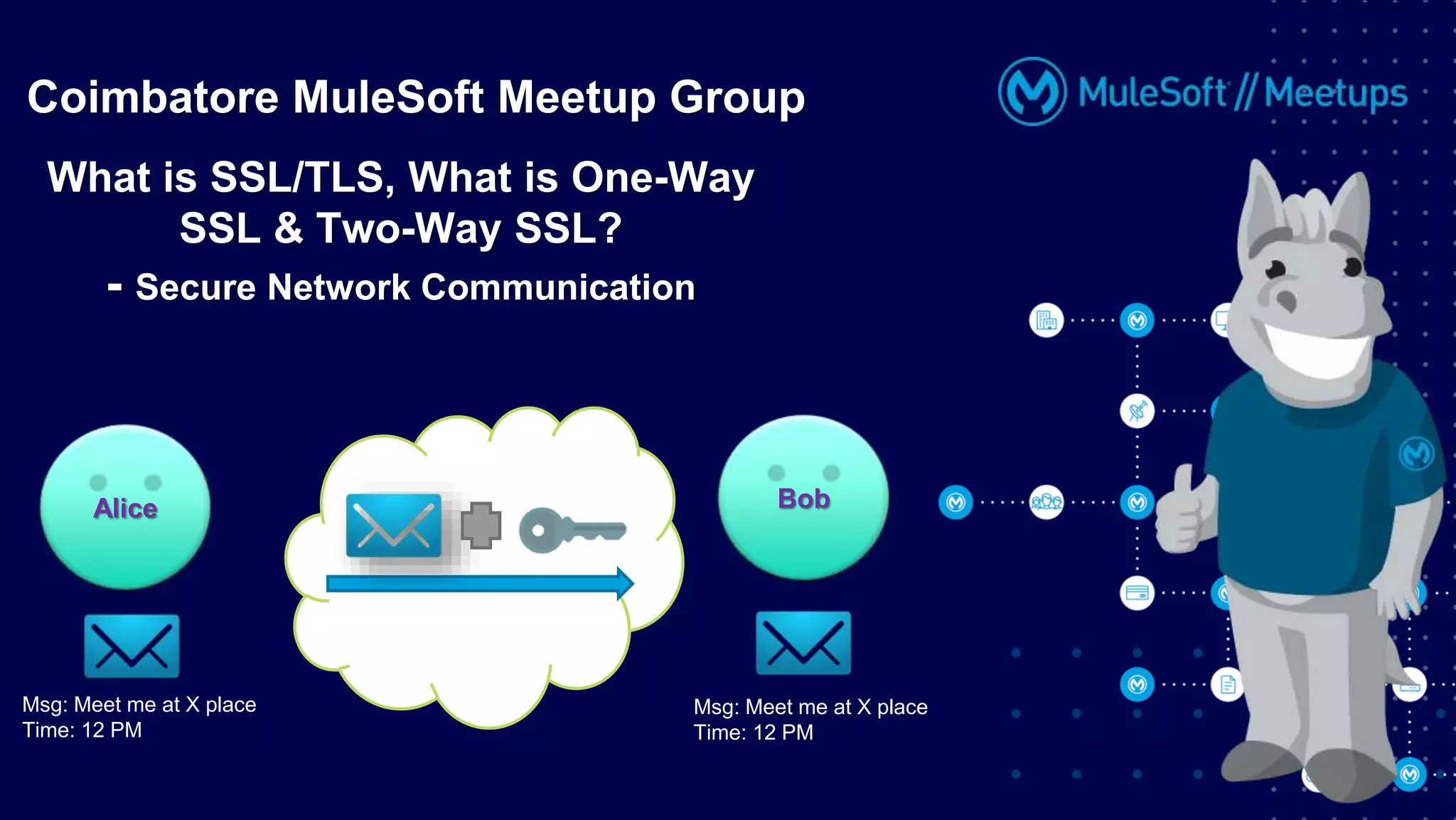
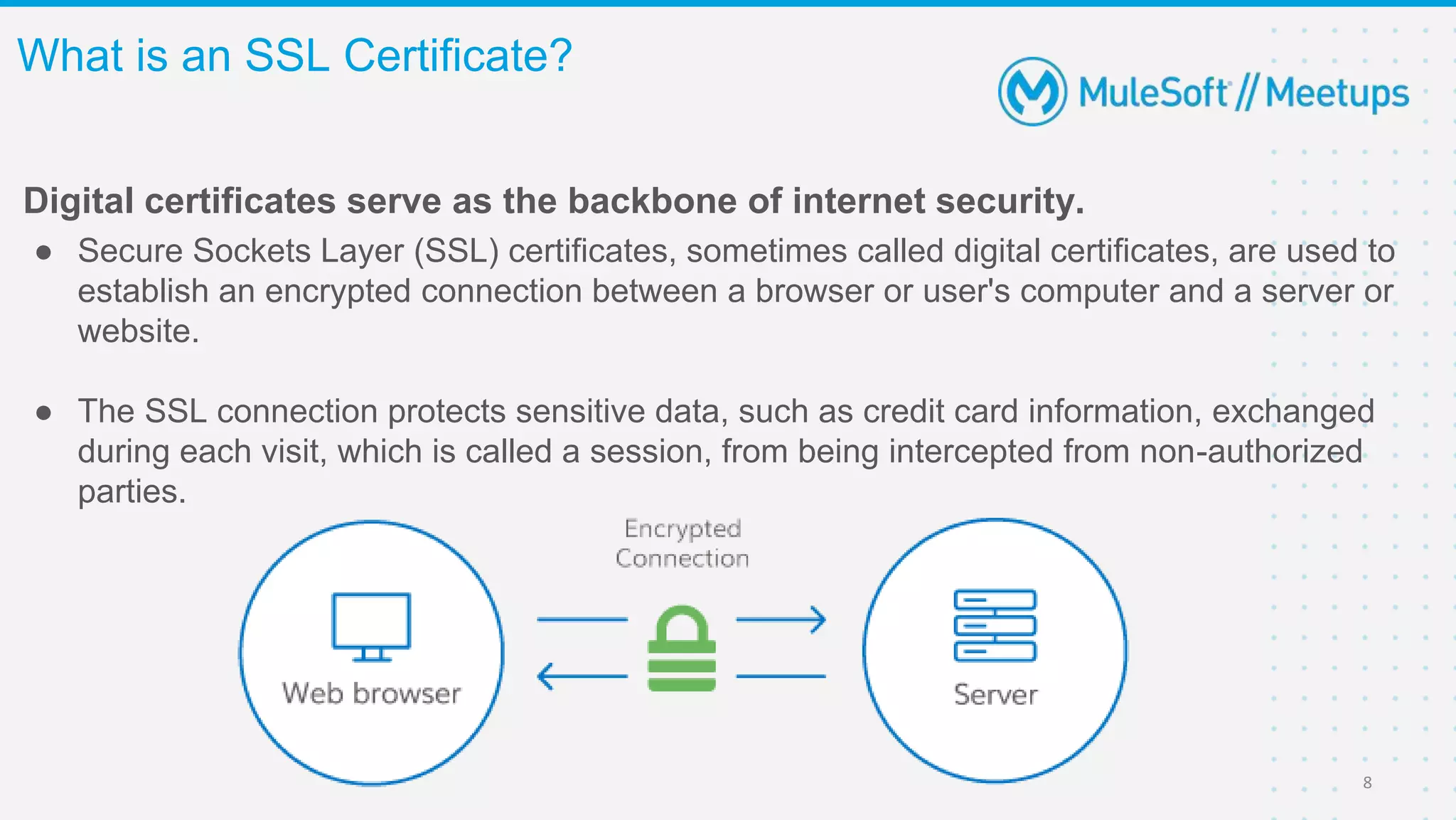
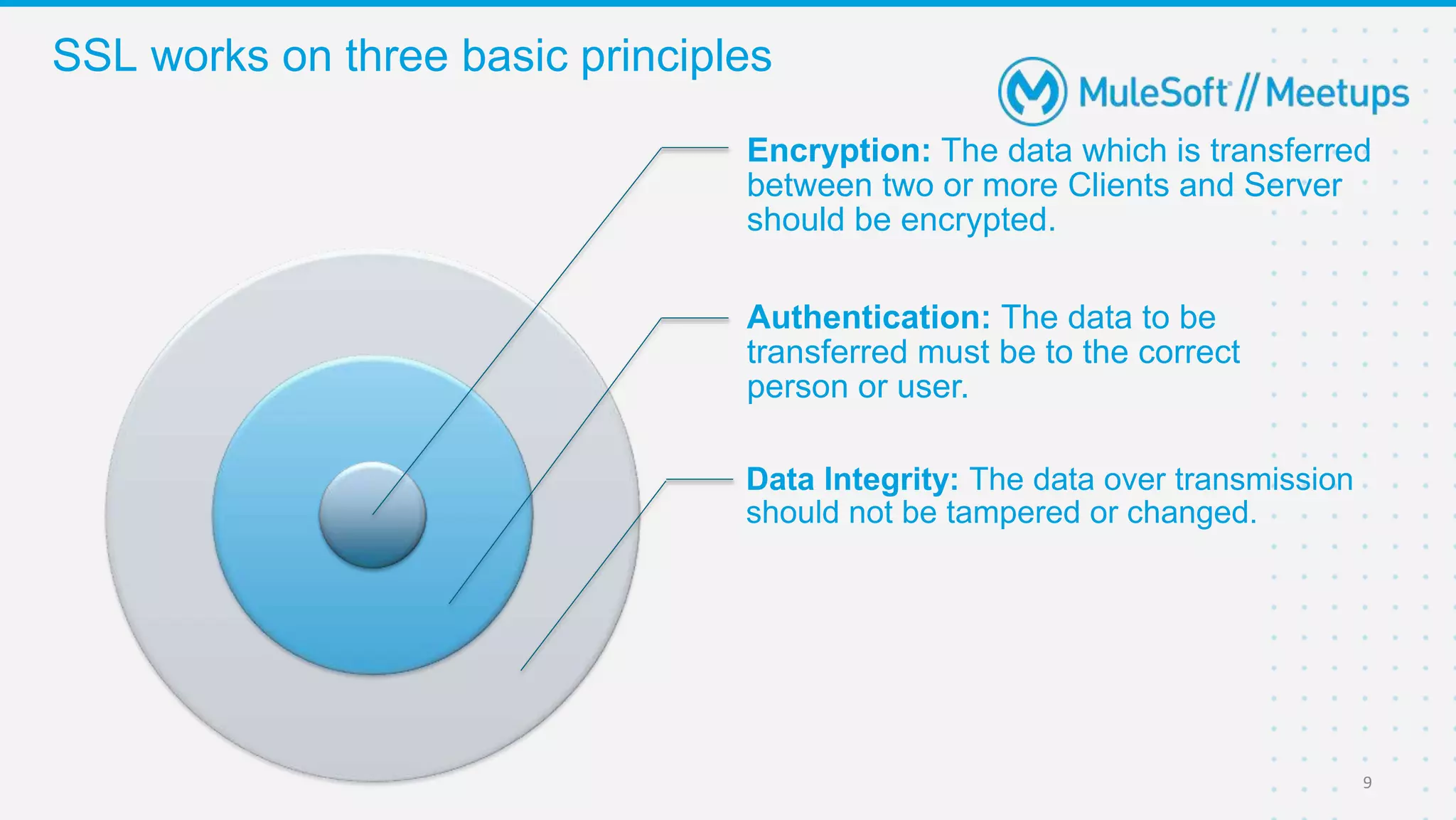
