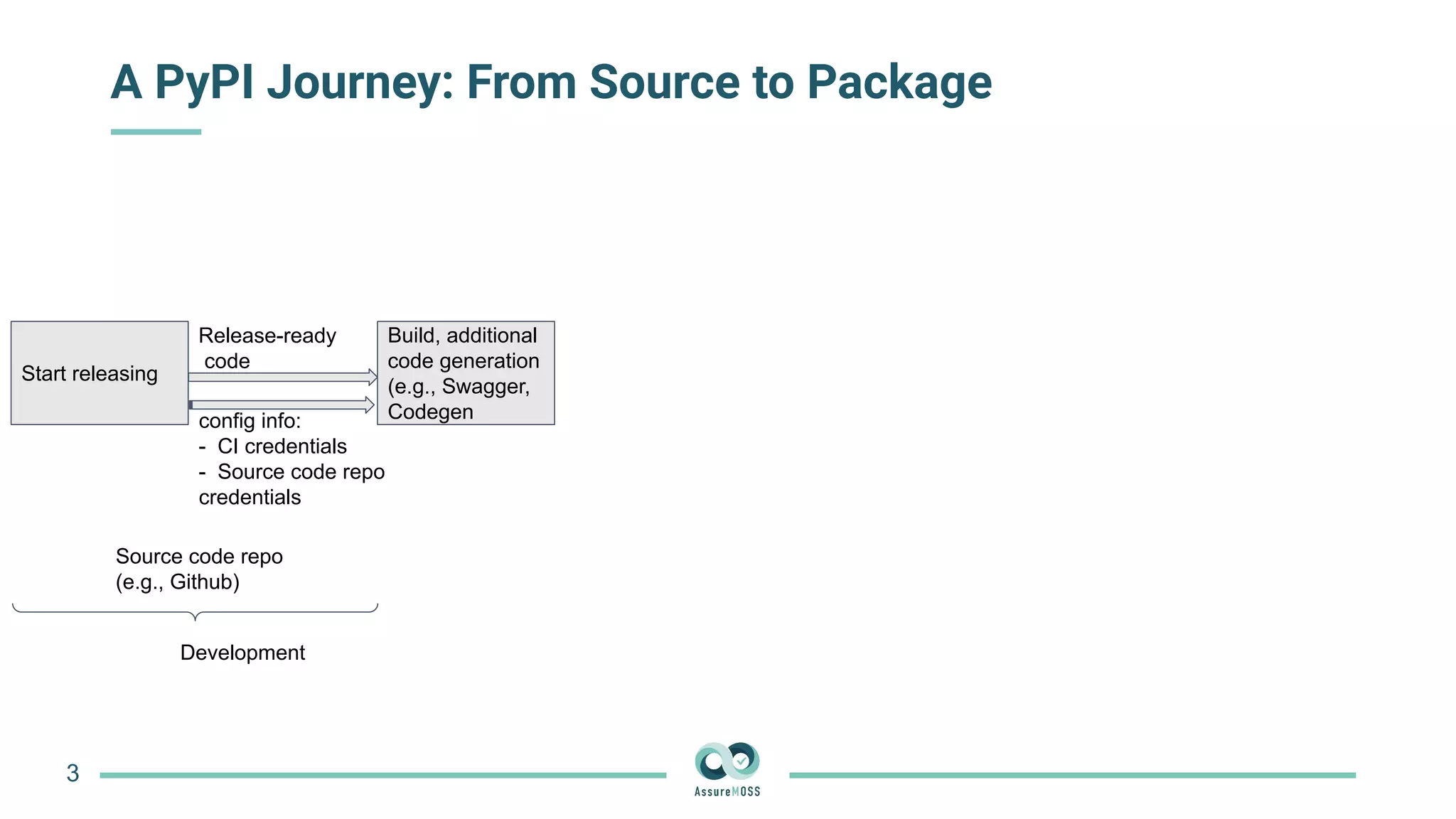
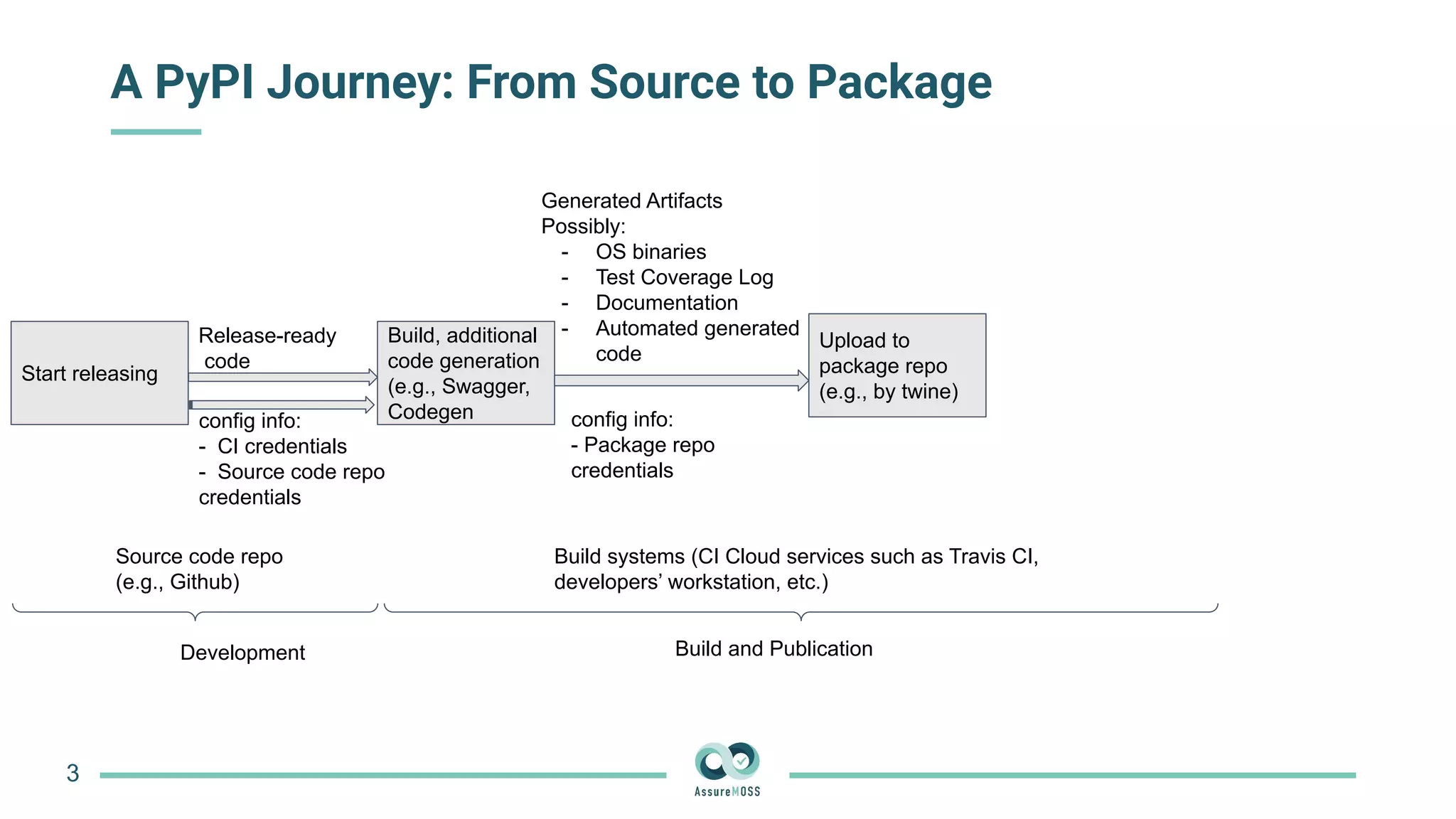
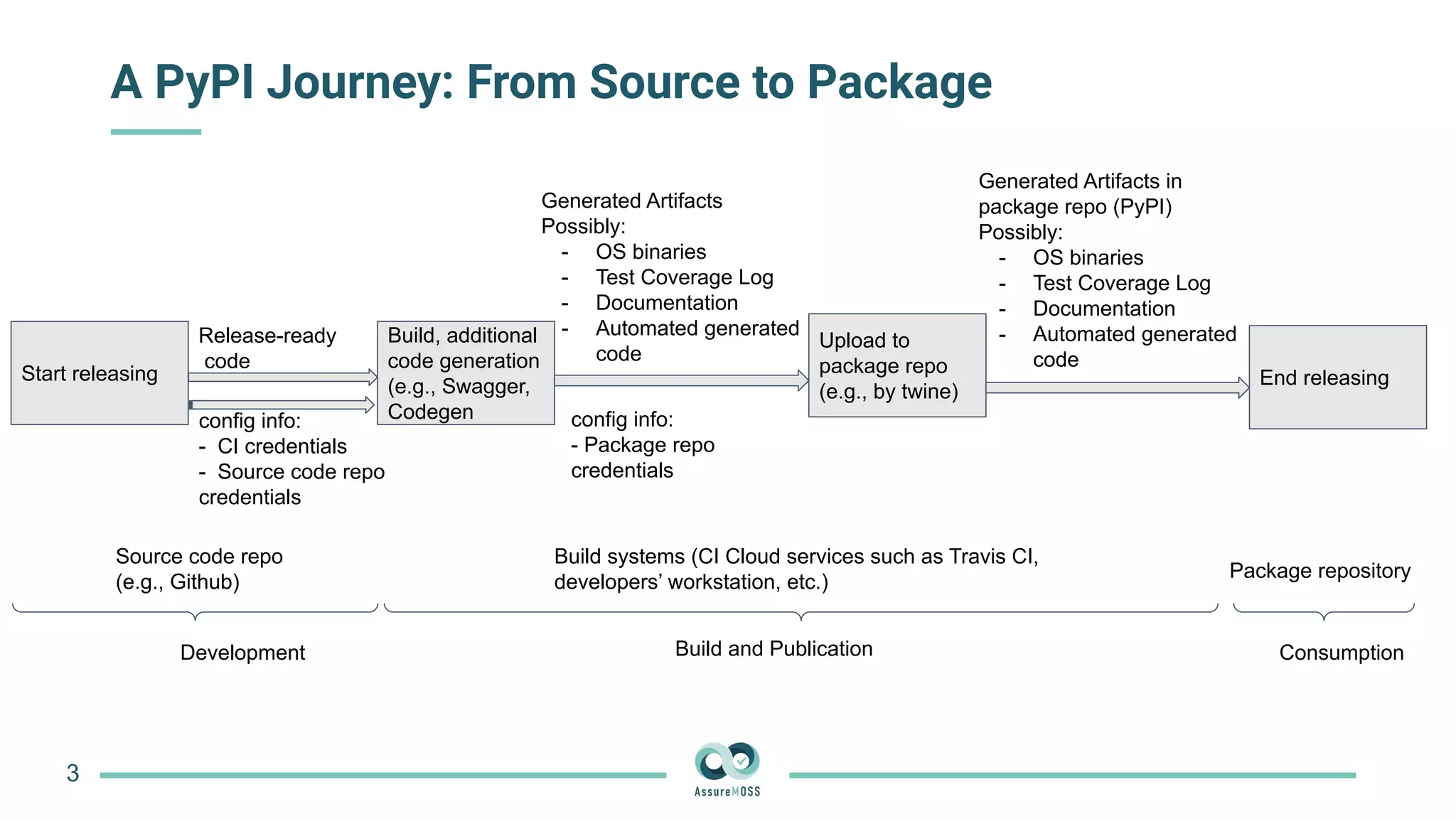
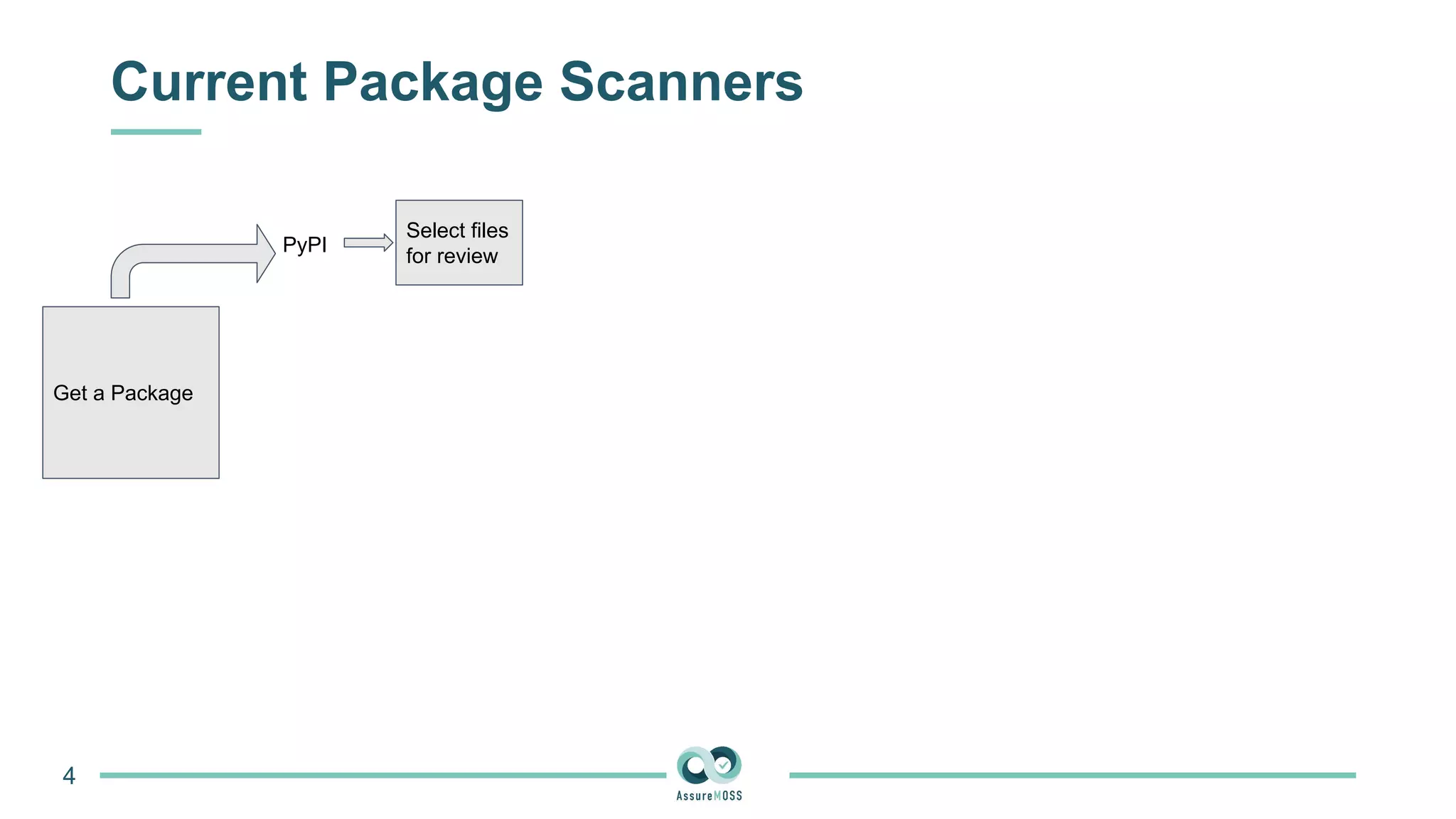
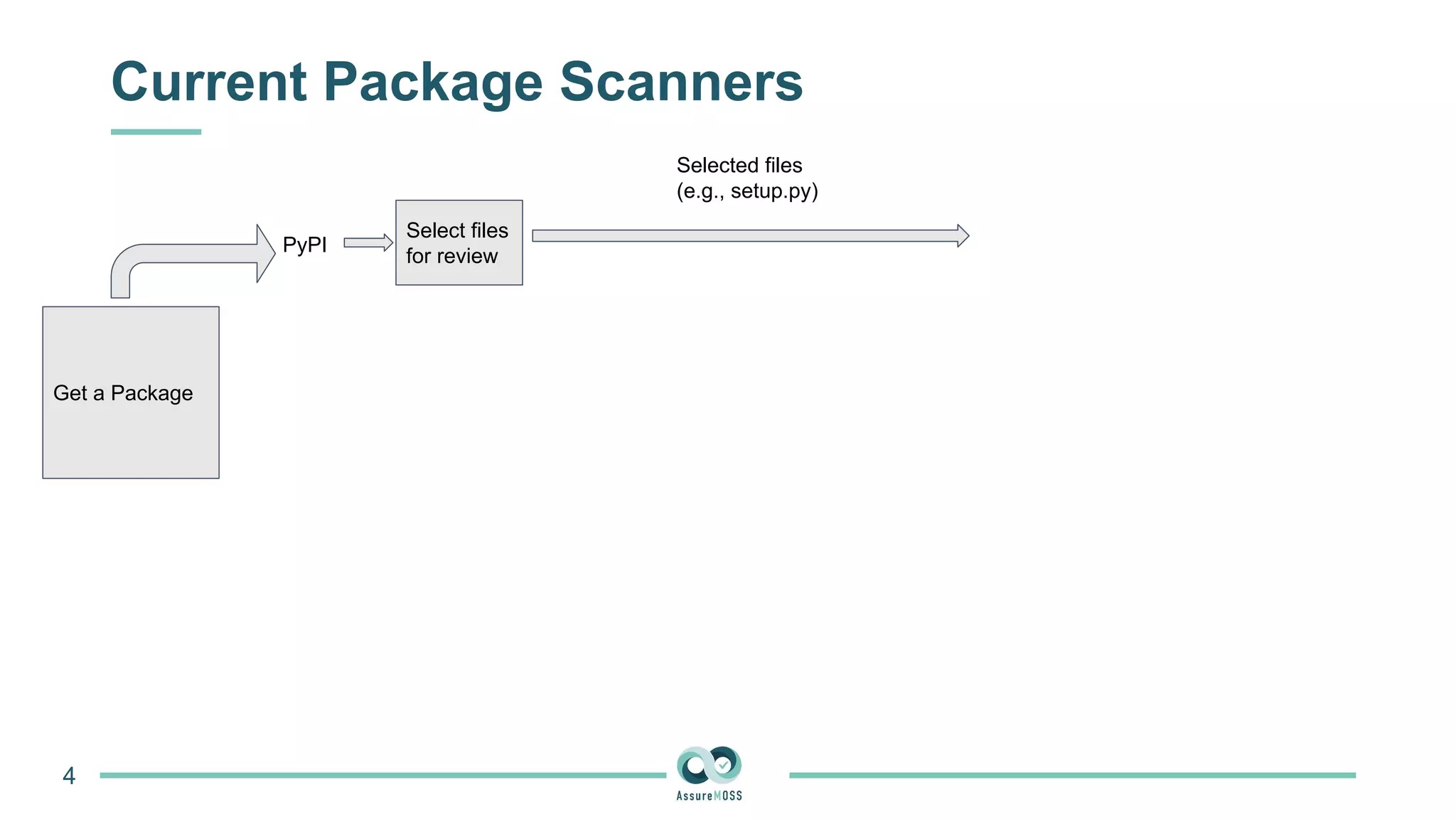
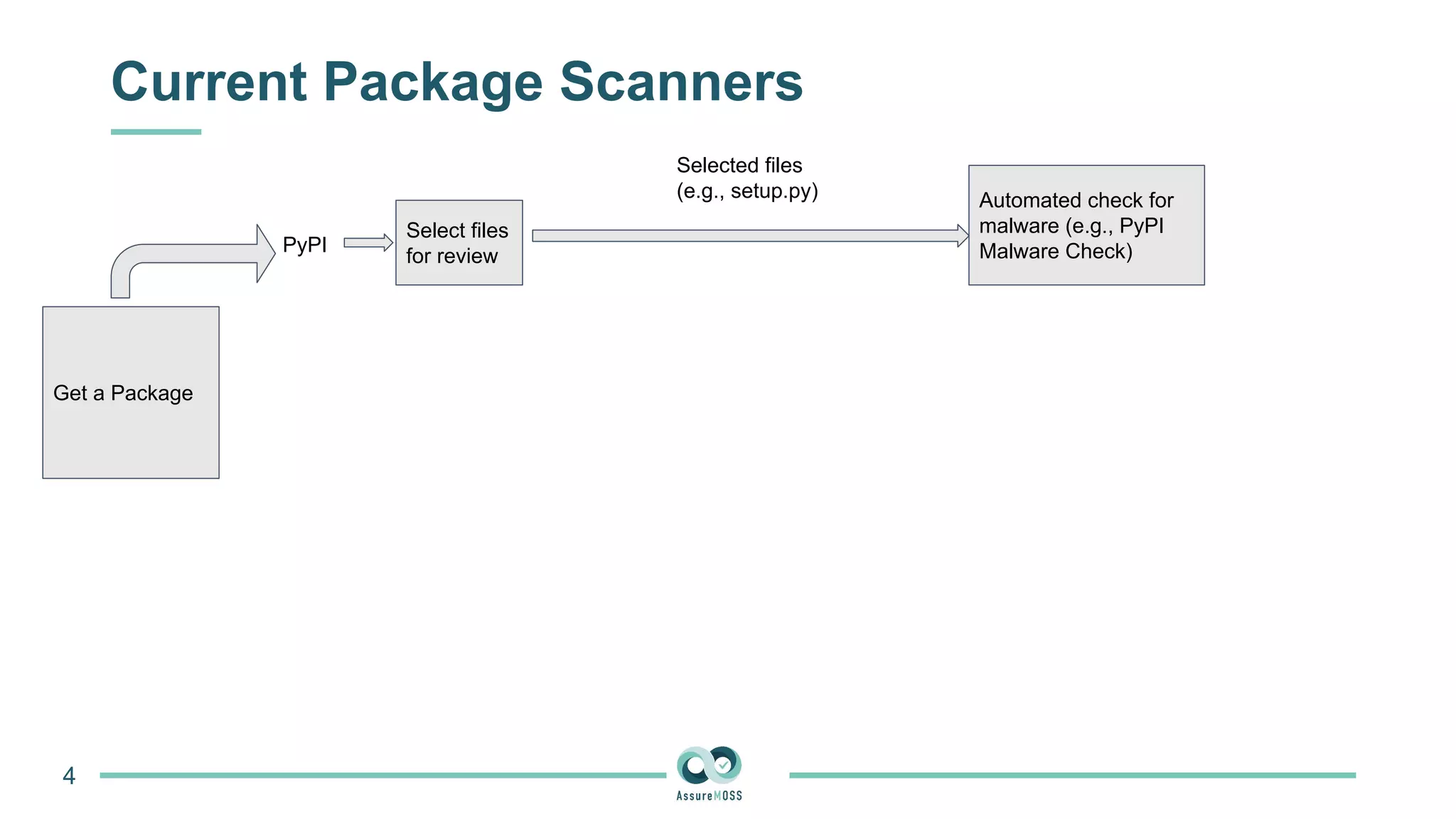
