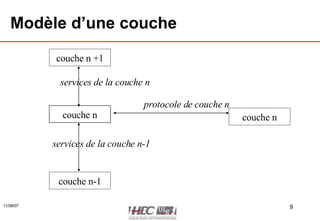
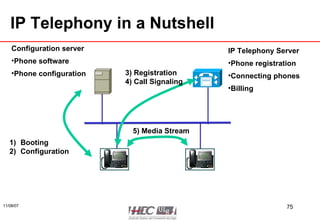
The document discusses network technologies and concepts. It covers topics like network layers, IP addressing, routing, and protocols. It provides an overview of common network standards and technologies used in both home and enterprise networks, such as Ethernet, switches, WiFi, and IP routing.
![Veille technologique en TIC Aspects stratégiques des réseaux Eric Vyncke [email_address] Dernière mise à jour: 7 novembre 2007](https://image.slidesharecdn.com/aspects-stratgiques-des-rseaux-1194551999604724-4/75/Aspects-Strategiques-des-Reseaux-1-2048.jpg)
![References & Misc Slides on http://mastertic.blogspot.com/ Contacts Main job: Cisco Systems as Distinguished Engineer Email: [email_address] Mobile: +32 475 312458](https://image.slidesharecdn.com/aspects-stratgiques-des-rseaux-1194551999604724-4/85/Aspects-Strategiques-des-Reseaux-2-320.jpg)