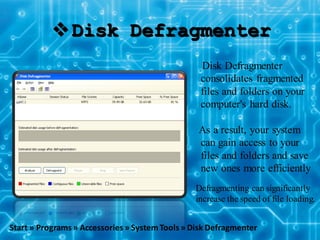
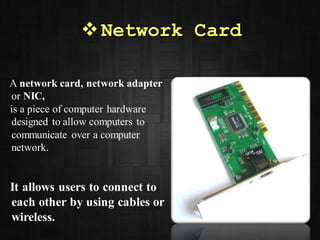
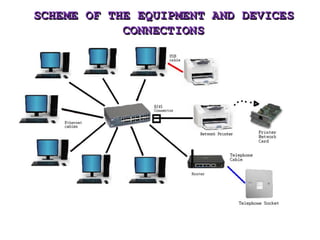
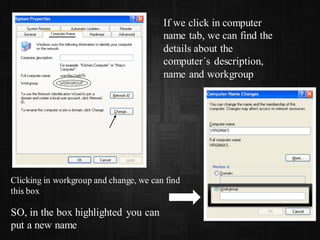
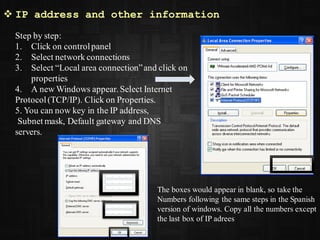
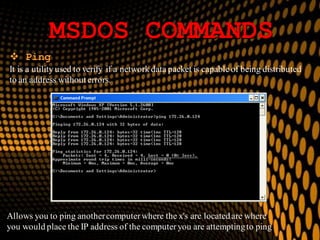
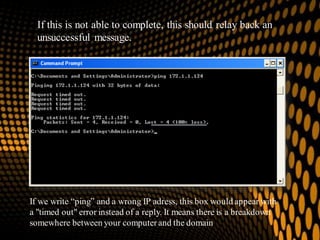
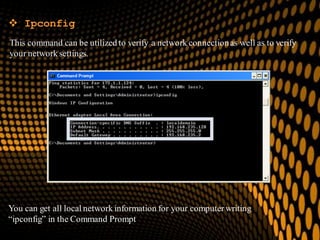
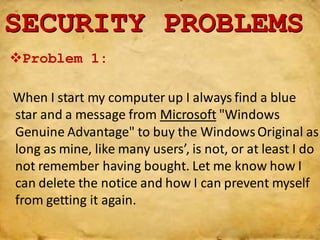
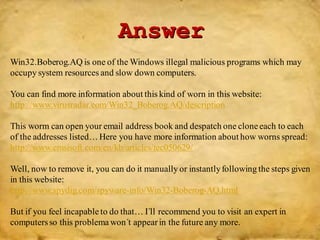
This document provides information on various Windows tools for system information, security, restore points, character input, disk defragmentation, and network hardware components. It discusses the System Information tool for viewing computer details, Security Center for checking security essentials, System Restore for reverting system files to earlier points, Character Map for inserting symbols, and Disk Defragmenter for consolidating fragmented files. It also outlines common network hardware like network interface cards, cables, repeaters and hubs, and routers. The document provides instructions for configuring network settings like computer name, workgroup, and IP address in Windows. It explains the ping and ipconfig commands used to verify network connectivity and settings. Finally, it addresses two security problems