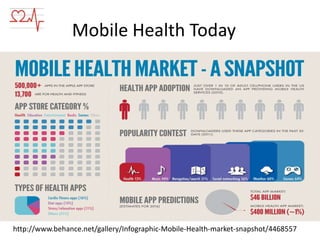
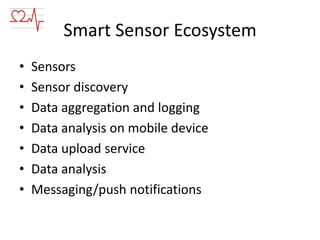
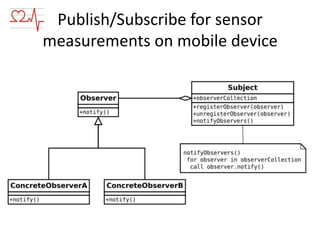
This document discusses wearable sensors and their use in collecting human wellness data. It notes that wearable technology is becoming a $6 billion market by 2016. Key points include: sensors can collect various health data; mobile devices can process this data; challenges include managing large amounts of data from many sensors; mistakes include improperly uploading all data or relying on single sensors; performing analysis on the sensor or mobile device filters data before uploading; and applications include wellness advice, health monitoring, and medical uses like remote patient monitoring. Security, FDA regulations, and developing a smart sensor ecosystem are also addressed.