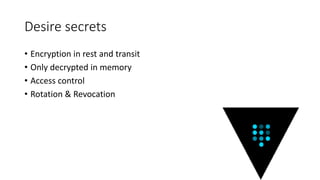
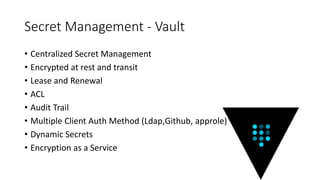
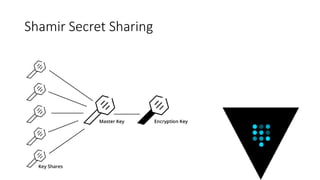
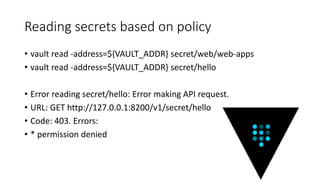
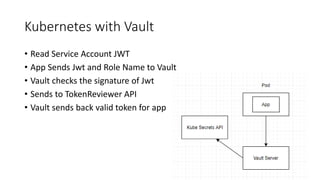
The document discusses the management of secrets in Node.js applications using Vault, highlighting the risks associated with secret sprawl in source code and configuration management. It details Vault's capabilities for centralized secret management, including encryption, access controls, dynamic secrets, and an audit trail while emphasizing the importance of securely unsealing the vault with multiple keys. Additionally, it covers practical applications for integrating Vault with Docker and Kubernetes for secure authentication and role-based access control.