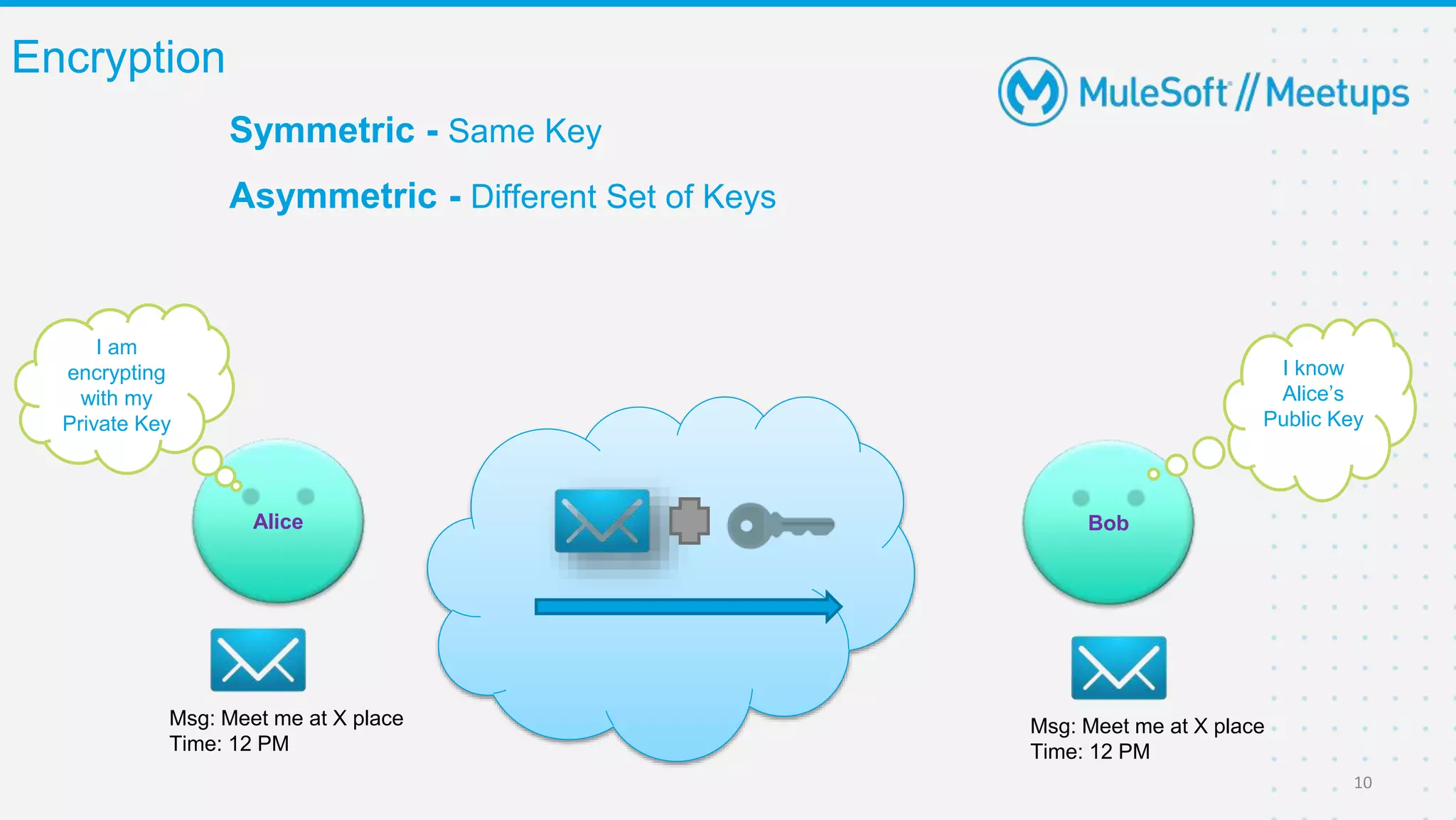
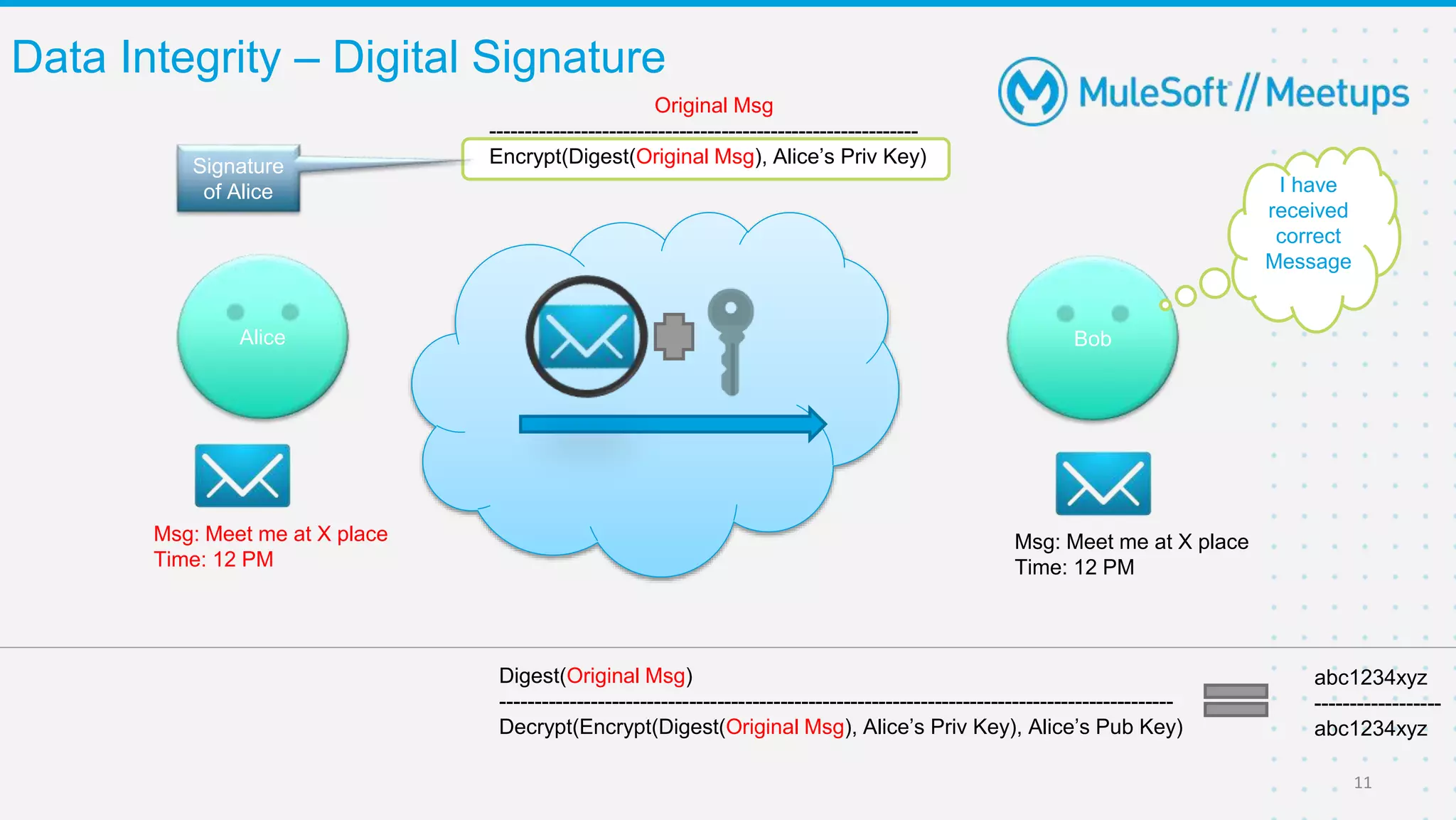
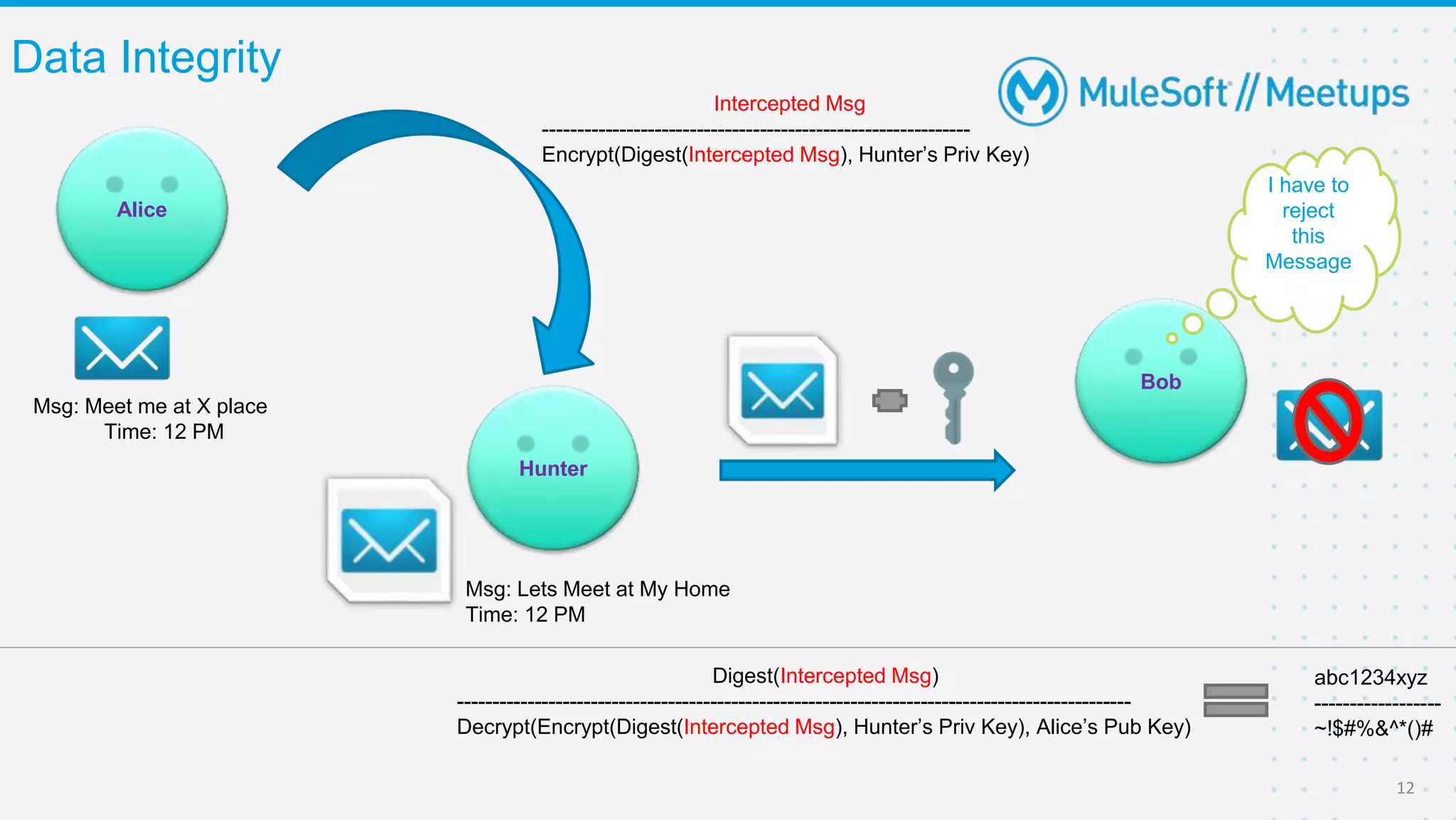
