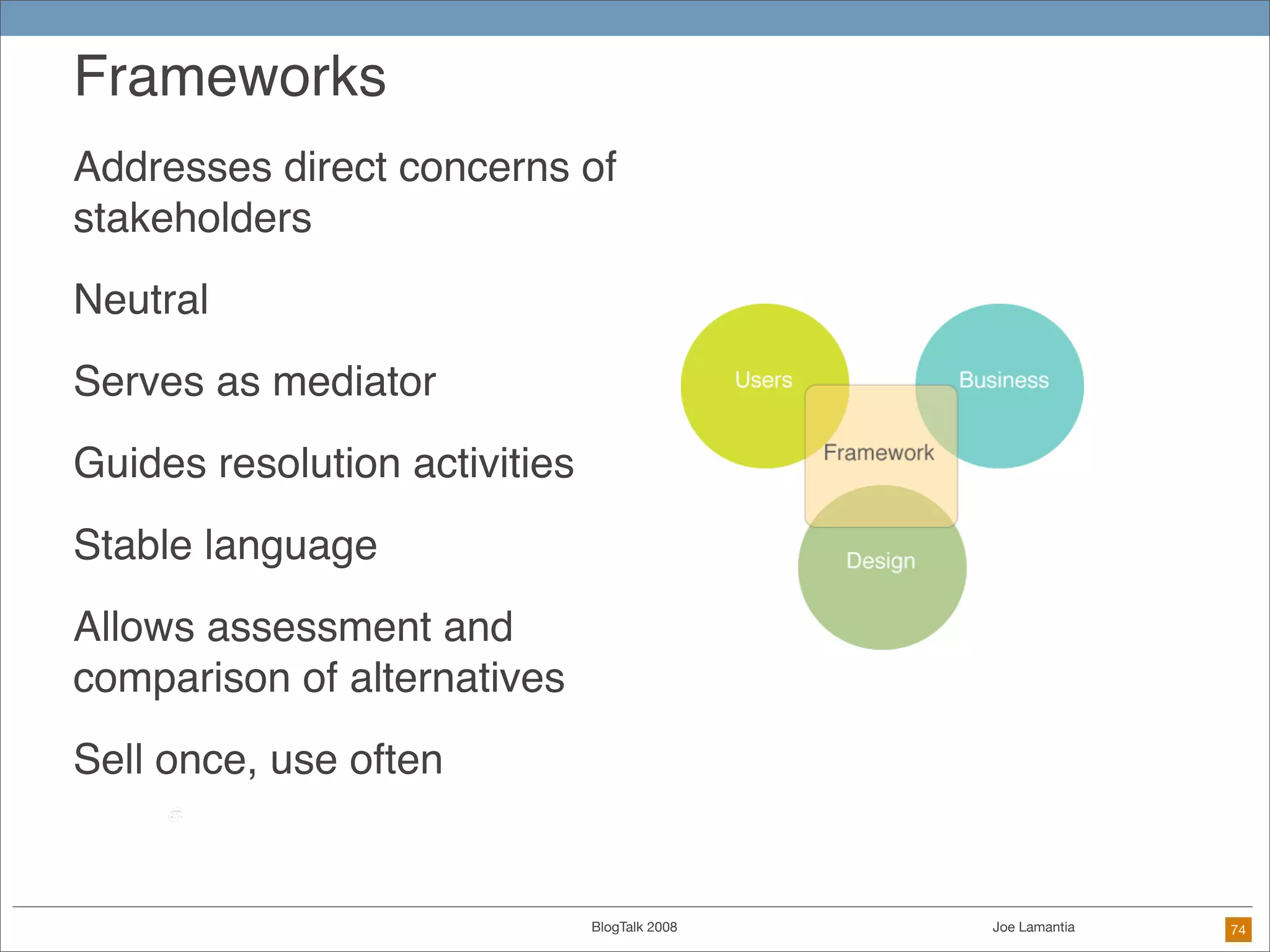
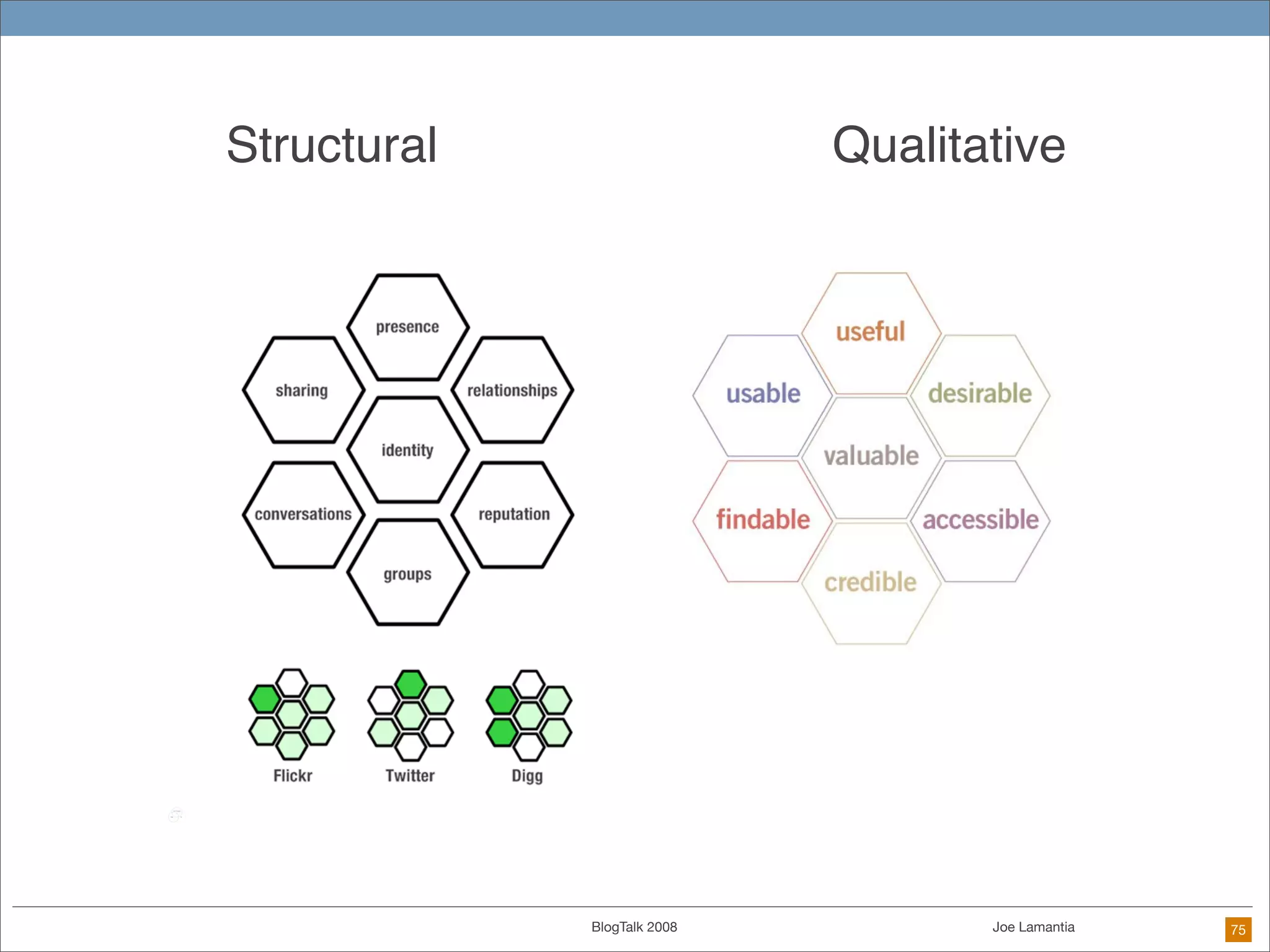
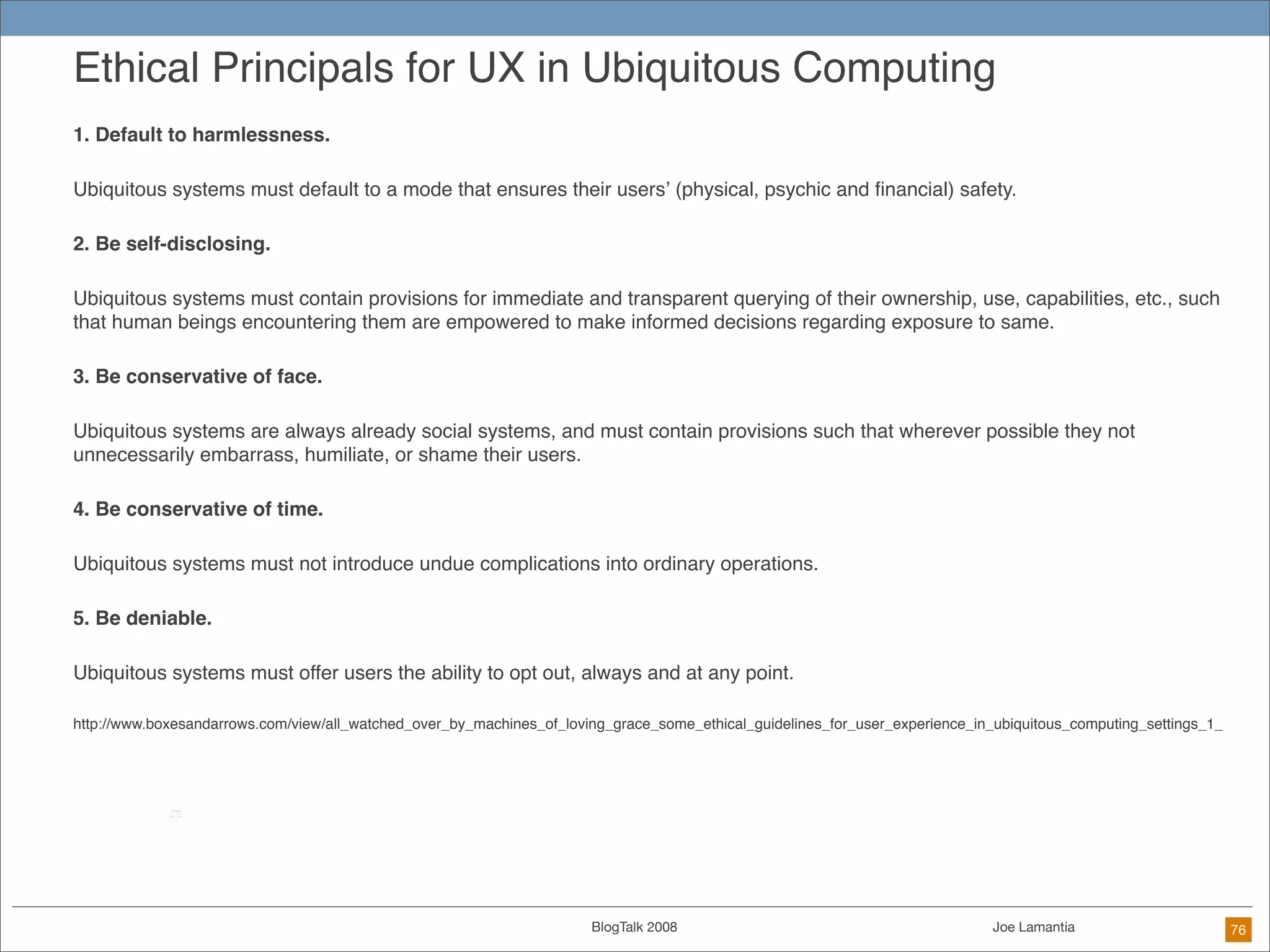
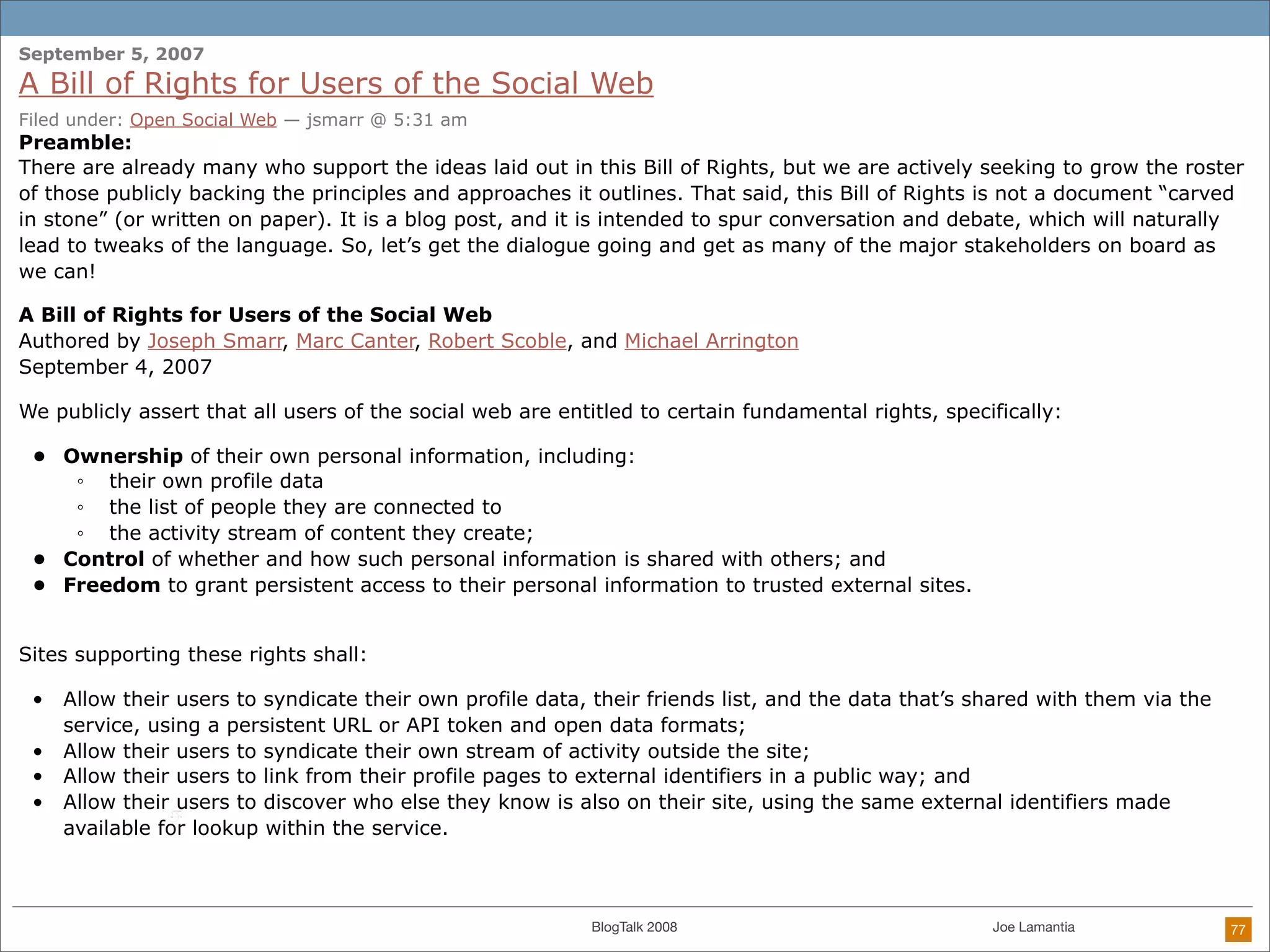

