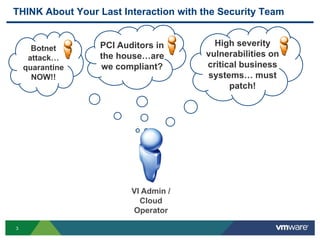
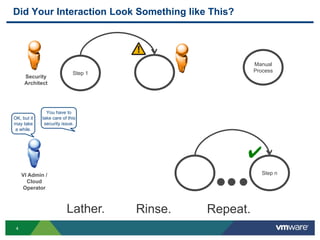
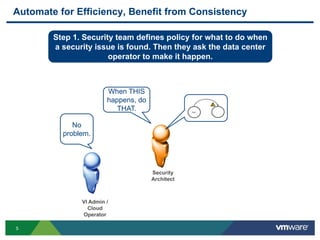
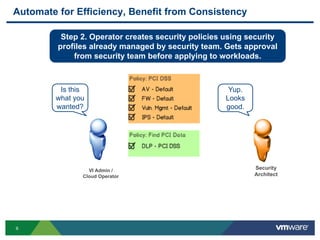
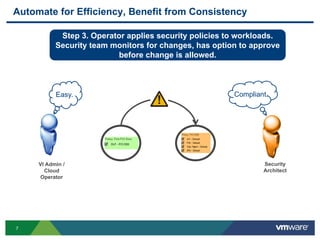
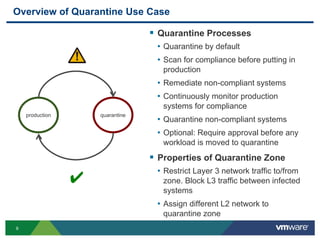
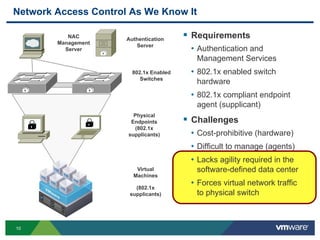
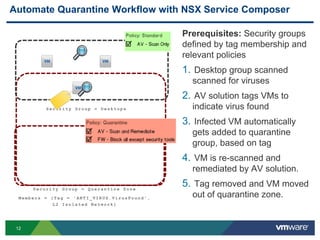
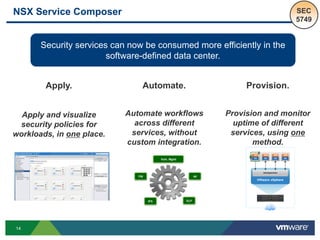
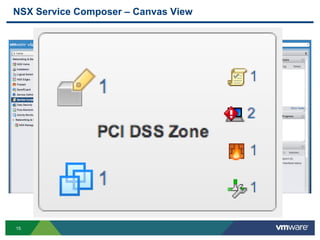
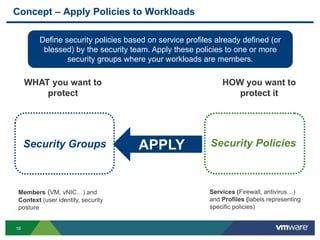
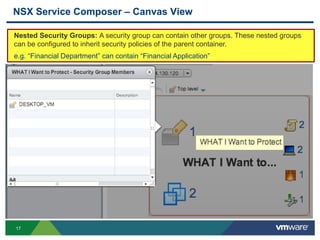
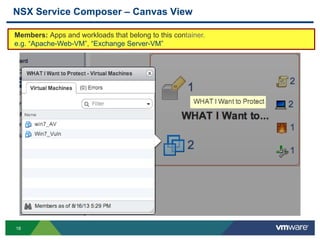
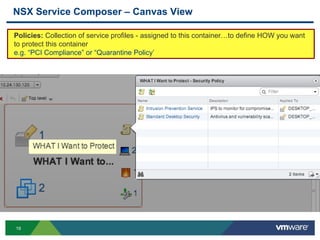
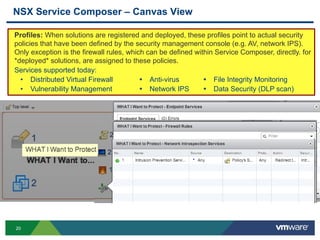
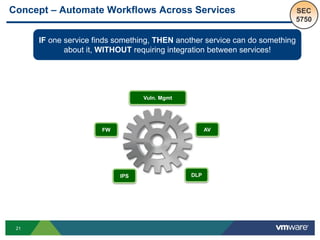
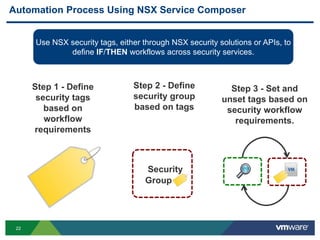
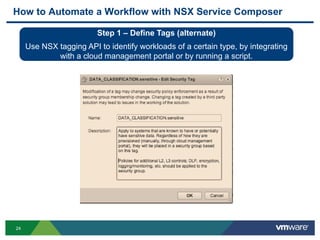
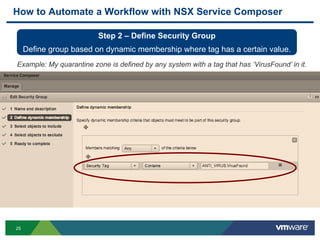
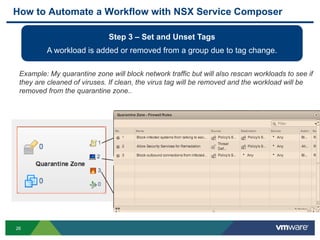
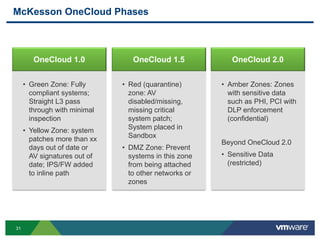
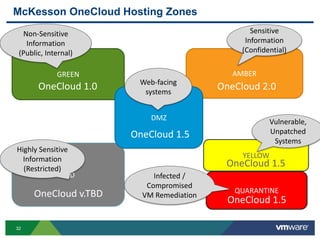
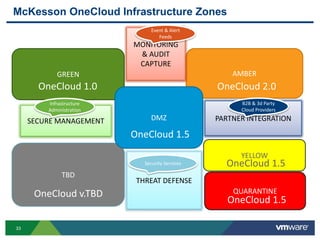
