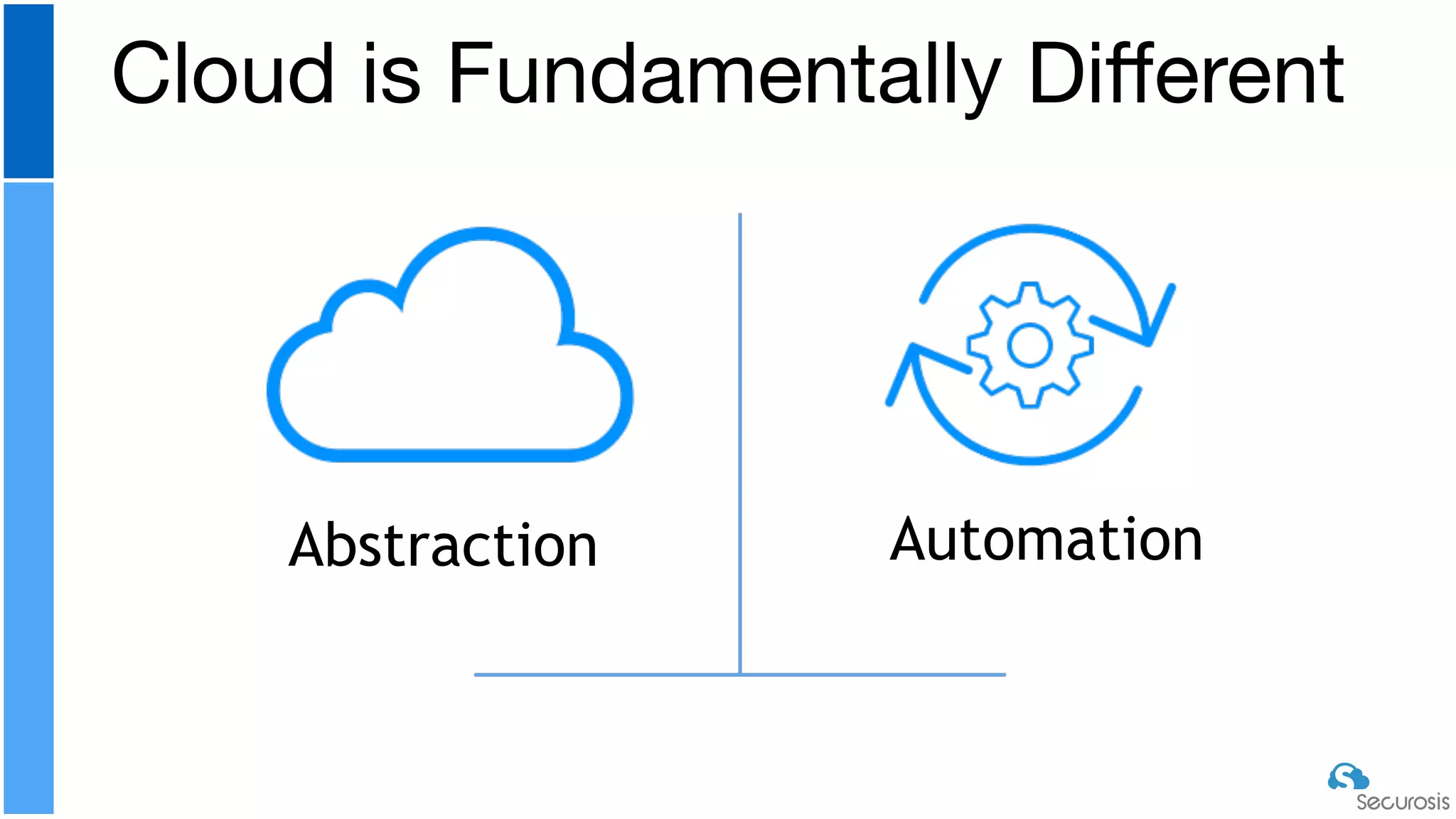
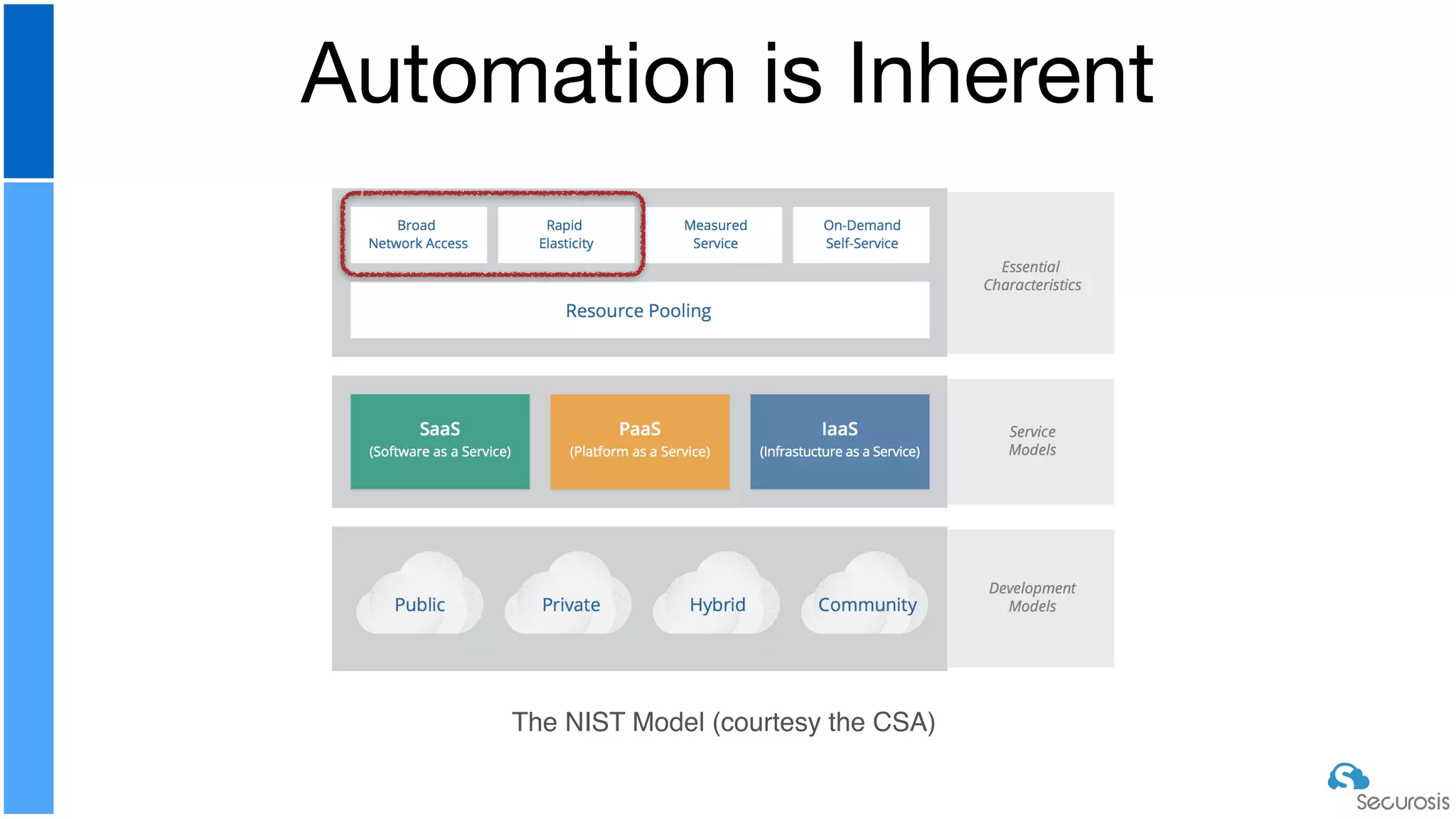
