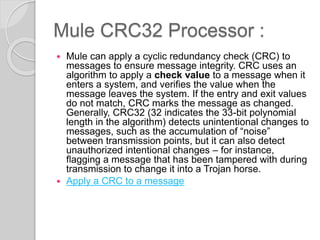
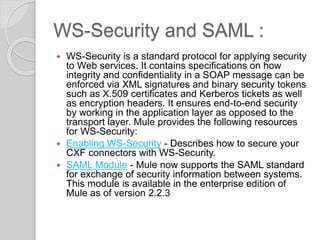
Anypoint Enterprise Security provides various security features in Mule applications, including the Mule Secure Token Service, Credentials Vault, message encryption and digital signature processors, and filters. These features help secure valuable application information from unauthorized access while allowing authorized users and systems to access data. Security is configured in Mule through the Security Manager and supports standards like Spring Security, WS-Security, and SAML. As of version 3.5.0, Mule can also be configured to run in FIPS 140-2 compliant mode for additional security.