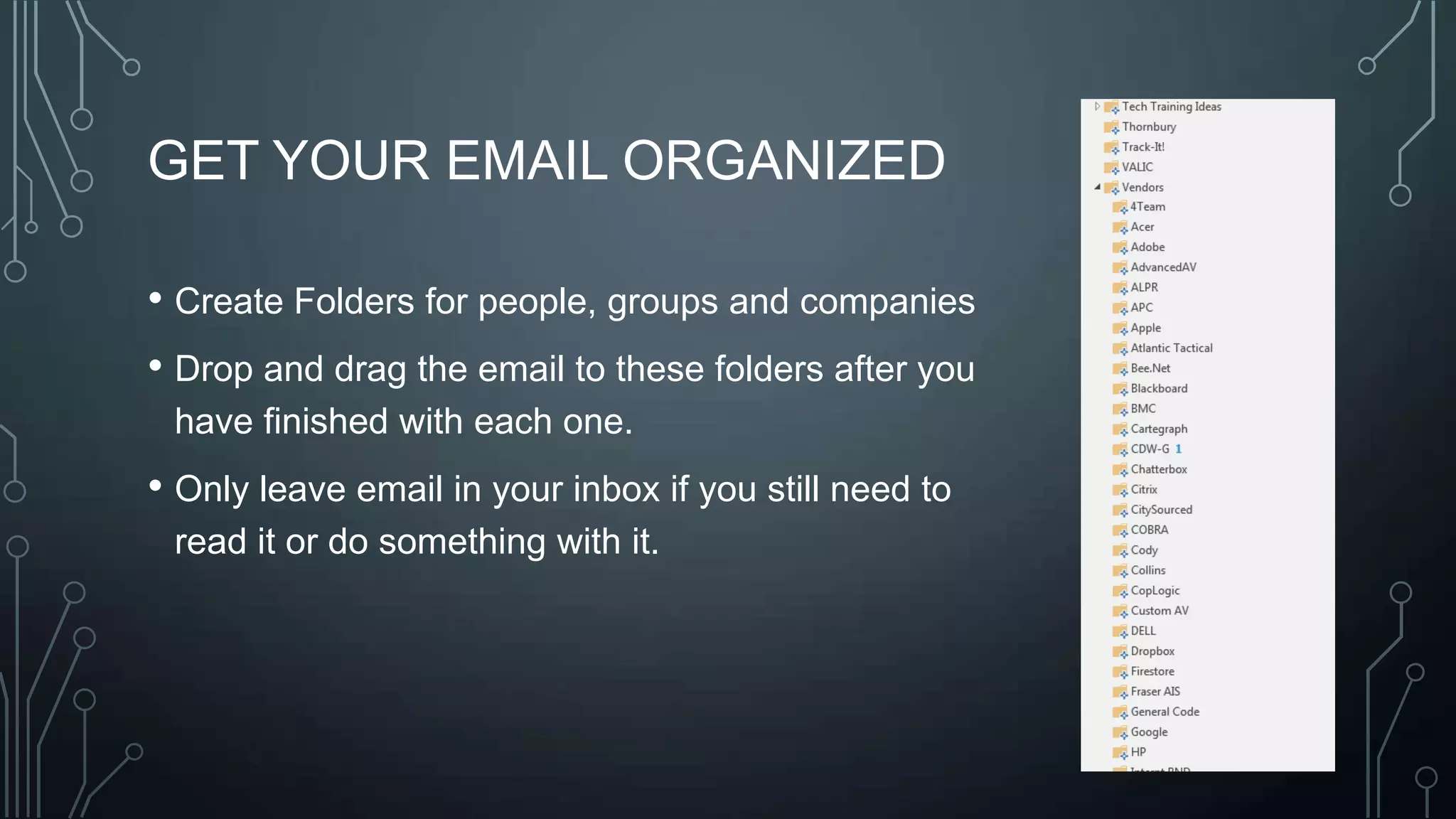
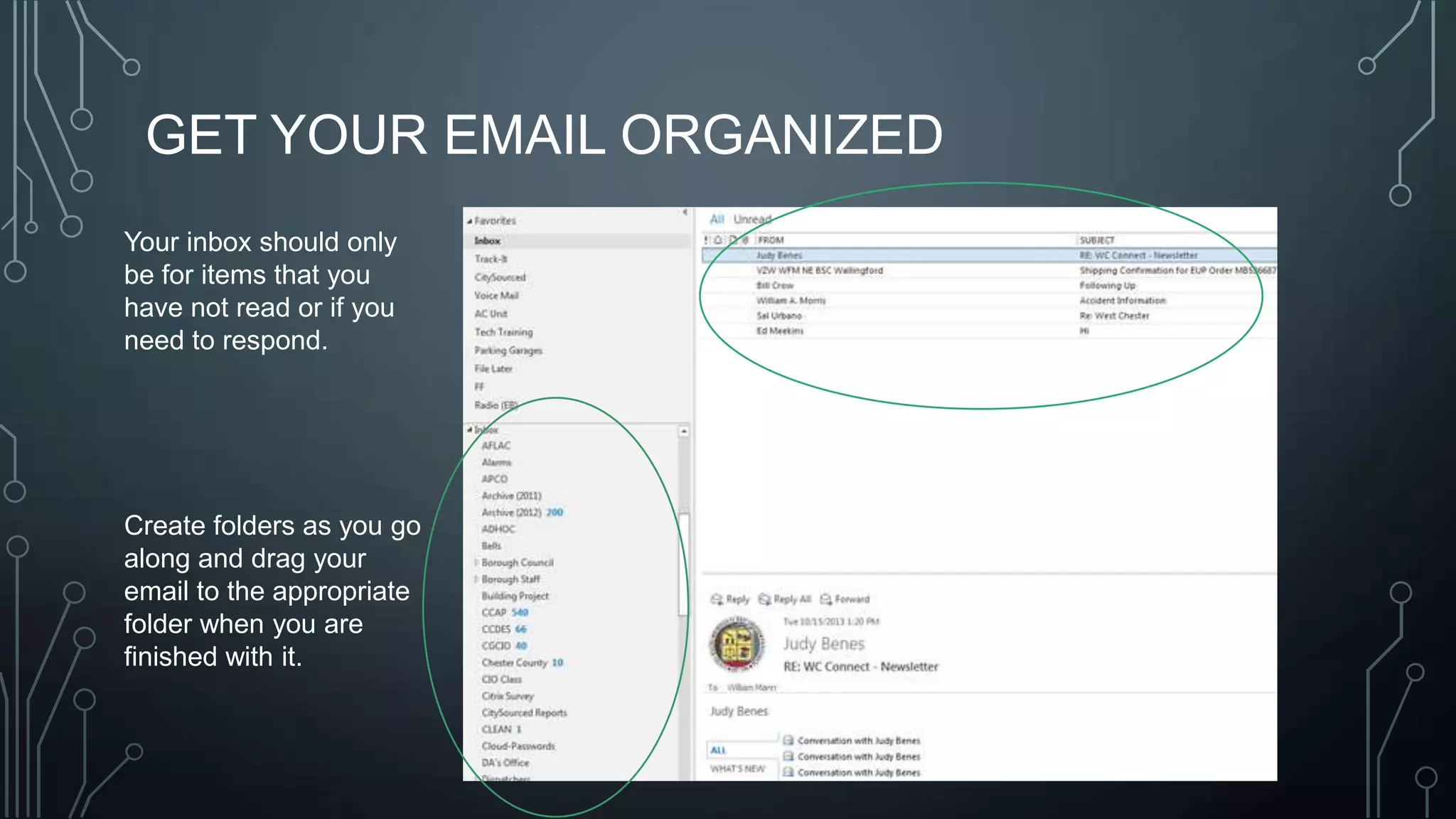
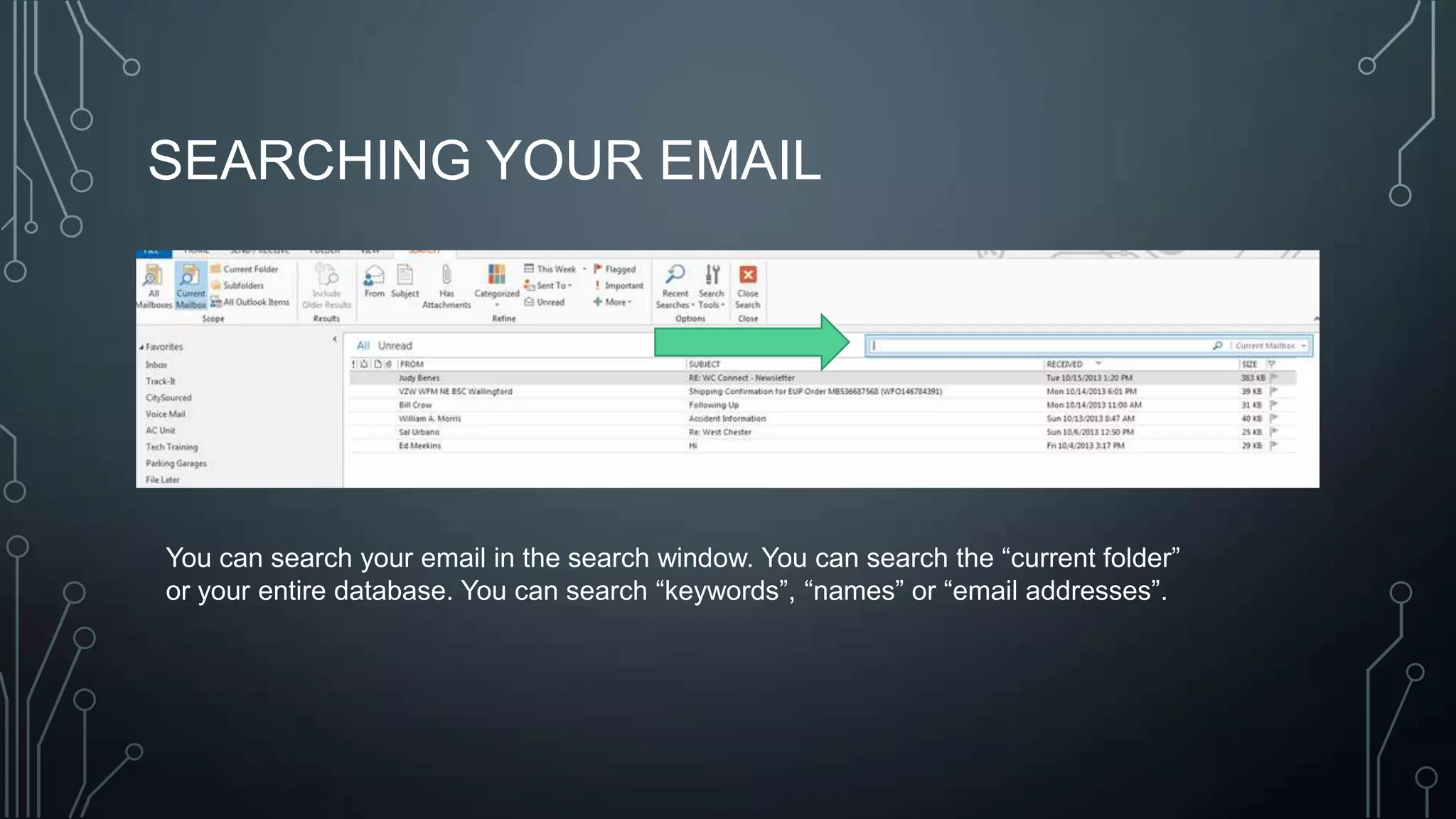