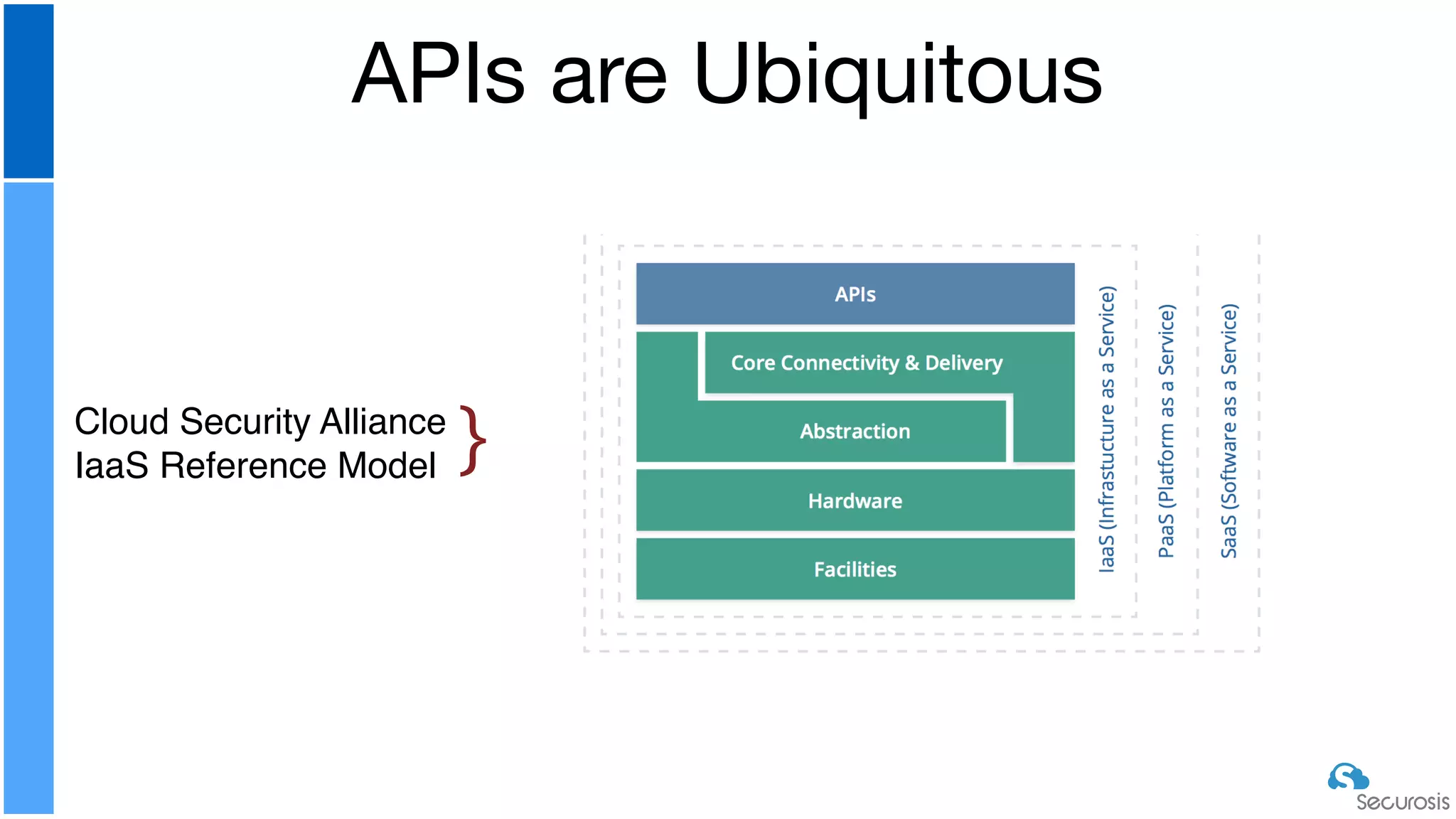
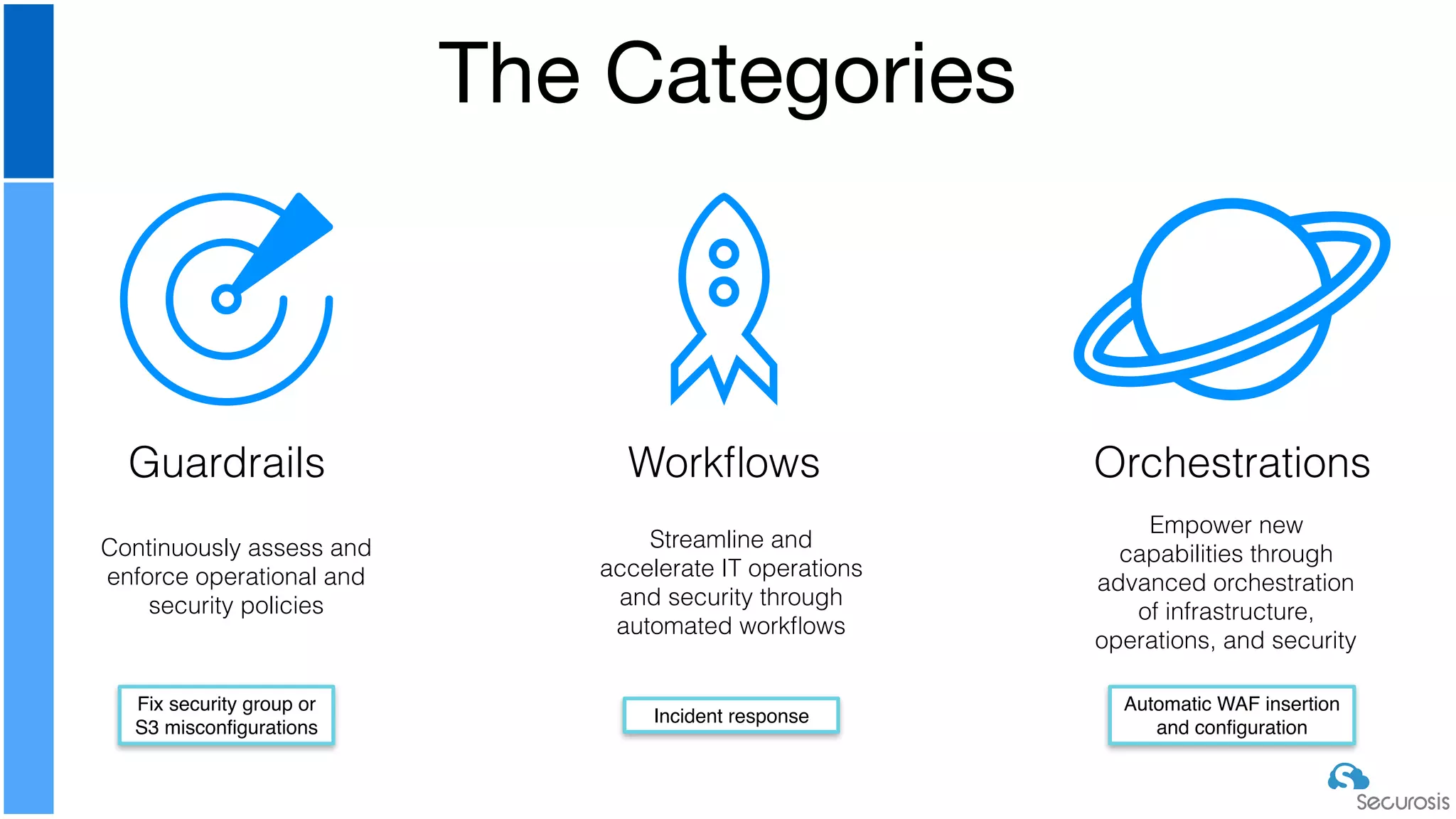
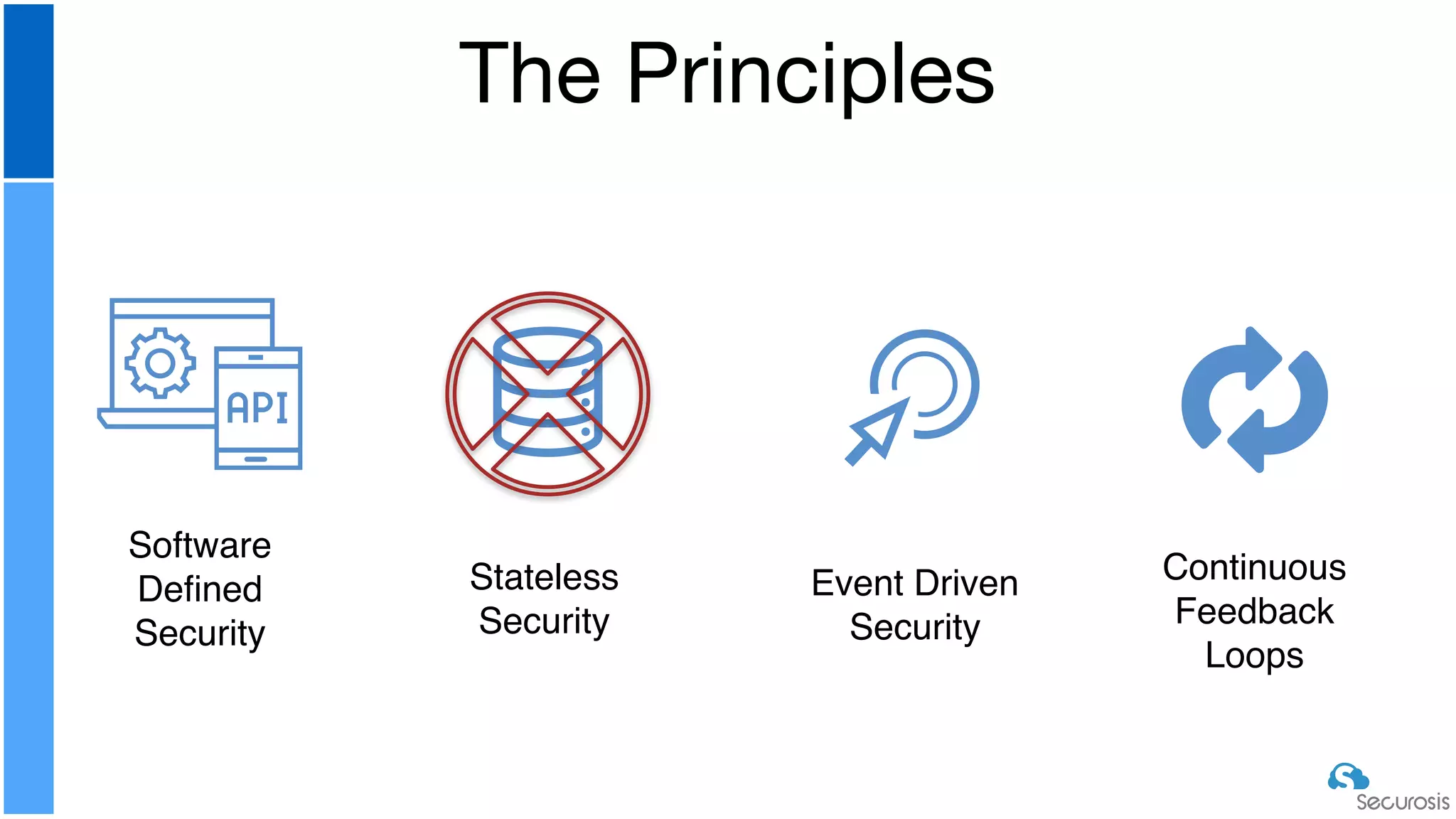