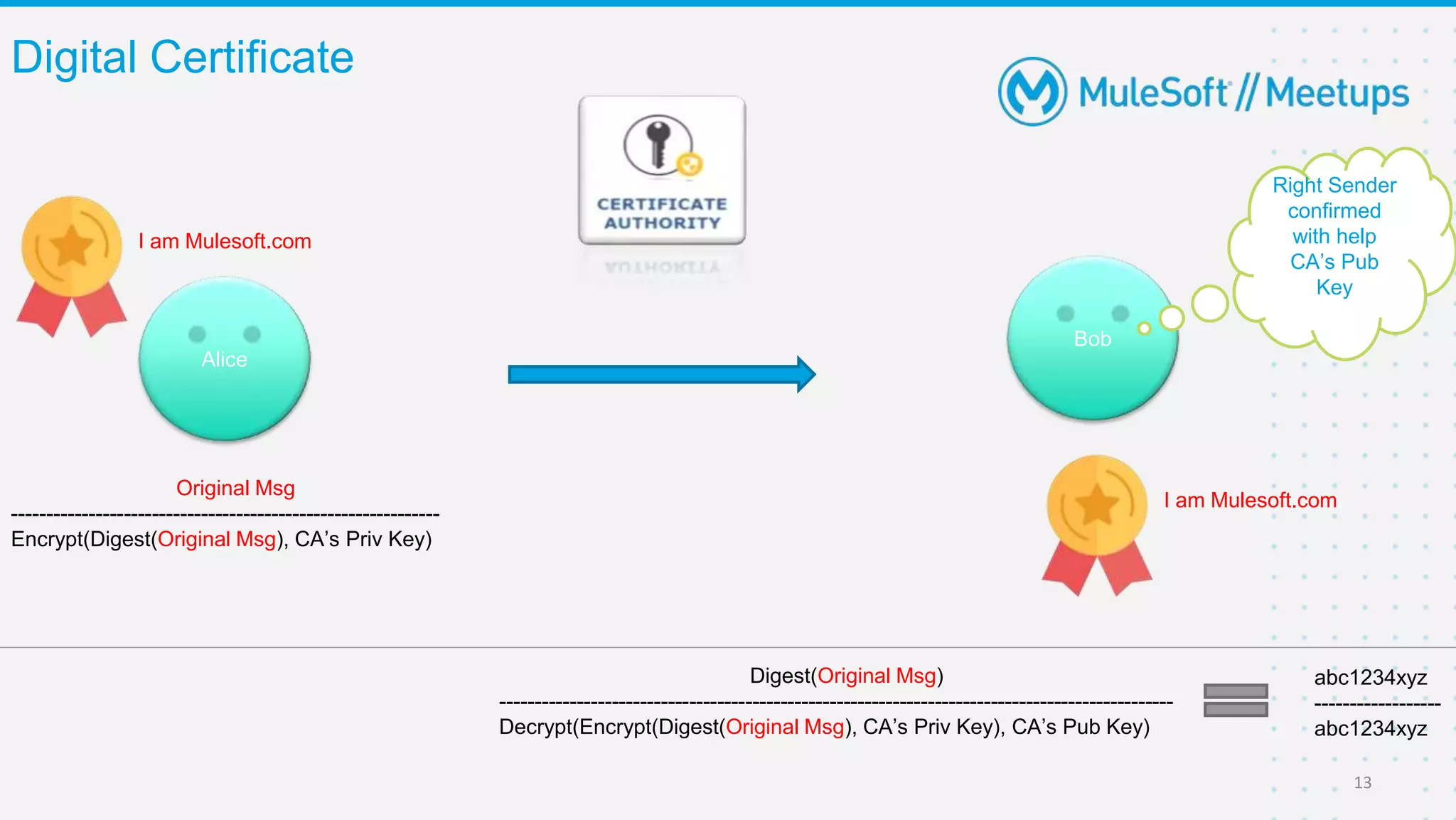
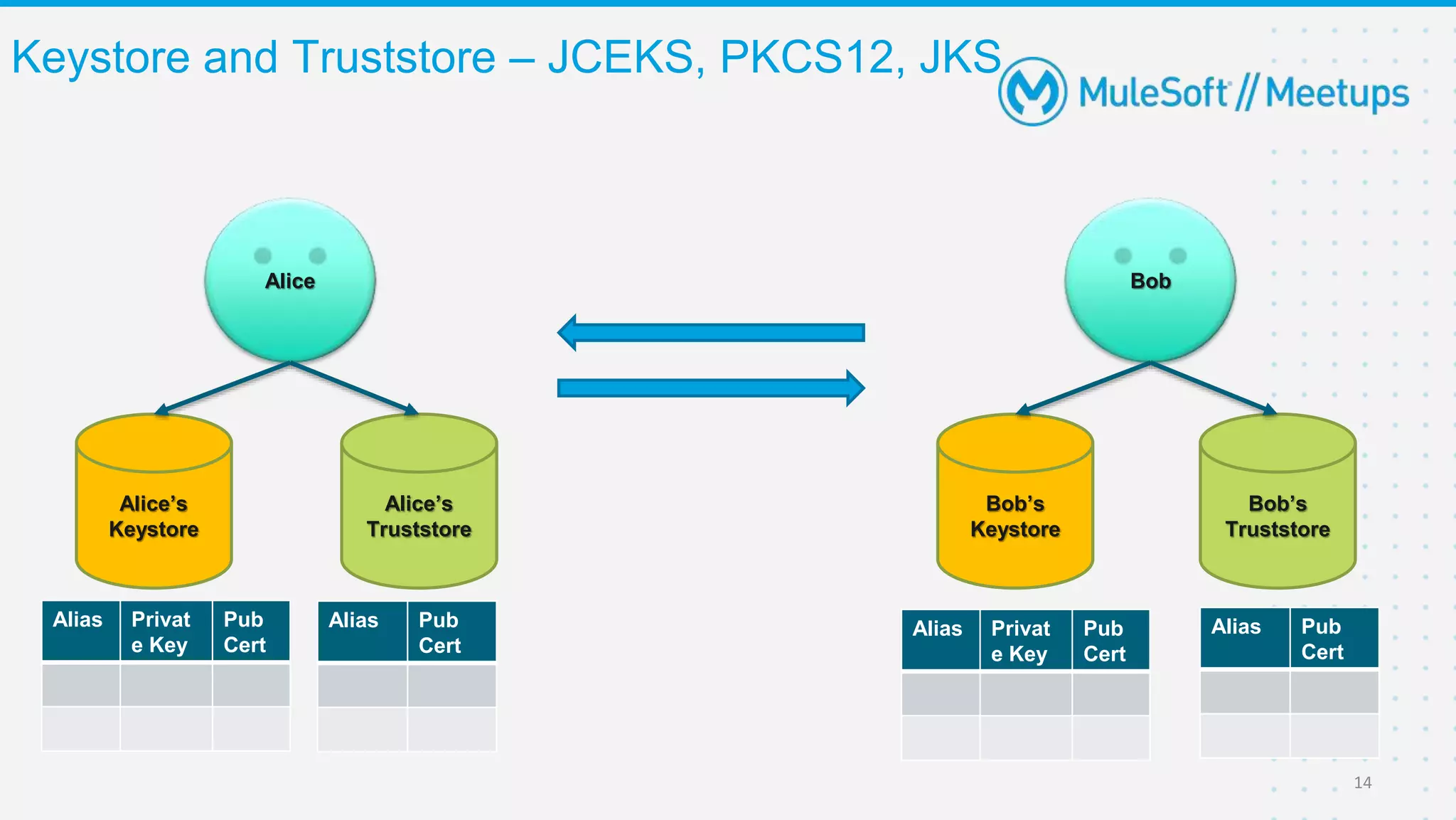