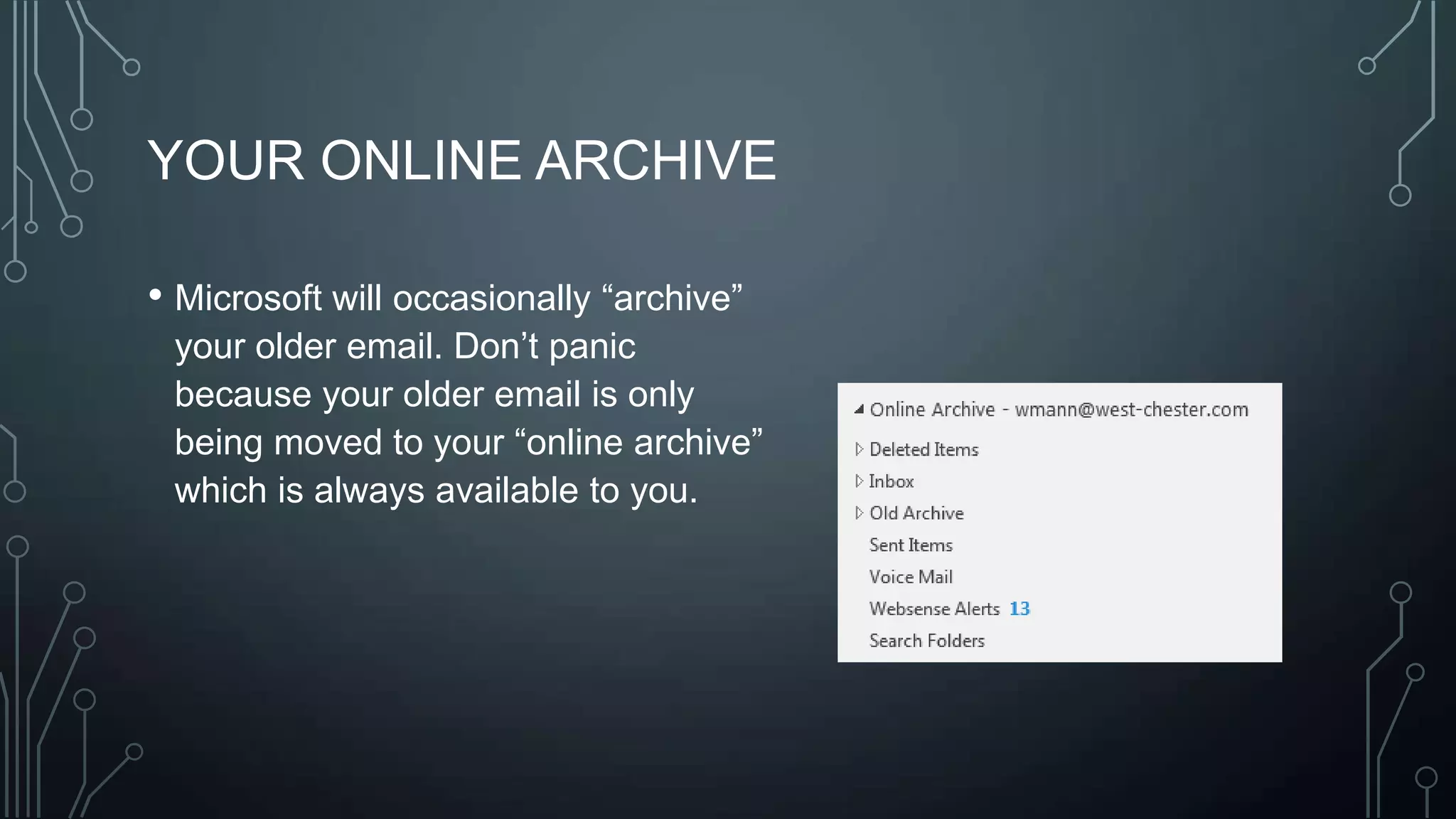
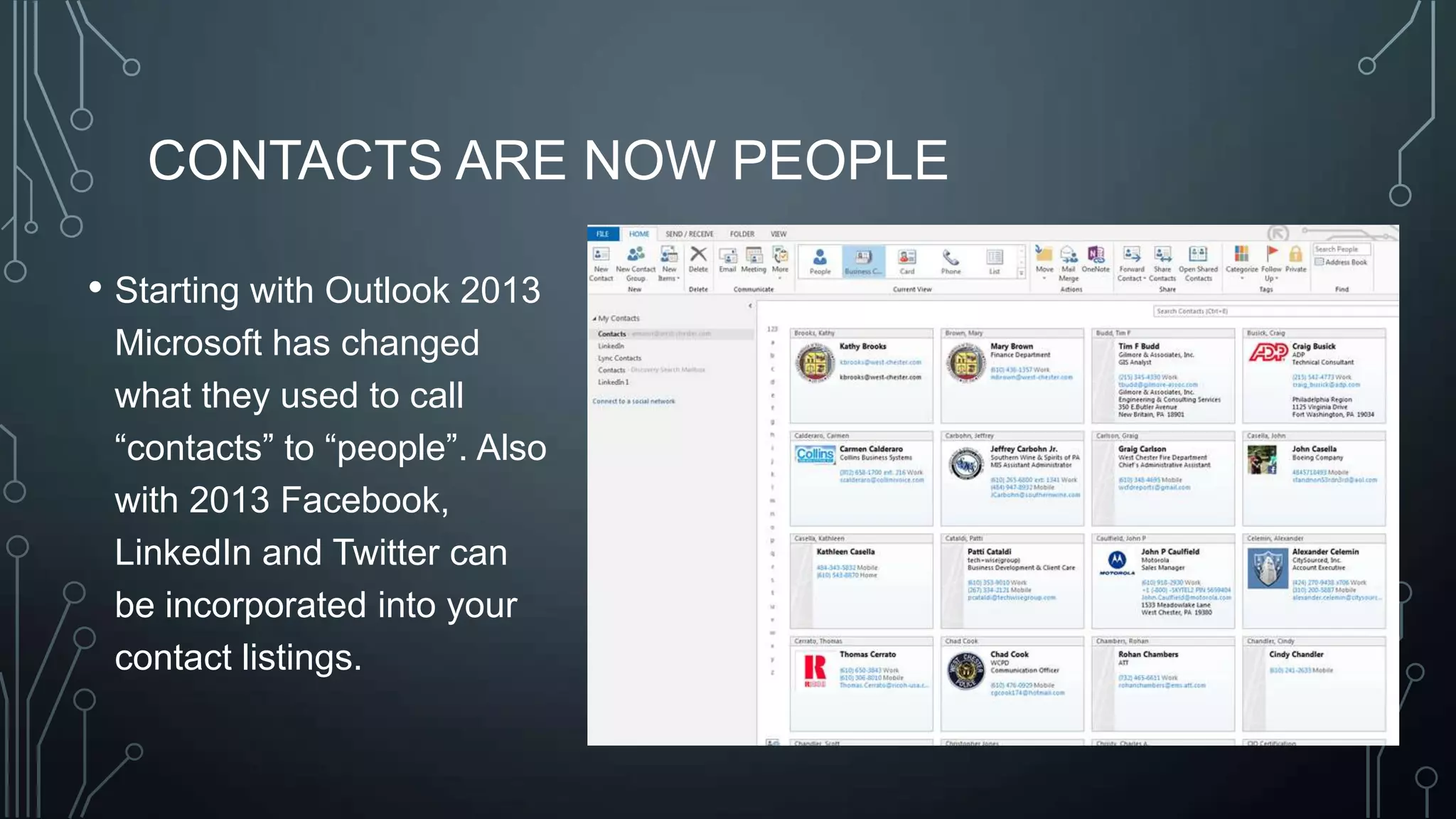