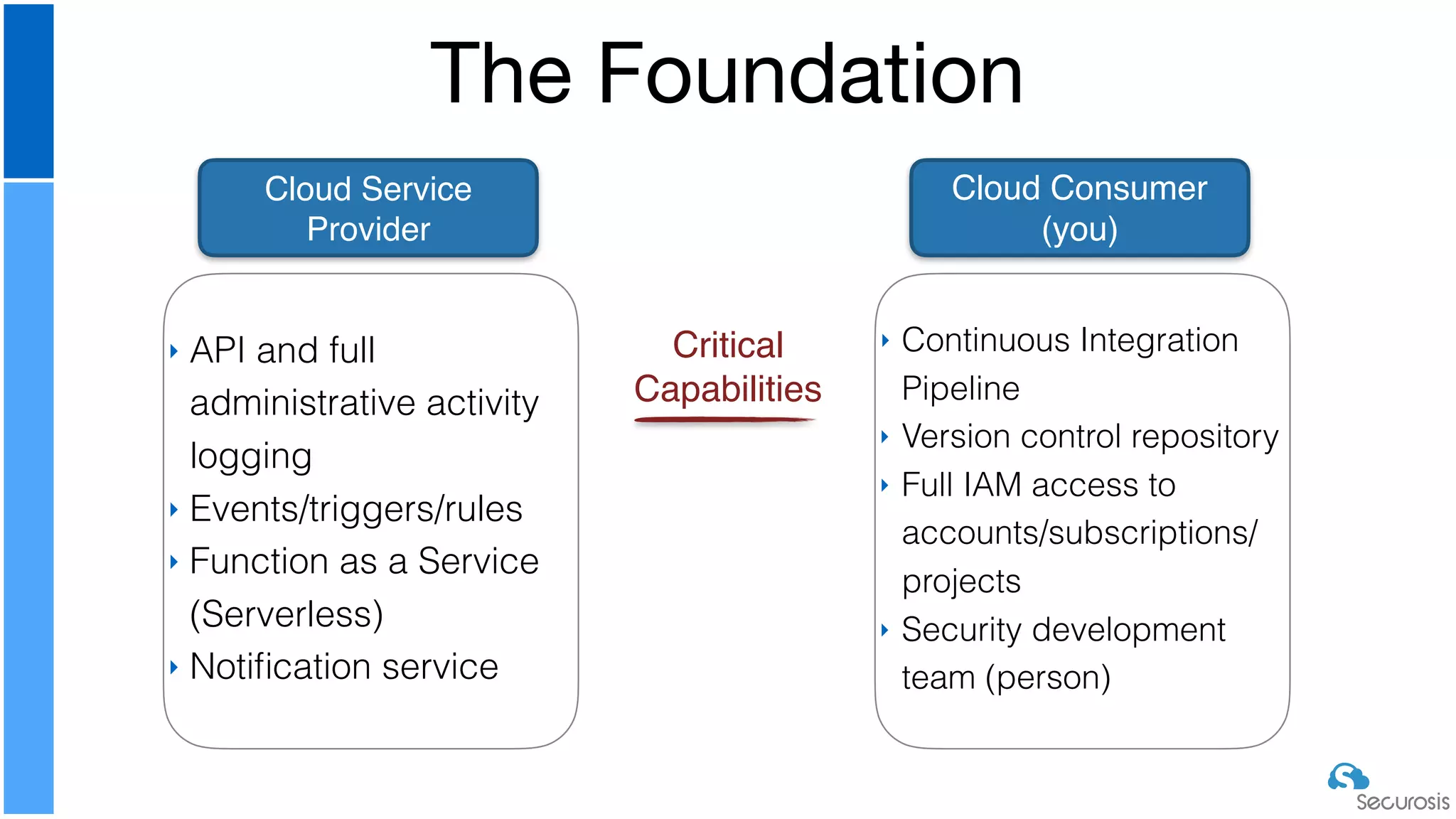
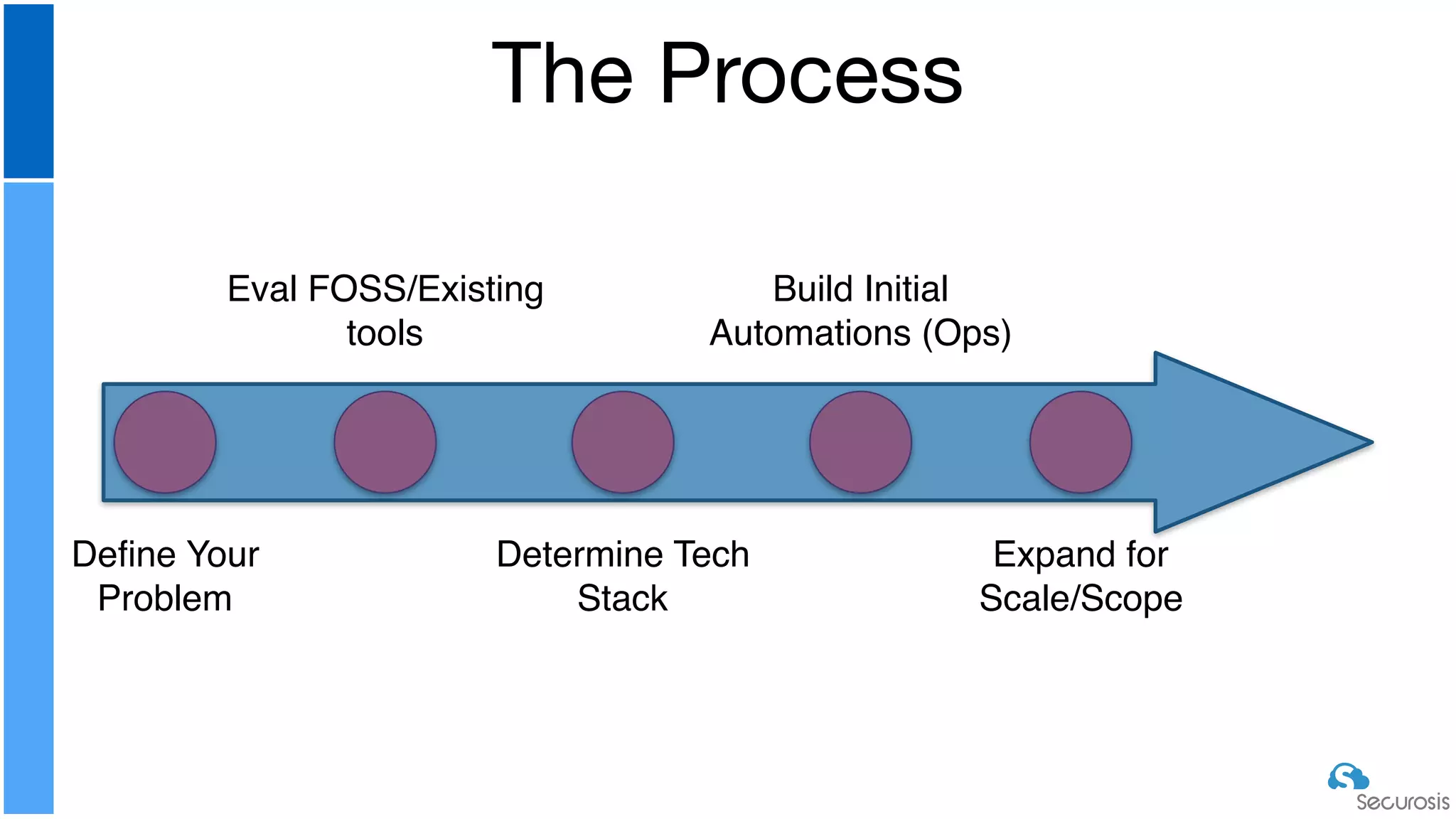
