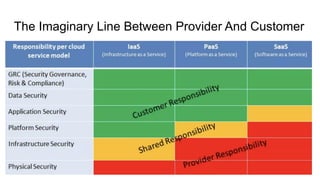
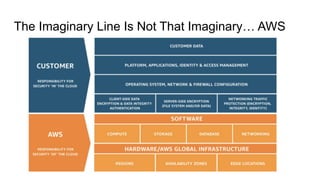
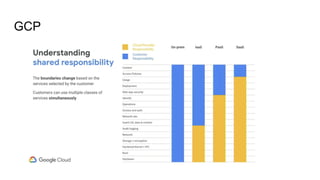
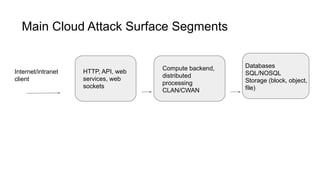
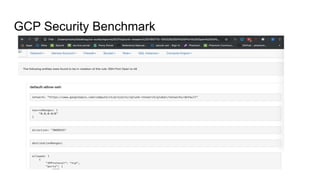
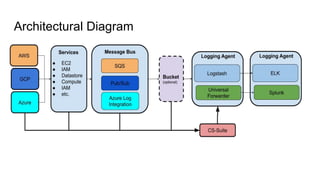
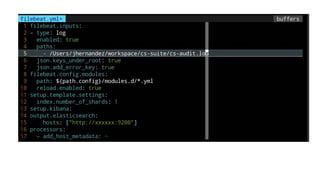
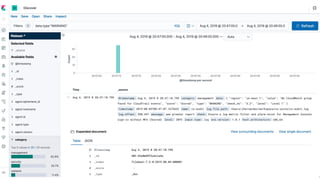
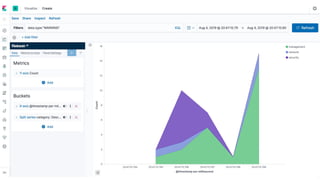
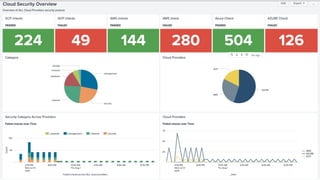
This document discusses using Splunk/ELK to audit the security posture of cloud environments like AWS, GCP, and Azure. It introduces Rod Soto and José Hernandez, security researchers at Splunk. It then outlines common cloud attack vectors and targets. It proposes common criteria for auditing cloud security across compute, management, storage, security, and network areas. Finally, it introduces the Cloud Security Suite tool for unified auditing across clouds and how outputs can be integrated with Splunk/ELK for analysis and alerting.