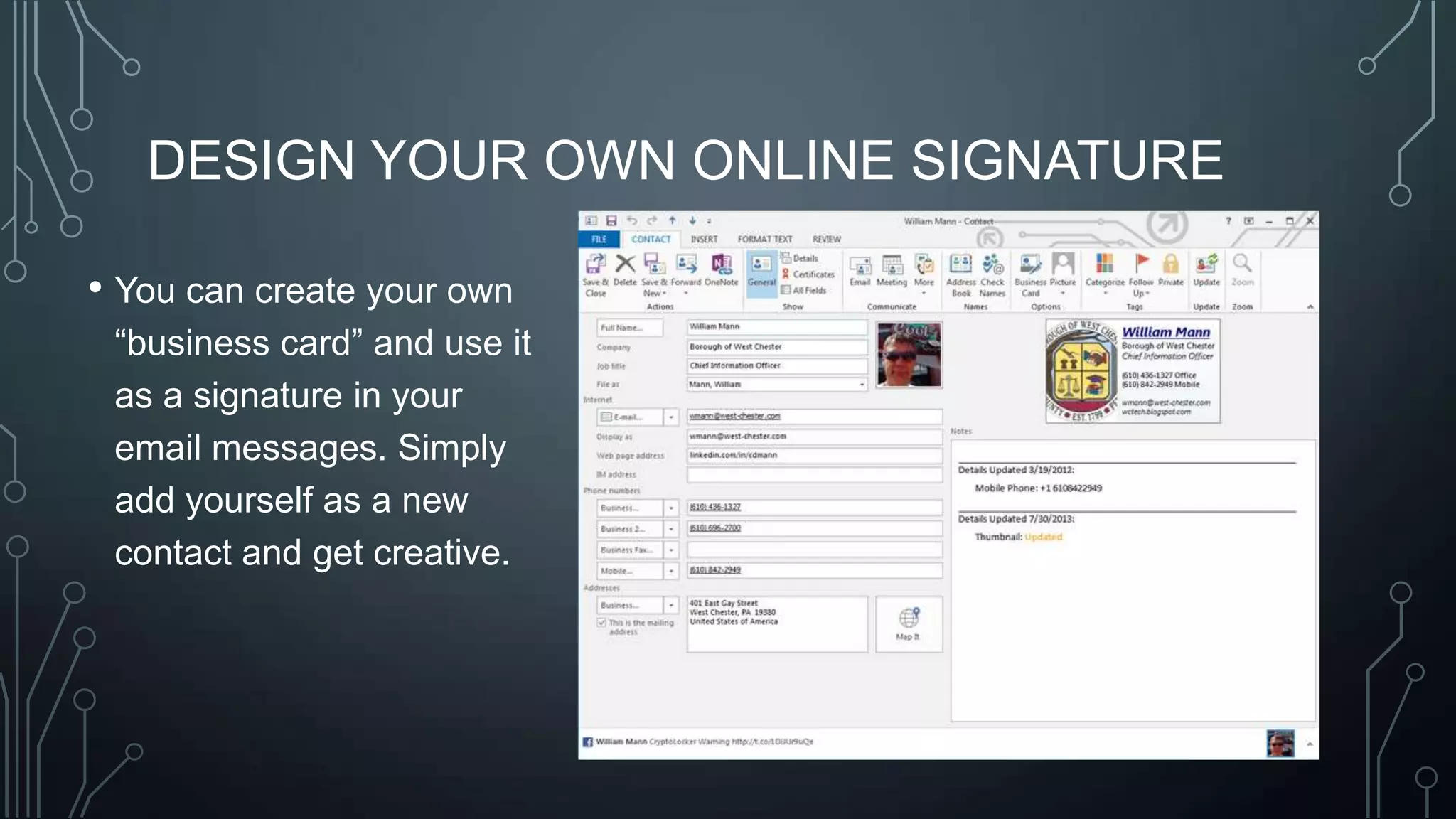
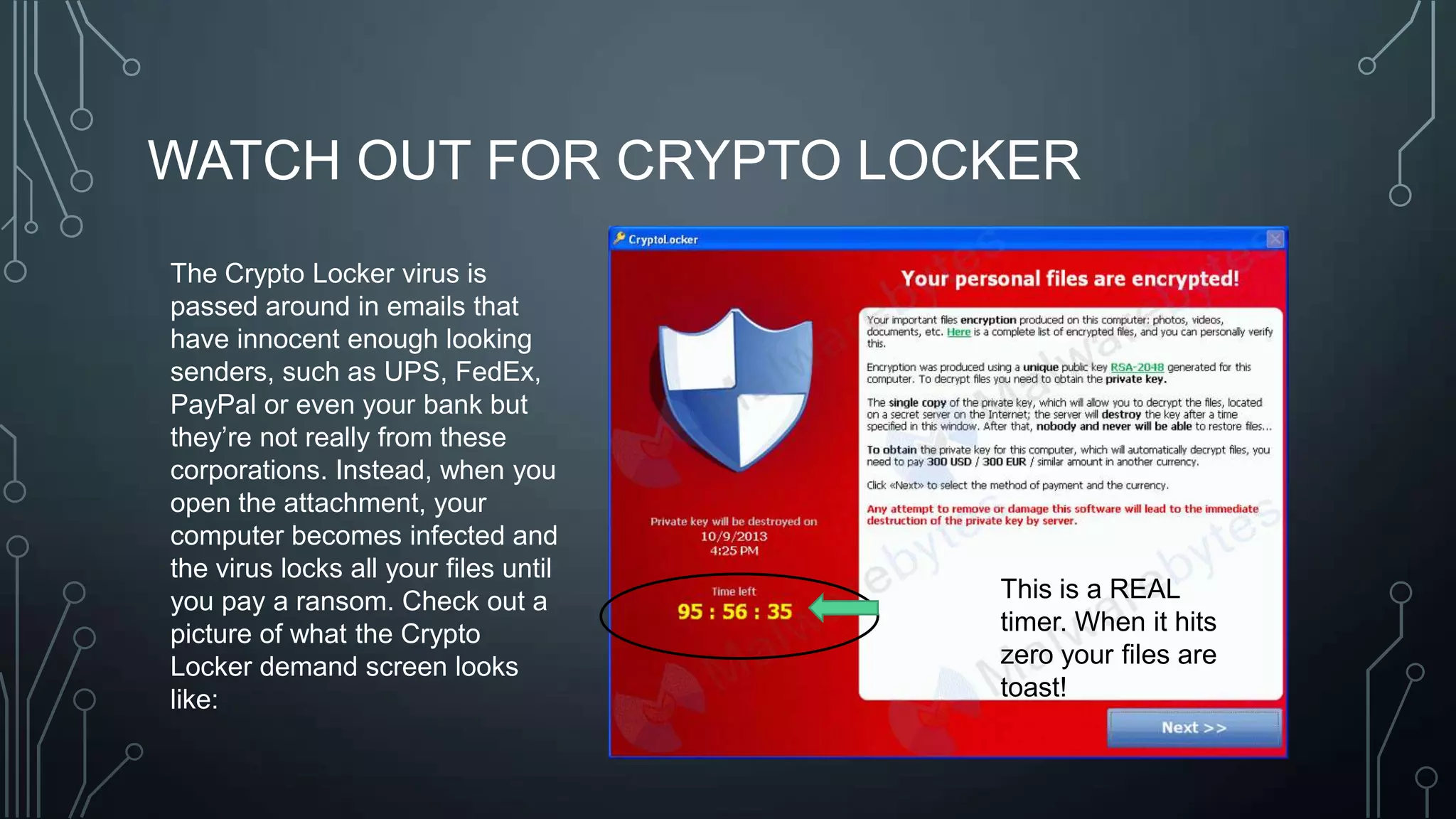
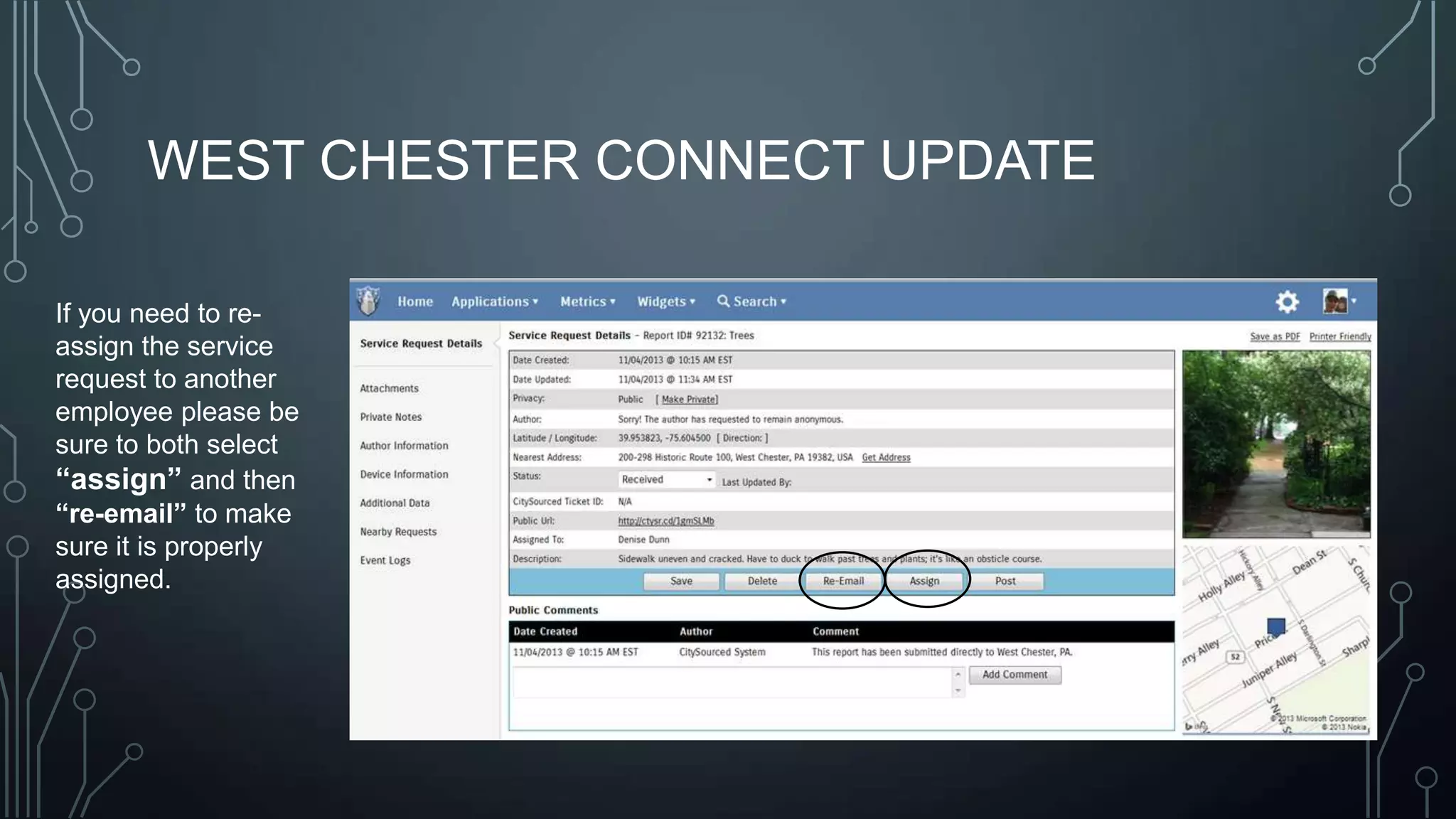
