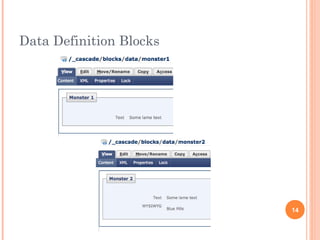
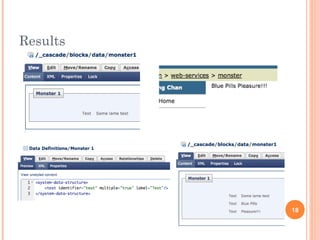
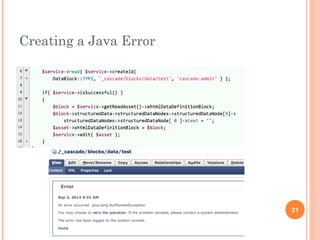
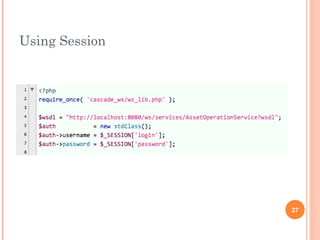
The document discusses web services and their encapsulation, reusability, and simplicity. It covers topics like hiding usernames/passwords, using fully qualified identifiers to locate nodes, and creating reusable classes like Asset and Property. Code examples show how to retrieve assets, work with data definition blocks, and traverse an asset tree to publish pages simply using global functions. The presentation aims to highlight best practices for web services development.