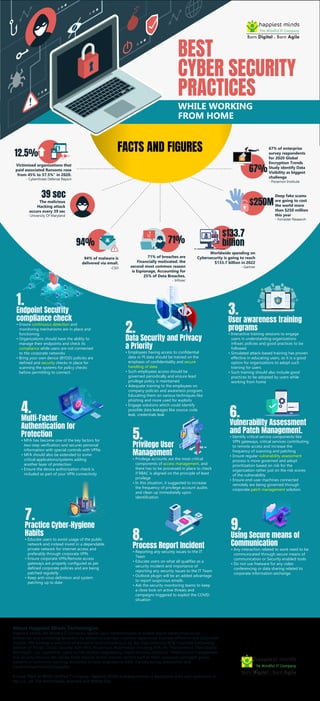
The document provides best practices and statistics for working from home cybersecurity. It lists that 94% of malware is delivered via email, 71% of breaches are financially motivated, and worldwide cybersecurity spending will reach $133.7 billion in 2022. The document also outlines nine key practices for remote work cybersecurity including endpoint security compliance, data security and privacy training, multi-factor authentication, vulnerability assessment and patch management, and using secure communication means.