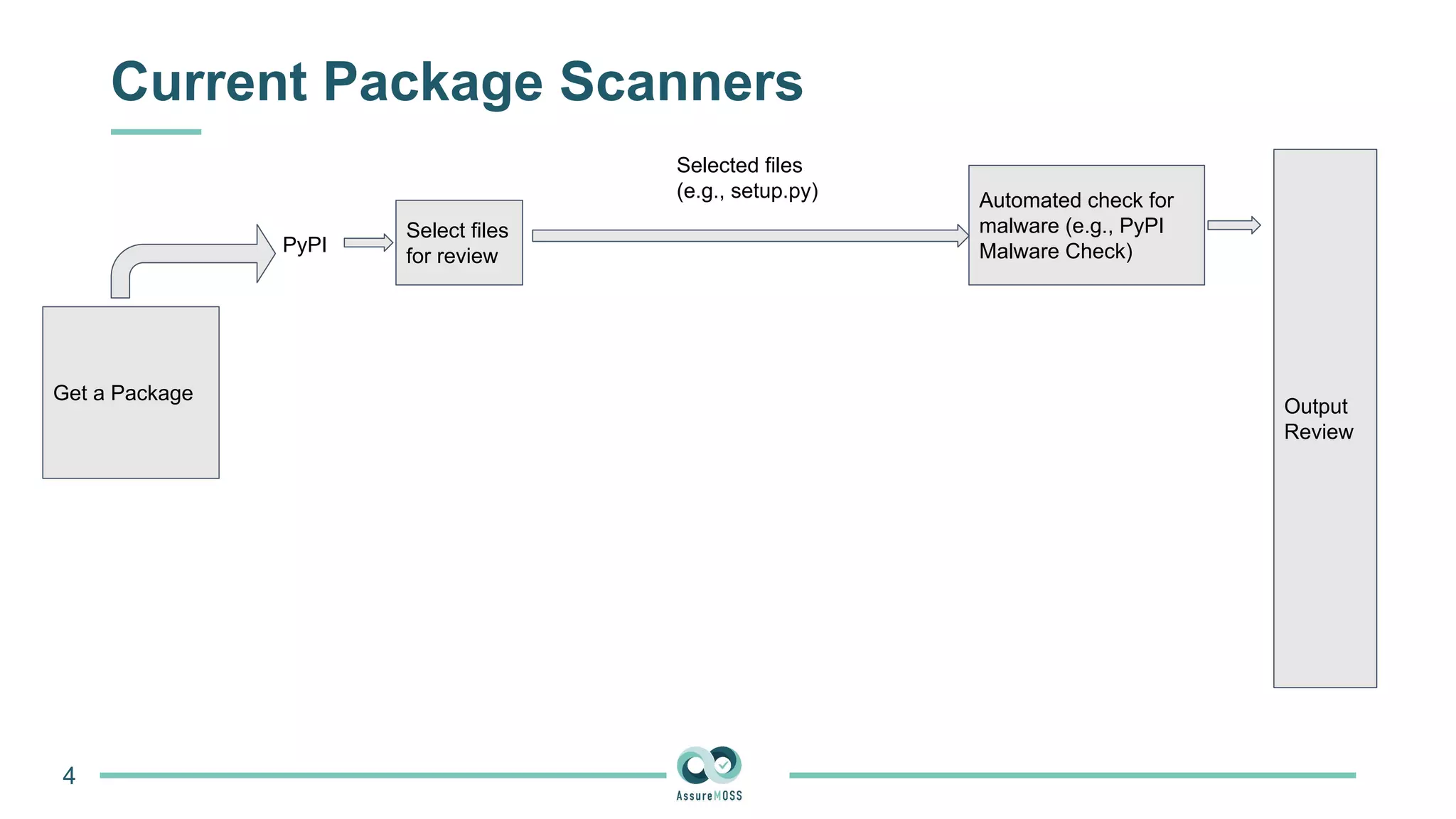
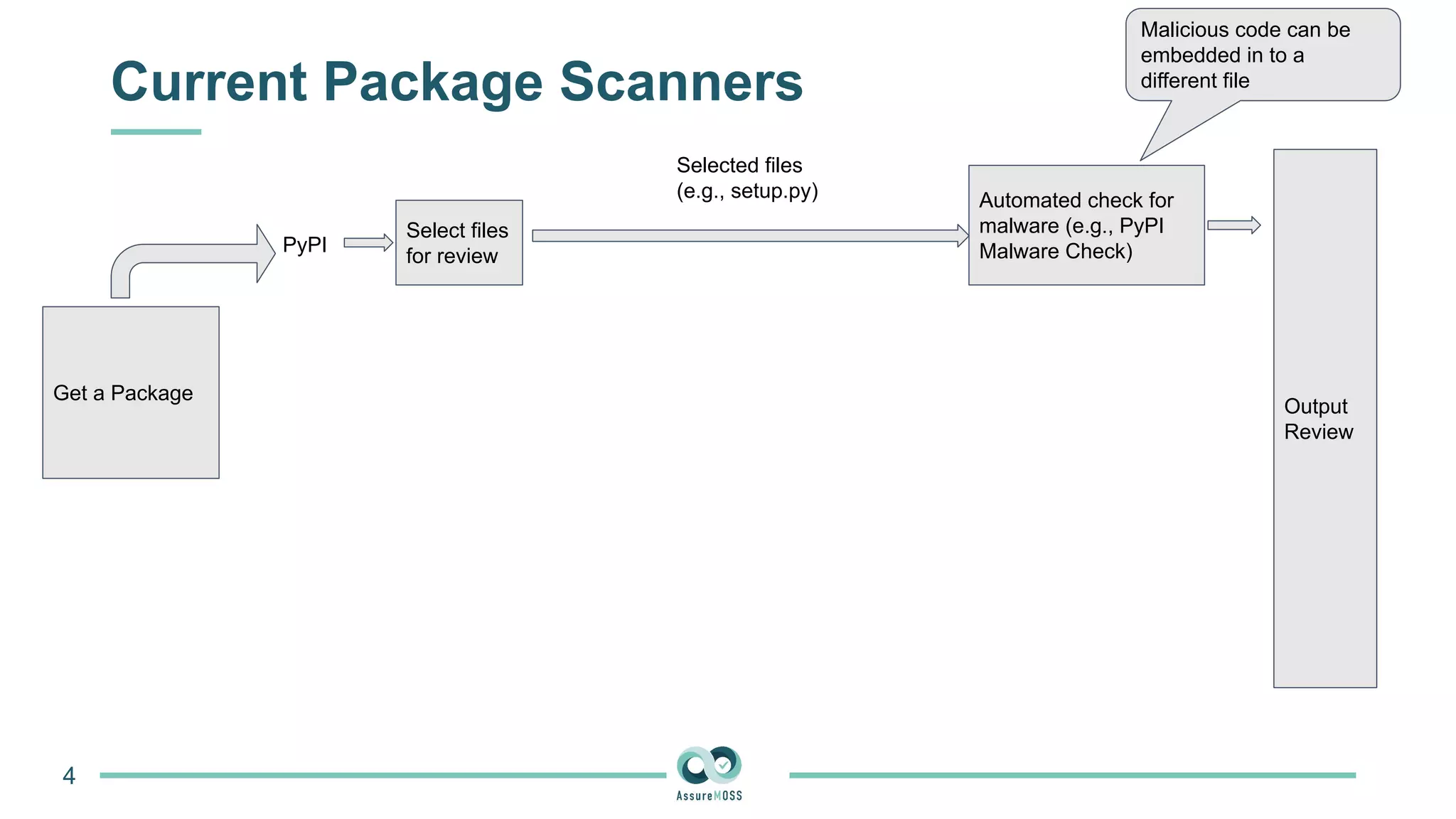
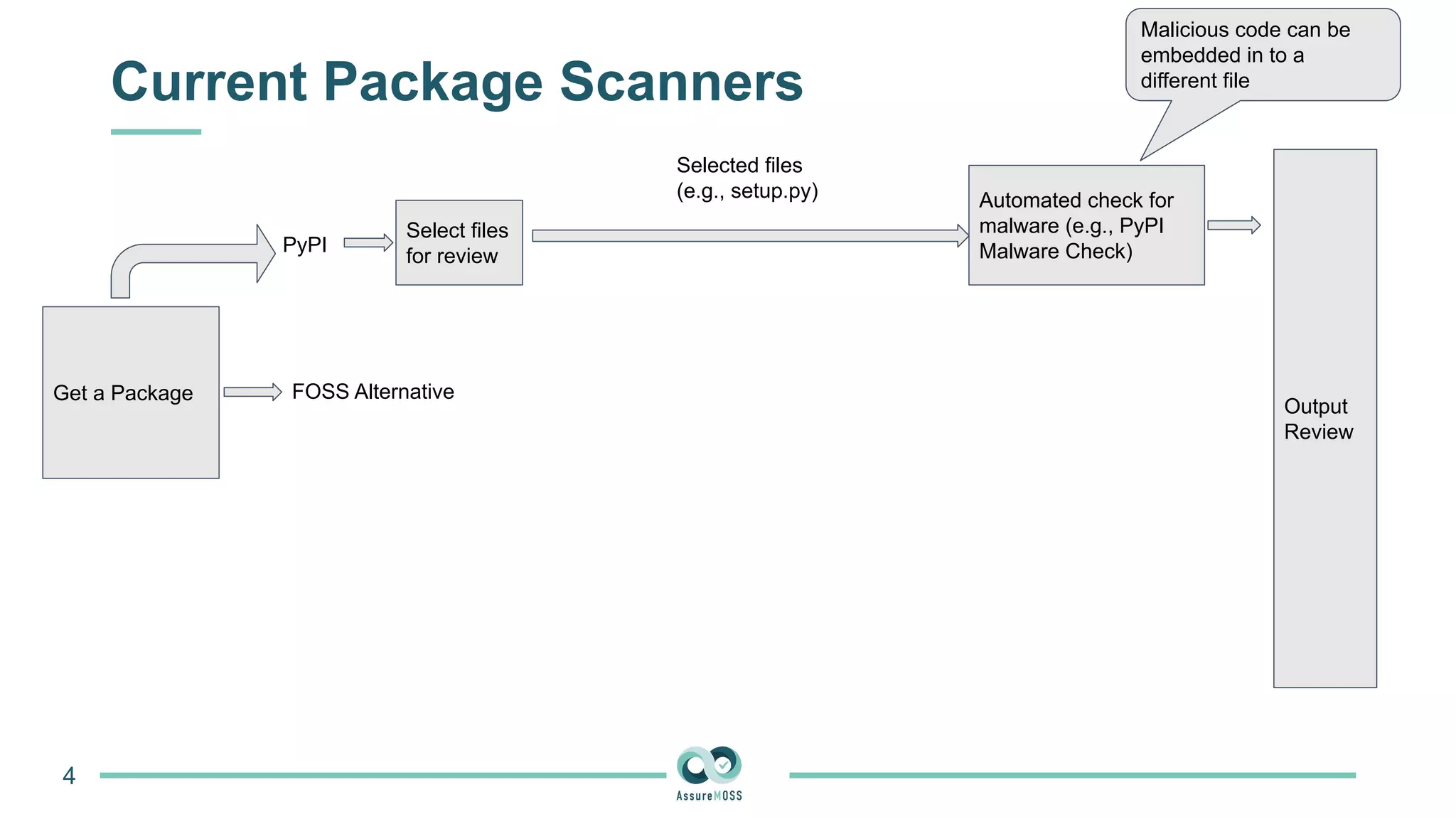
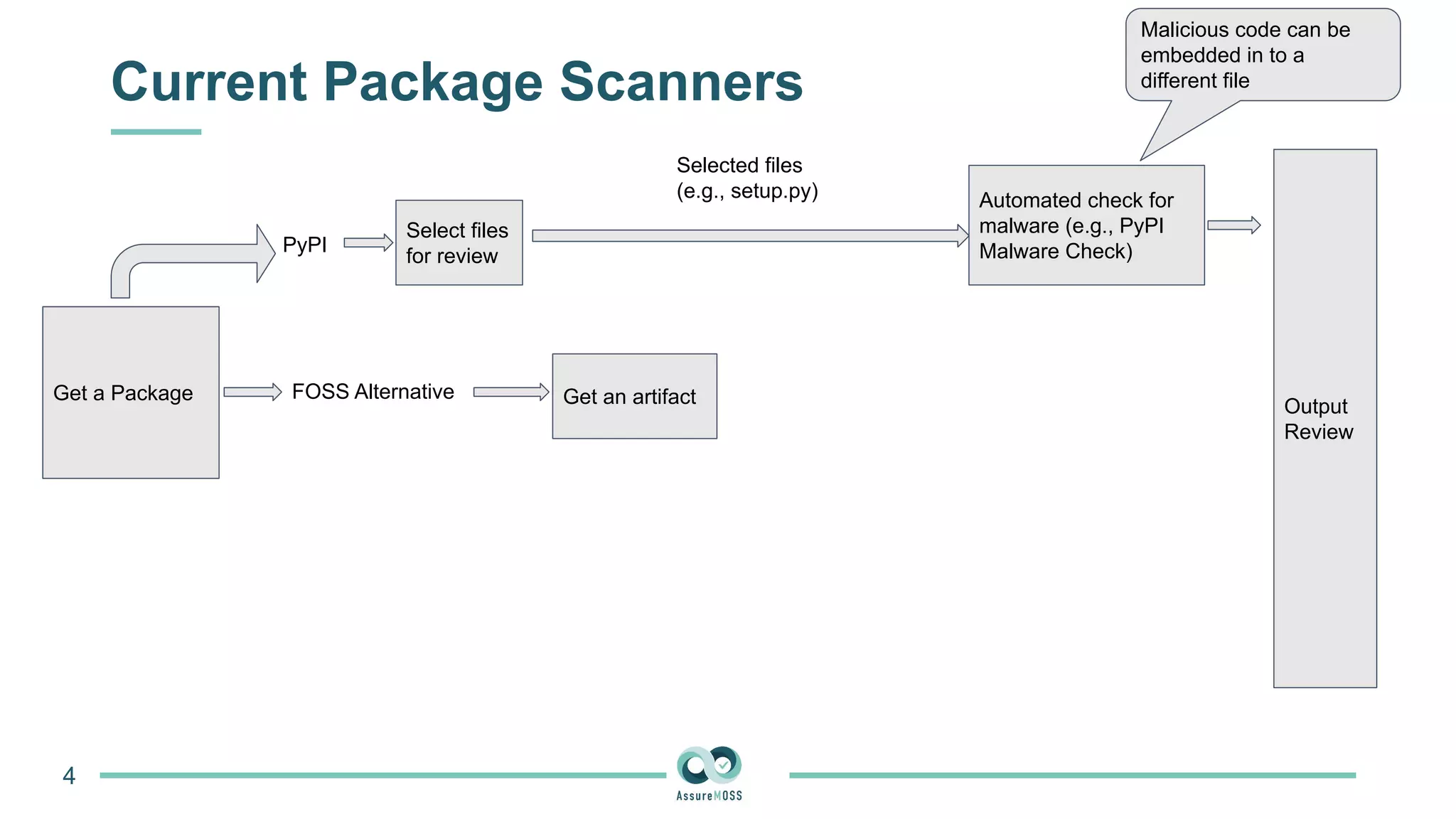
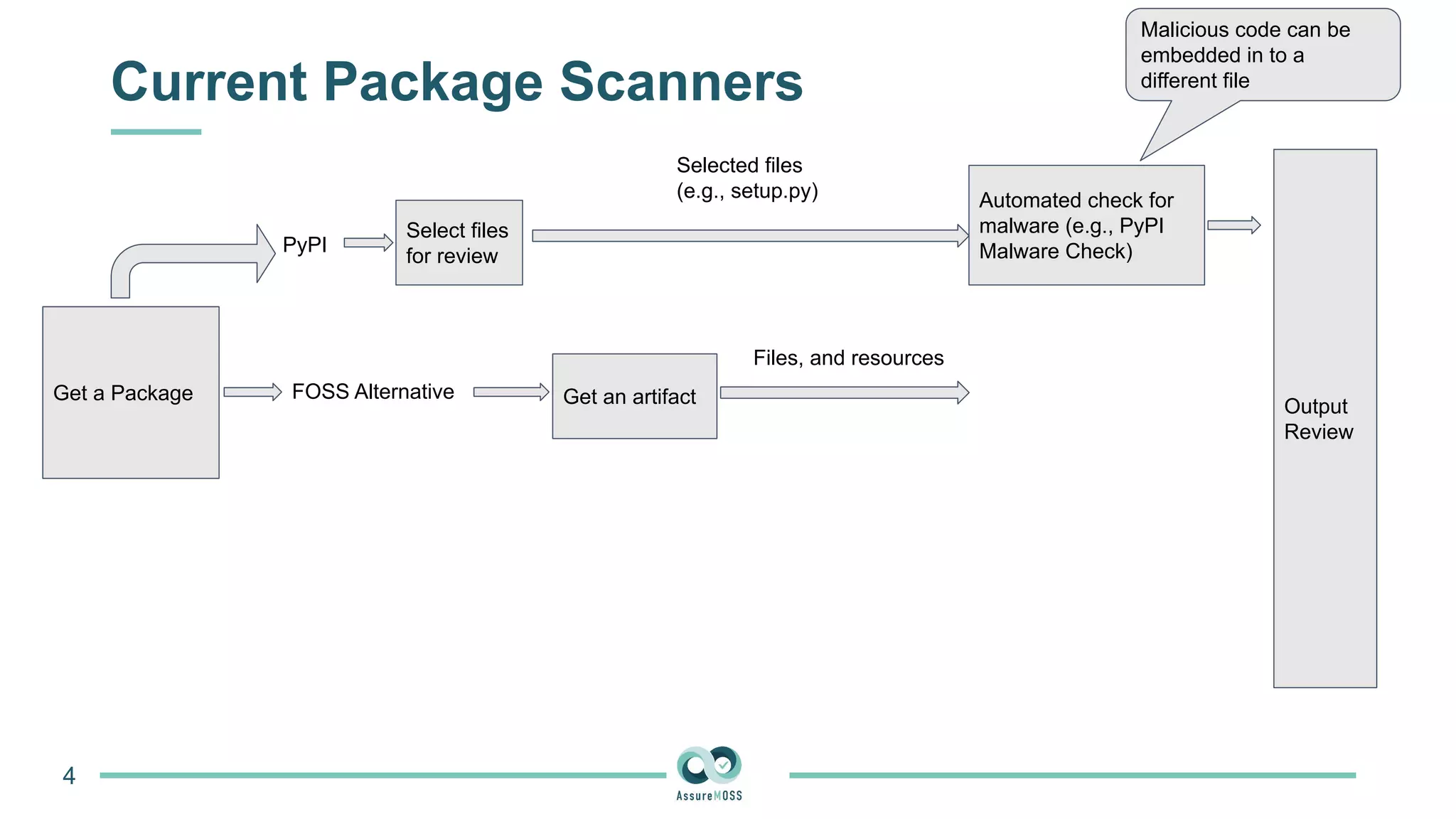
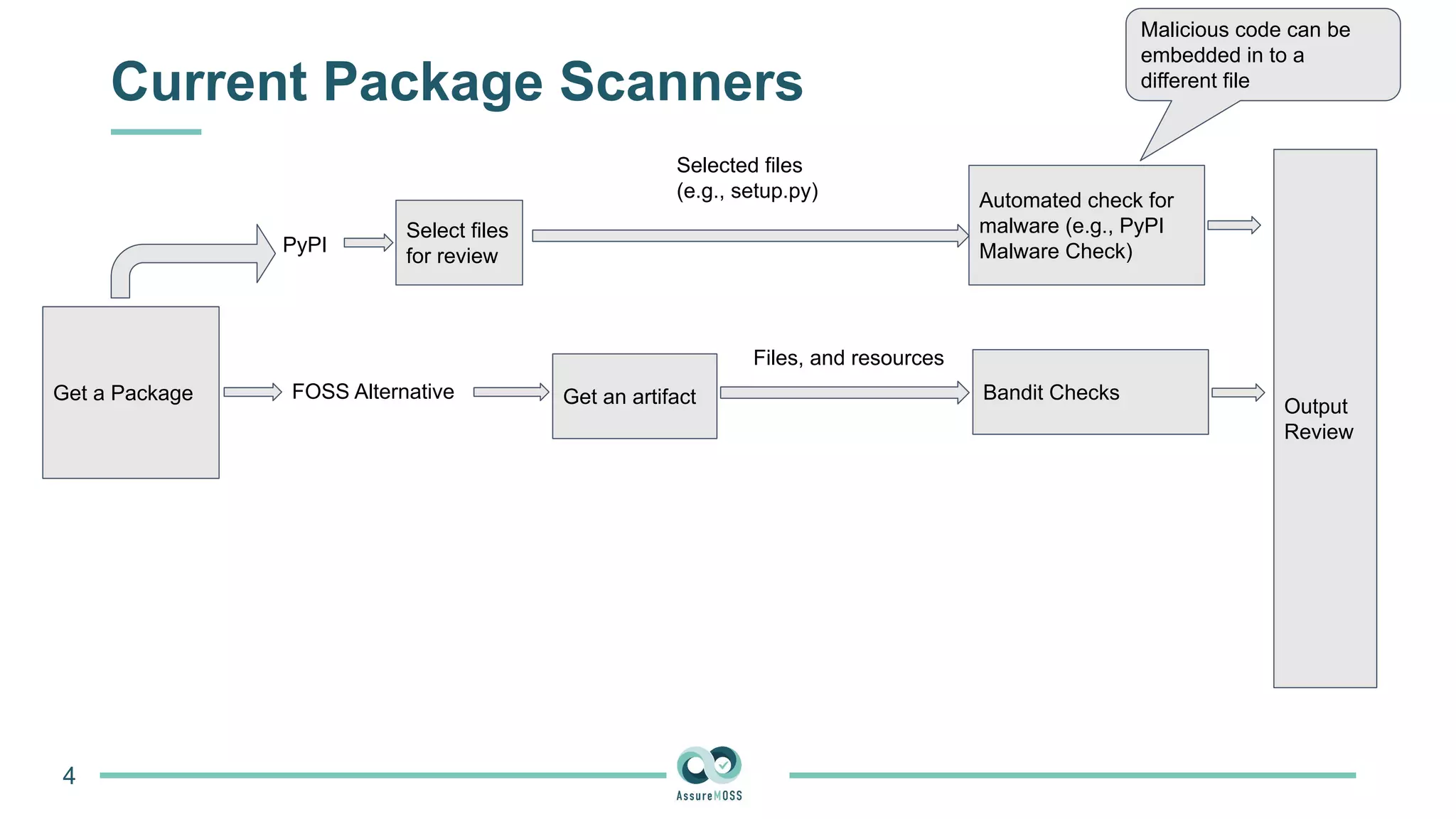