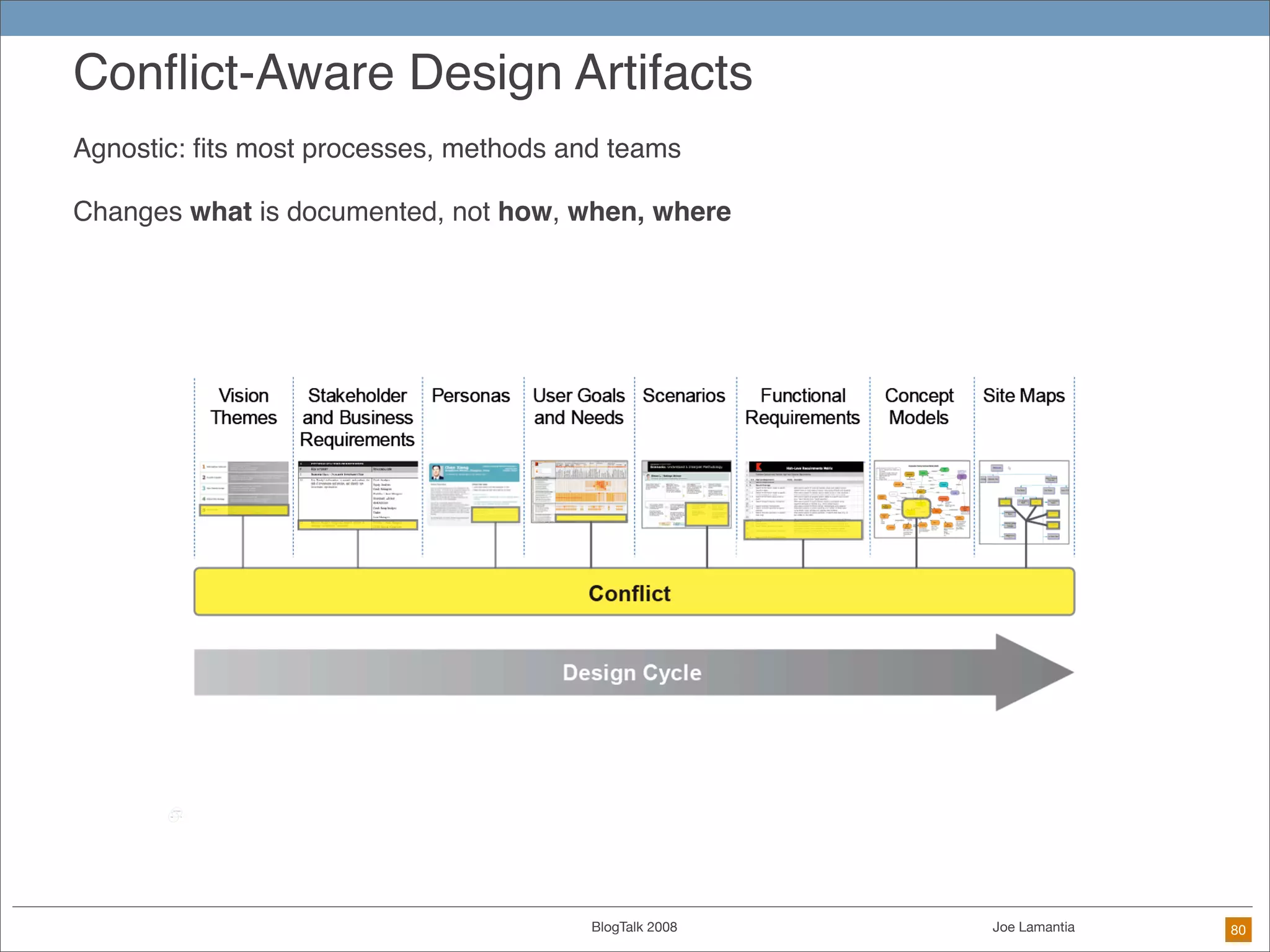

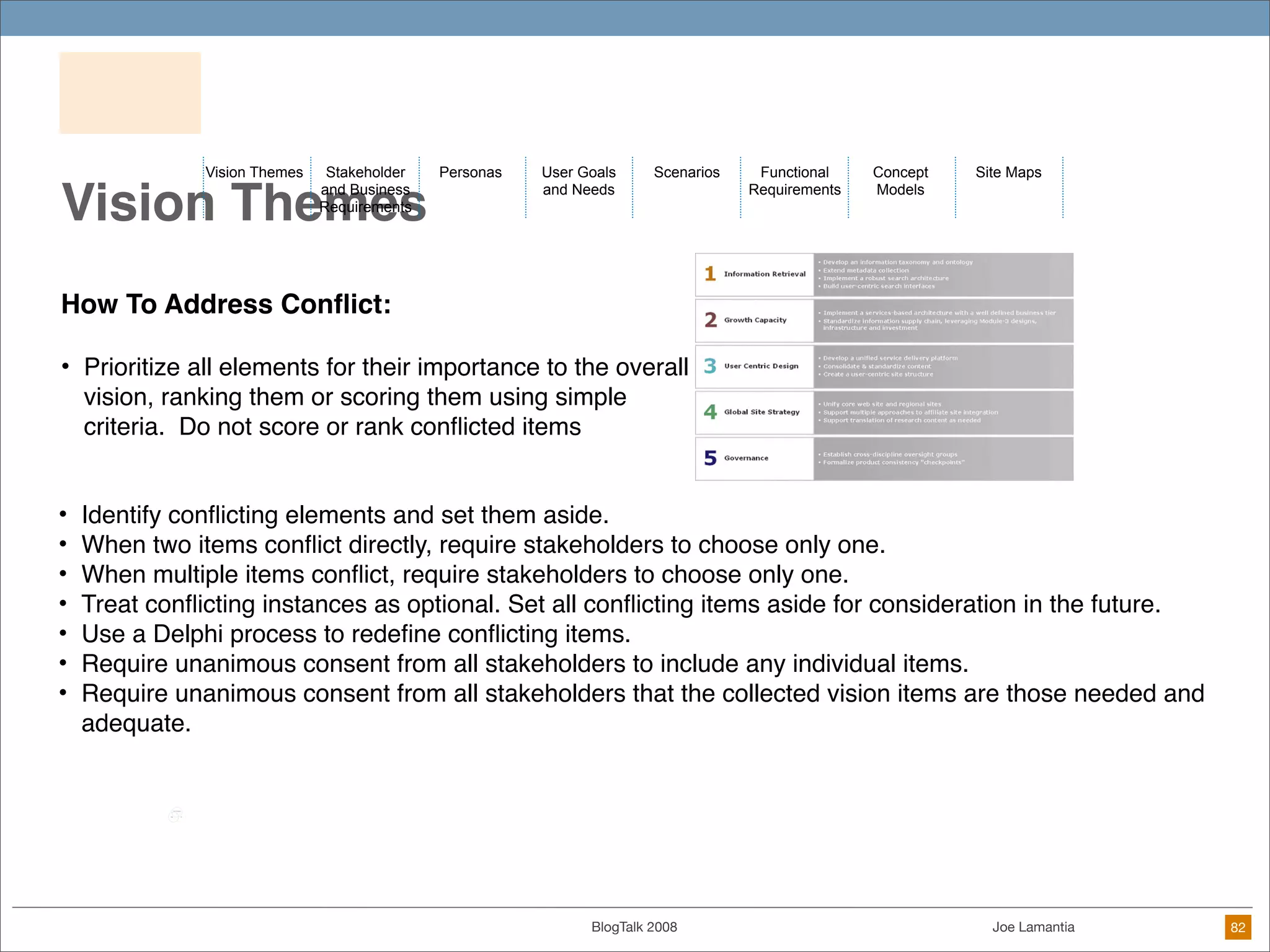
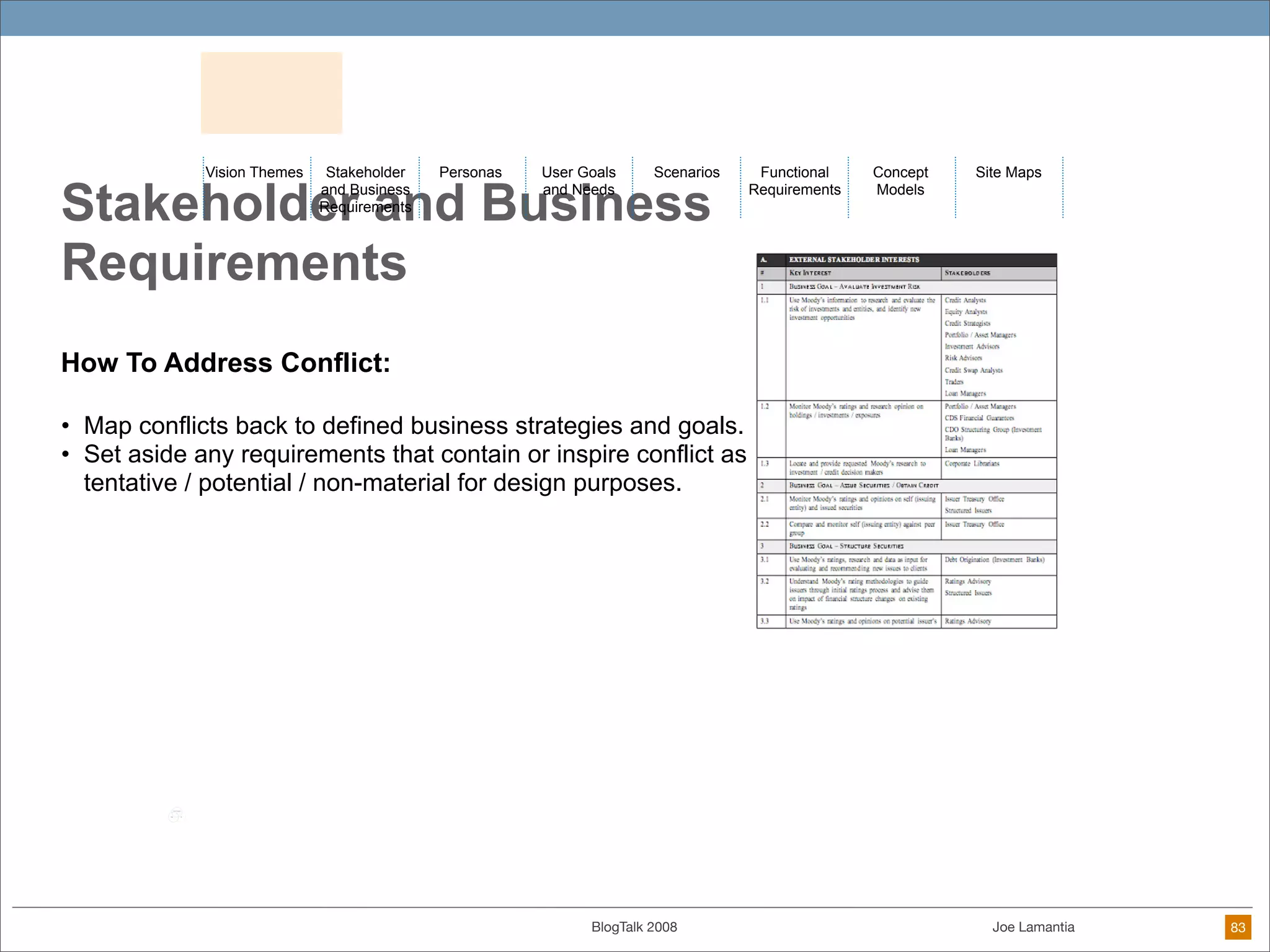
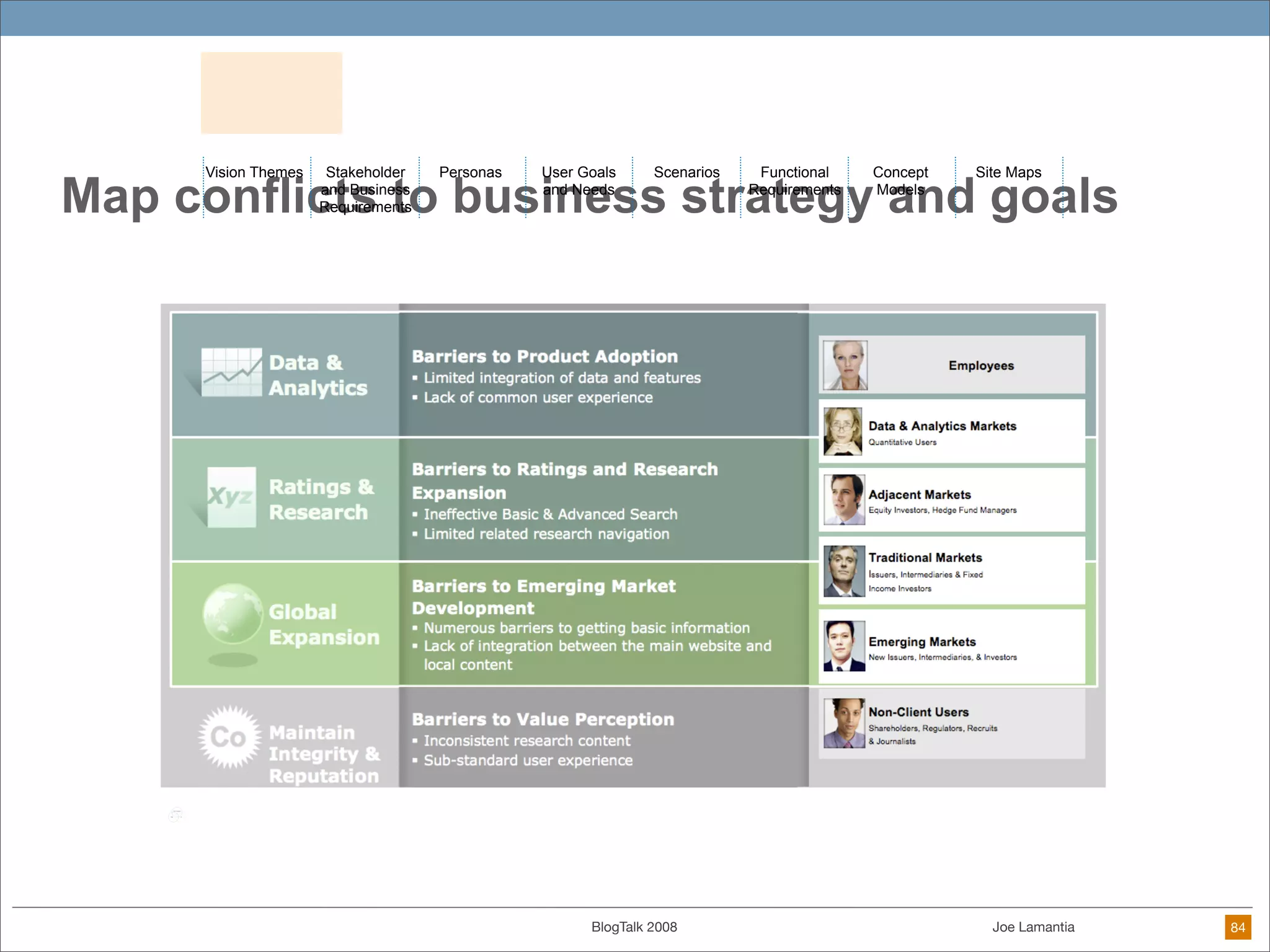
