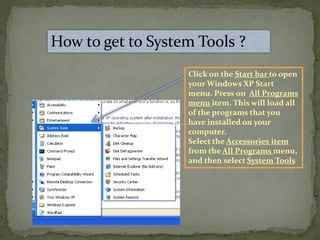
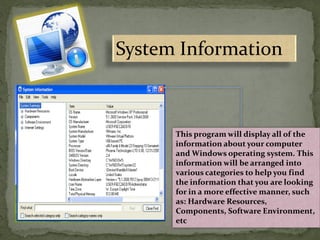
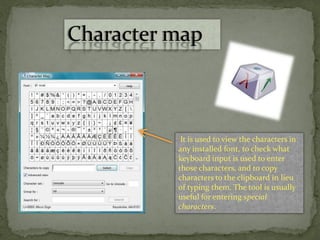
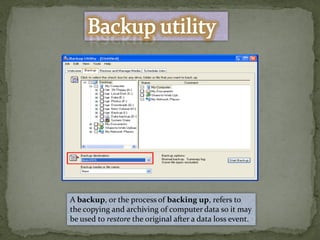
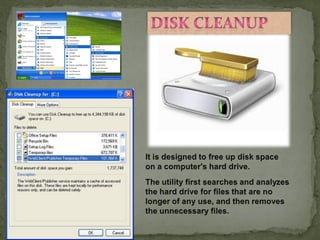
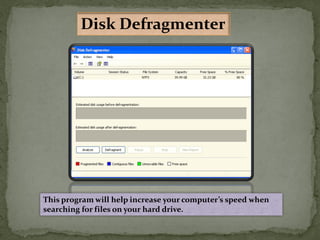
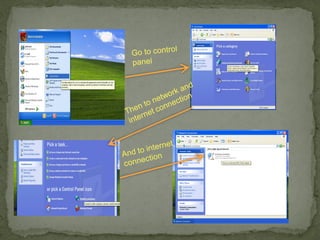
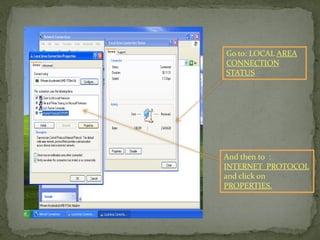
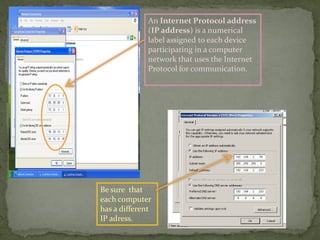
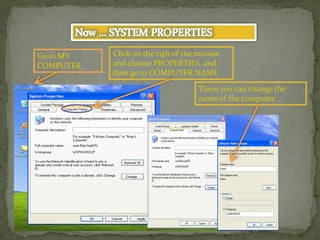
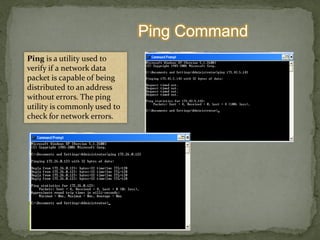
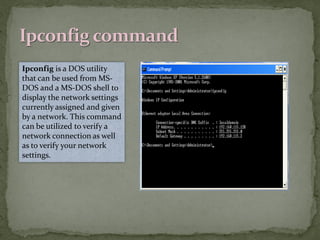
This document provides instructions for accessing System Tools in Windows XP. It explains that you first click the Start button to open the Start menu. Then select the All Programs menu item, which loads all installed programs. From there, select Accessories then System Tools to access programs like System Information, Character Map, and Disk Defragmenter.