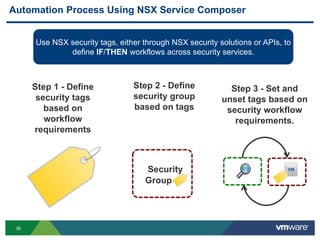
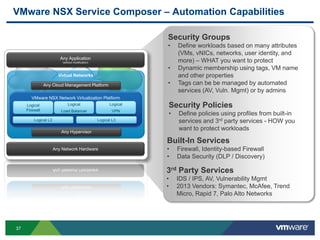
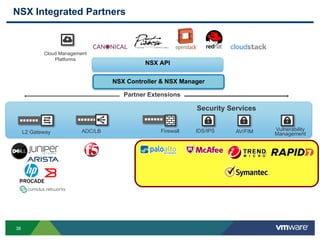
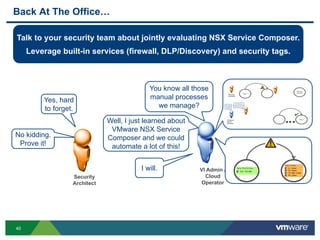
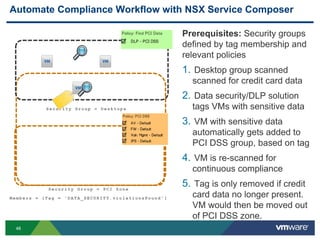
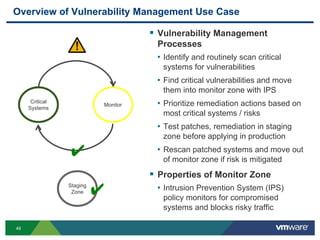
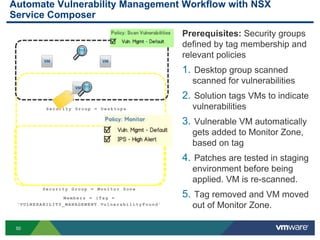
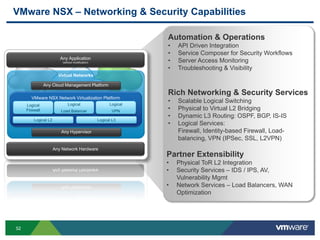
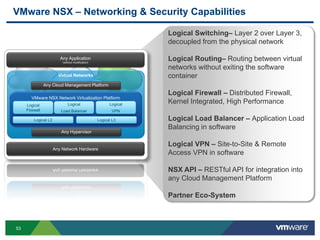
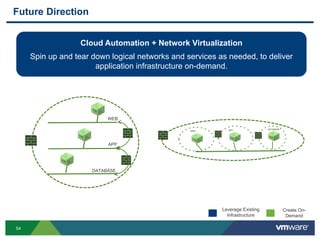
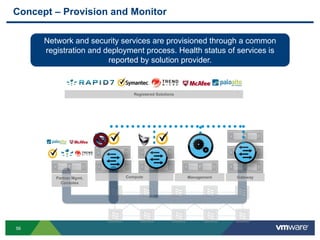
The document discusses the automation of security workflows using VMware's NSX Service Composer, emphasizing efficiency and consistency in handling security issues. It outlines a step-by-step approach to automate quarantine processes for infected systems and outlines the integration of compliance and vulnerability management workflows. Additionally, it highlights the benefits and capabilities of NSX in a software-defined data center, along with a case study on McKesson's use of the OneCloud platform.