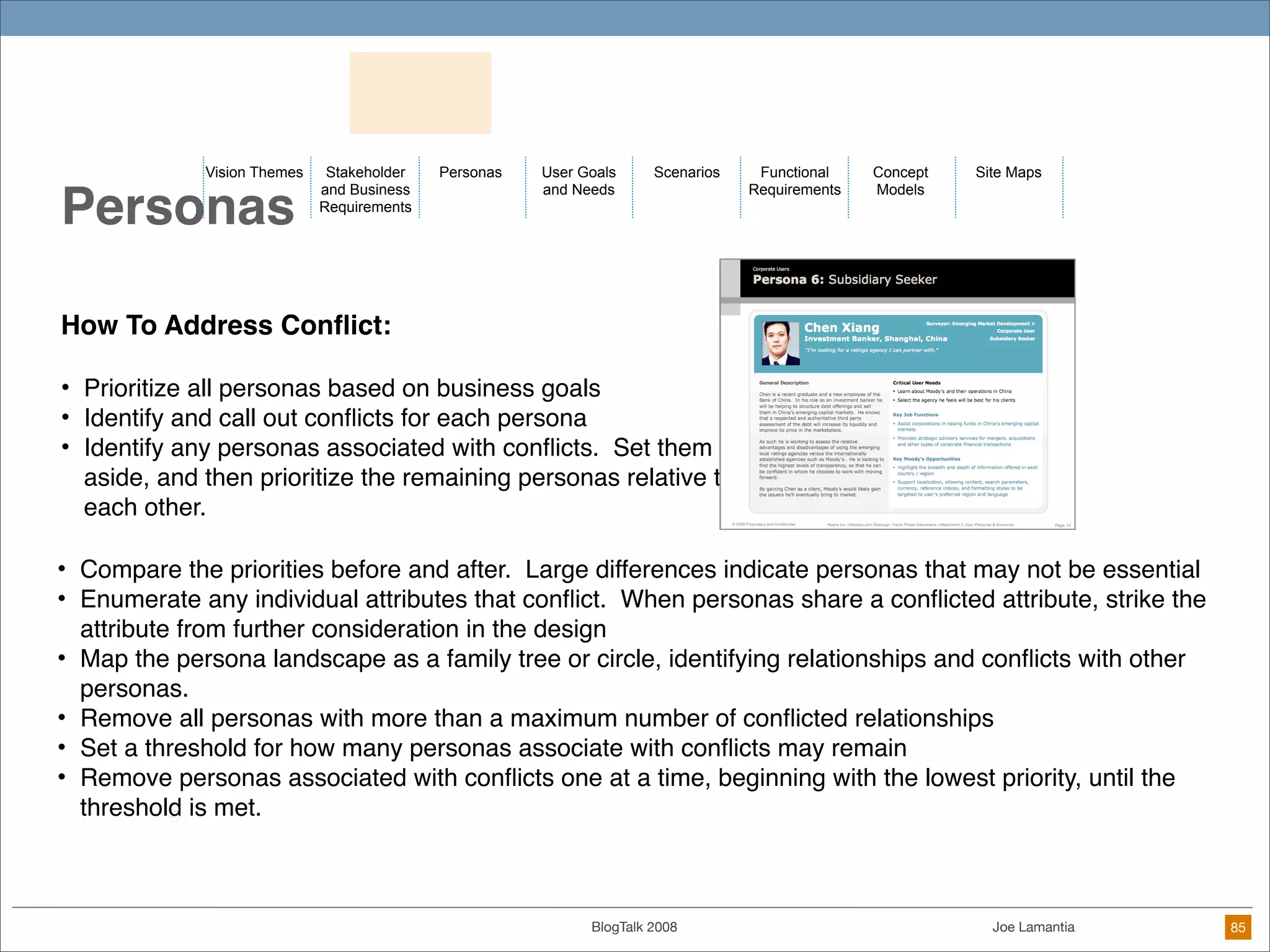
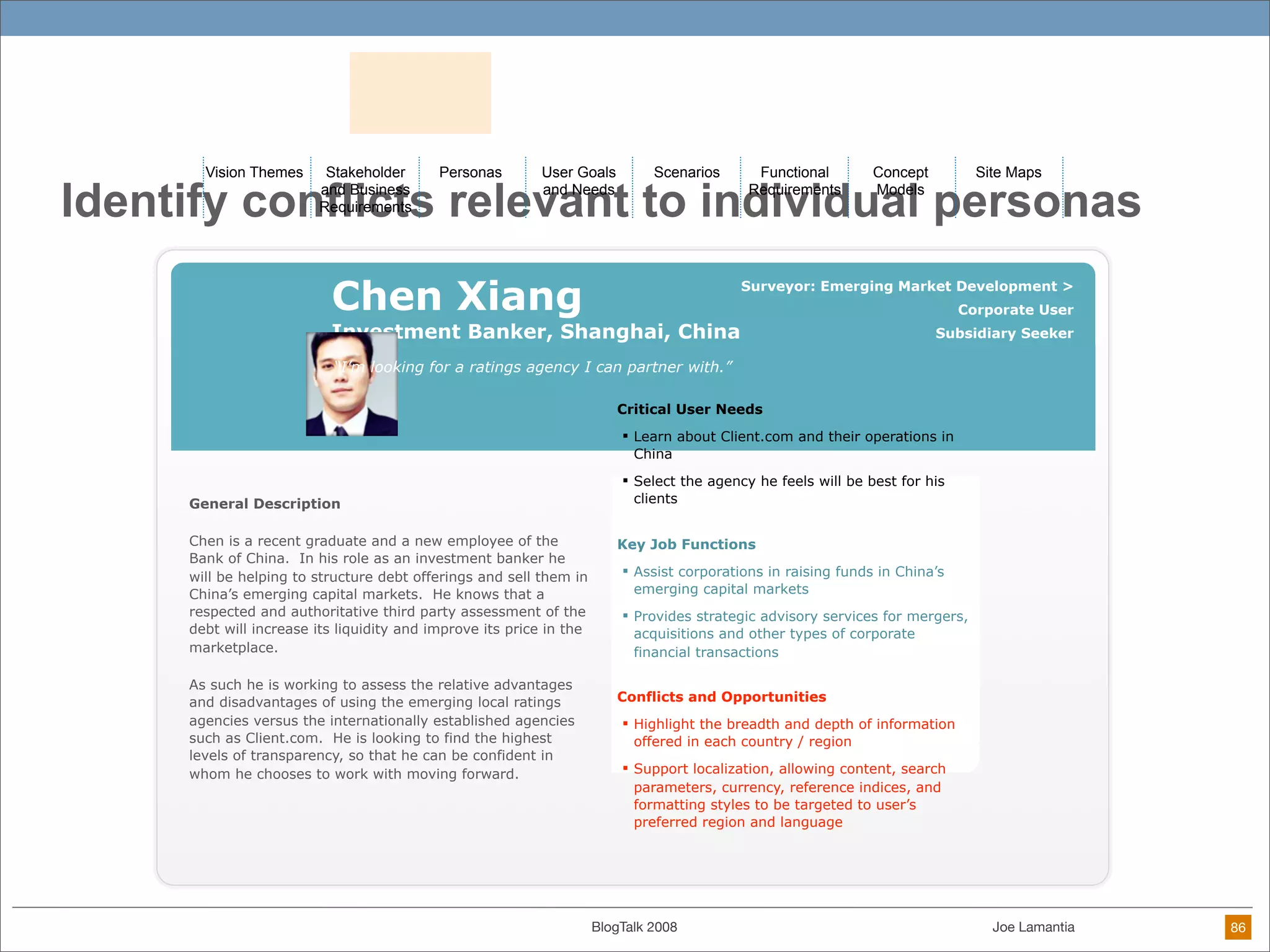
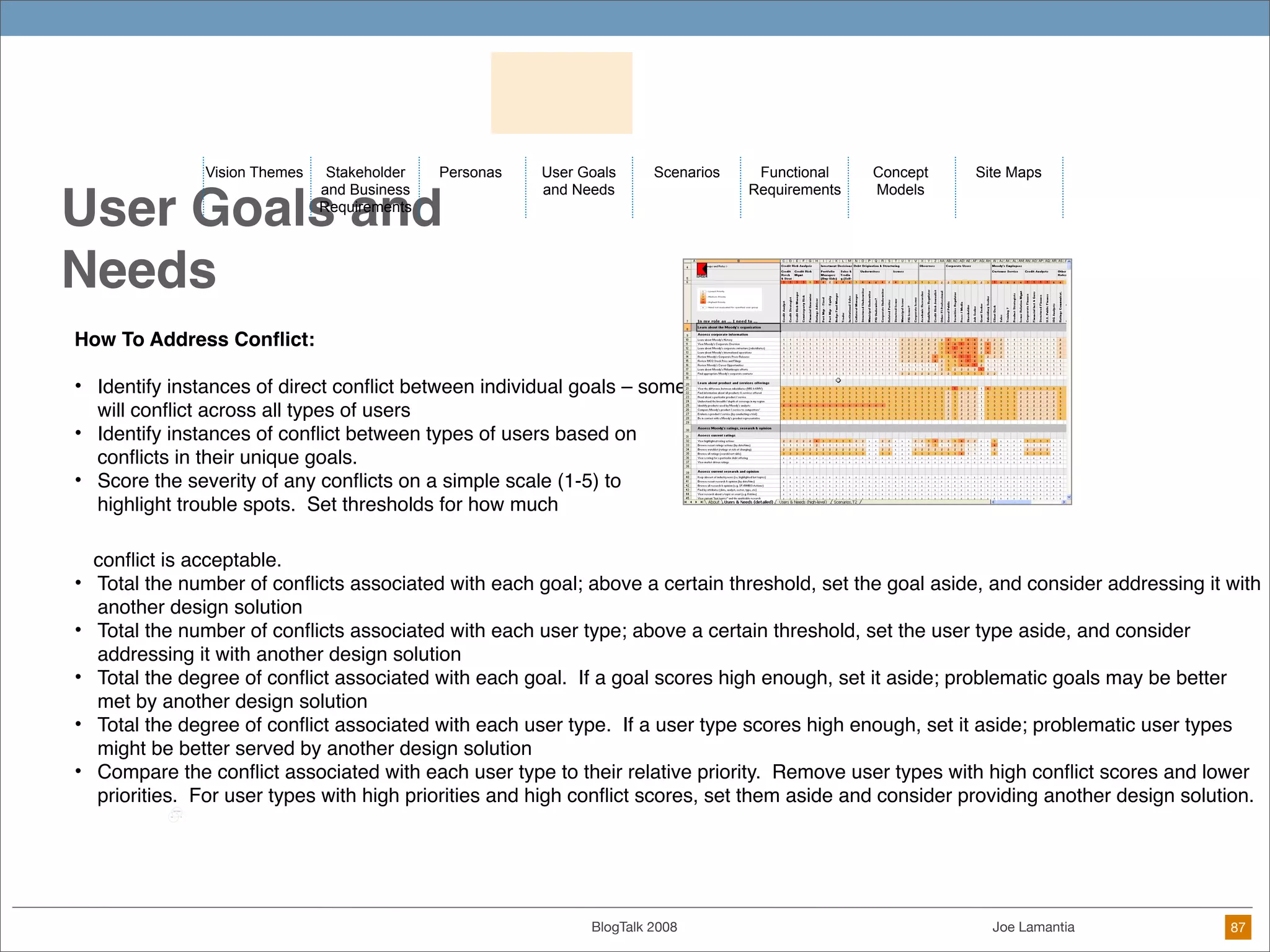
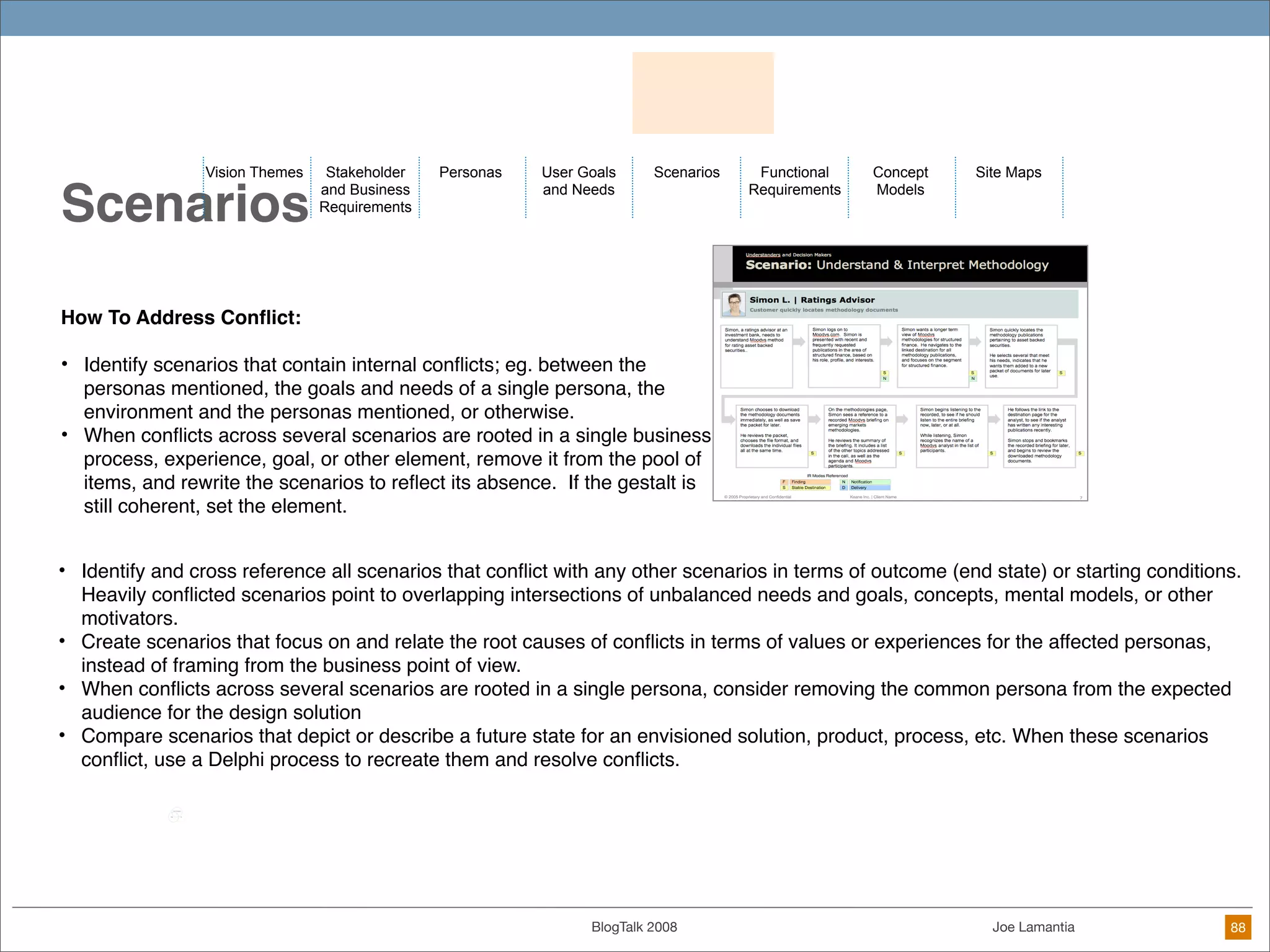
