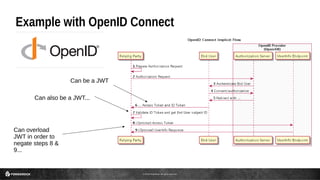
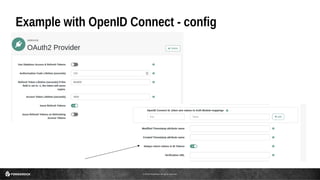
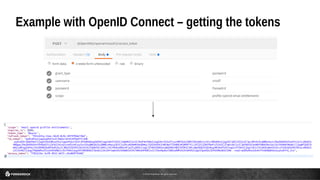
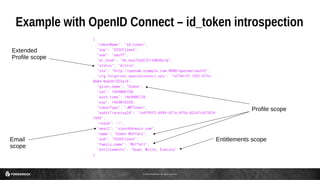
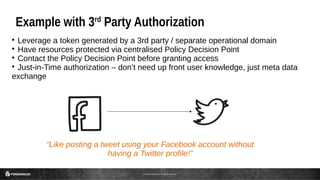
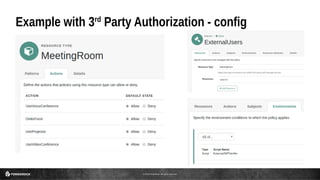
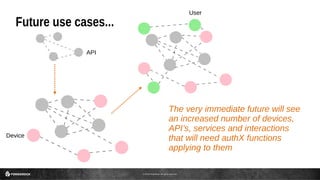
This document discusses the use of JSON Web Tokens (JWTs) for authorization. It provides an introduction to JWTs, describing their compact format and how they can be signed and contain claims. It then gives examples of using JWTs in OpenID Connect flows and for third-party authorization. Finally, it discusses some future use cases around hyper-scale authorization across many autonomous services and devices.