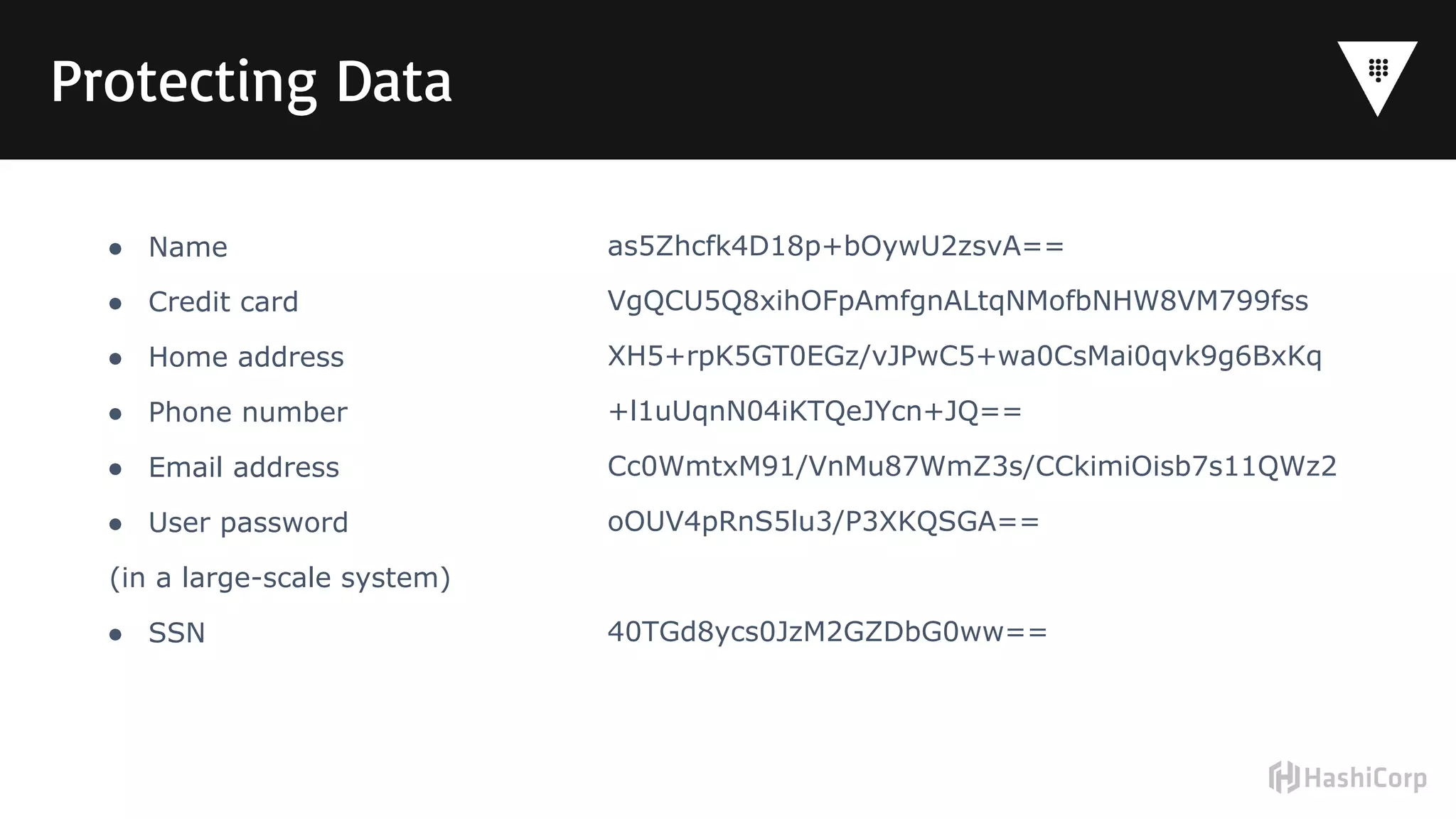
Vault is a tool for centrally managing secrets like passwords, API keys, and certificates. It addresses the problem of "secrets sprawl" where credentials are stored insecurely in multiple places like source code, emails, and configuration files. Vault centralizes secrets management, provides access control and auditing, and generates unique short-lived credentials to reduce risk if a secret is compromised. It also supports encrypting sensitive data for additional protection. Implementing Vault involves deciding where it will run, who will manage encryption keys, which secrets it will store, where audit logs will go, and who will operate and configure the system on an ongoing basis.















![Example
path "secret/training_*" {
capabilities = ["create", "read"]
}
base.hcl](https://image.slidesharecdn.com/secretssprawlwebinar-180713074552/75/Eliminating-Secret-Sprawl-in-the-Cloud-with-HashiCorp-Vault-07-11-2018-19-2048.jpg)