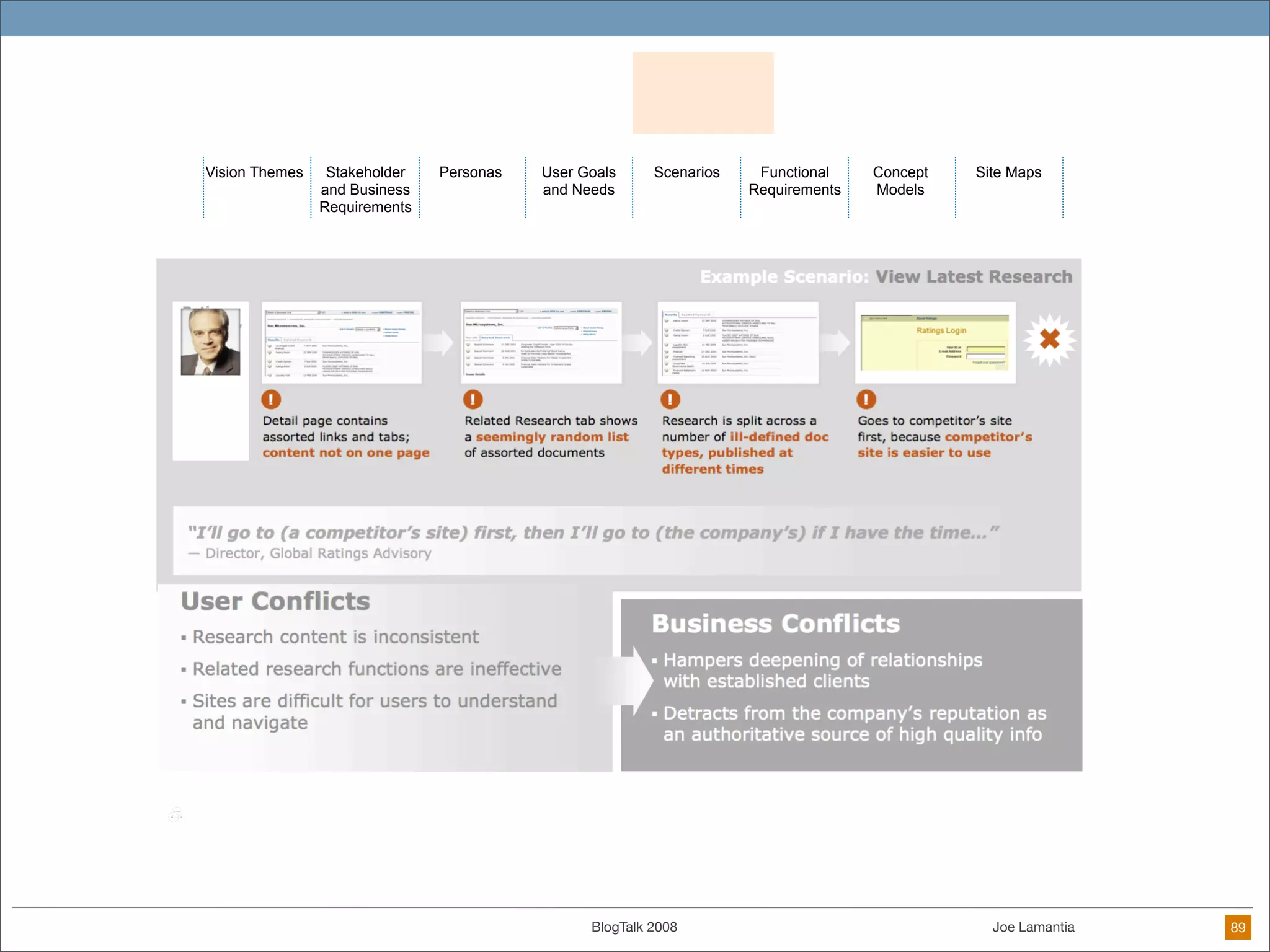
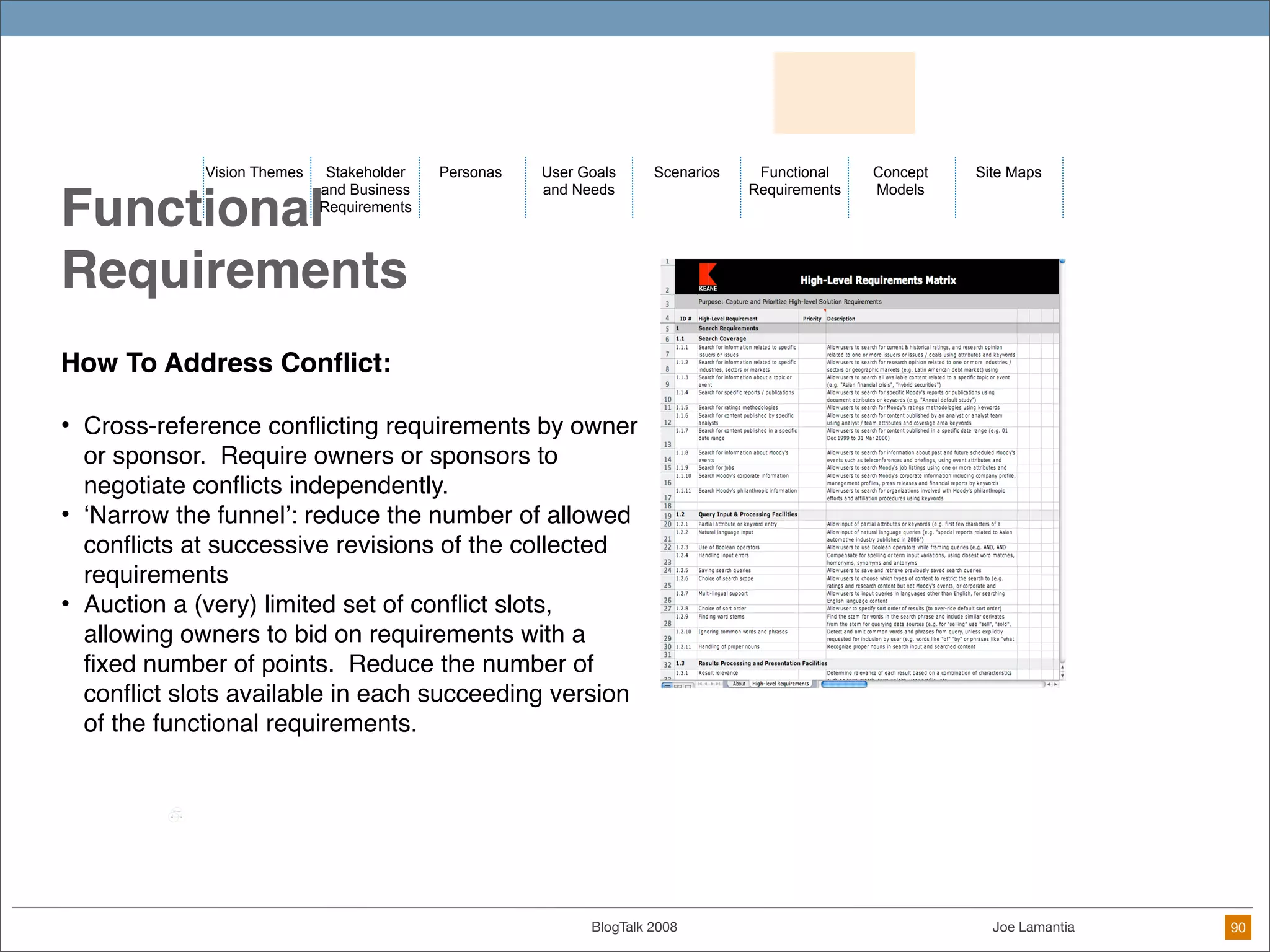
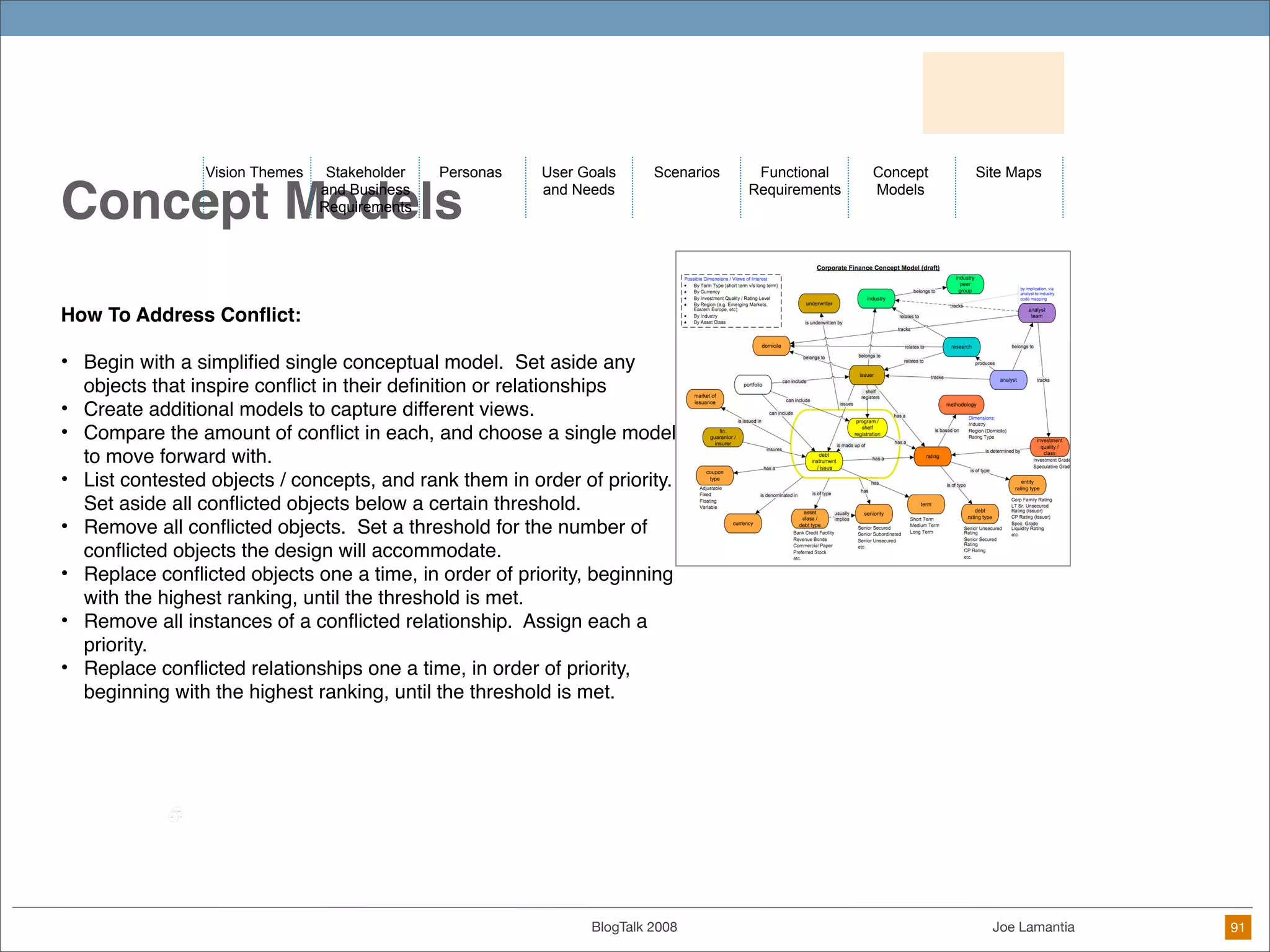
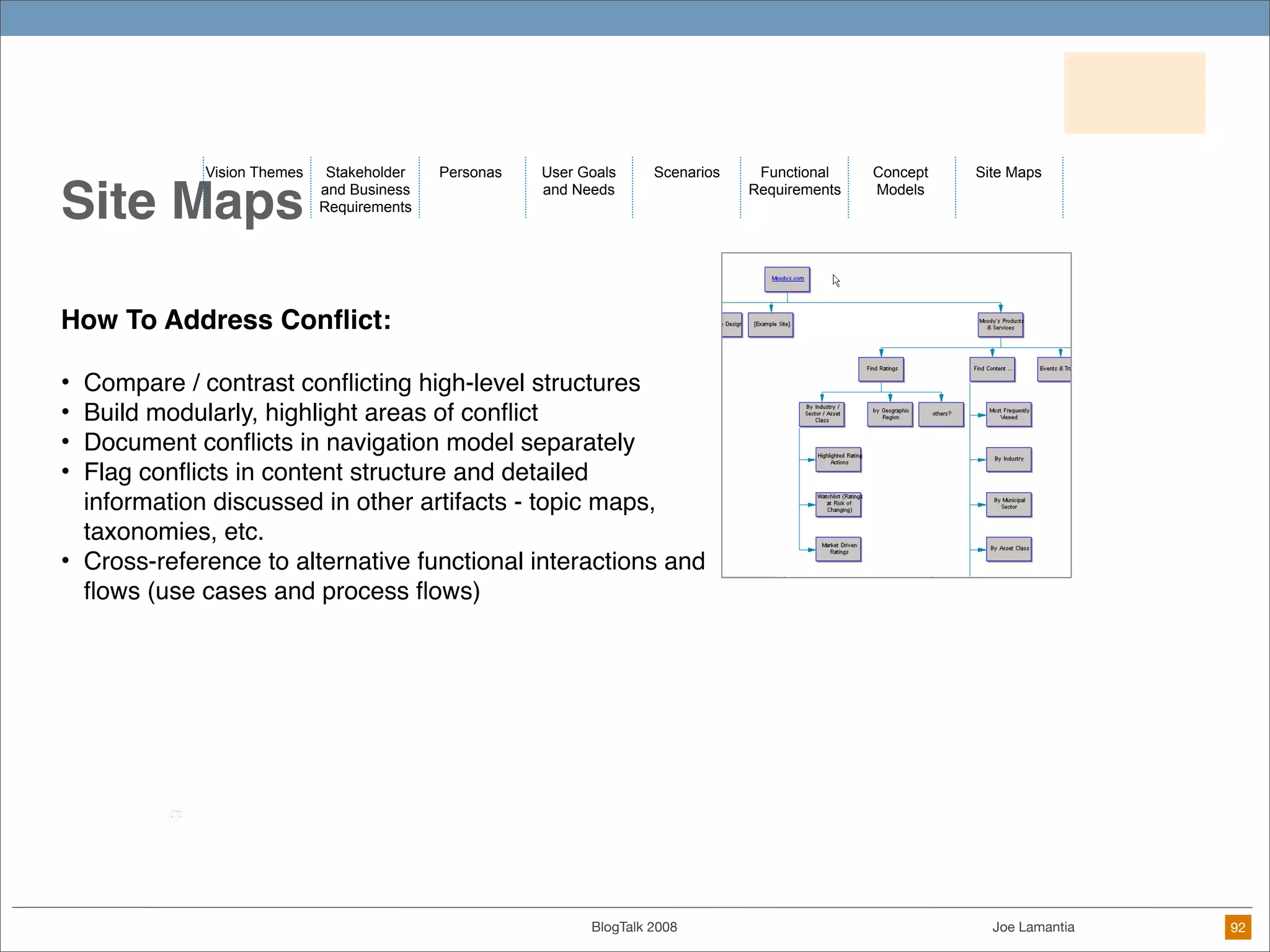