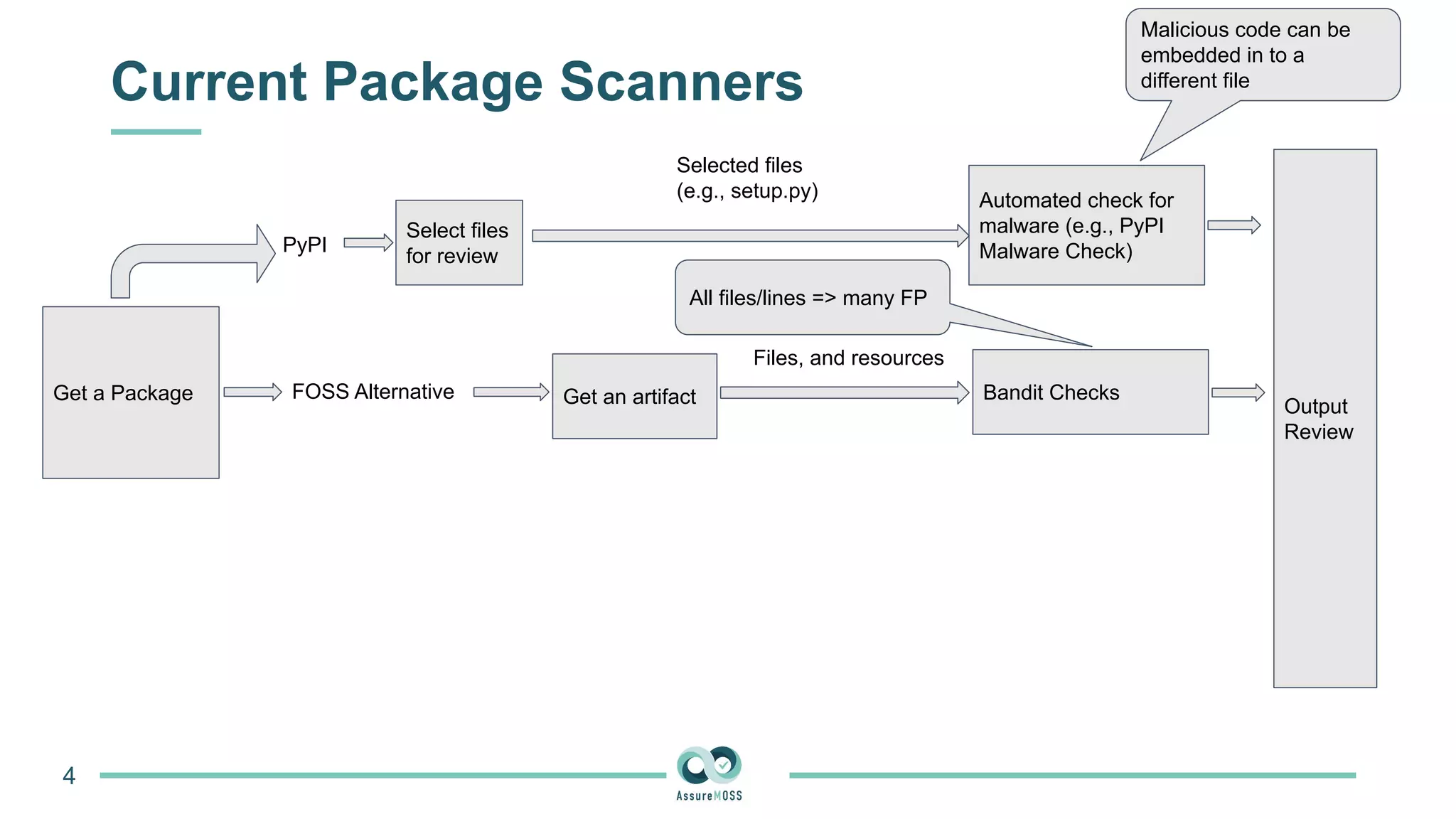
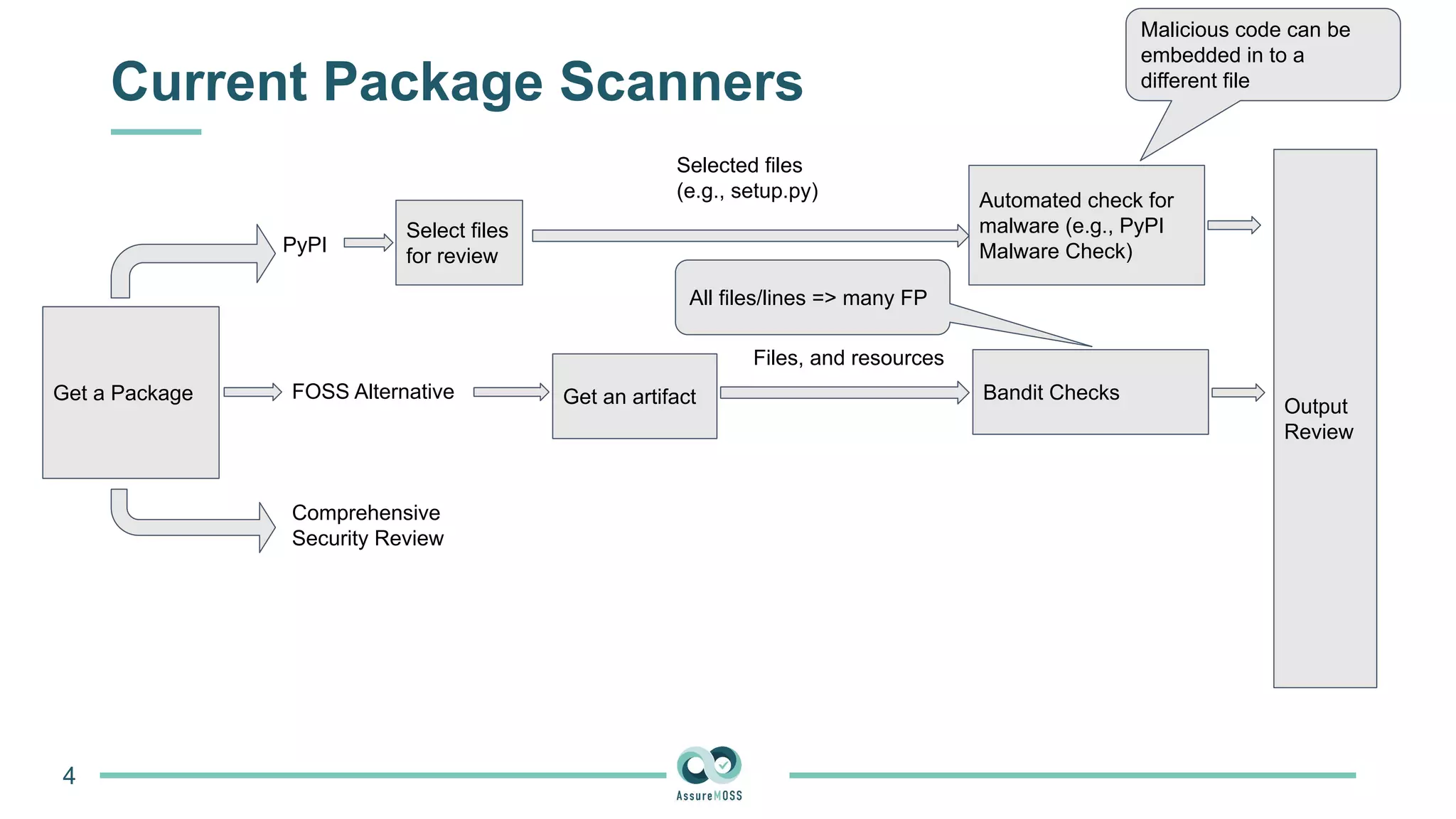
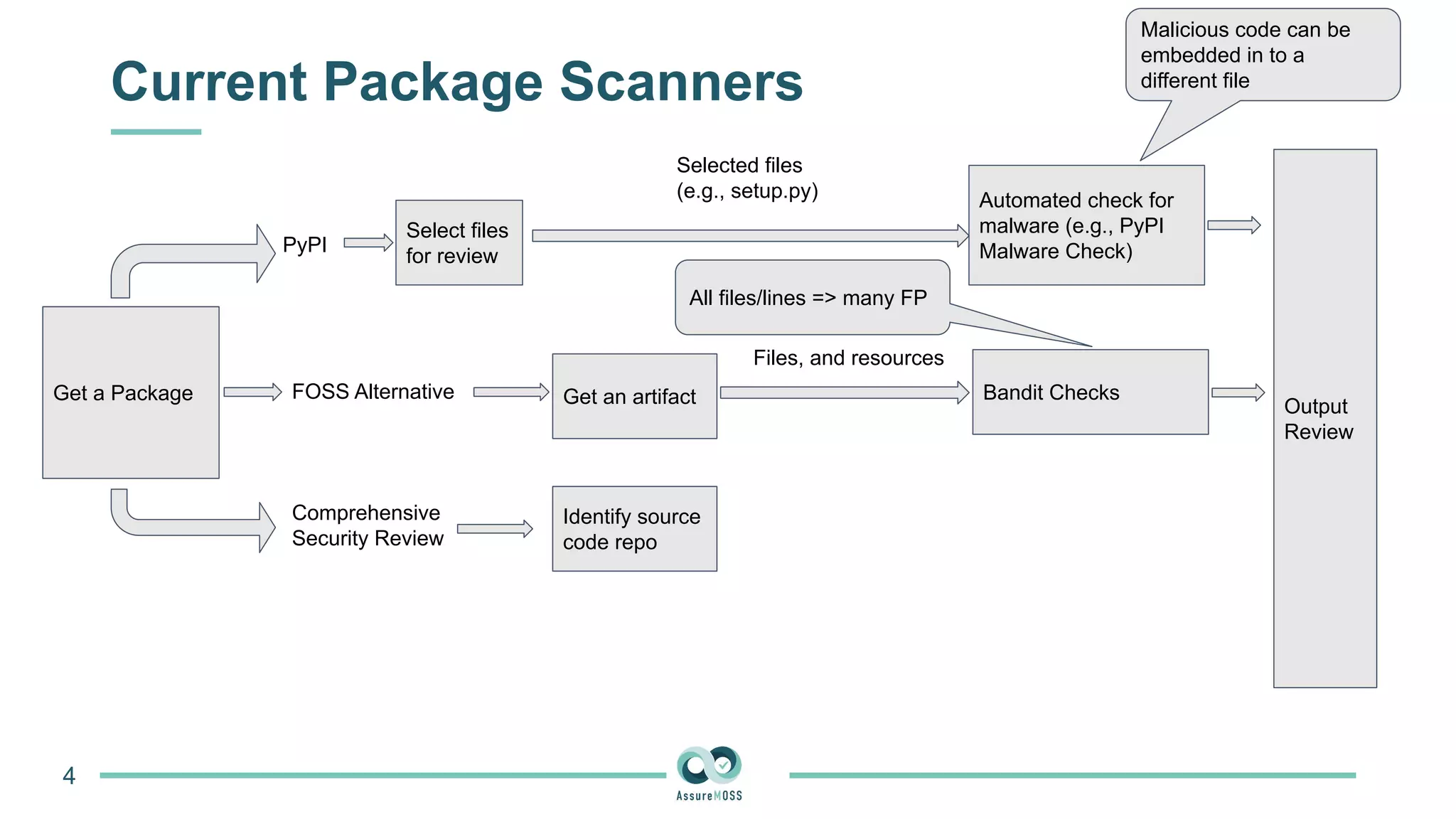
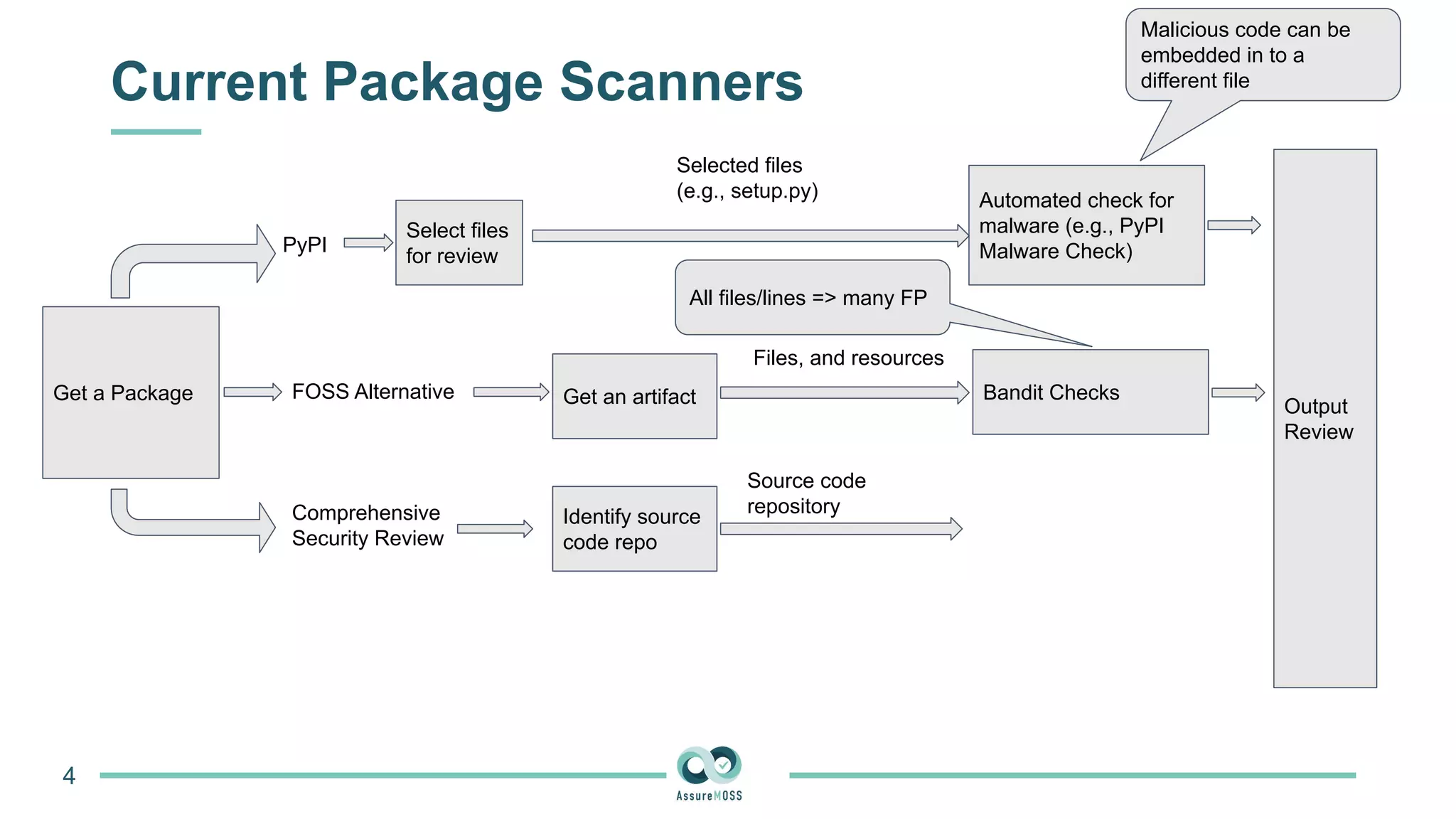
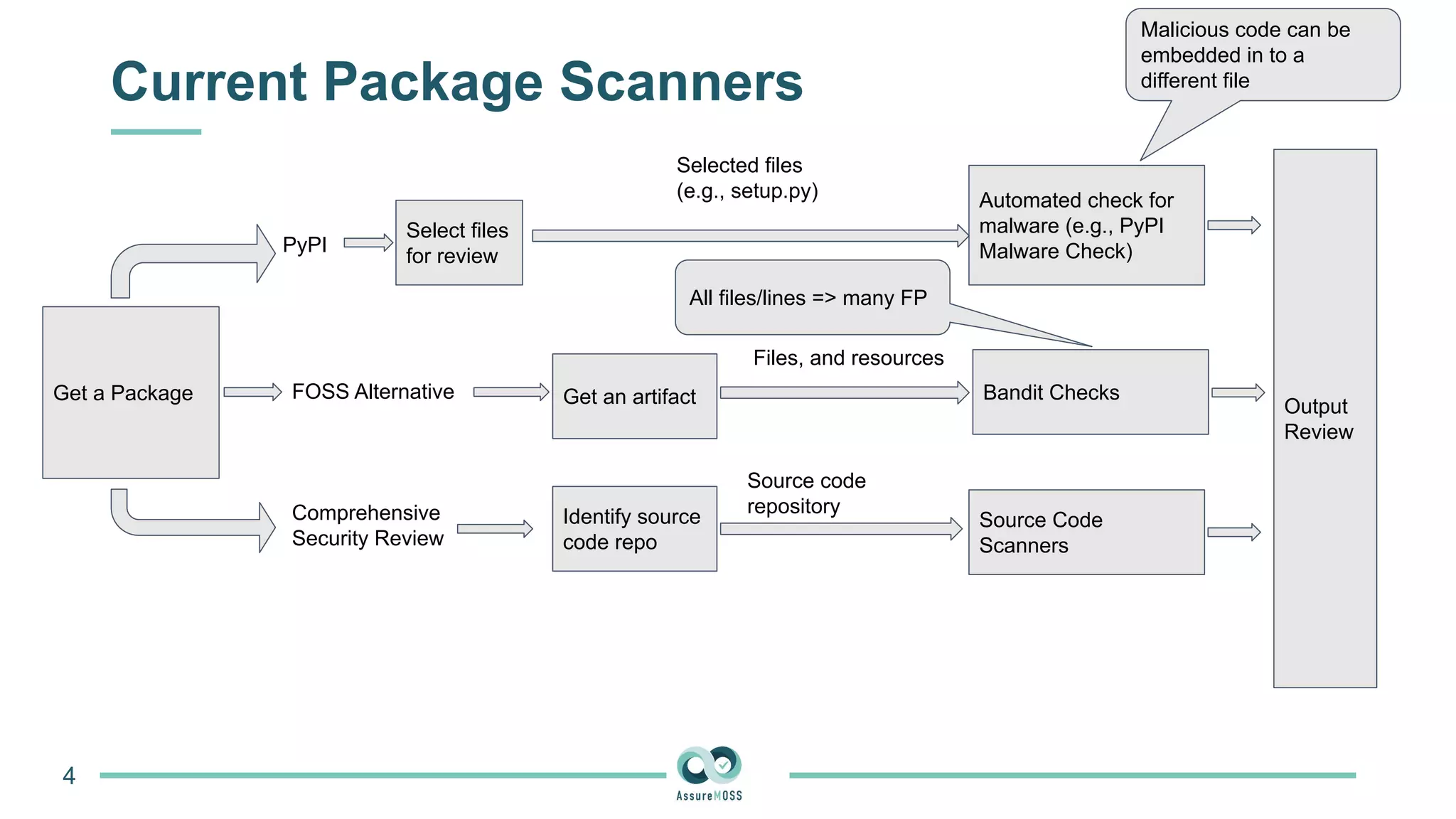
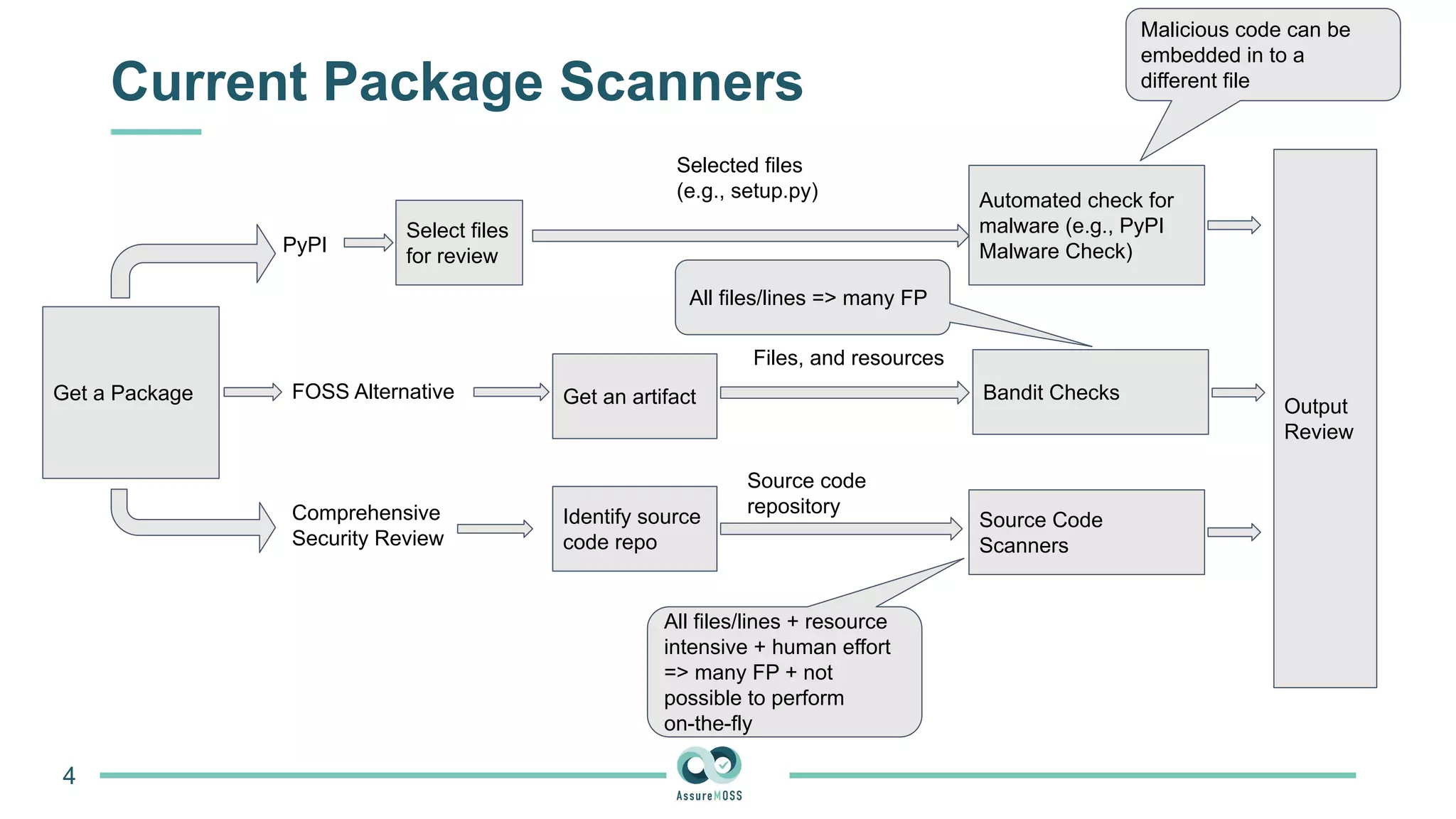
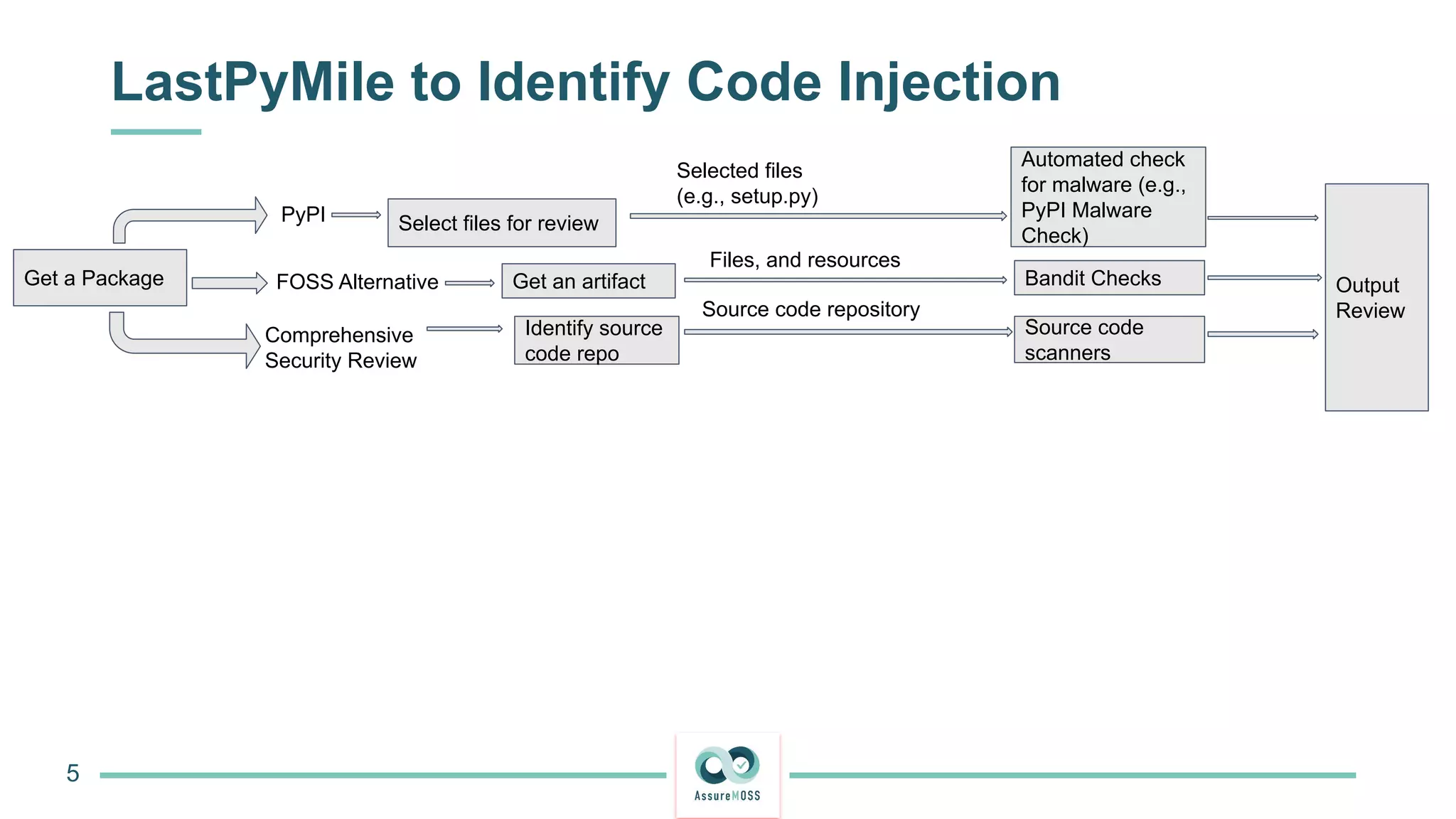
