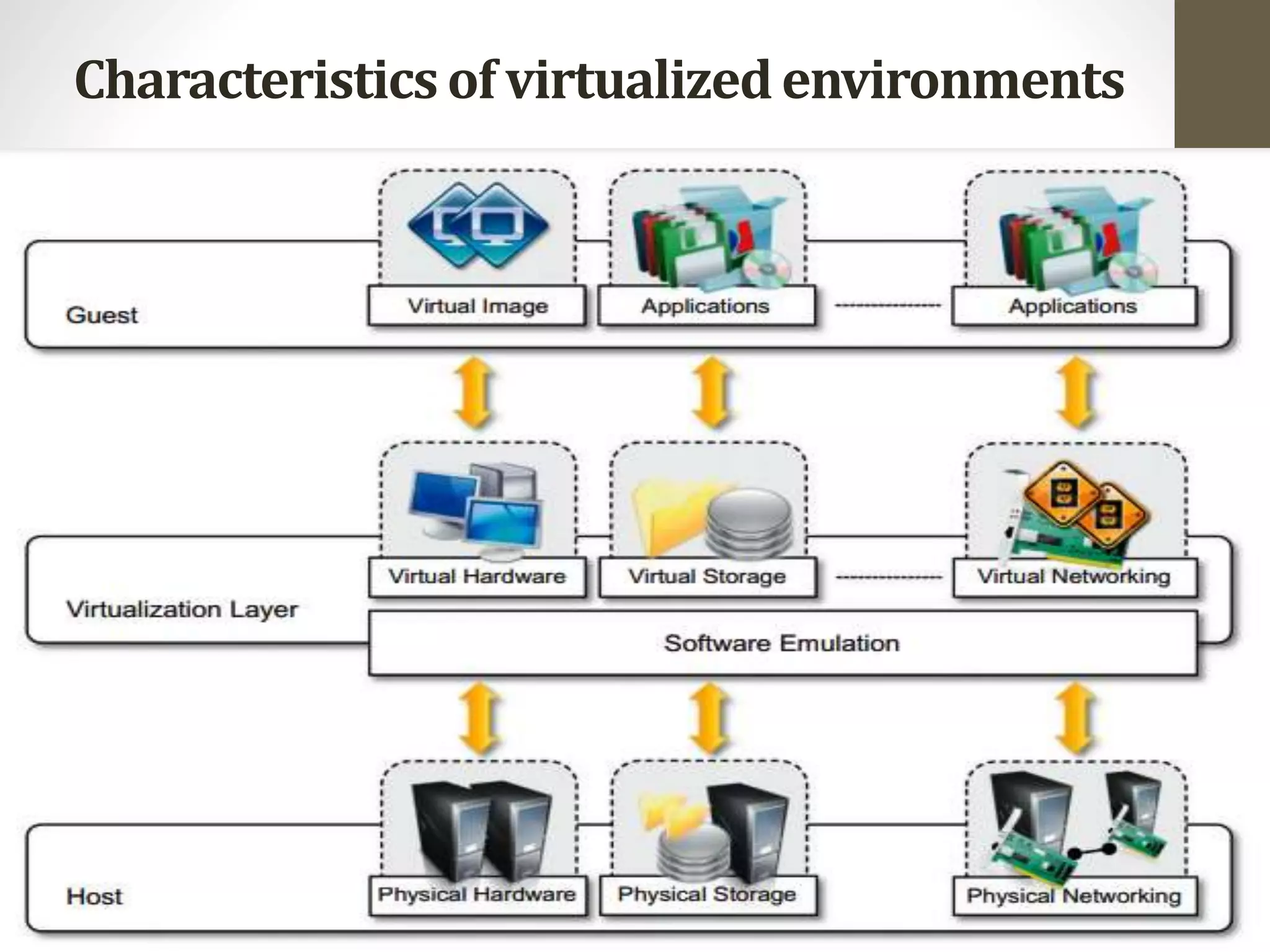
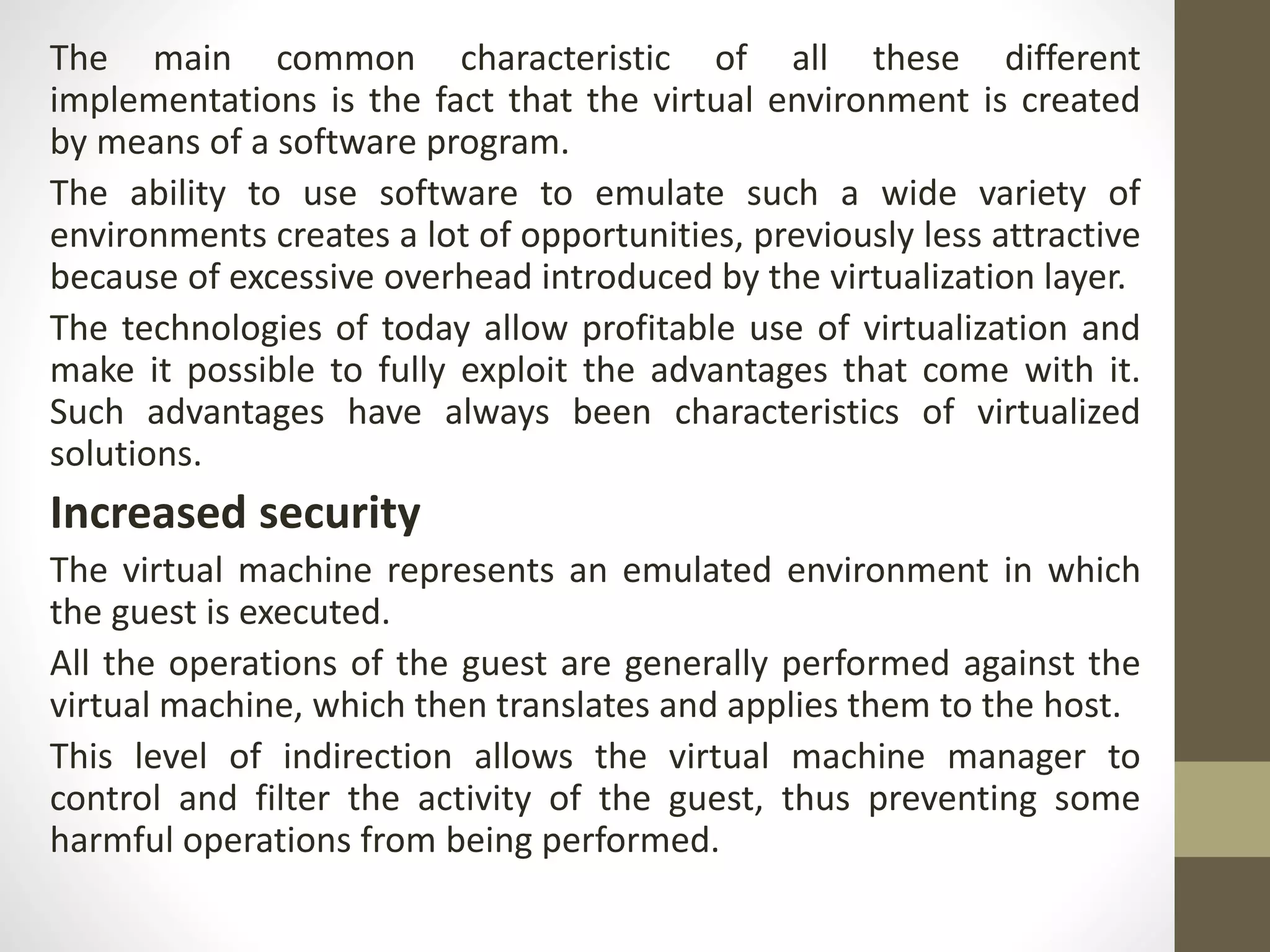
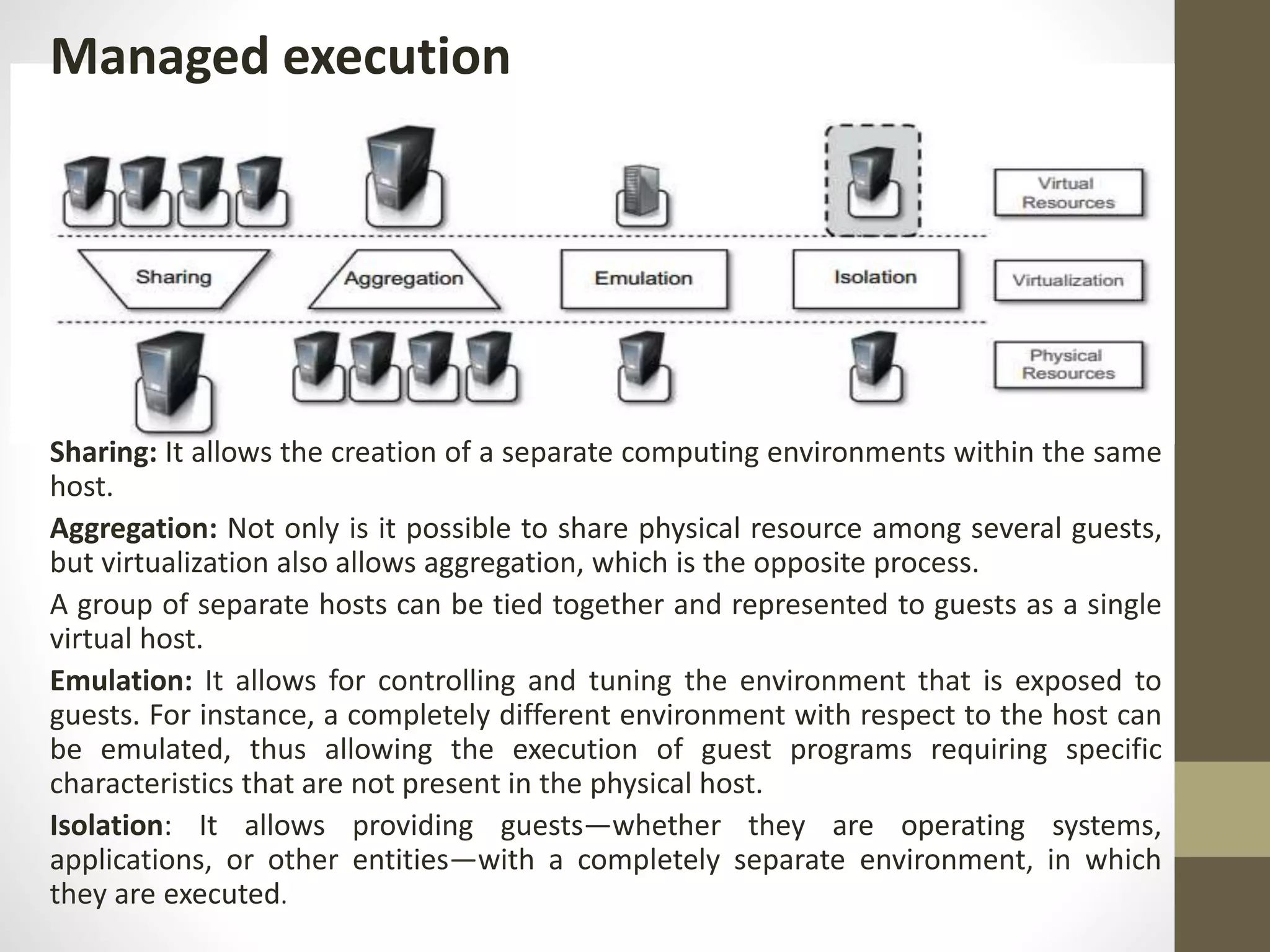