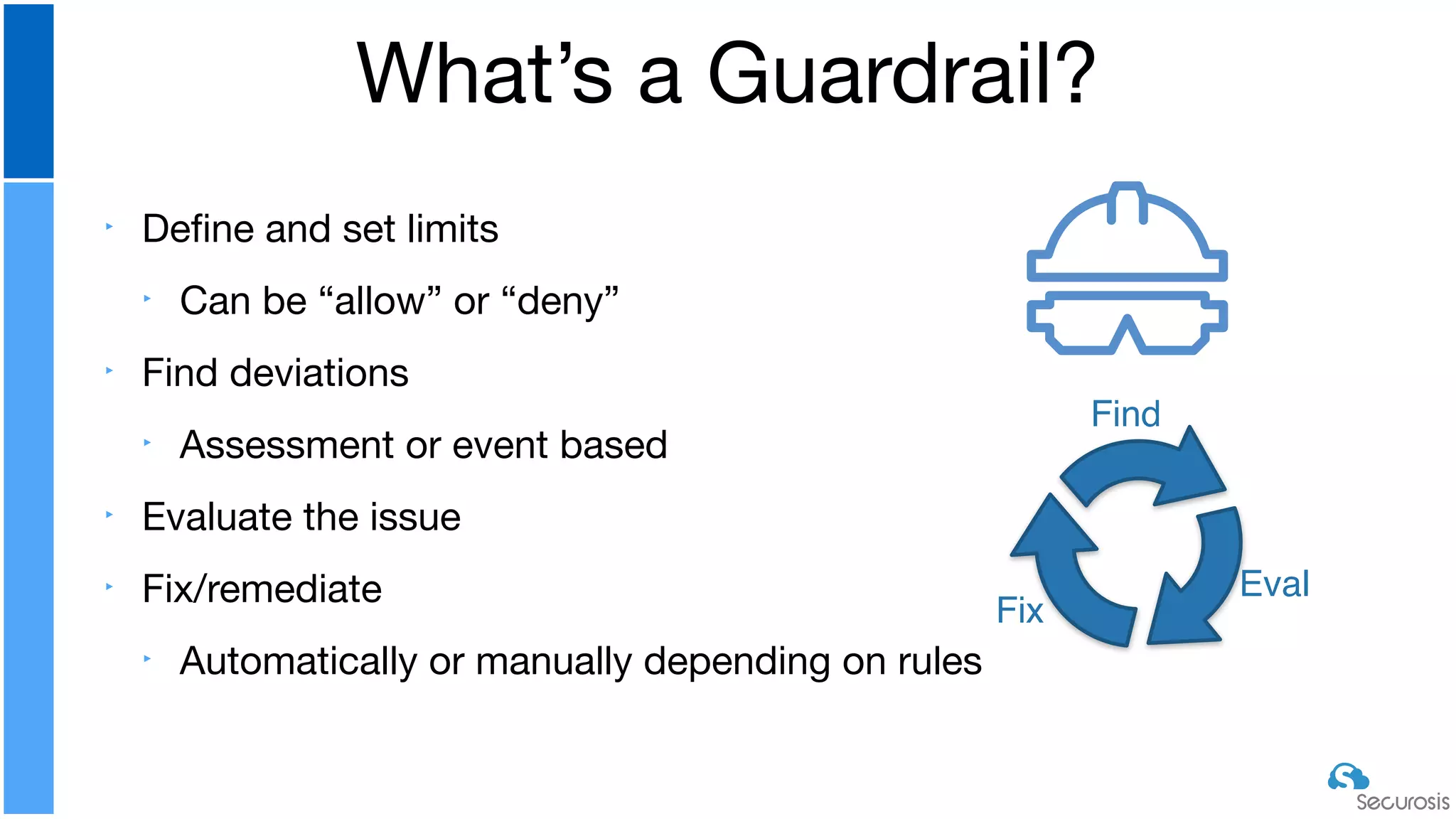
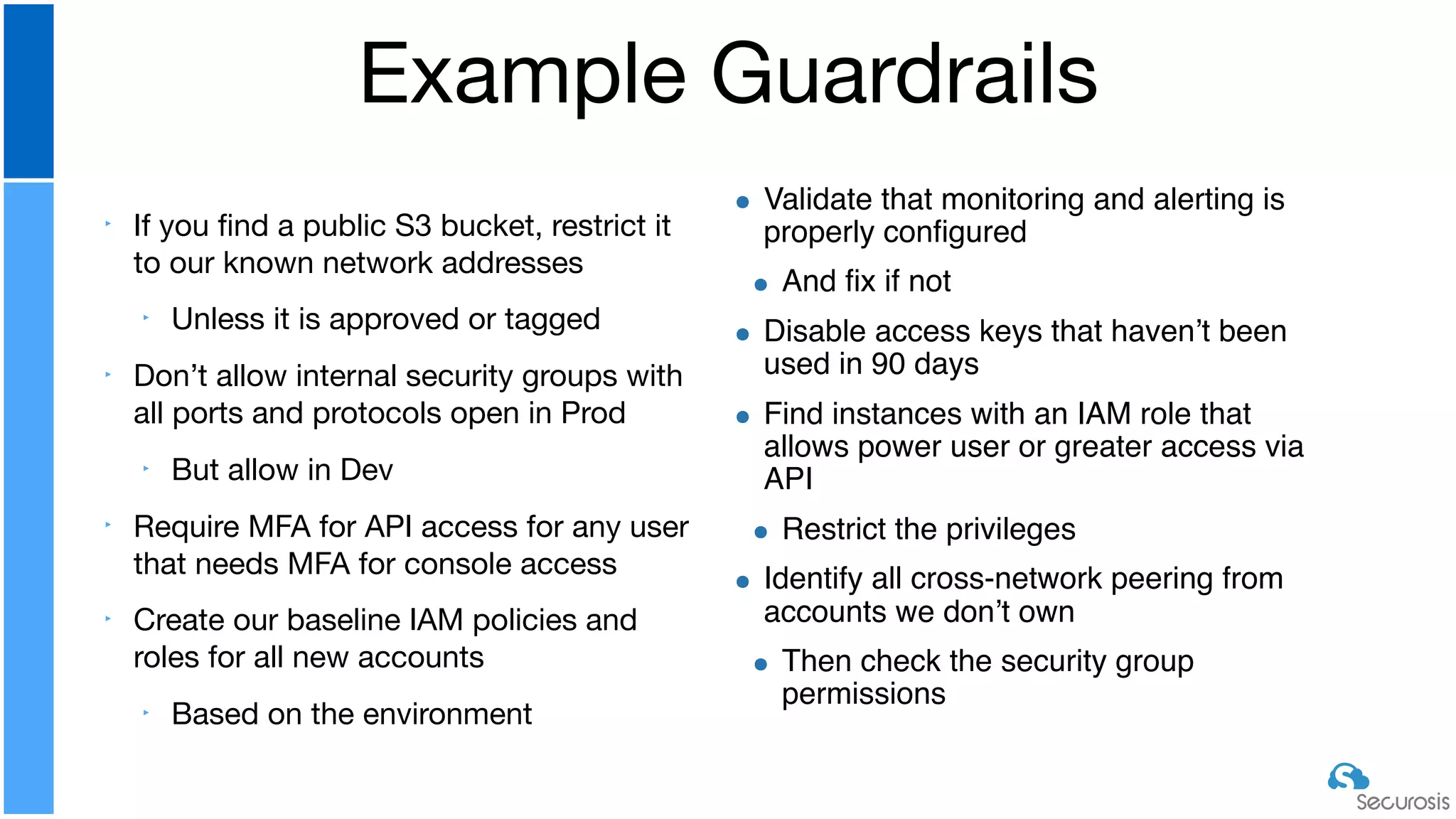
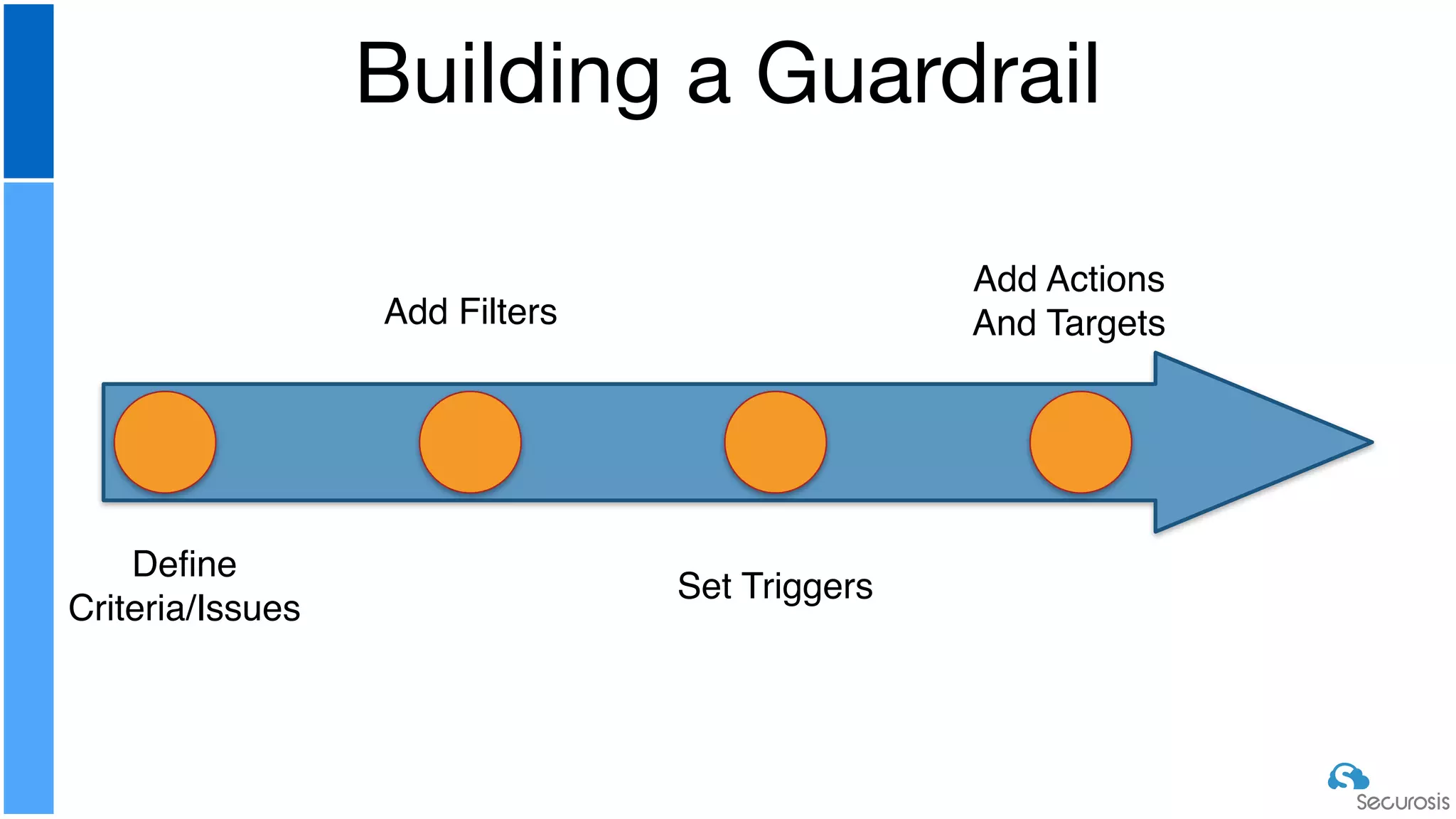