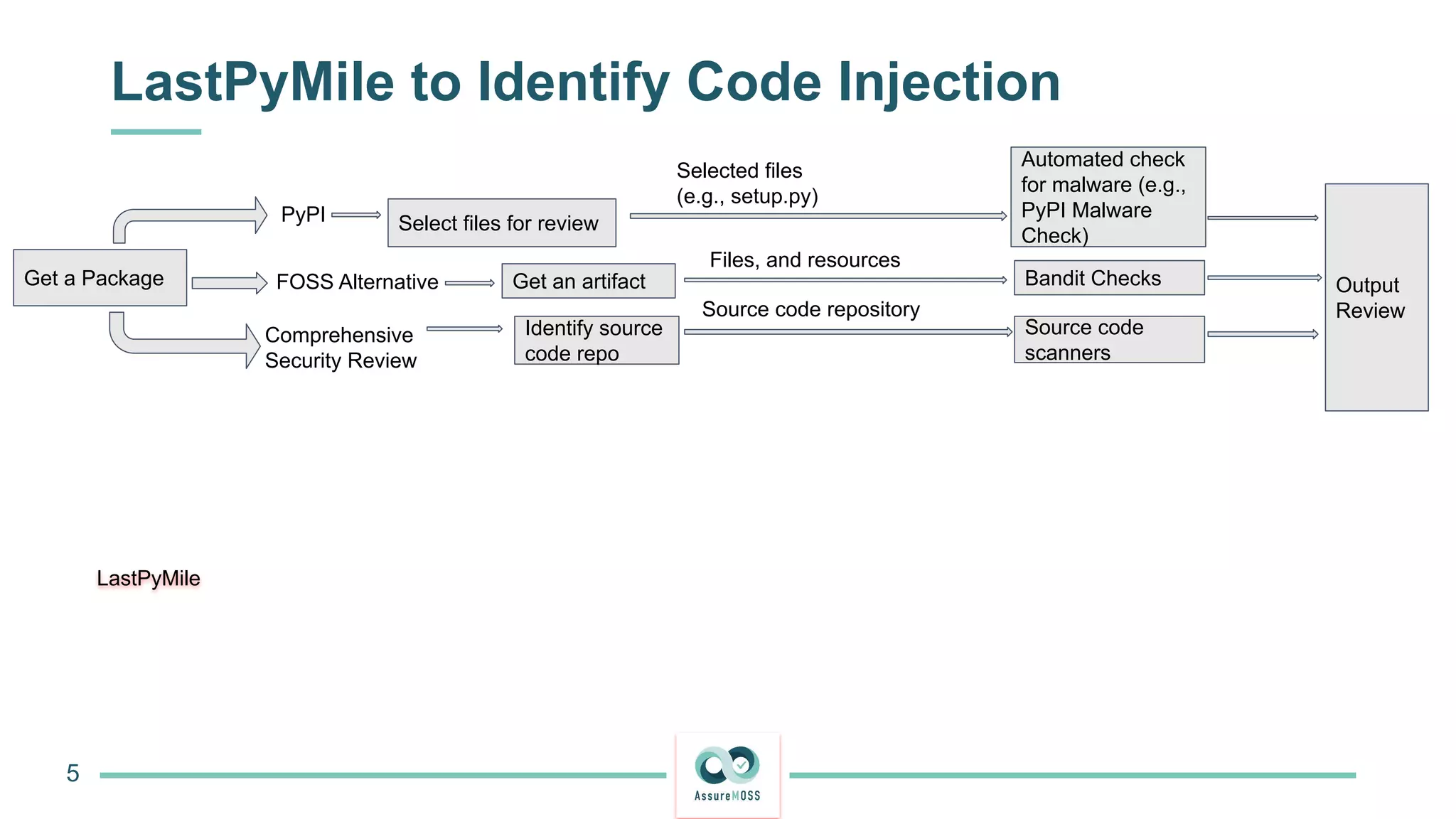
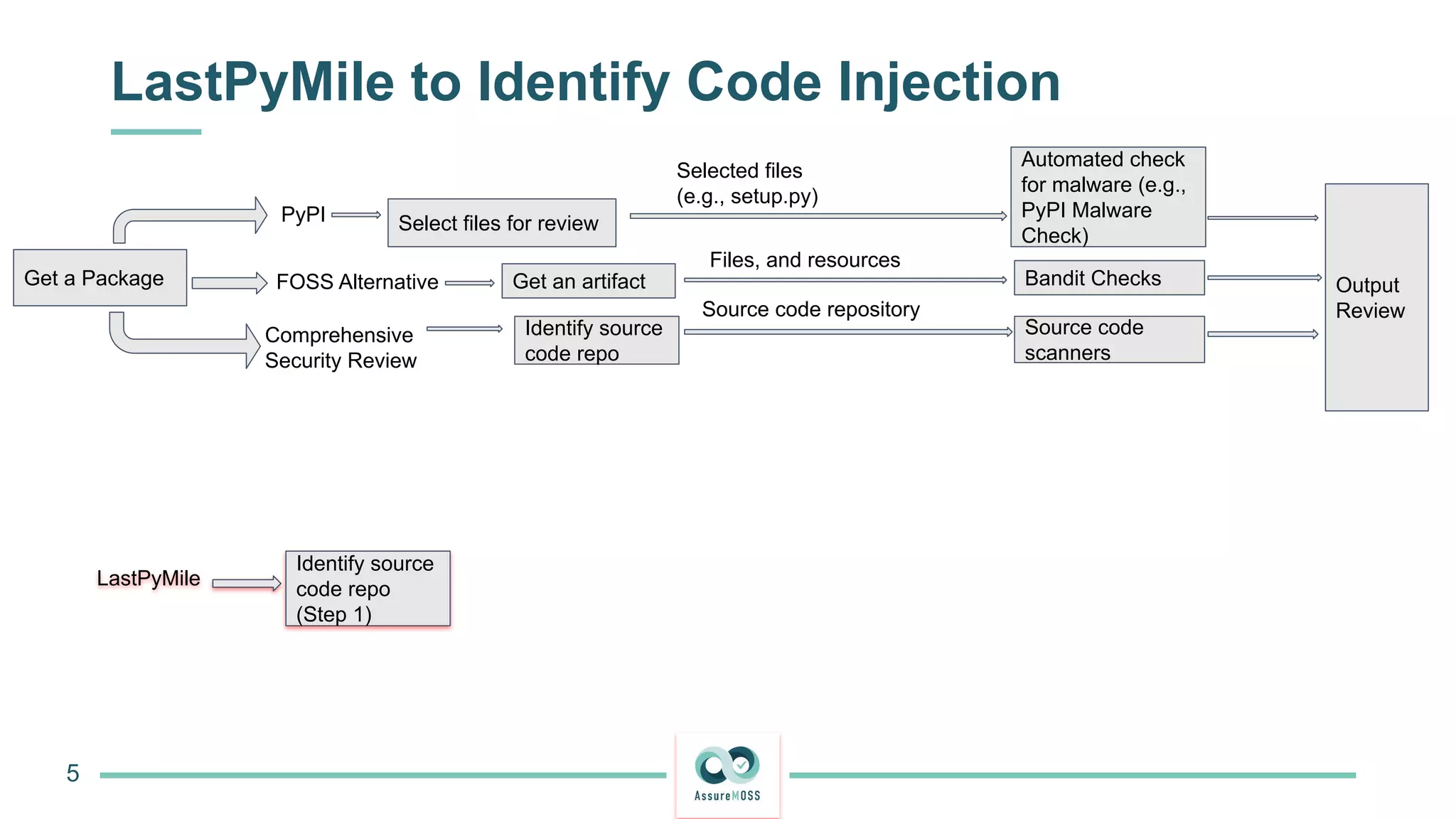
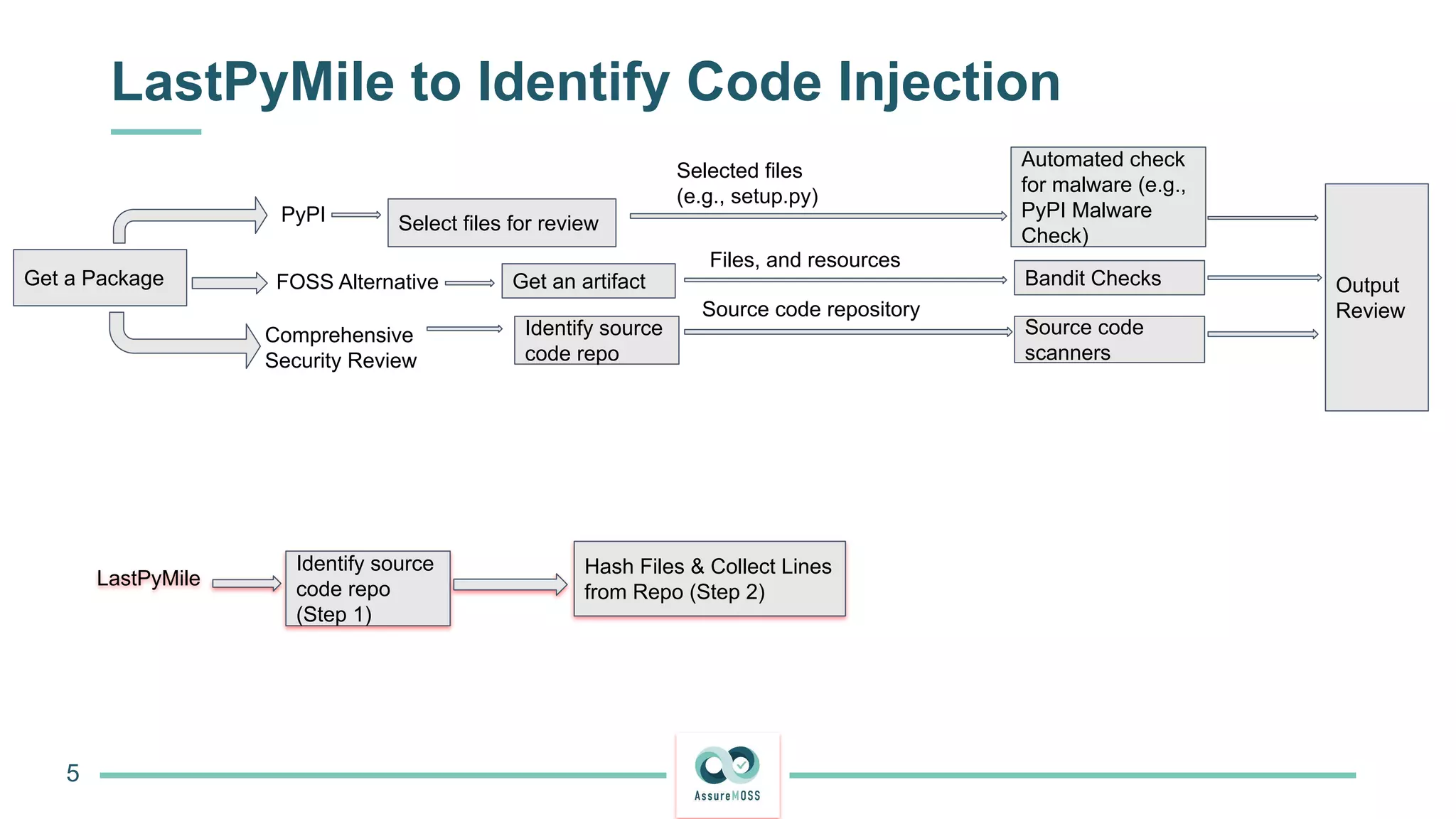
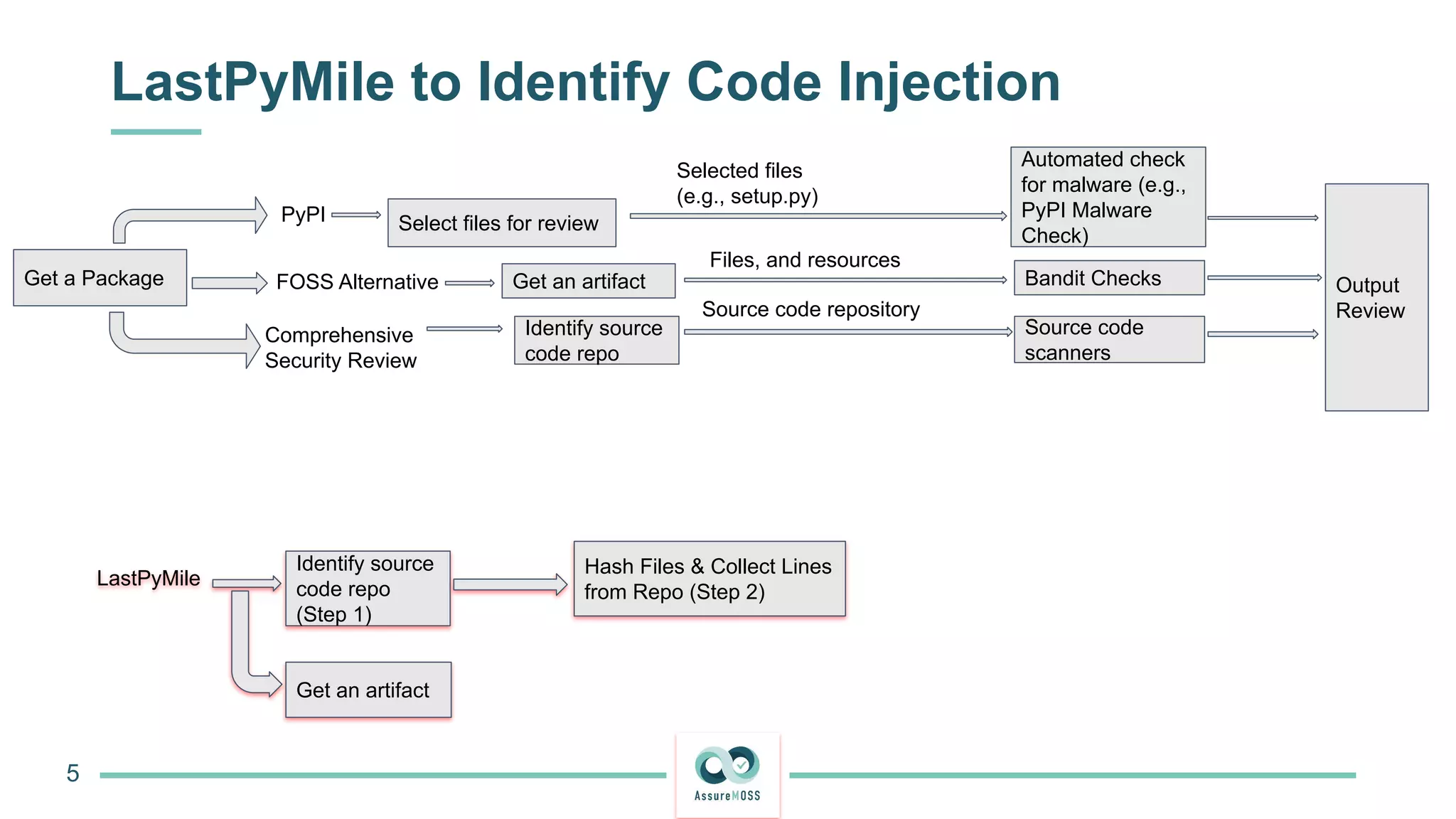
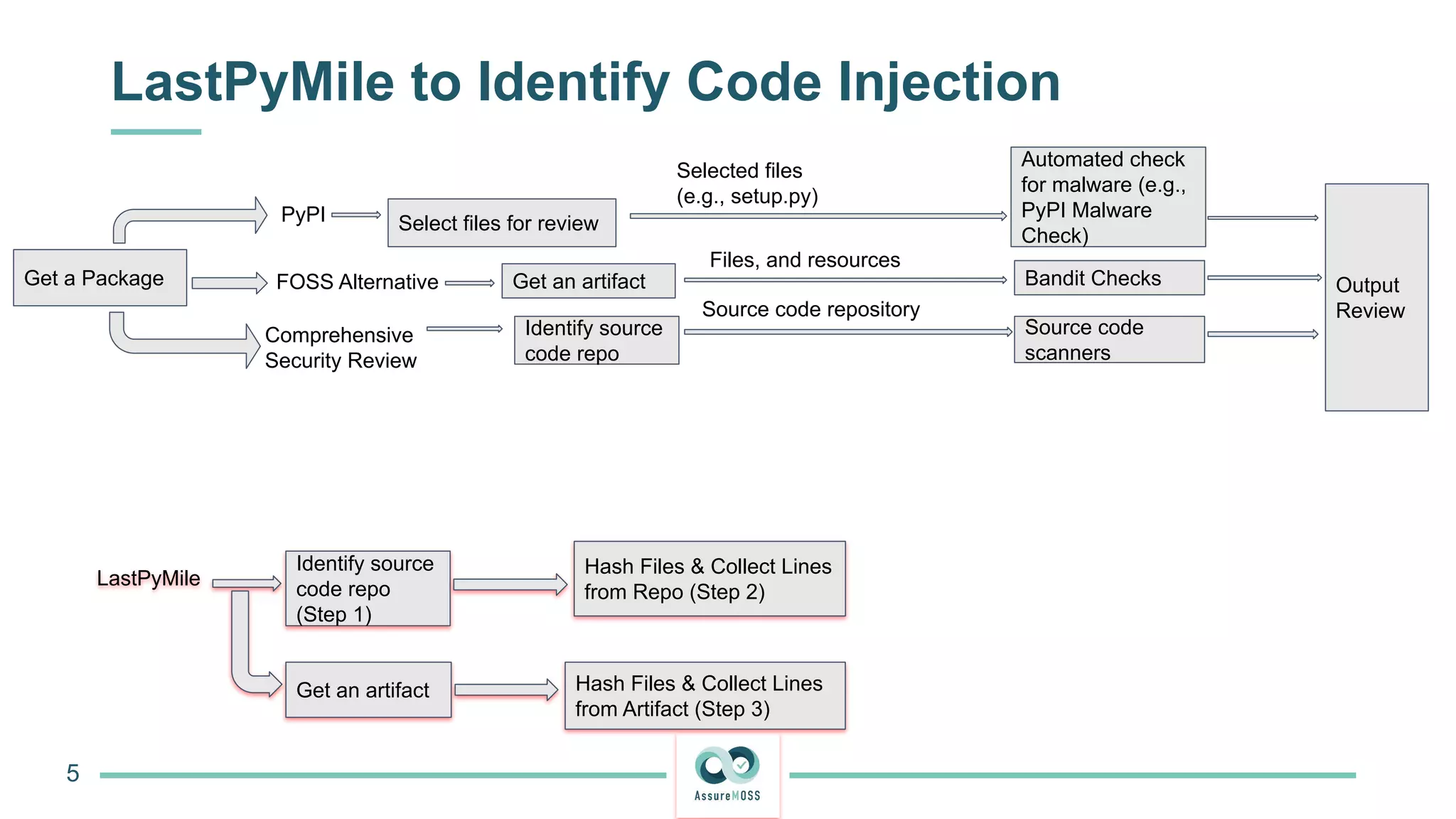
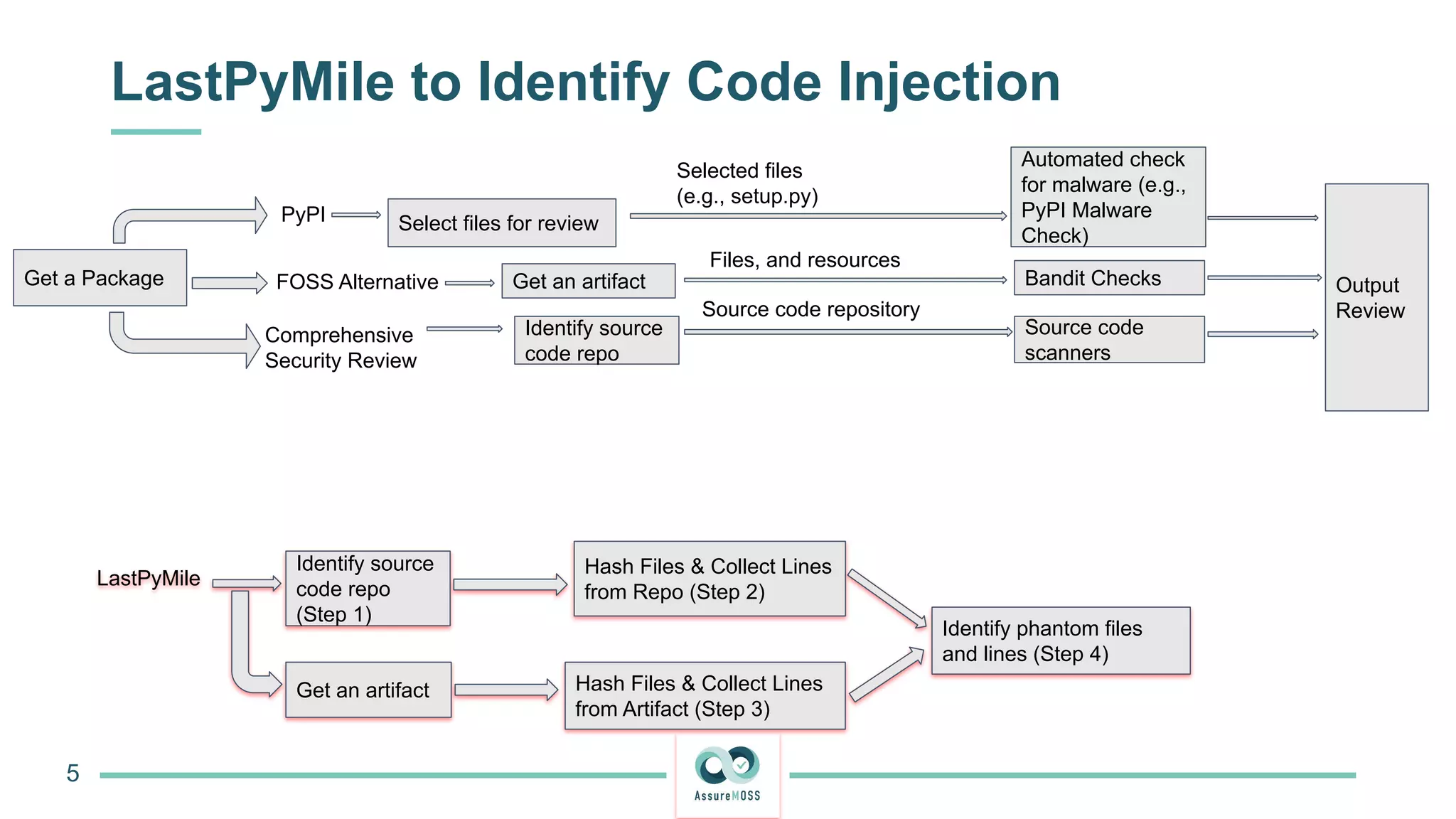
