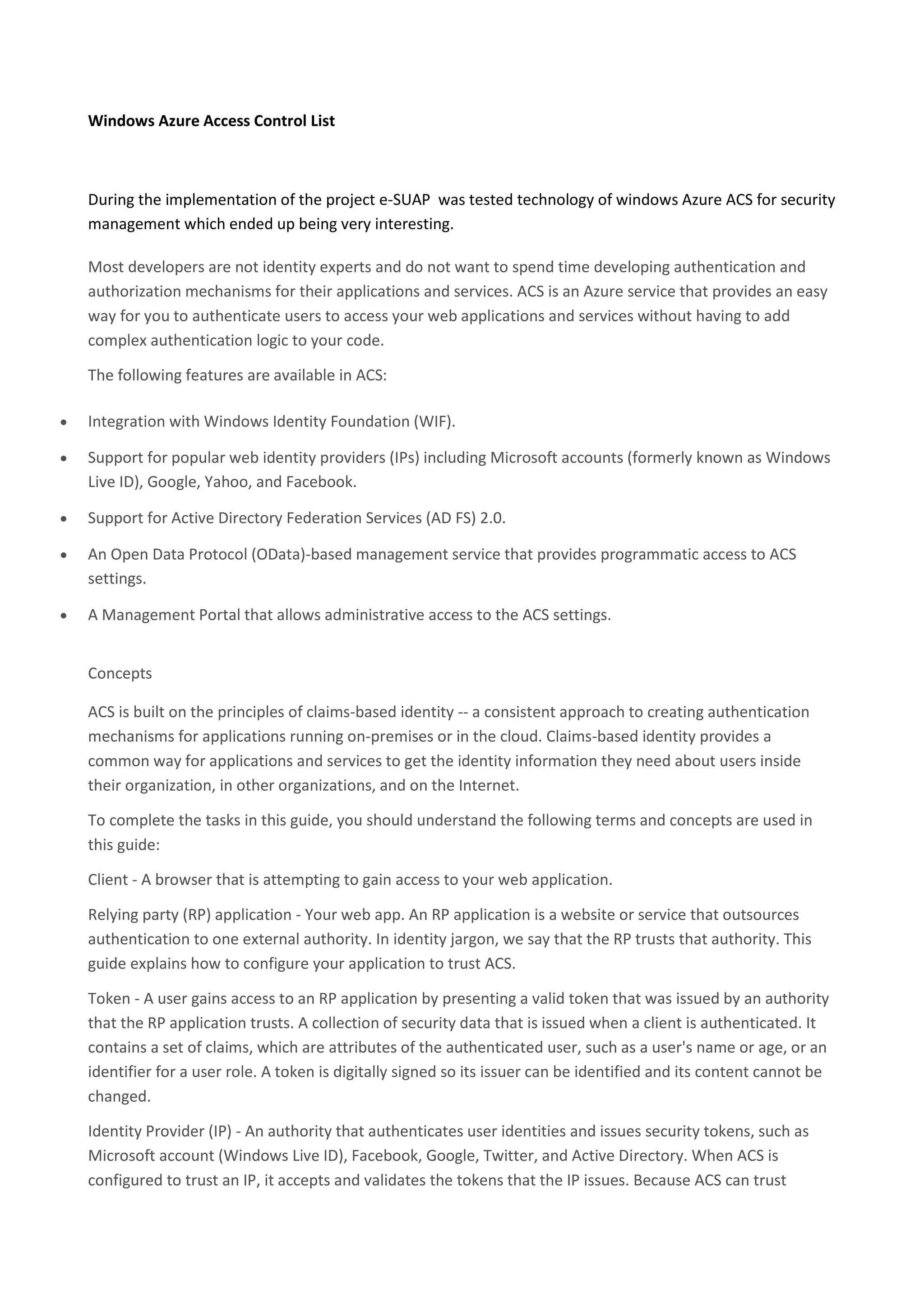
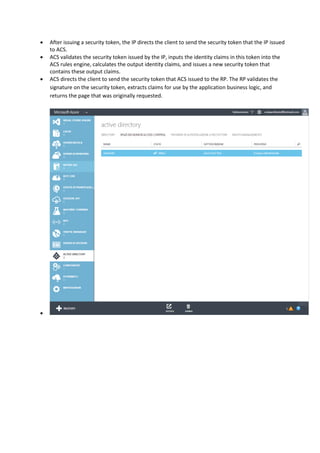
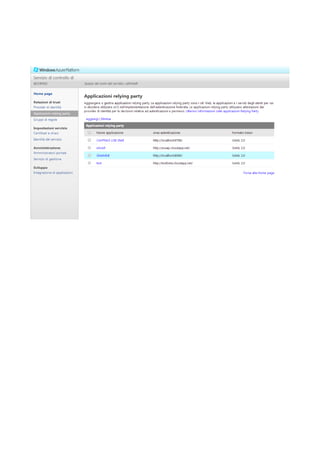
ACS is an Azure service that provides easy authentication for web applications without requiring developers to build authentication logic. It supports popular identity providers like Microsoft, Google, and Facebook, and integrates with Active Directory. ACS uses claims-based identity to get user information and uses a rule engine to transform claims between identity providers and applications.