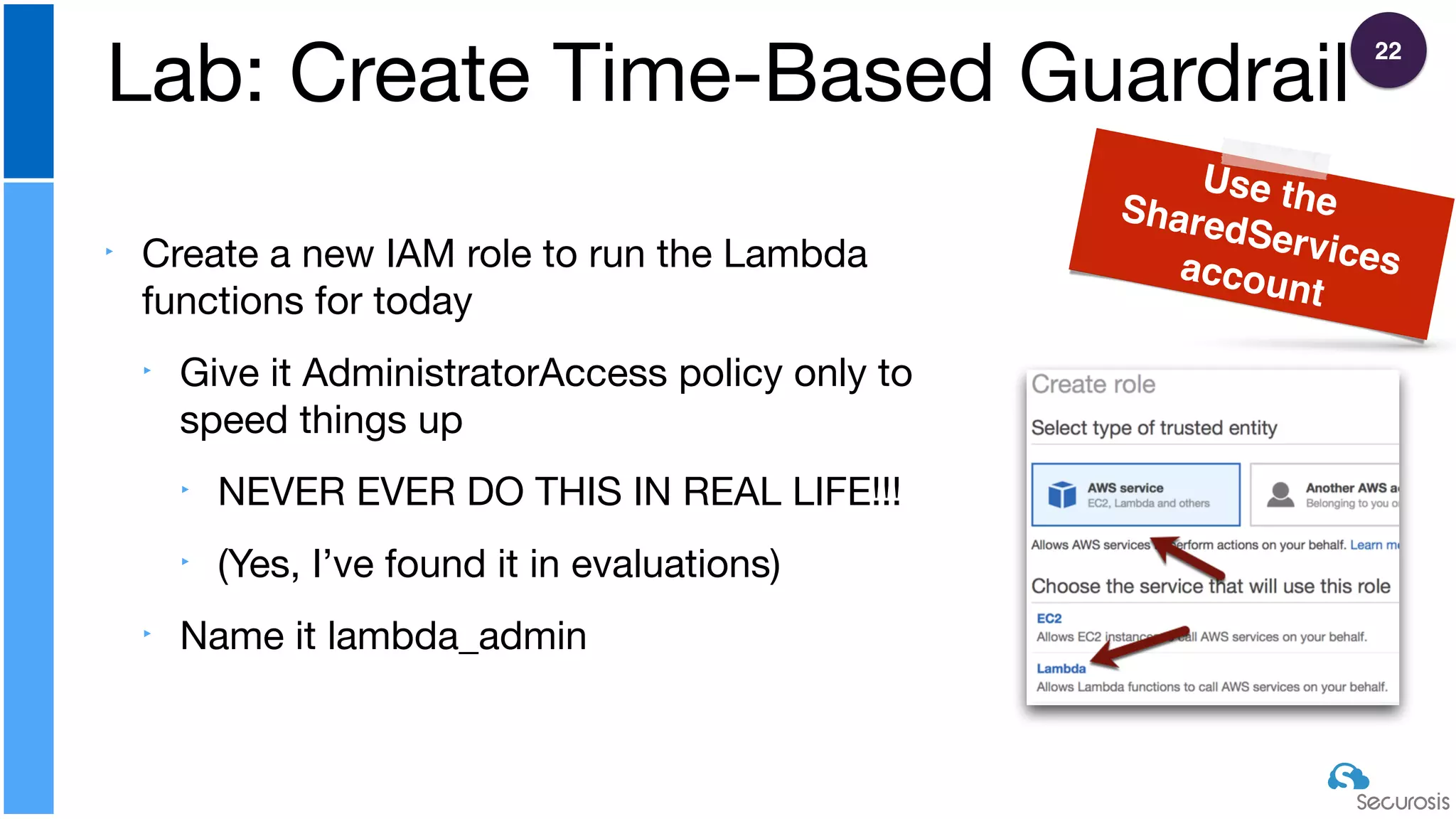
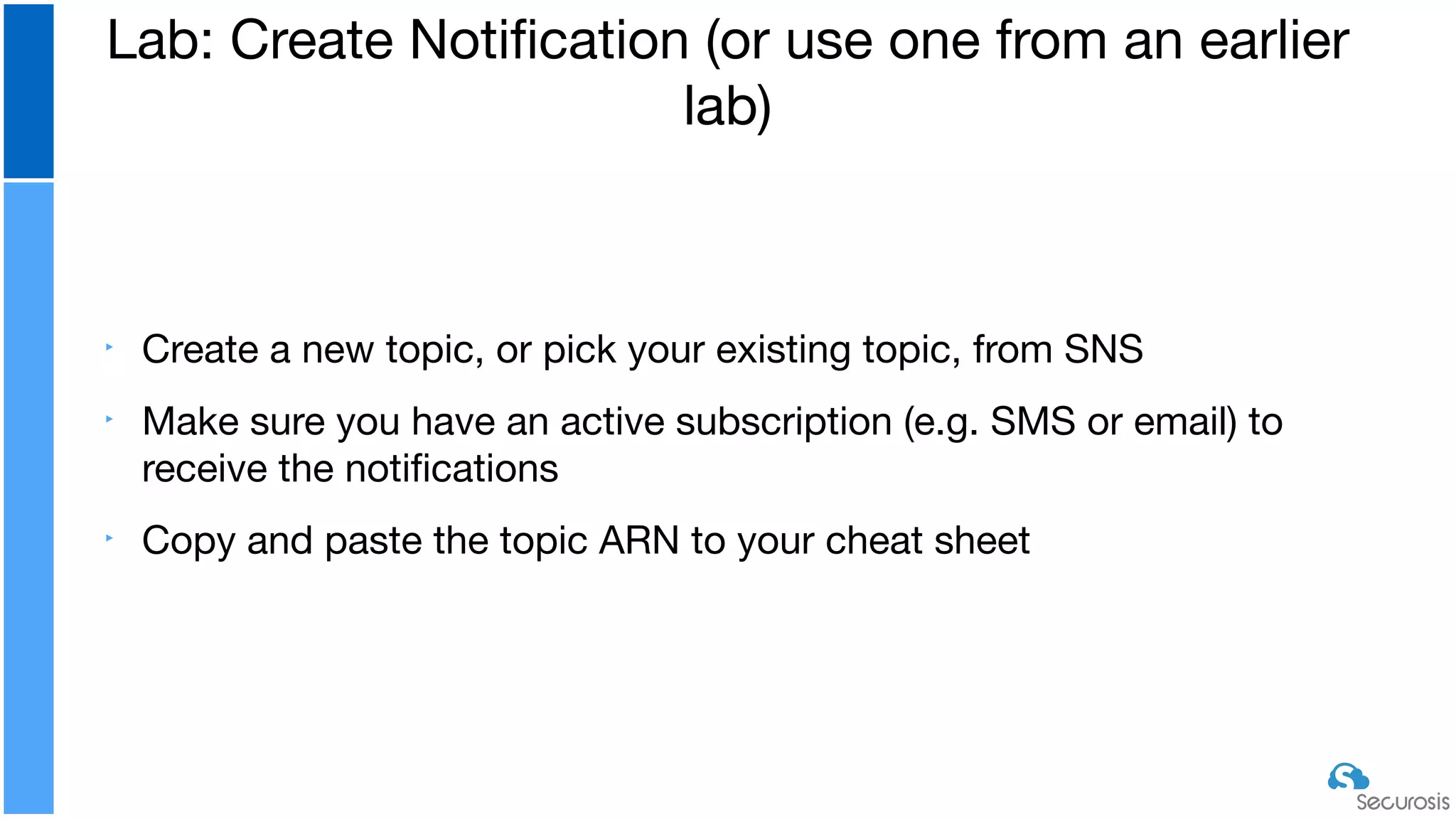