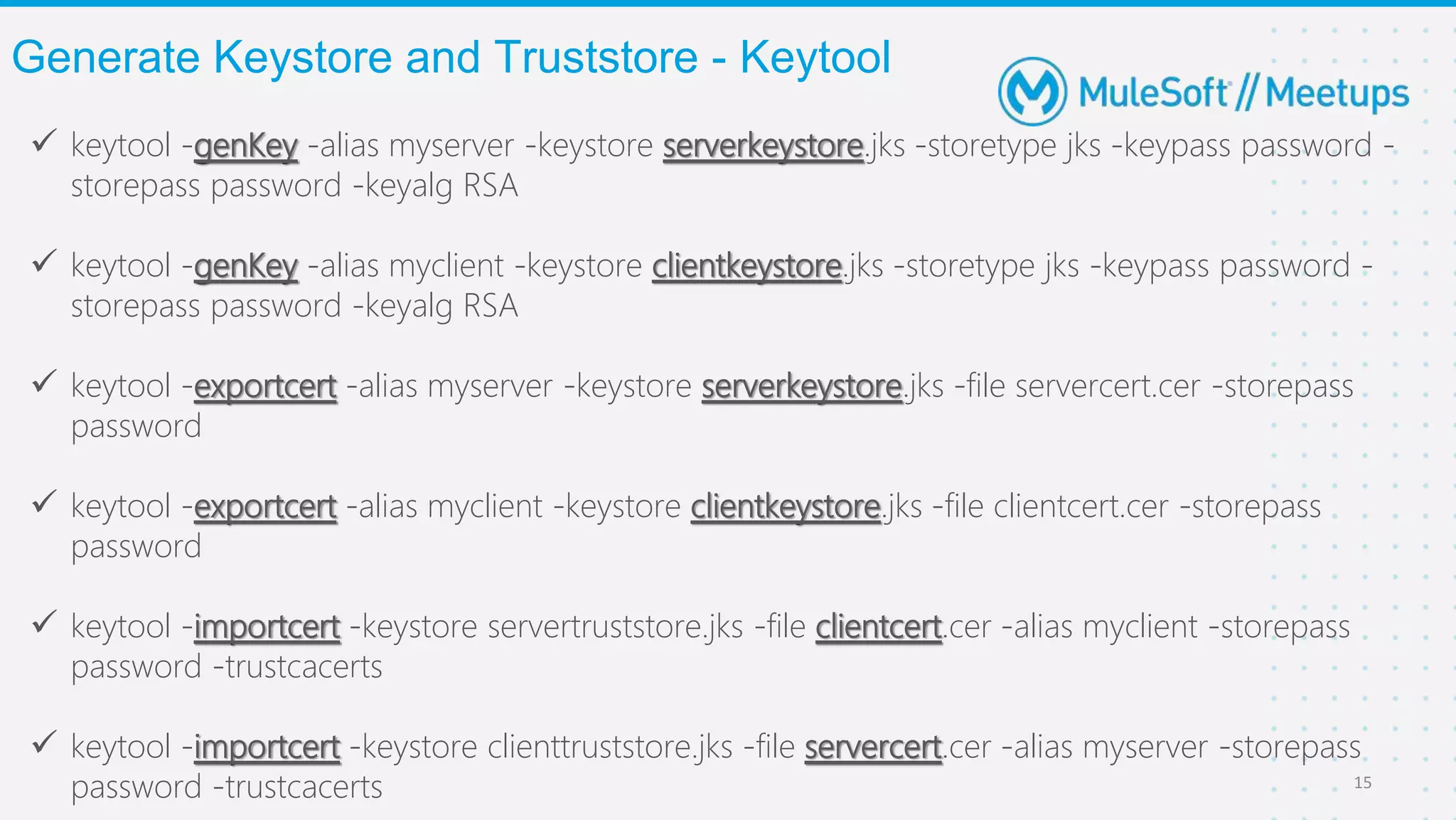
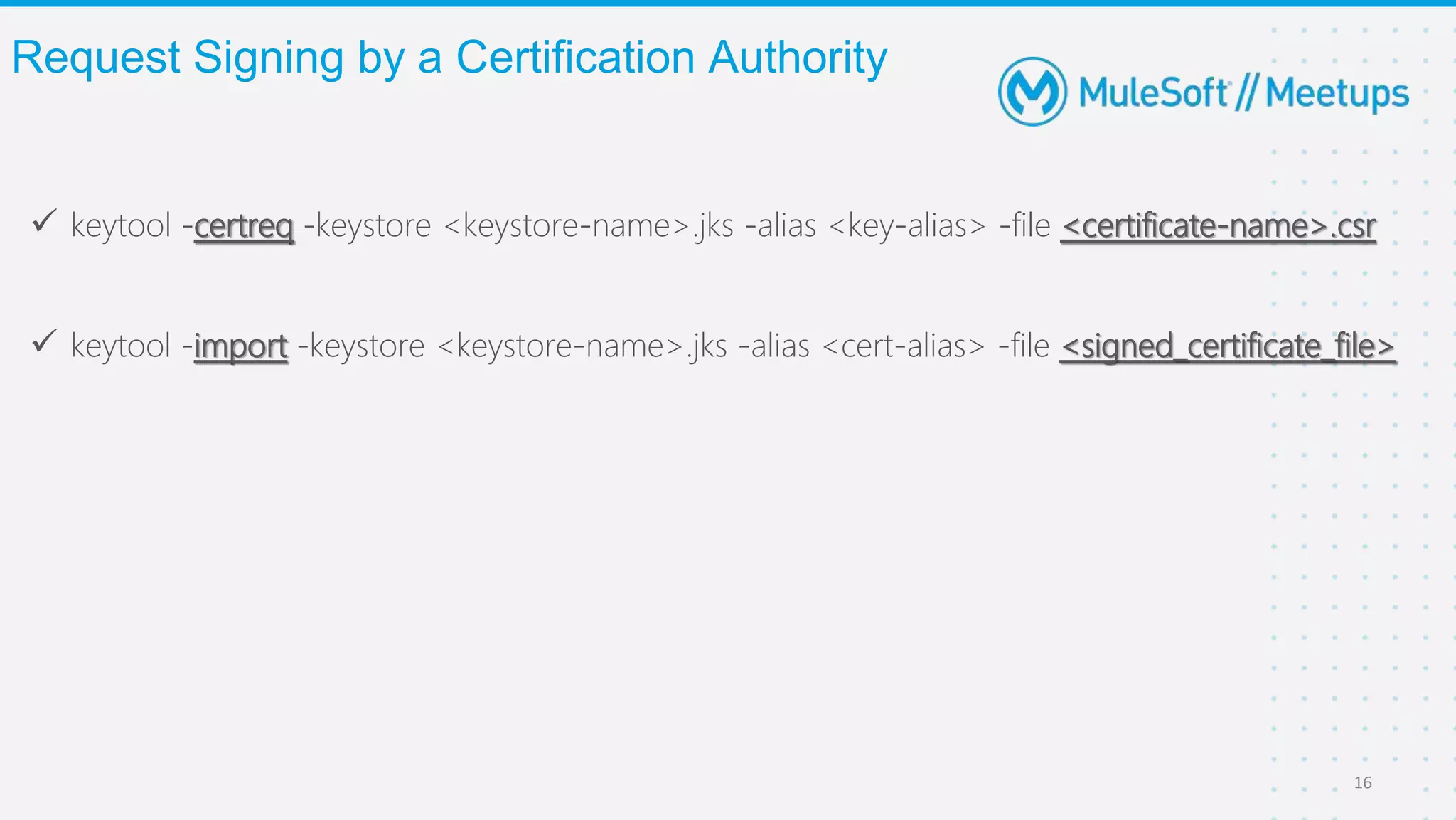
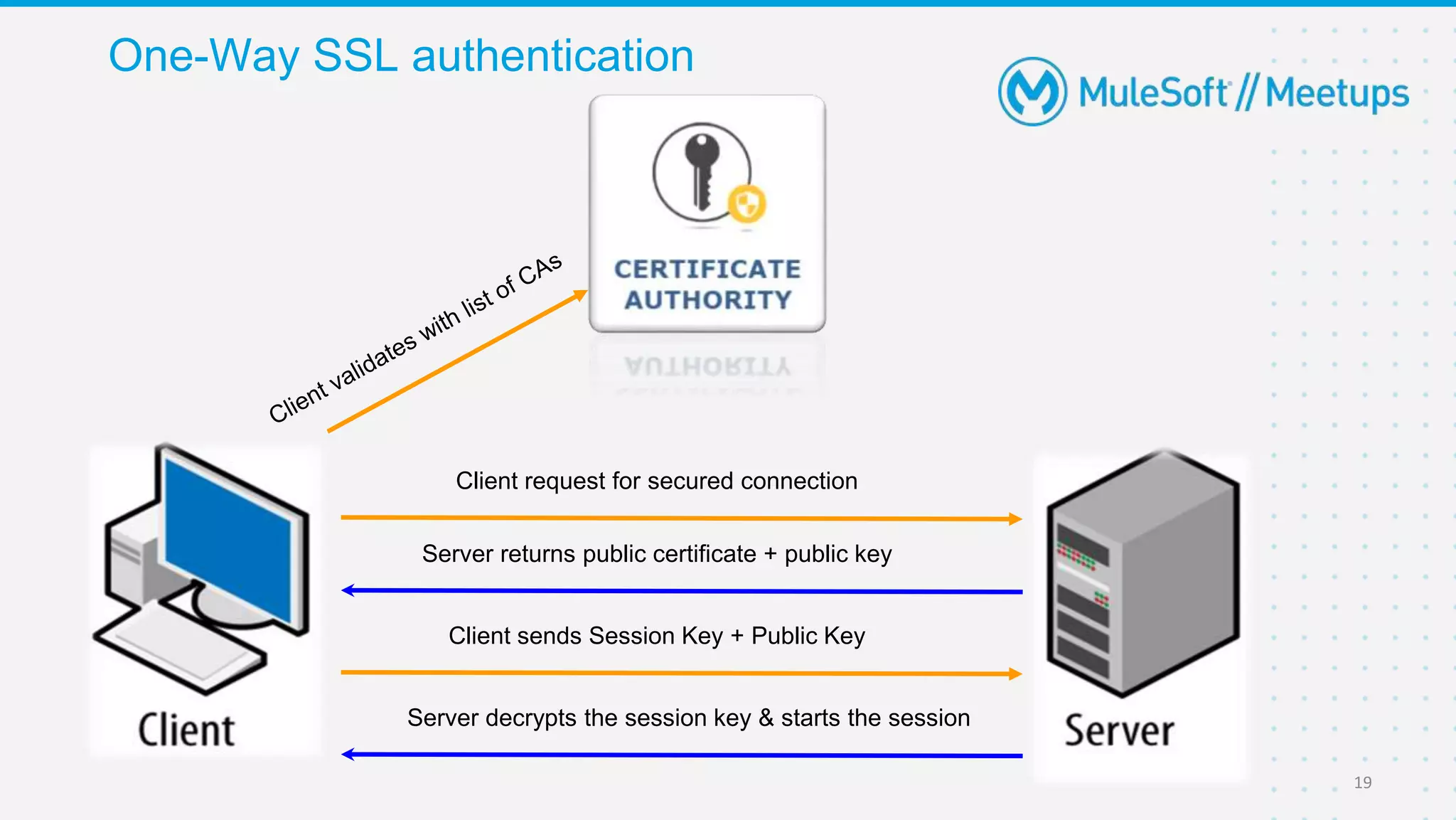