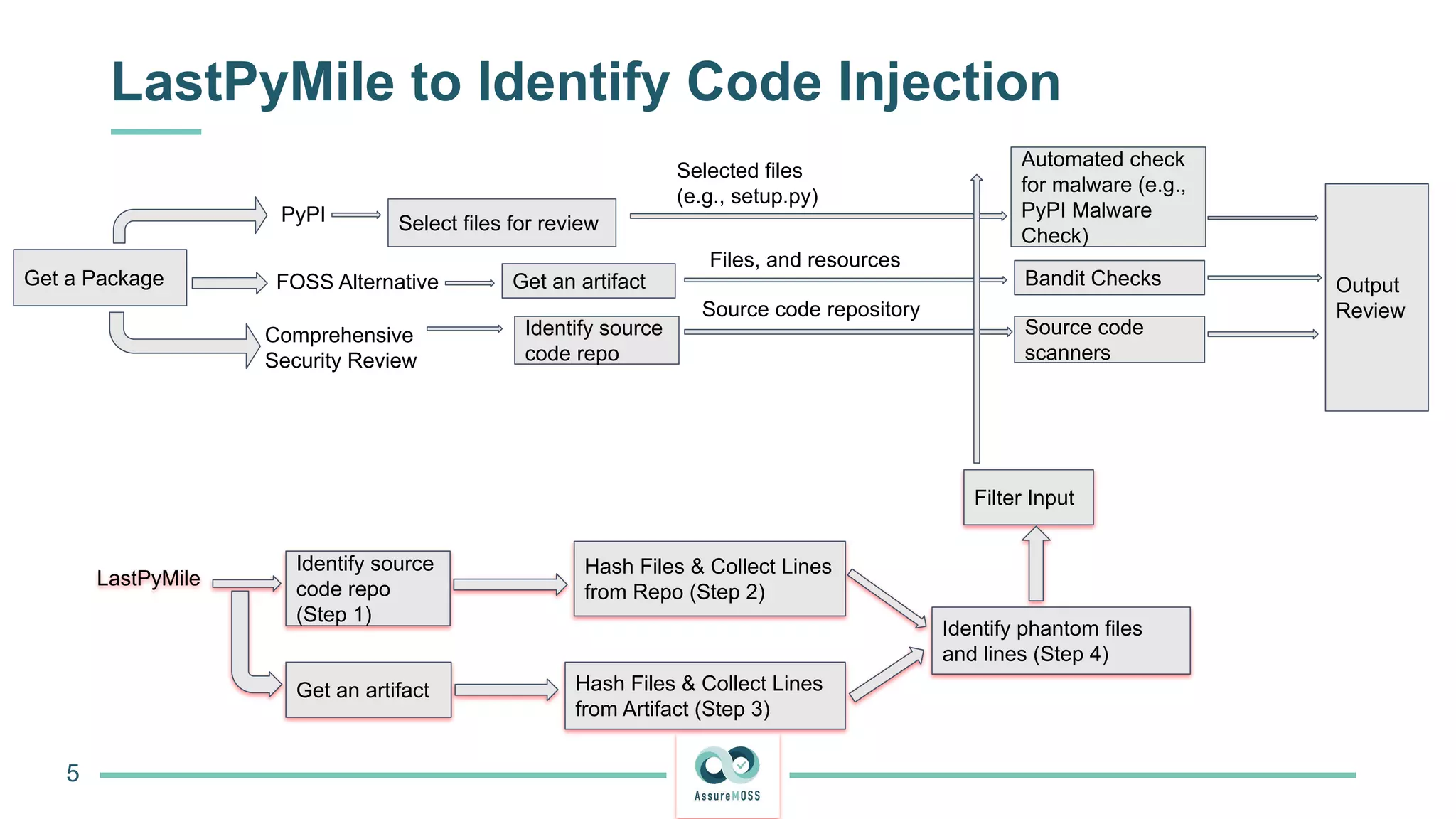
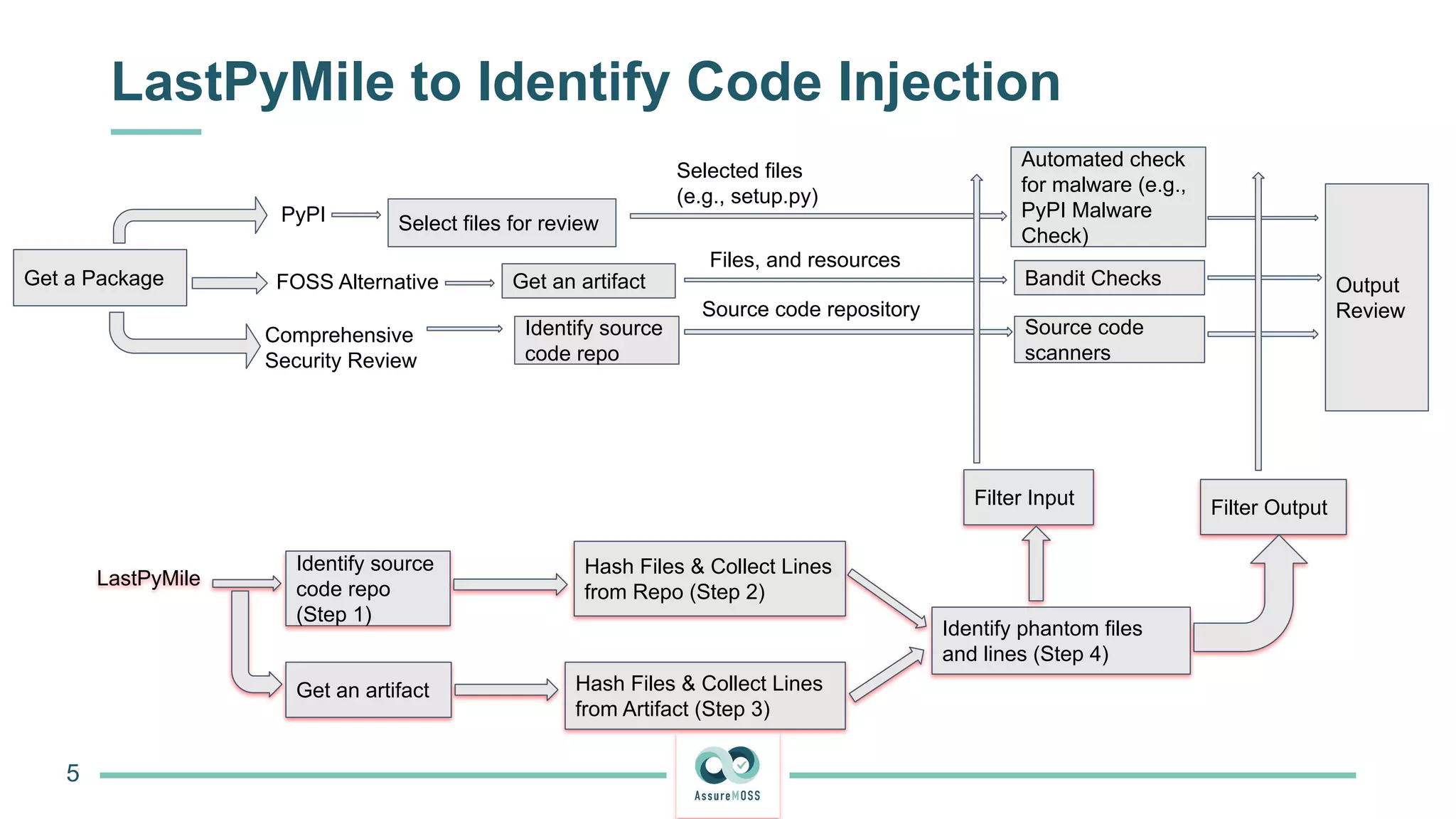
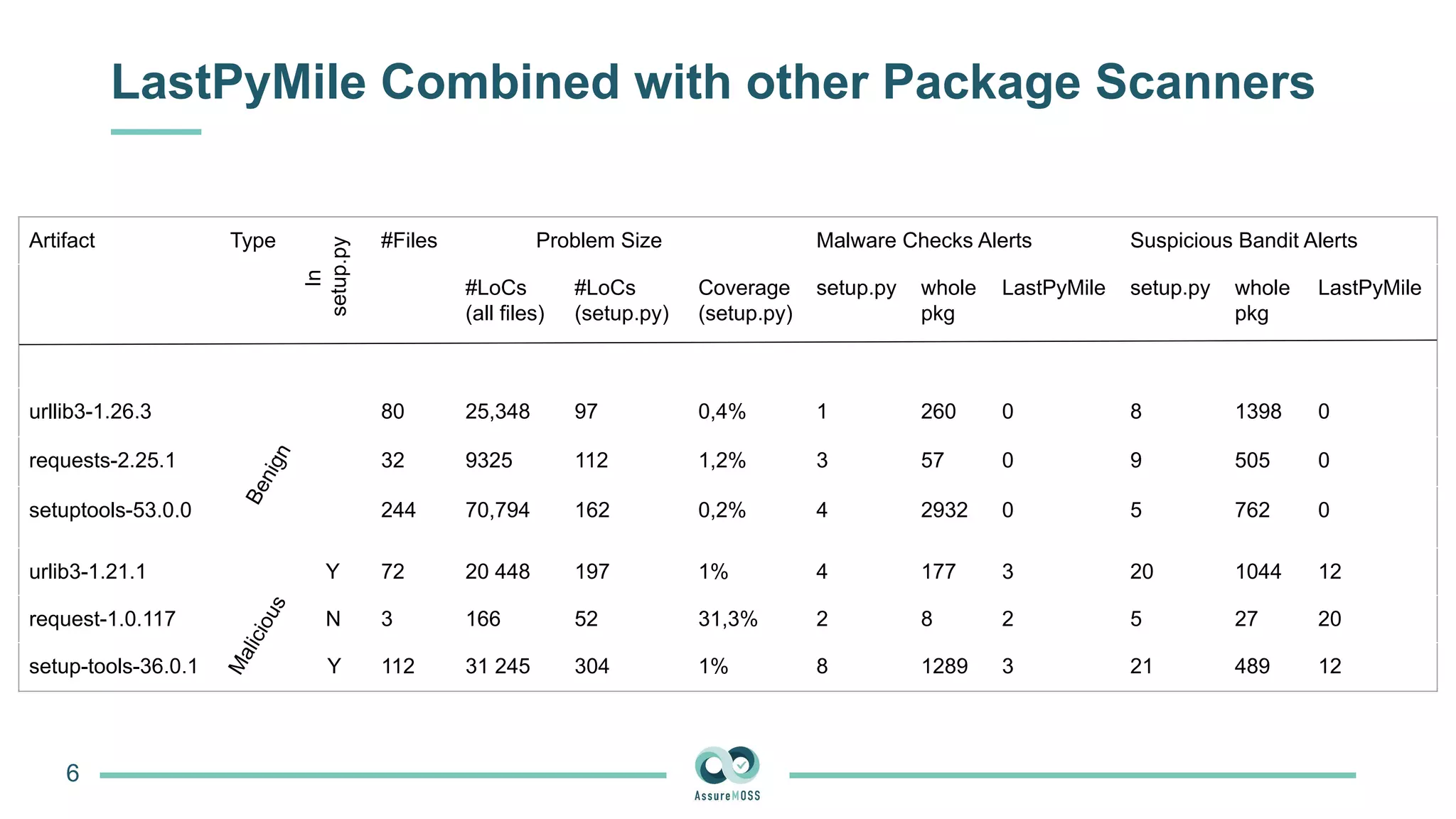
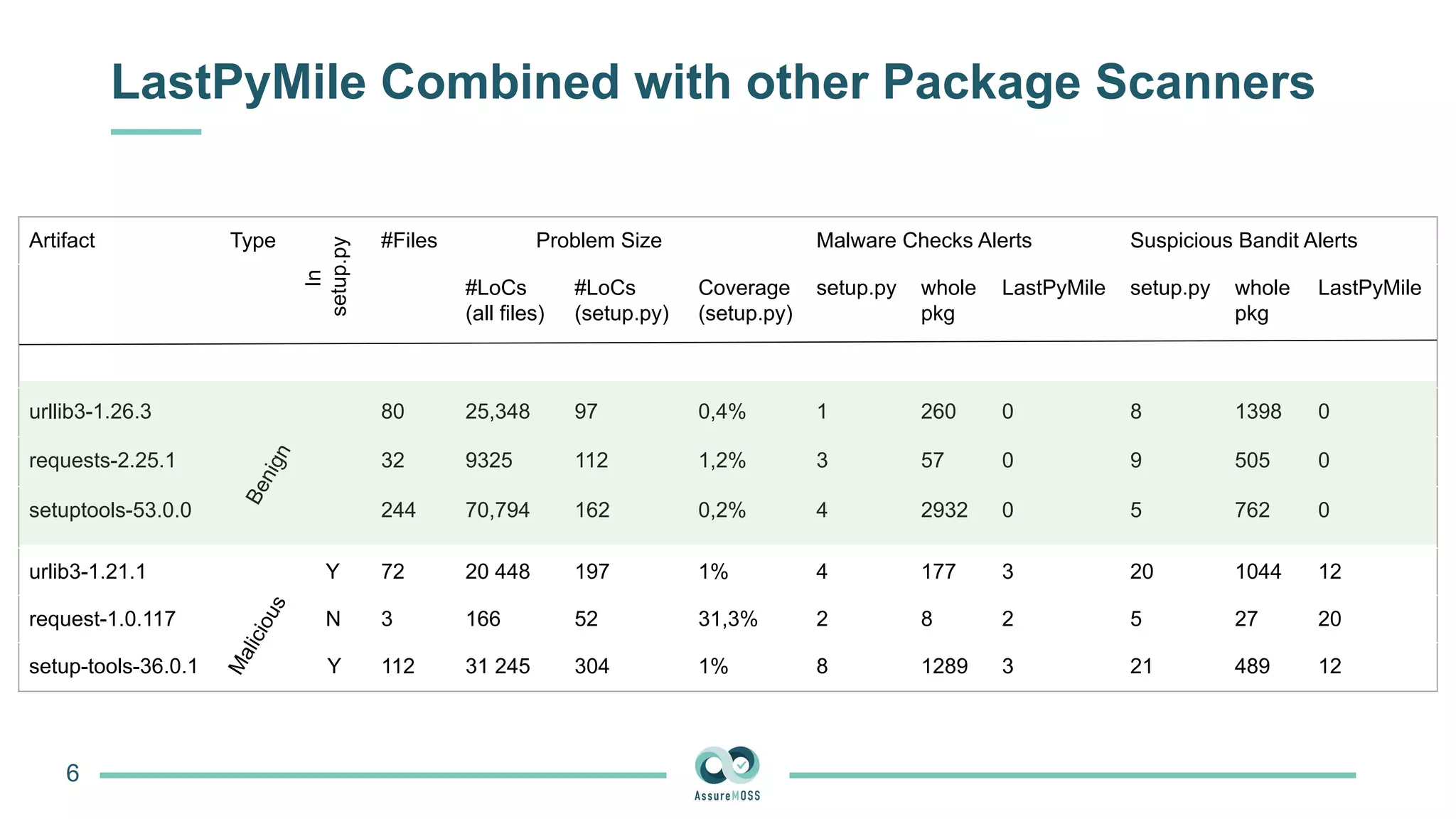
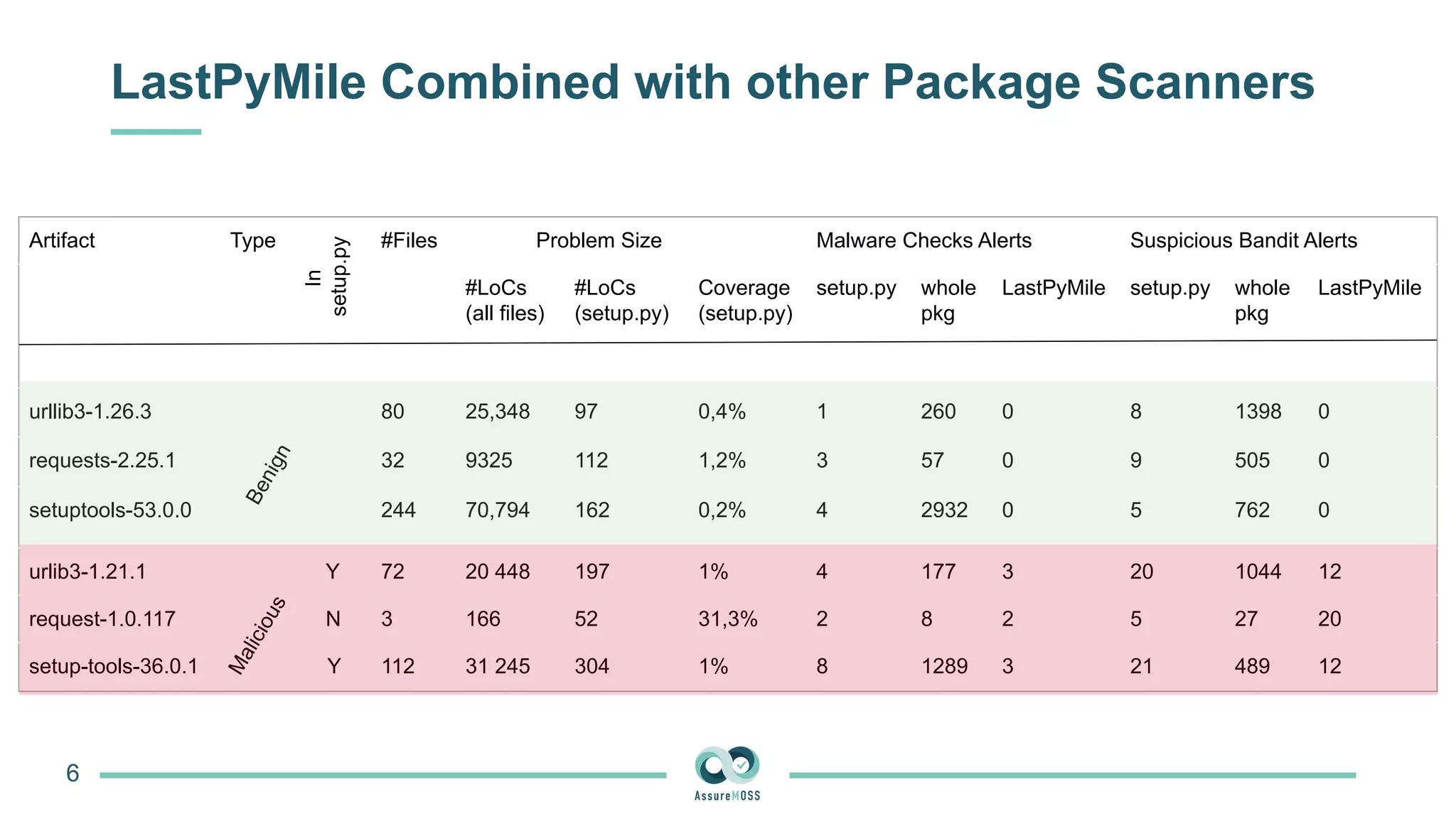
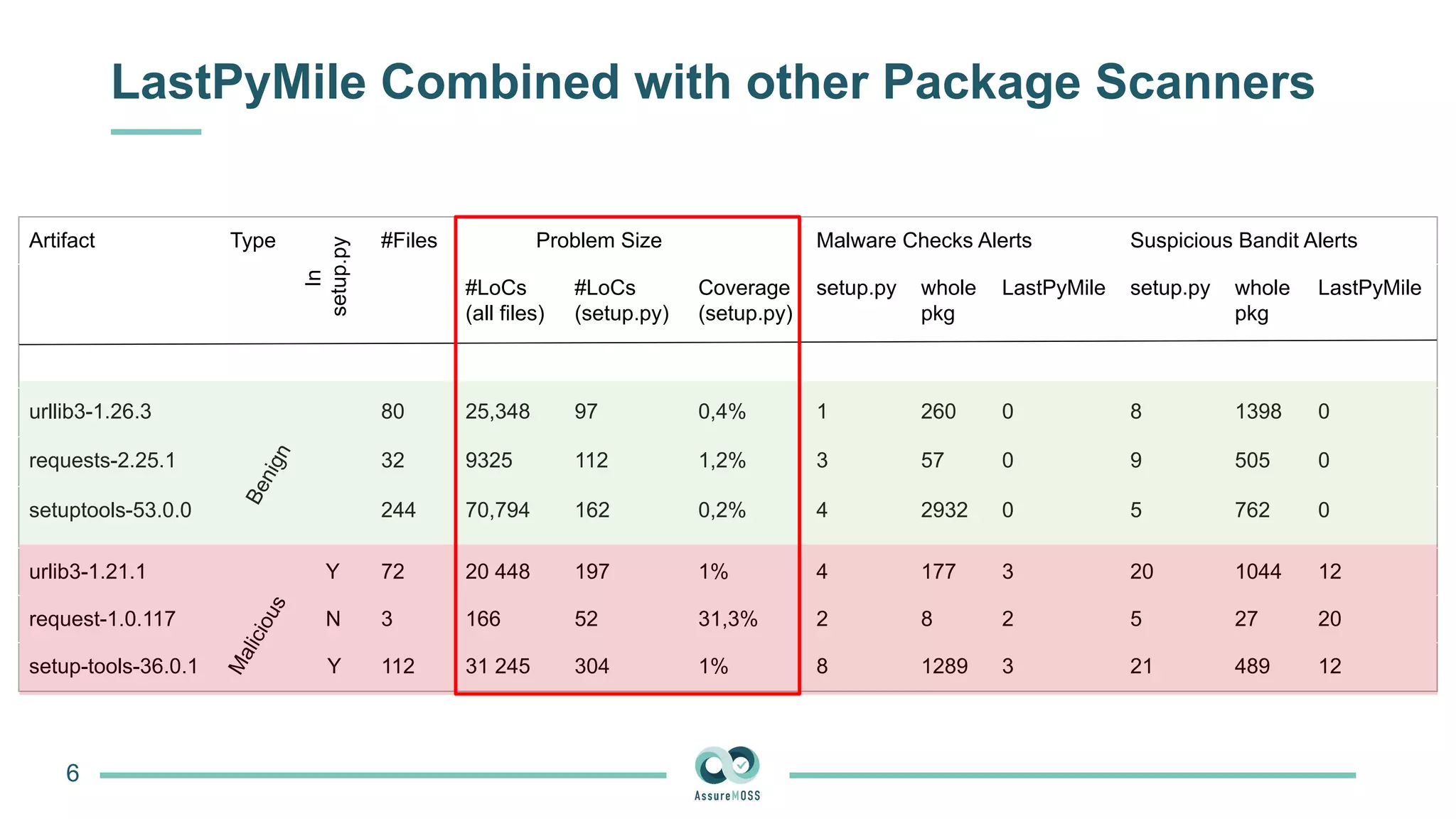
