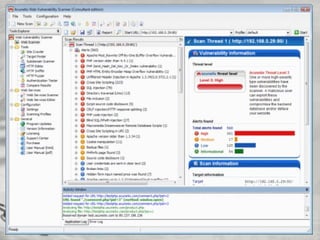
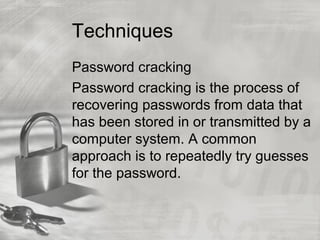
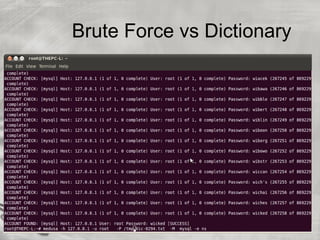
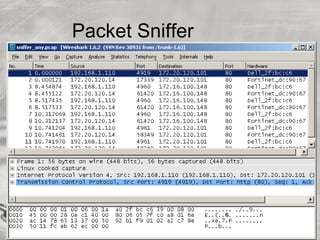
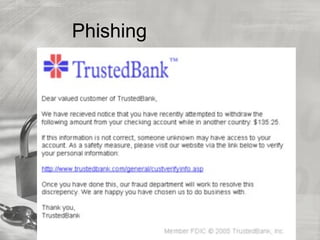
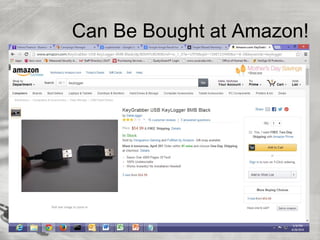
The document provides an overview of cybersecurity topics, including hacking methods, types of hackers, and various security exploits like trojan horses, viruses, and botnets. It discusses ransomware, specifically the Cryptolocker attack, and the implications of Bitcoin in cybercrime. Additionally, it delves into the deep web and social engineering techniques utilized by cybercriminals.




































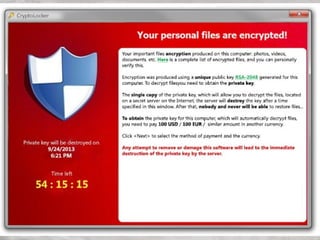




![What is Bitcoin?
Bitcoin is a peer-to-peer payment
system introduced as open source
software in 2009 by developer Satoshi
Nakamoto.[4] The digital currency
created and used in the system is also
called bitcoin](https://image.slidesharecdn.com/wud-140428180256-phpapp01/85/Cybersecurity-Hacking-and-Privacy-58-320.jpg)




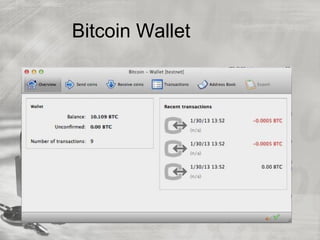

![Status of Bitcoin (IRS)
The US Government Accountability Office reviewed
virtual currencies upon the request of the Senate
Finance Committee and in May 2013
recommended[136] that the IRS formulate tax
guidance for bitcoin businesses. On 25 March
2014, in time for 2013 tax filing, the IRS issued
guidance that virtual currency is treated as property
for US federal tax purposes and that "an individual
who 'mines' virtual currency as a trade or business
[is] subject to self-employment tax](https://image.slidesharecdn.com/wud-140428180256-phpapp01/85/Cybersecurity-Hacking-and-Privacy-66-320.jpg)

