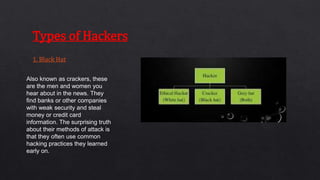
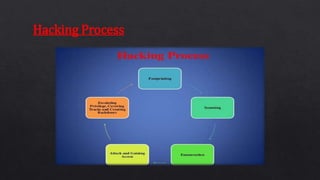
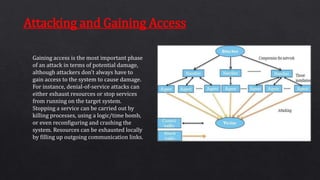
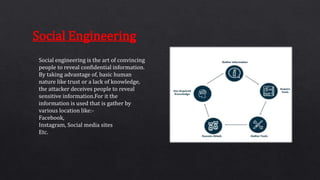
The document discusses ethical hacking, which involves legally testing systems for vulnerabilities with permission, contrasting it with malicious hacking. It details various types of hackers, the hacking process, and techniques such as footprinting, scanning, enumeration, and social engineering. Additionally, it covers tools for ethical hacking, advantages and disadvantages of the practice, and the necessity for cybersecurity in a world increasingly reliant on technology.