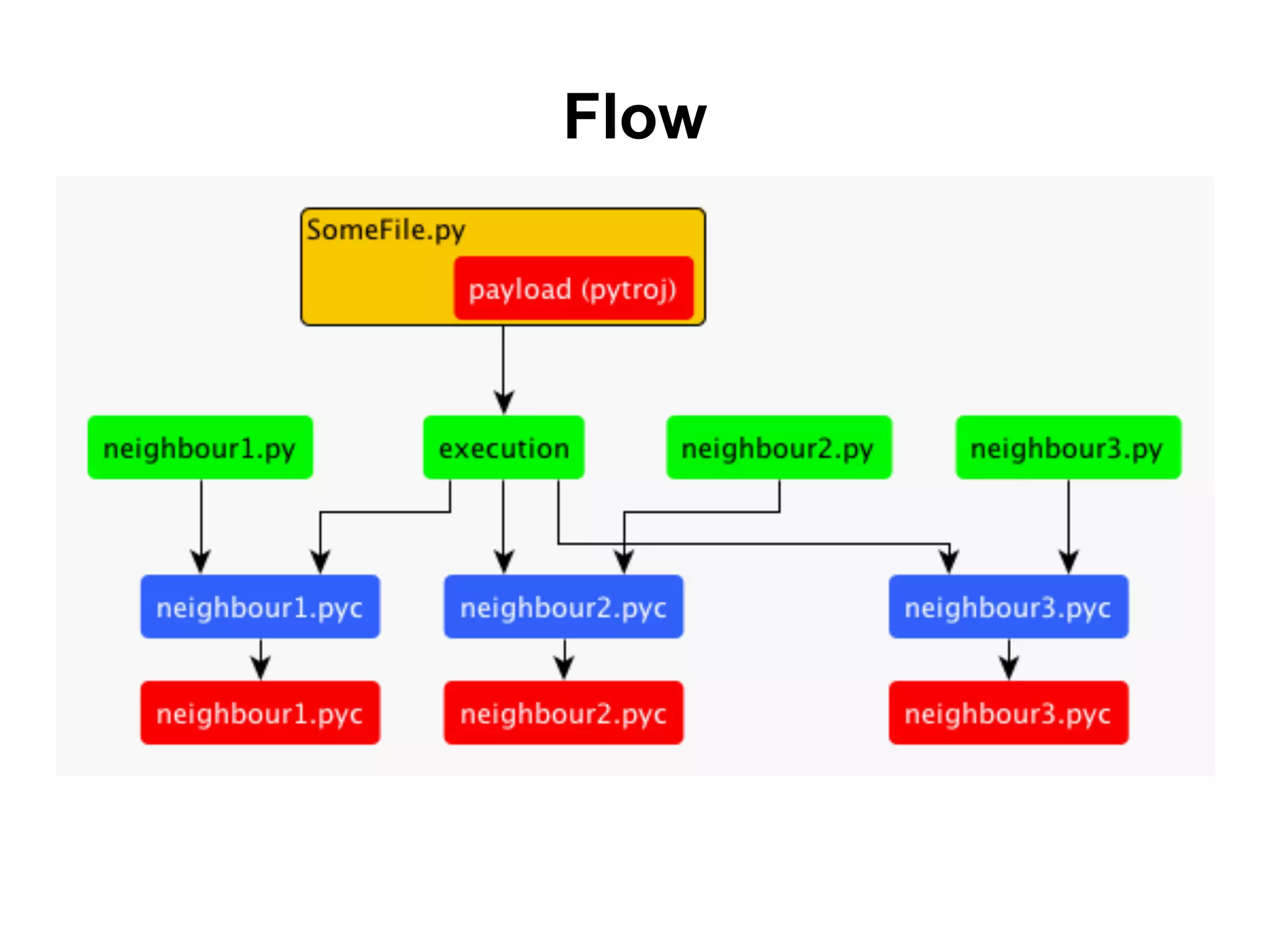
The document discusses a hackathon project called Pytroj, which focuses on creating a self-infecting payload for Python files. Pytroj targets .pyc files, injecting itself to execute original bytecode while maintaining timestamps to avoid detection. The document also highlights methods for minimizing the payload size and the potential for malicious applications, such as installing harmful packages through pip.








![Automatically detecting length of
exploit
● Simple hack - begin and end code with:
signature = "DC9723"
● Gets translated into:
0 LOAD_CONST 0 ('DC9723')
3 STORE_NAME 0 (signature)
● if data.code[1][1] == signature:
#Code is already infected
return
● To find exploit size, iterate over own code
until you come to the second signature,
easy!](https://image.slidesharecdn.com/pytroj-111120040505-phpapp01/75/Infecting-Python-Bytecode-12-2048.jpg)