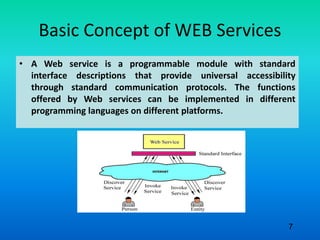
The document discusses the fundamental concepts and standards related to web services, focusing on web services description language (WSDL) and simple object access protocol (SOAP). It highlights how web services enhance business-to-business collaboration, interoperability, and software deployment efficiency. Furthermore, it details the structure and operation types defined in WSDL and the role of SOAP as the messaging protocol for web services communication.