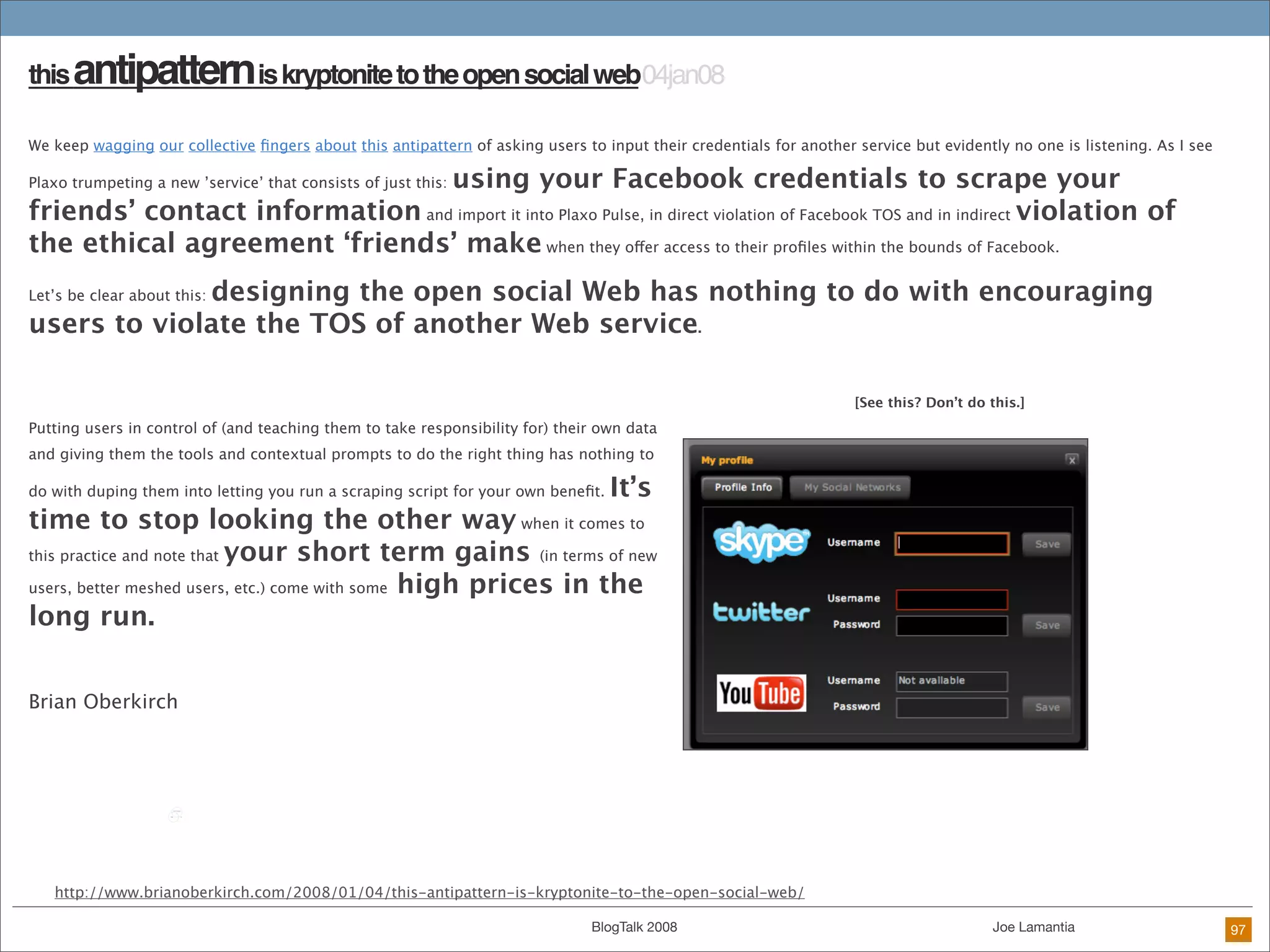



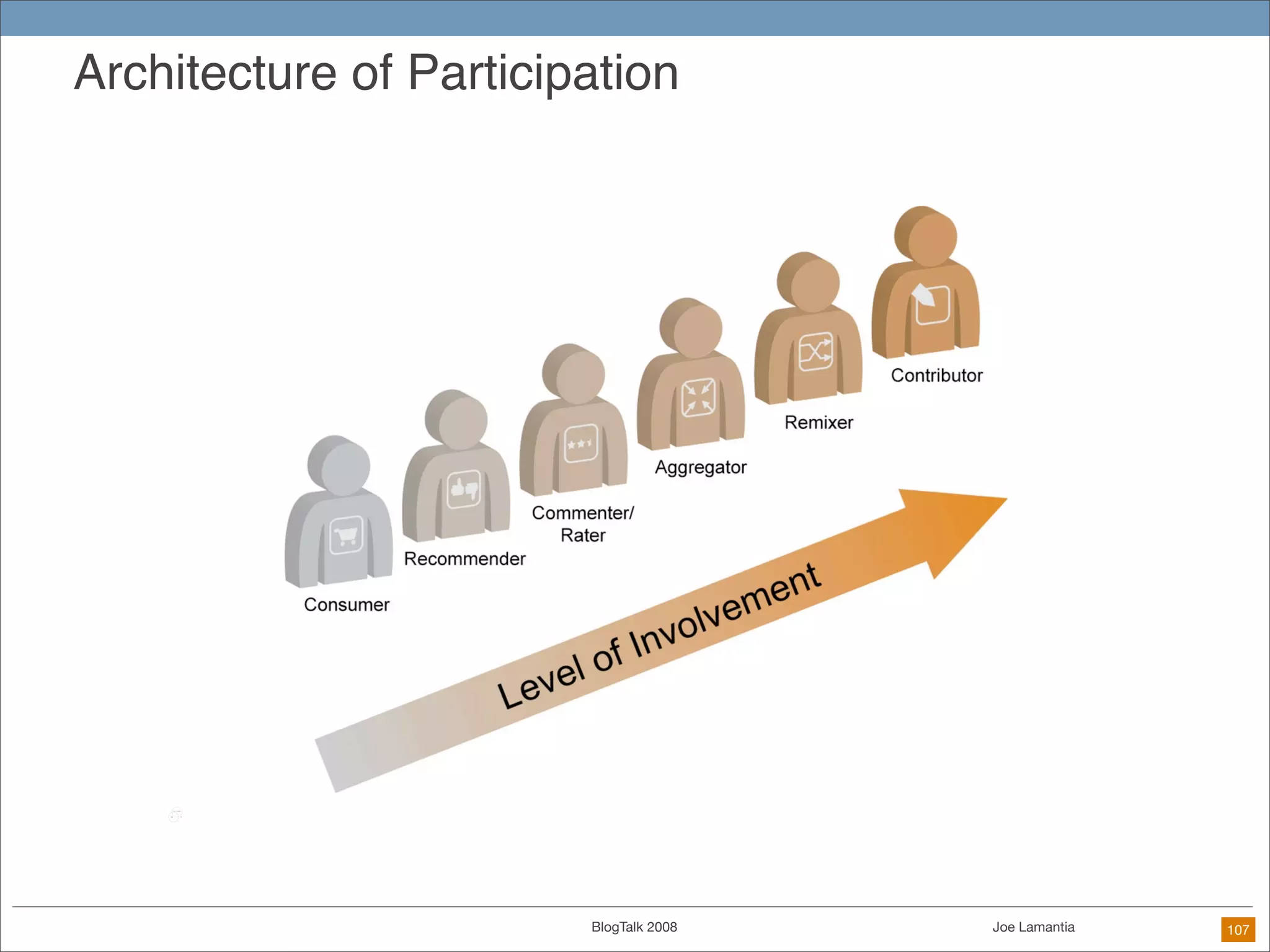

The document discusses ethical challenges in user experience design, particularly in the context of social media and DIY design. It highlights issues related to privacy, user misrepresentation, and the implications of aggressive user acquisition strategies in online platforms like Tagged.com. The content emphasizes the blurring lines between creator and consumer roles, as well as the importance of ethical decision-making in design processes amidst rapidly evolving digital landscapes.










































































































