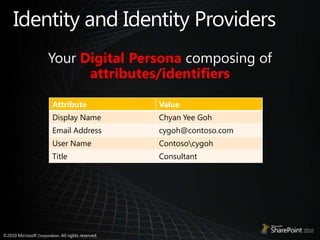
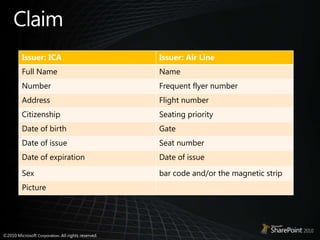
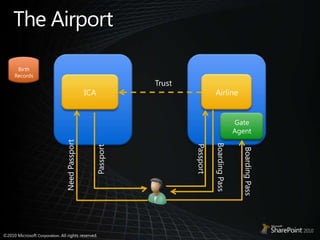
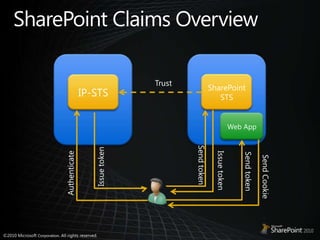
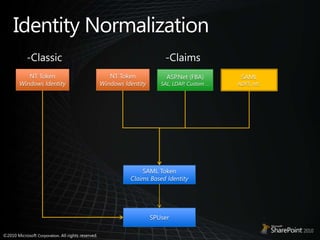
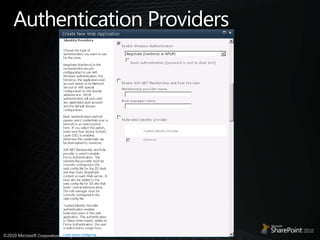
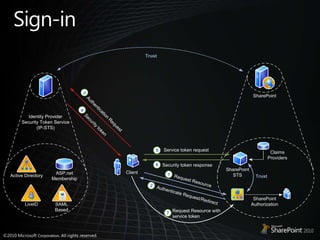
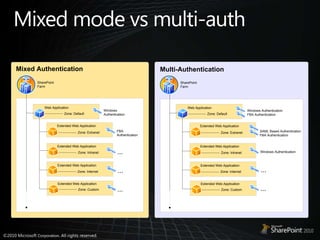
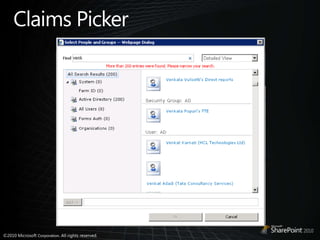
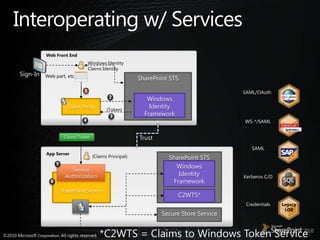
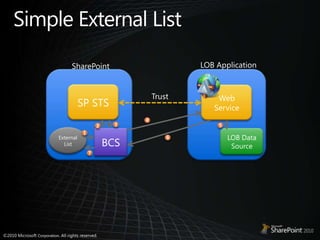
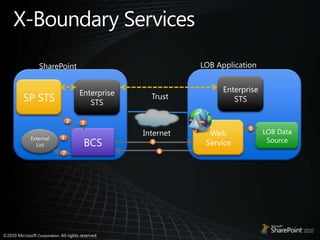
This document discusses claims-based identity in SharePoint 2010. SharePoint 2010 uses claims-based authentication which allows users to sign in using multiple identity providers. Claims are issued by an authority to describe attributes of a user. SharePoint acts as a claims-based application by using a security token service to authenticate users and issue claims. The document covers configuring claims providers and incoming/outgoing claims to provide identity and access across SharePoint and external applications.