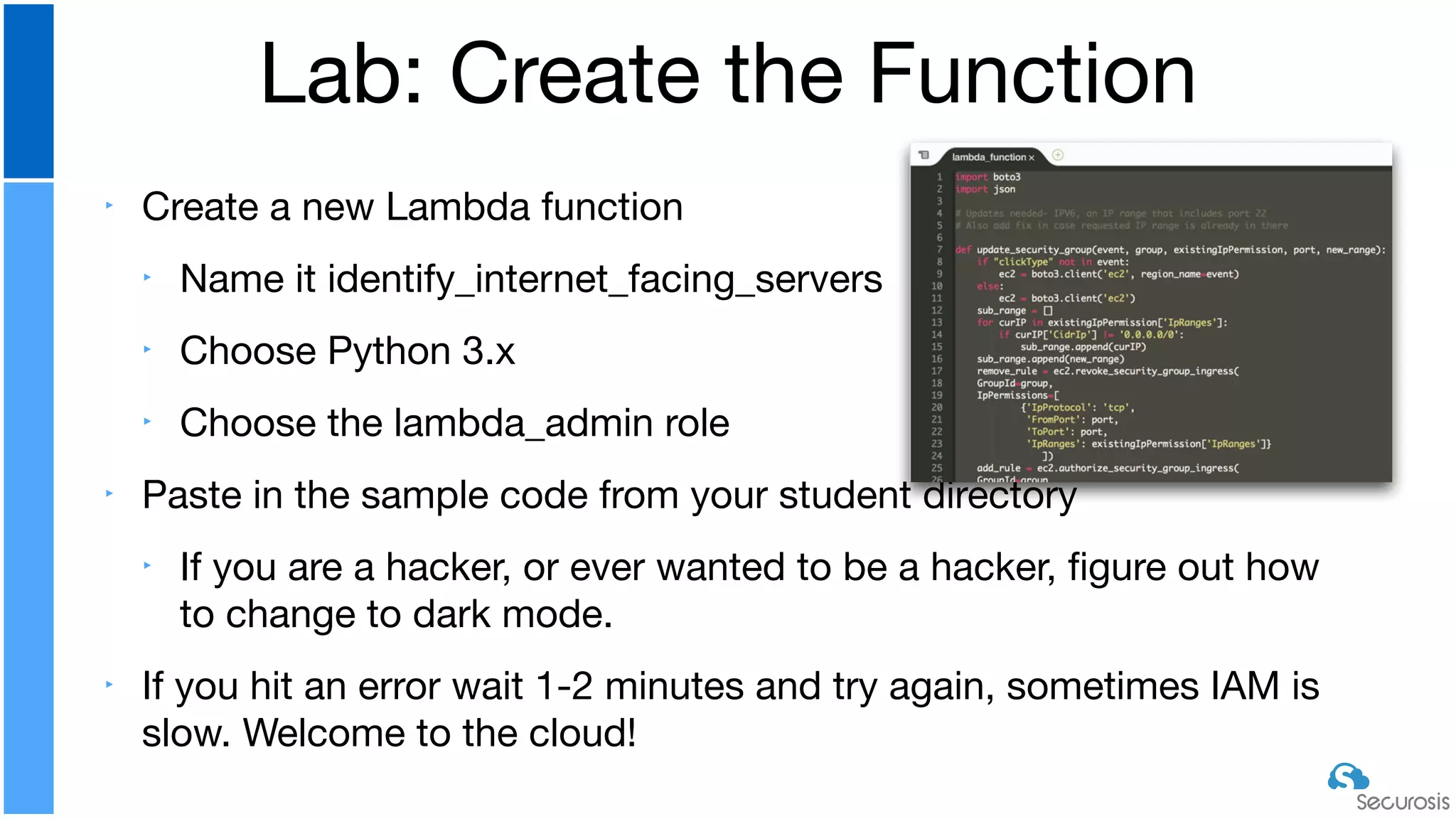
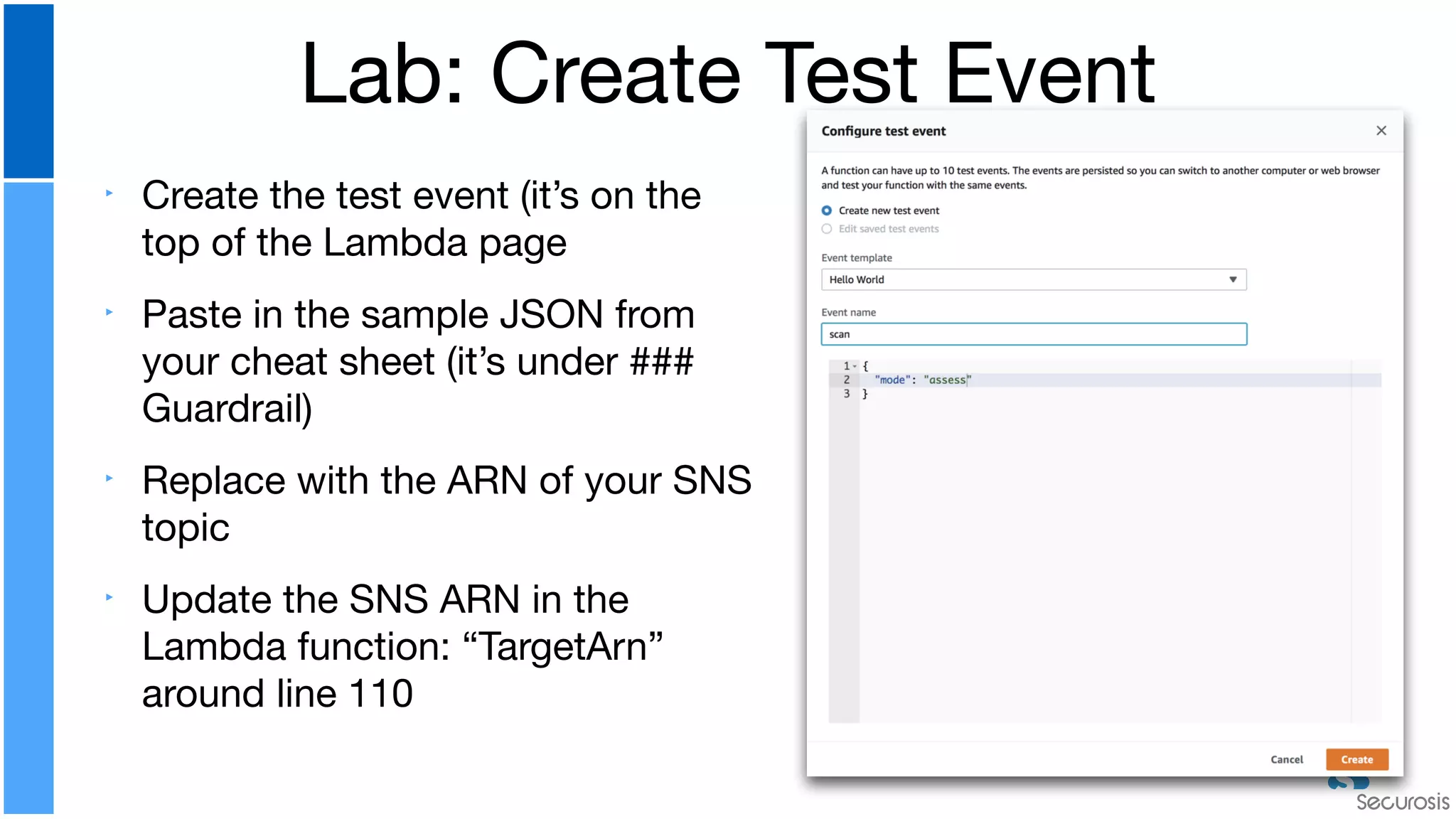