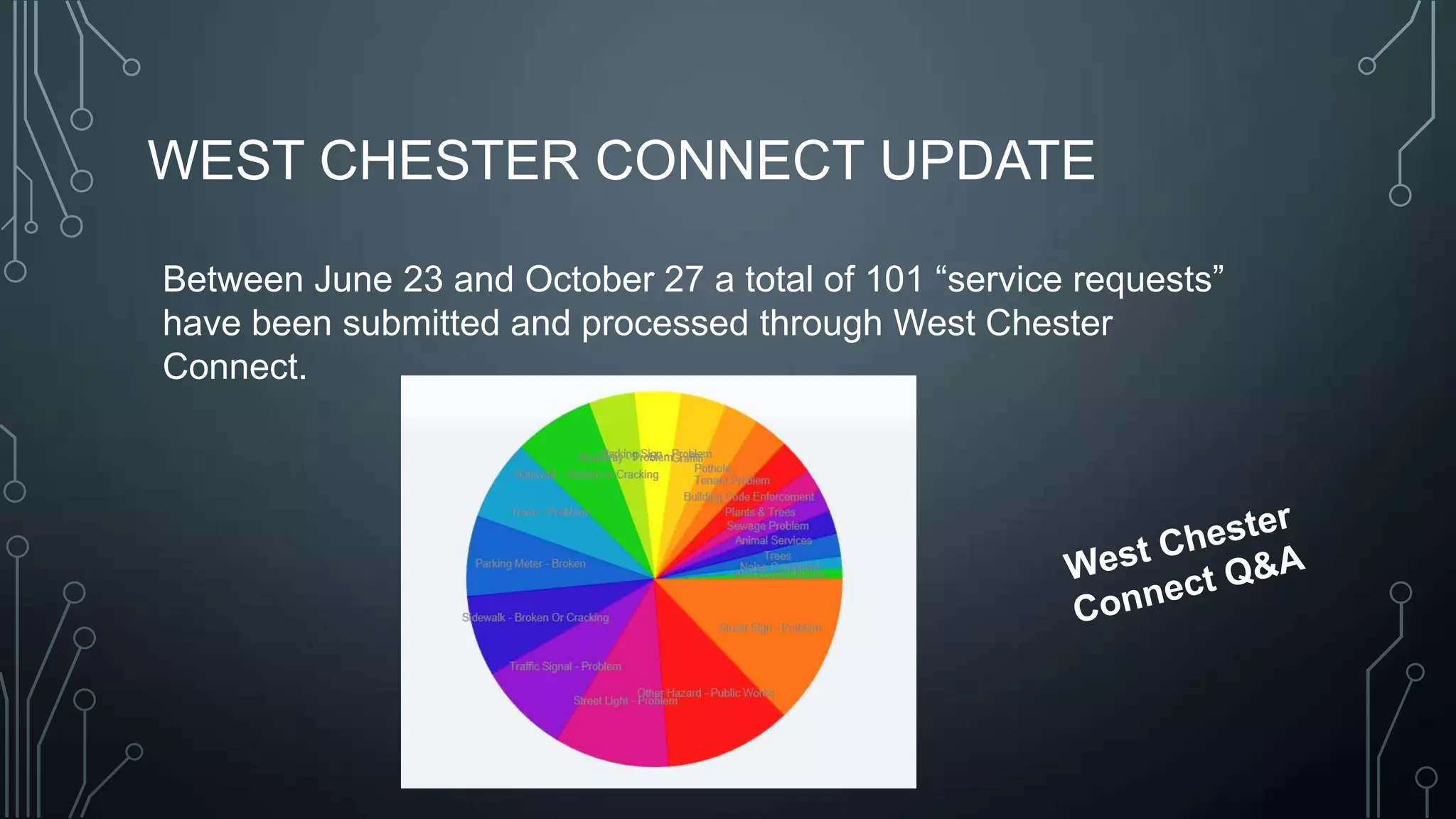
The document outlines a technology training session covering email management, file organization, cloud storage, tablet options, and computer security. It emphasizes the importance of organizing emails and documents, being cautious of email attachments to protect against threats like crypto locker, and suggests various cloud storage solutions. Additionally, it provides tips for using tablets and highlights updates related to the West Chester Connect service.