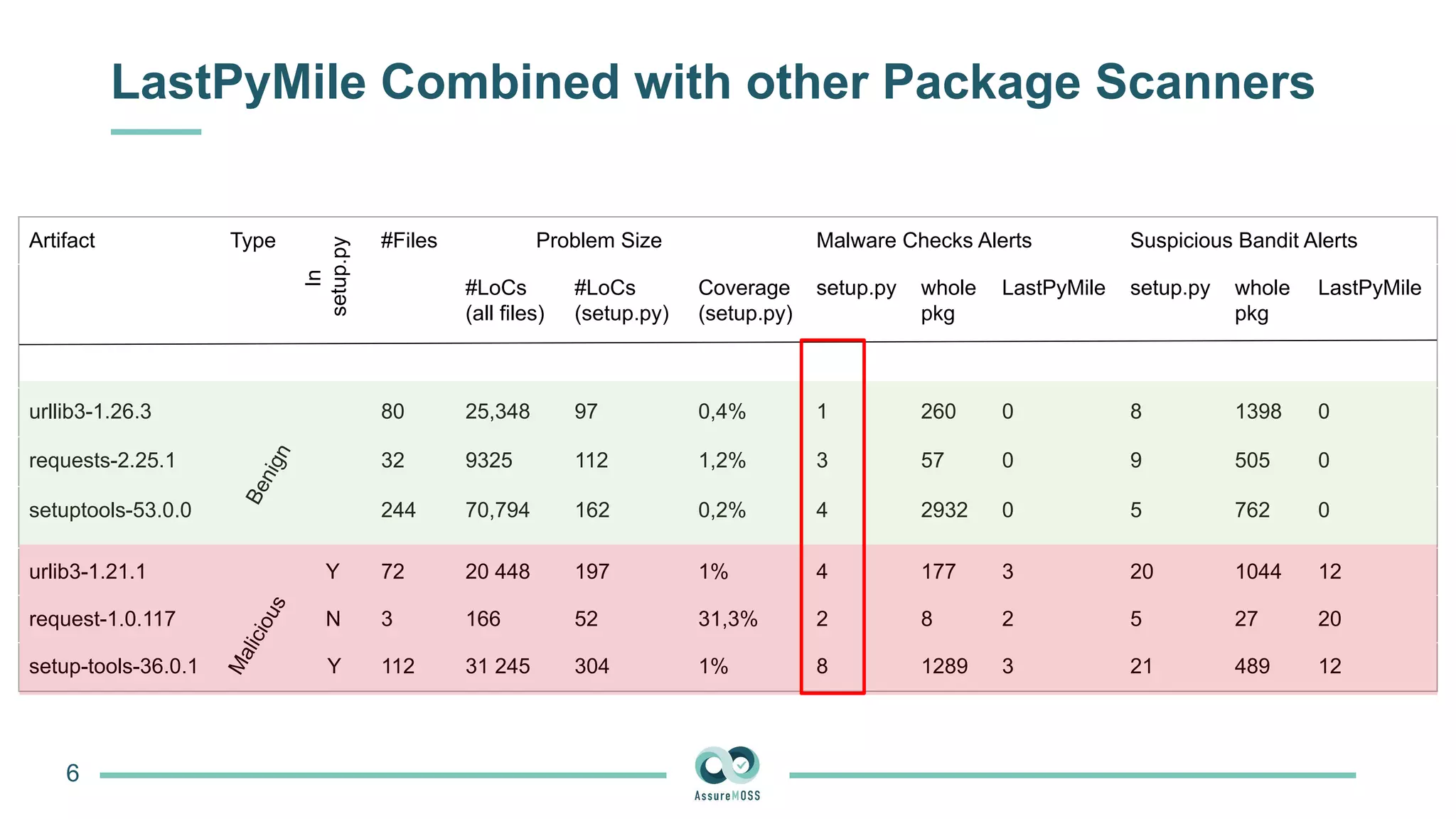
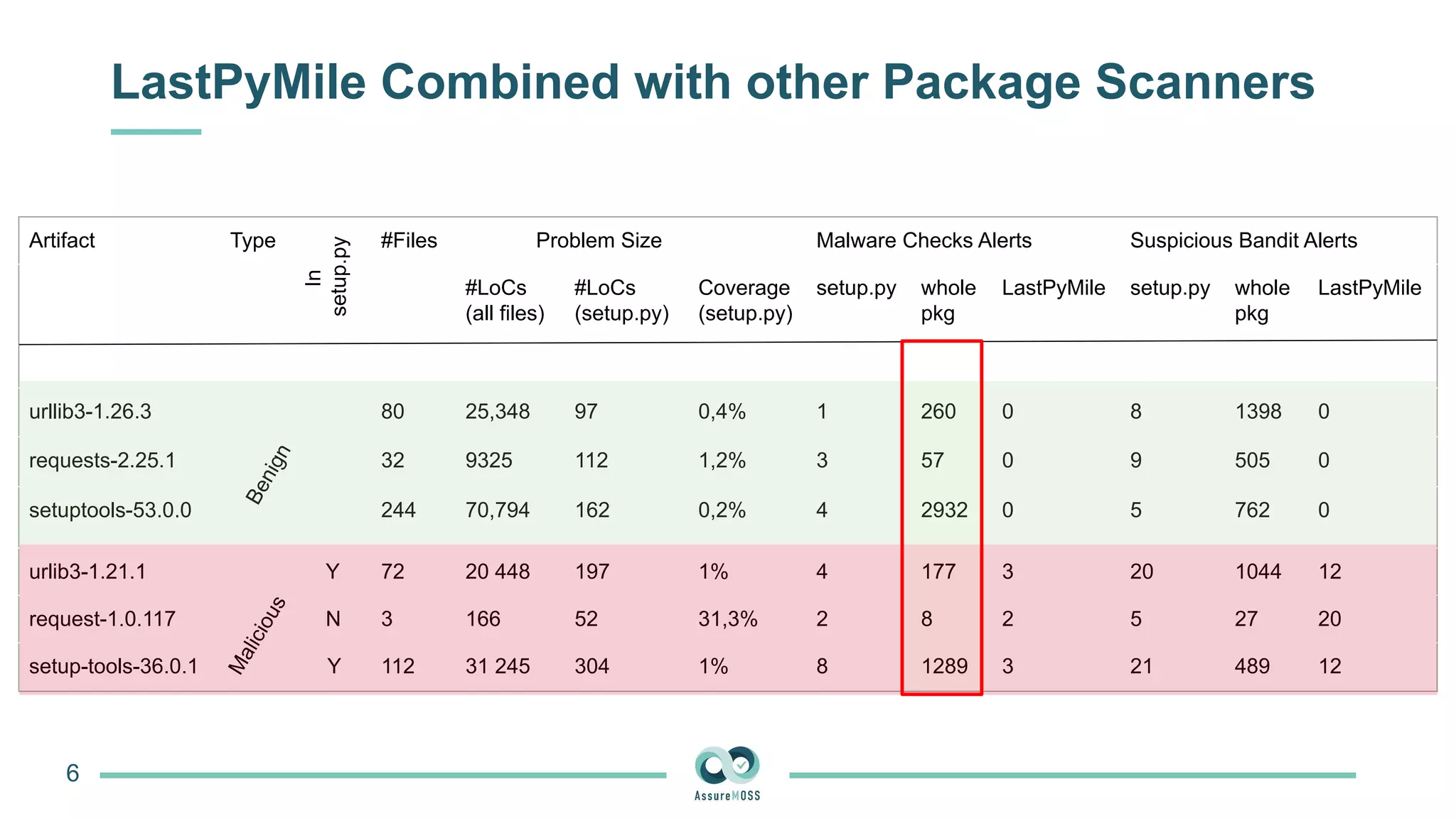
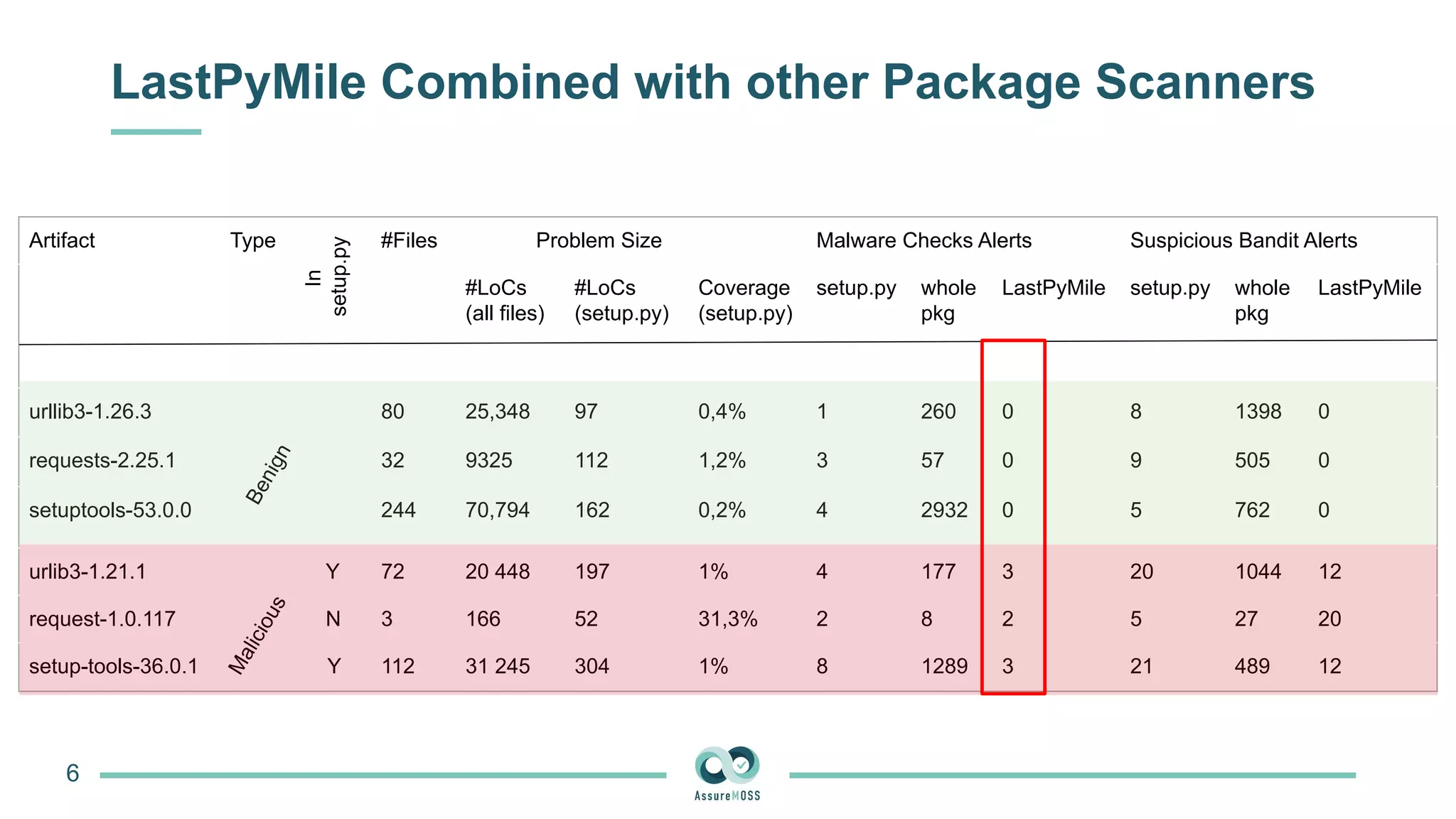
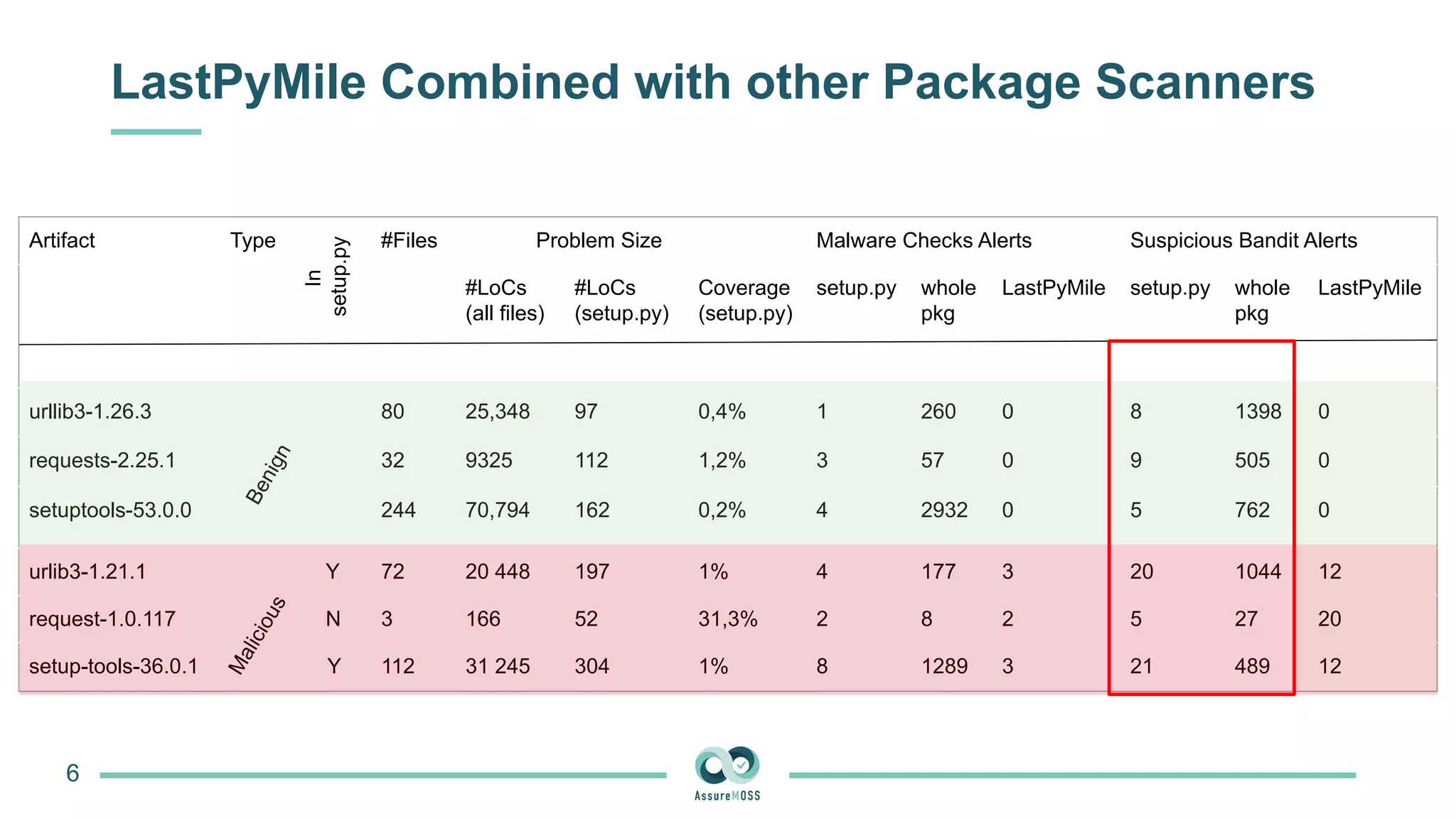
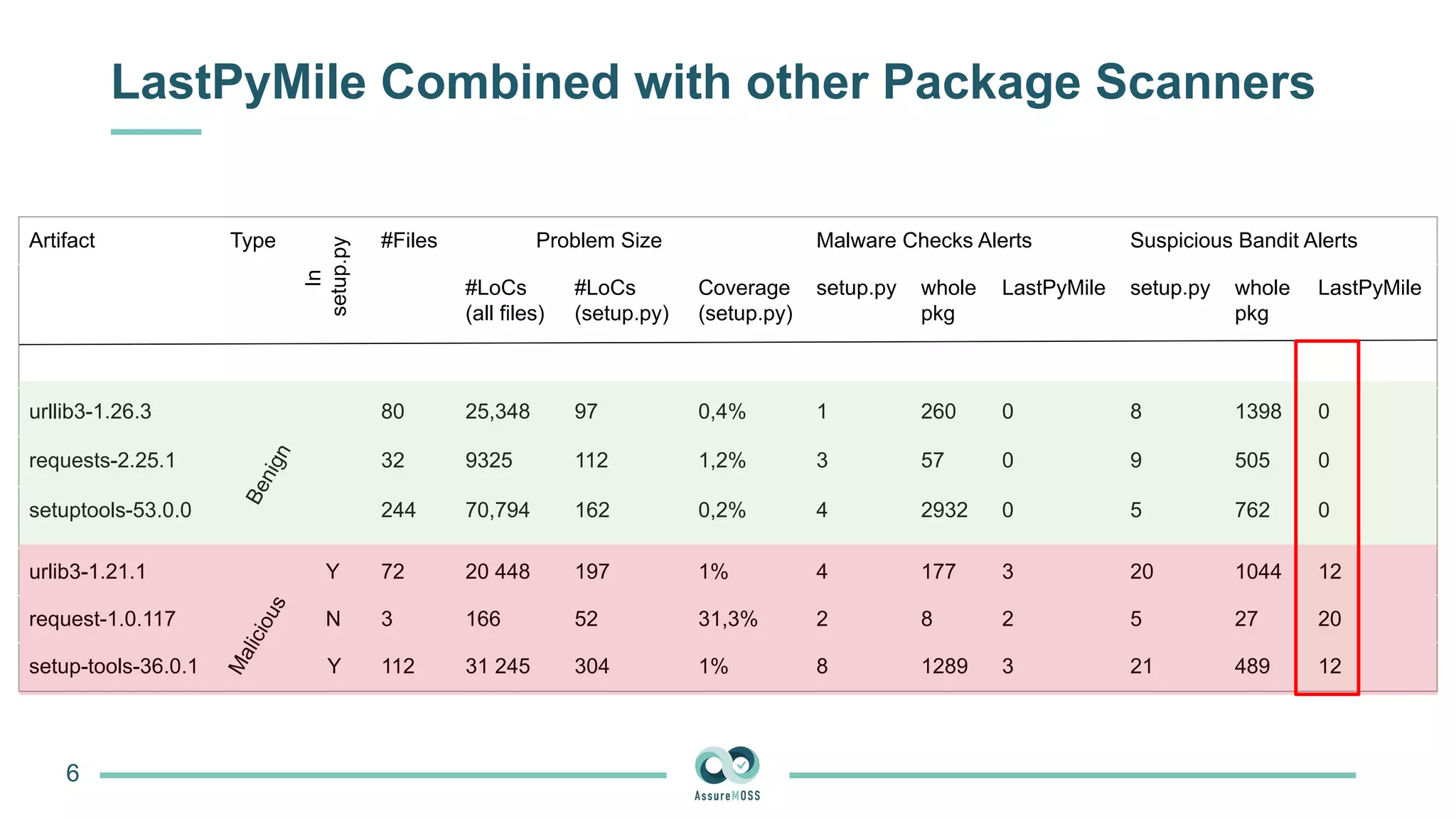
The document discusses a research project funded by various EU Horizon 2020 programs, focusing on a lightweight method called LastPymile for securing the Python ecosystem against software supply chain attacks. It highlights the prevalence of discrepancies between source code and distributed packages on PyPI, with a significant percentage of packages containing malicious code vulnerabilities. The paper outlines the challenges of verifying package security at scale and proposes solutions to improve the detection and prevention of code injection threats.