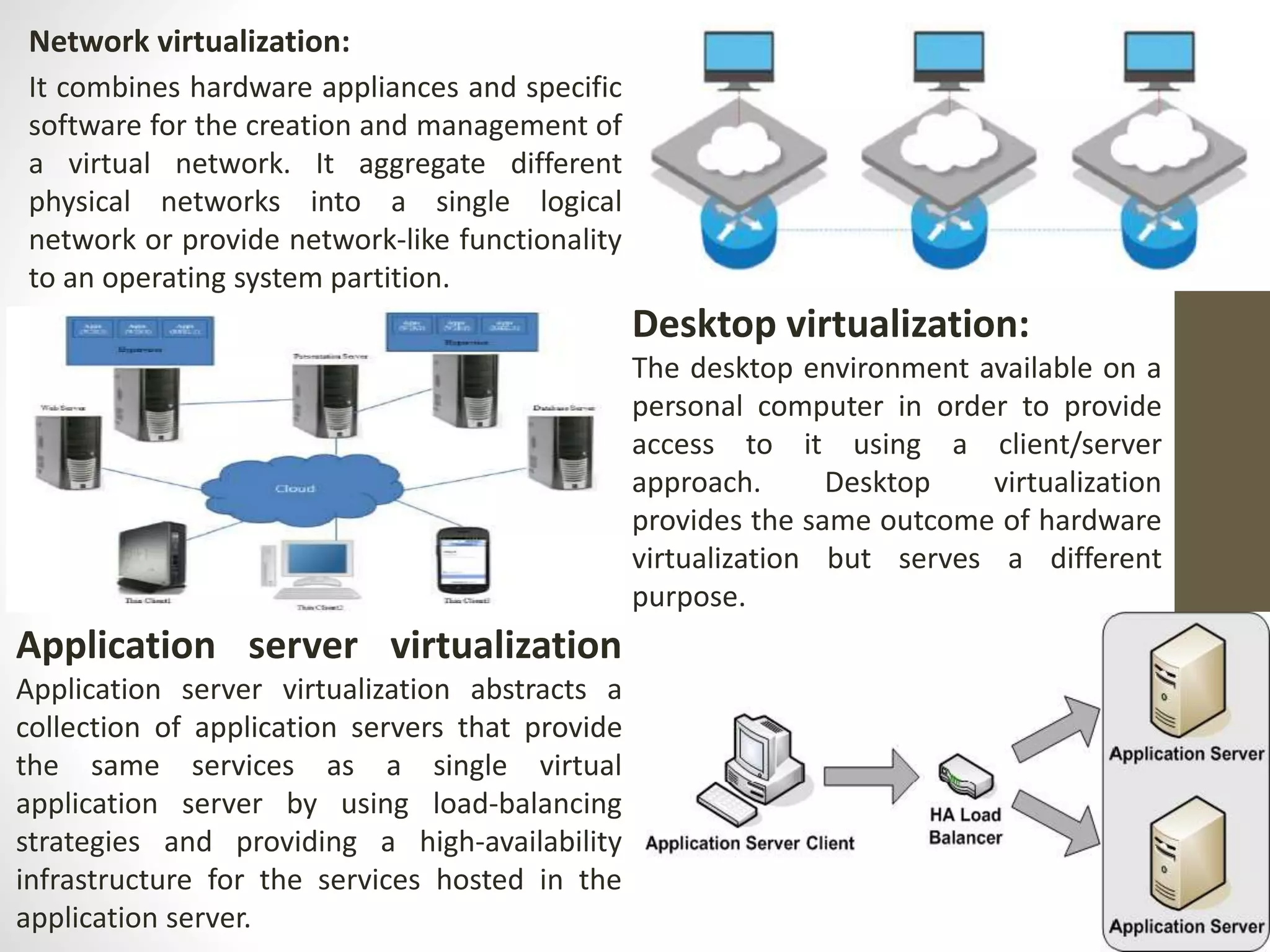
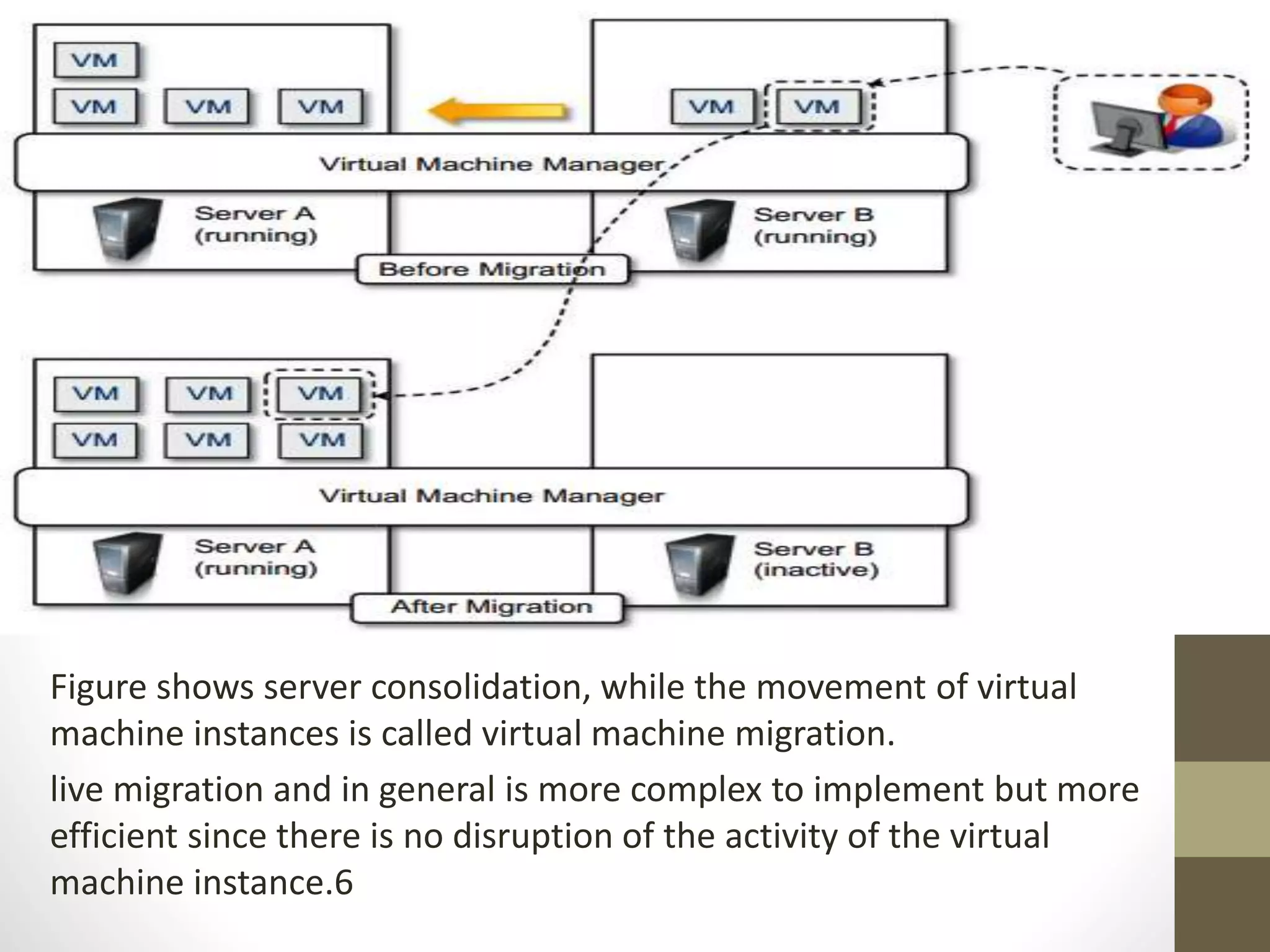