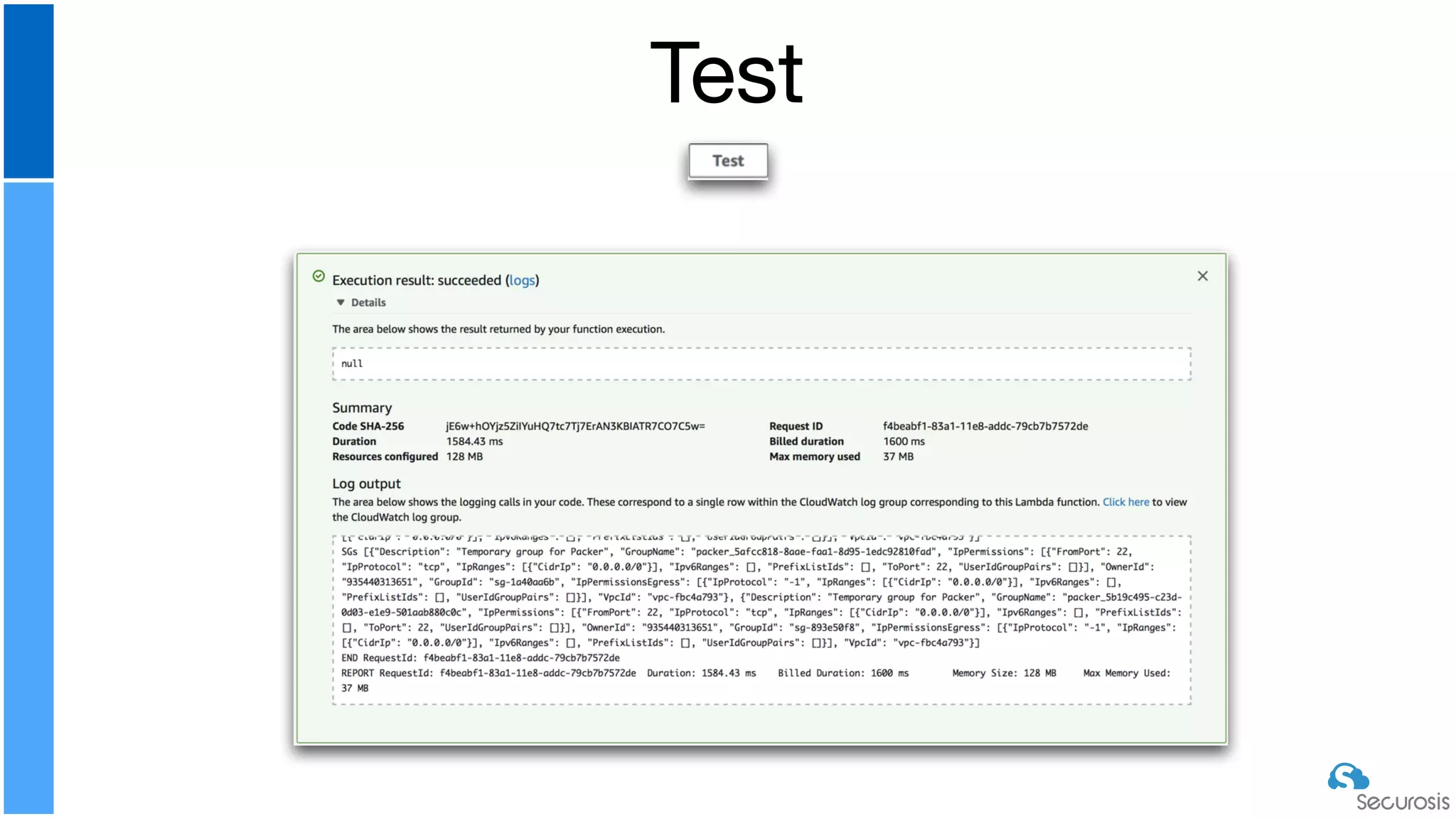
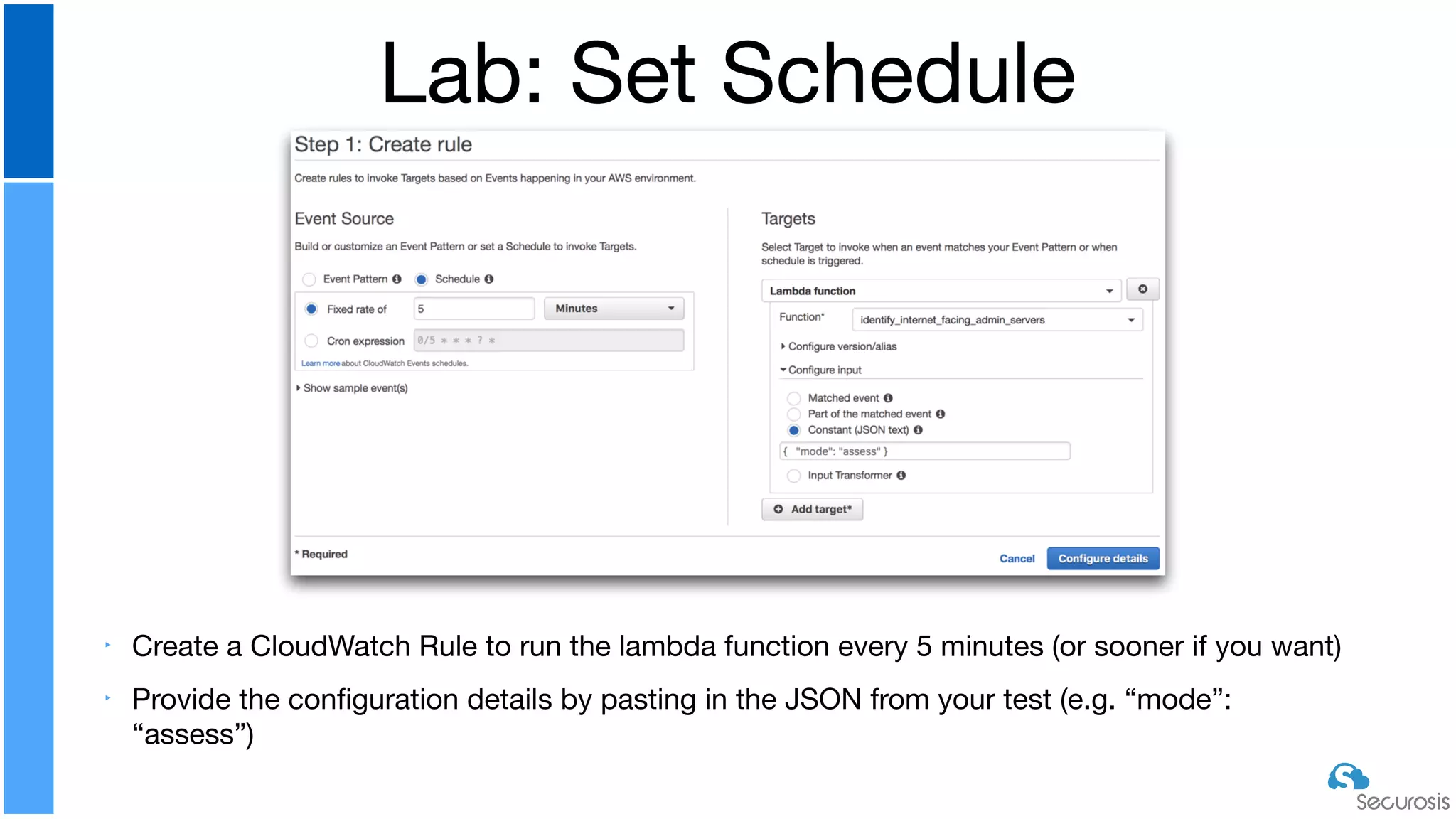
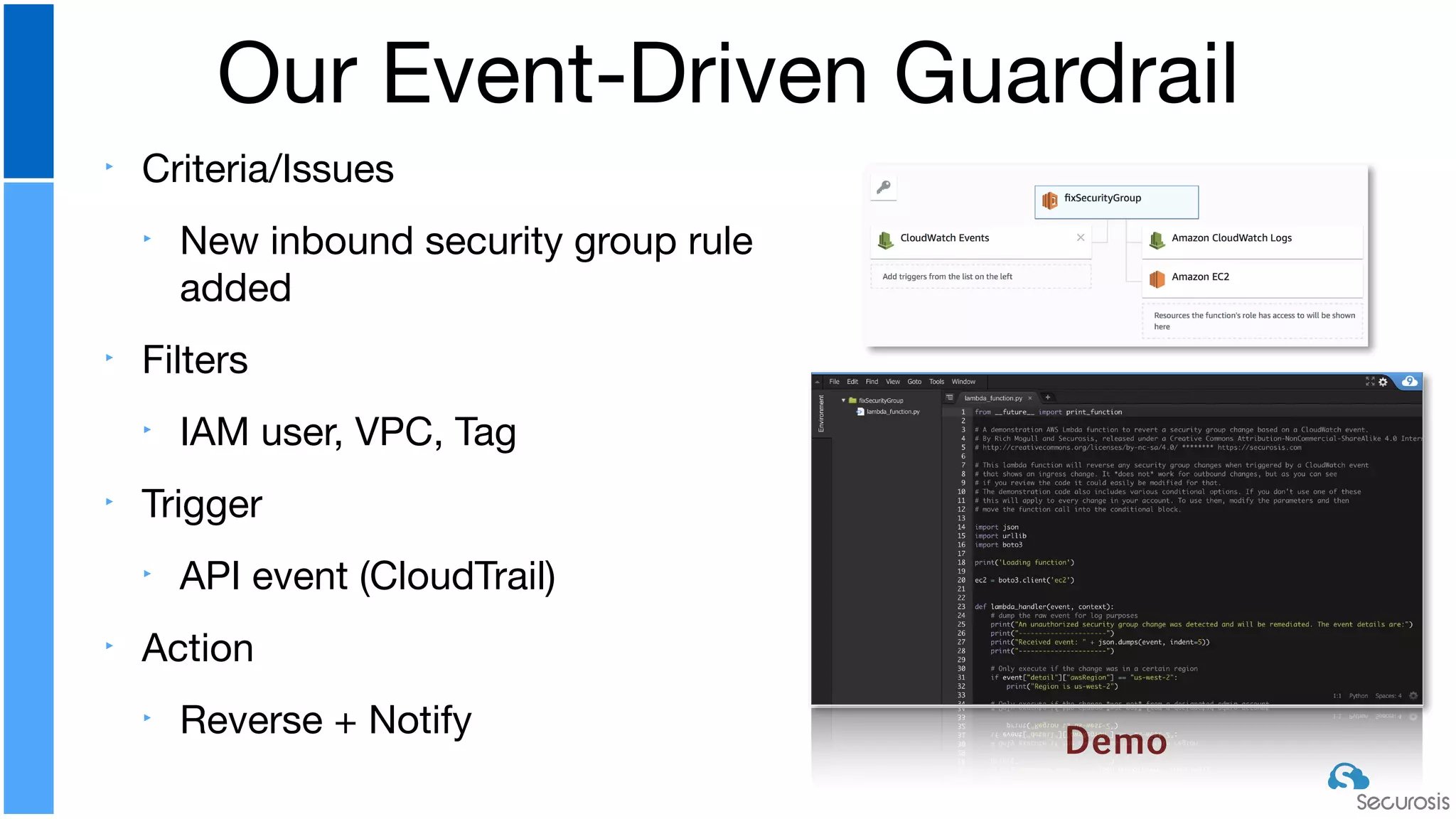
