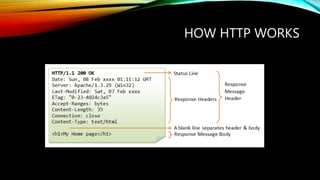
This document provides an overview of security best practices for developers. It discusses the software development lifecycle (SDLC) and phases like planning, architecture, testing, and release. It also summarizes Microsoft's recommendations for securing the SDLC, which include training, defining security requirements, threat modeling, using cryptography standards, and regularly penetration testing. The document then covers topics like how HTTP works with different request and response types, common vulnerabilities from the OWASP Top 10, and ways to test applications through penetration testing and bug bounty programs. It provides tips on applying security best practices and knowing about new vulnerabilities, and recommends securing continuous integration/continuous delivery (CI/CD) through techniques like code analysis, container hardening, and