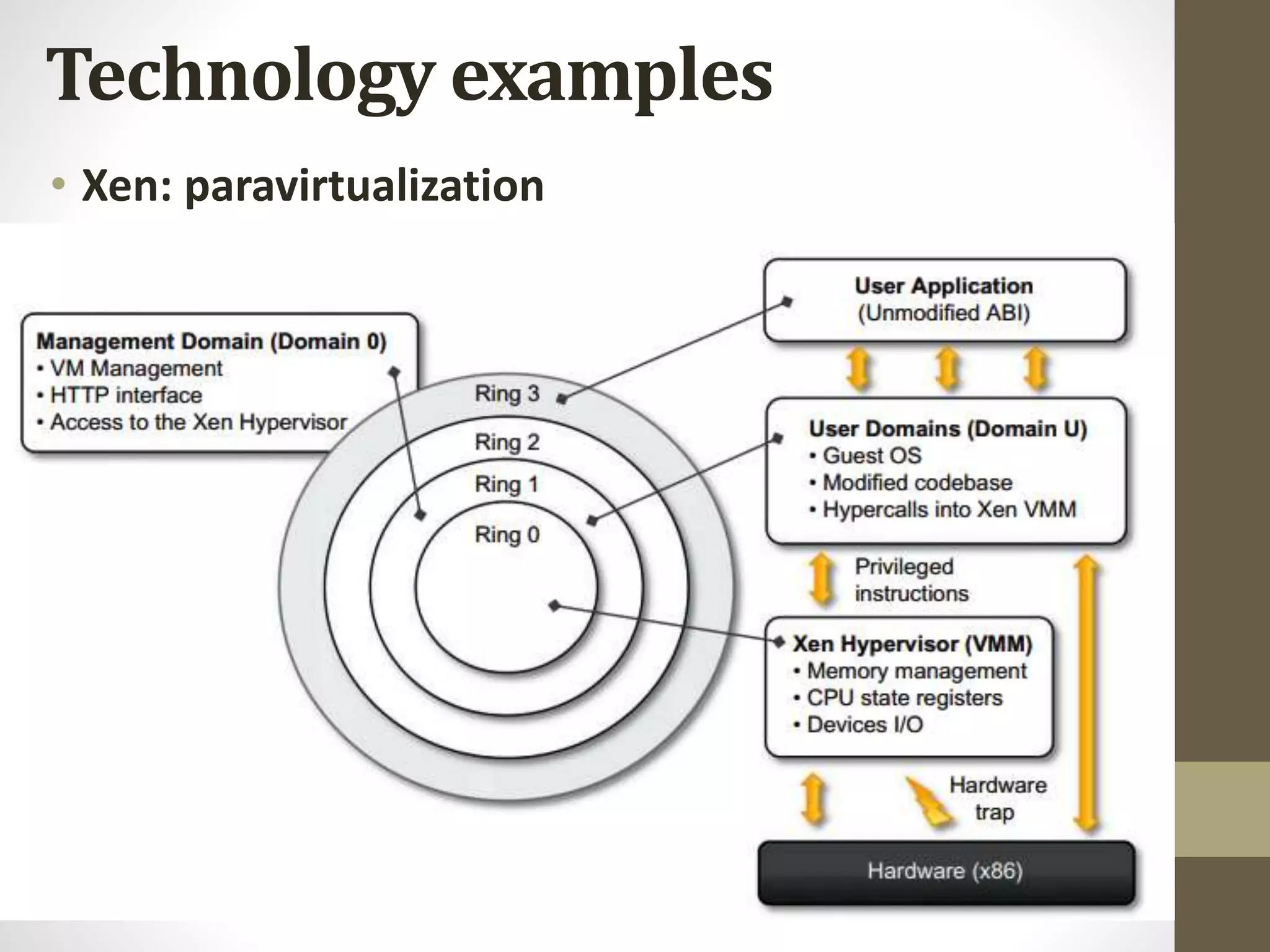
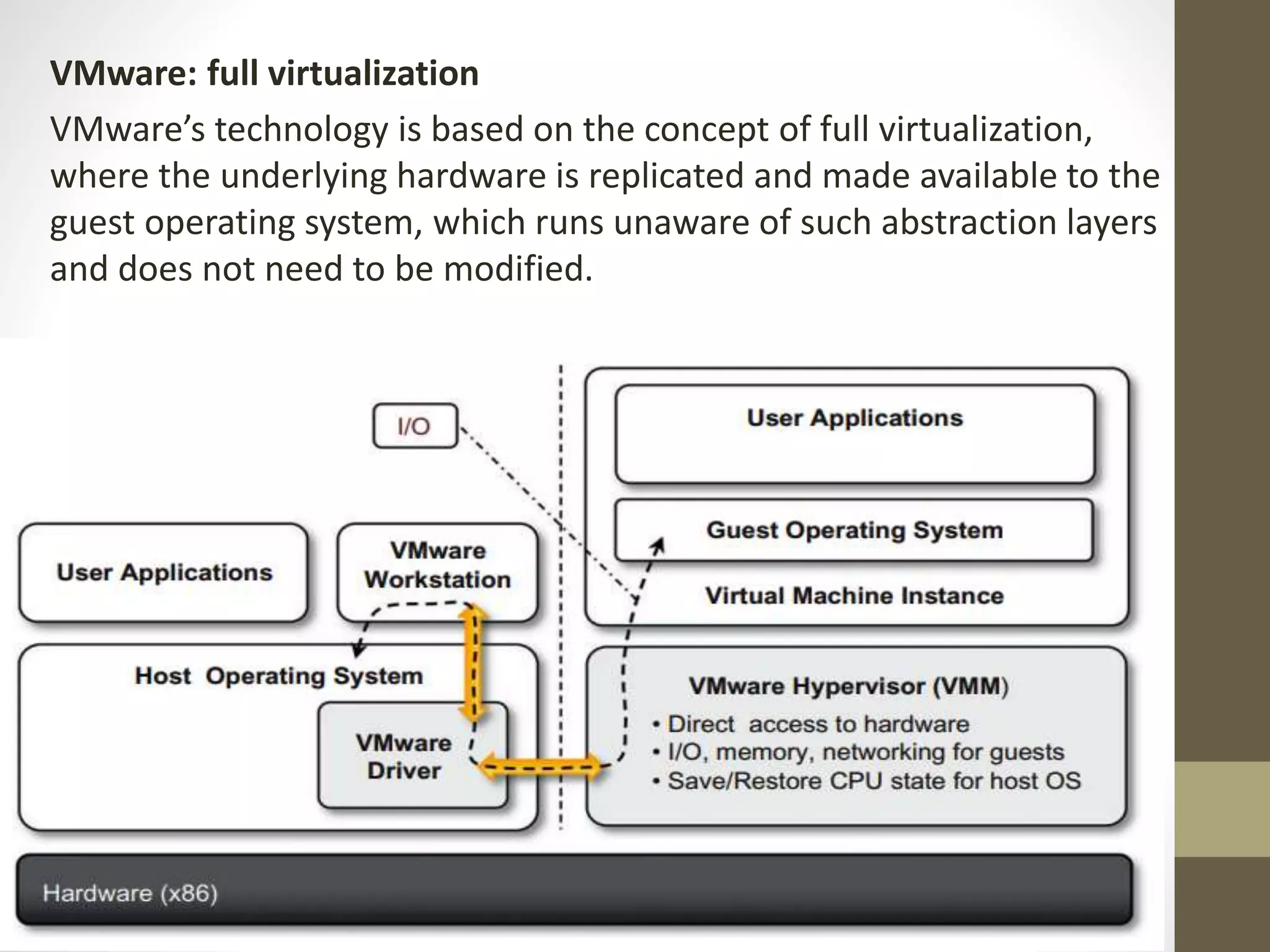
Virtualization in cloud computing creates secure and customizable execution environments for applications, allowing for scalable systems with resource efficiency. It provides benefits such as increased security, isolation, managed execution, and portability across platforms. While virtualization offers advantages like lower maintenance costs, it also presents challenges such as performance degradation and potential security vulnerabilities.