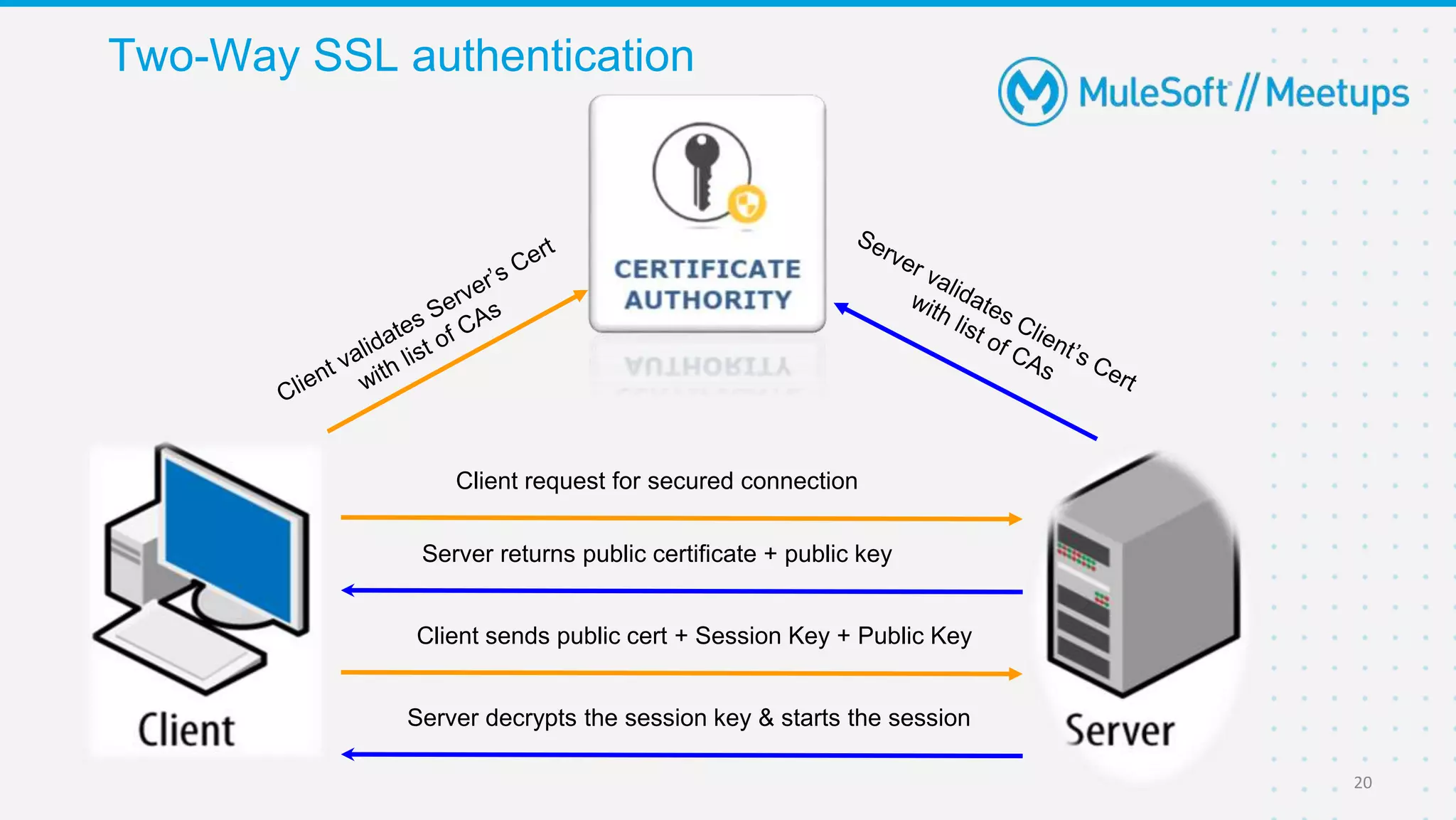
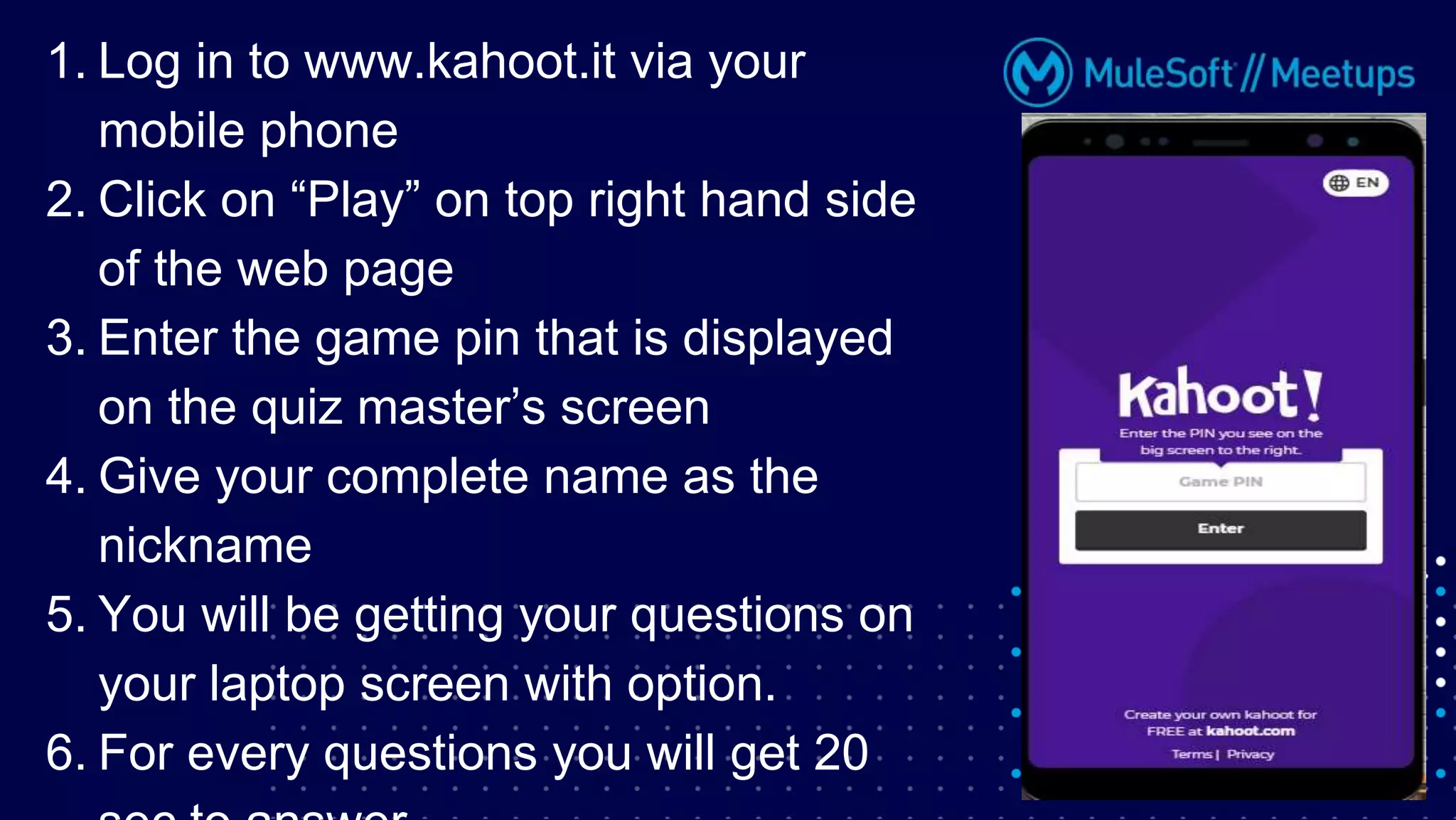
The Coimbatore Mulesoft Meetup discusses SSL/TLS, focusing on one-way and two-way SSL authentication methods, key generation, and digital certificates vital for secure network communications. Organizers include experienced Mulesoft professionals, and the event emphasizes community interaction and feedback. A quiz and future event announcements are also included in the meetup details.