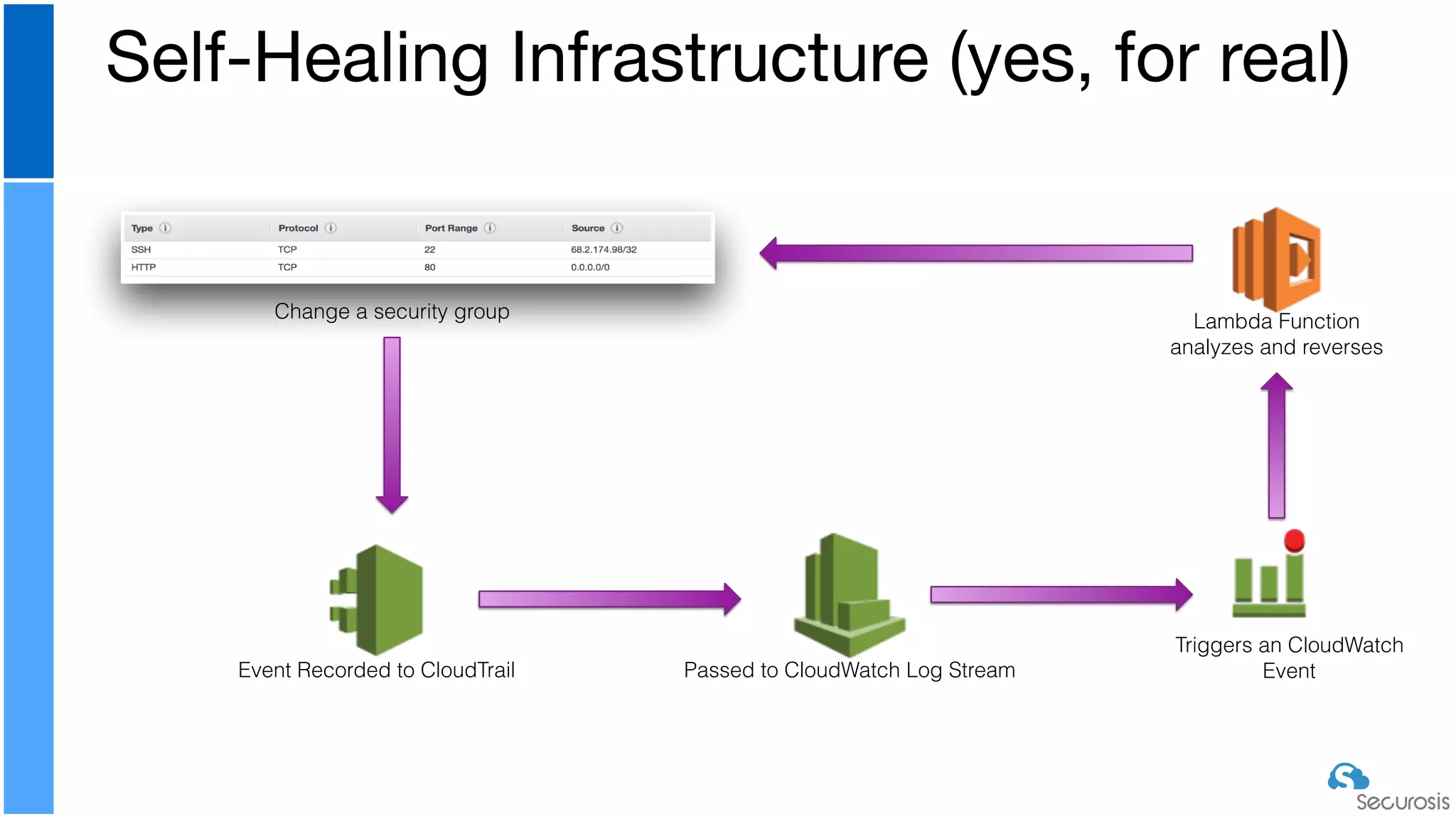
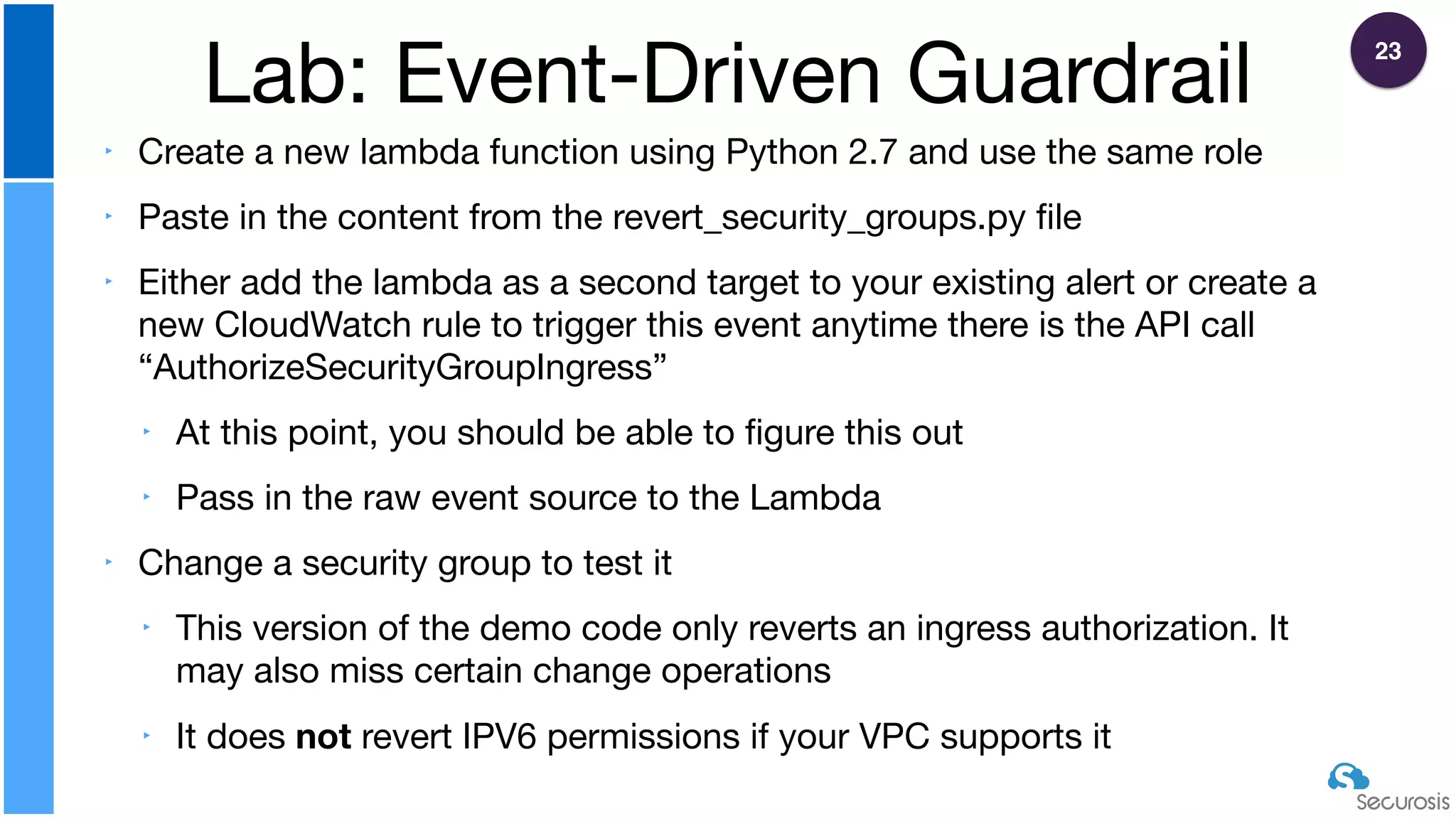
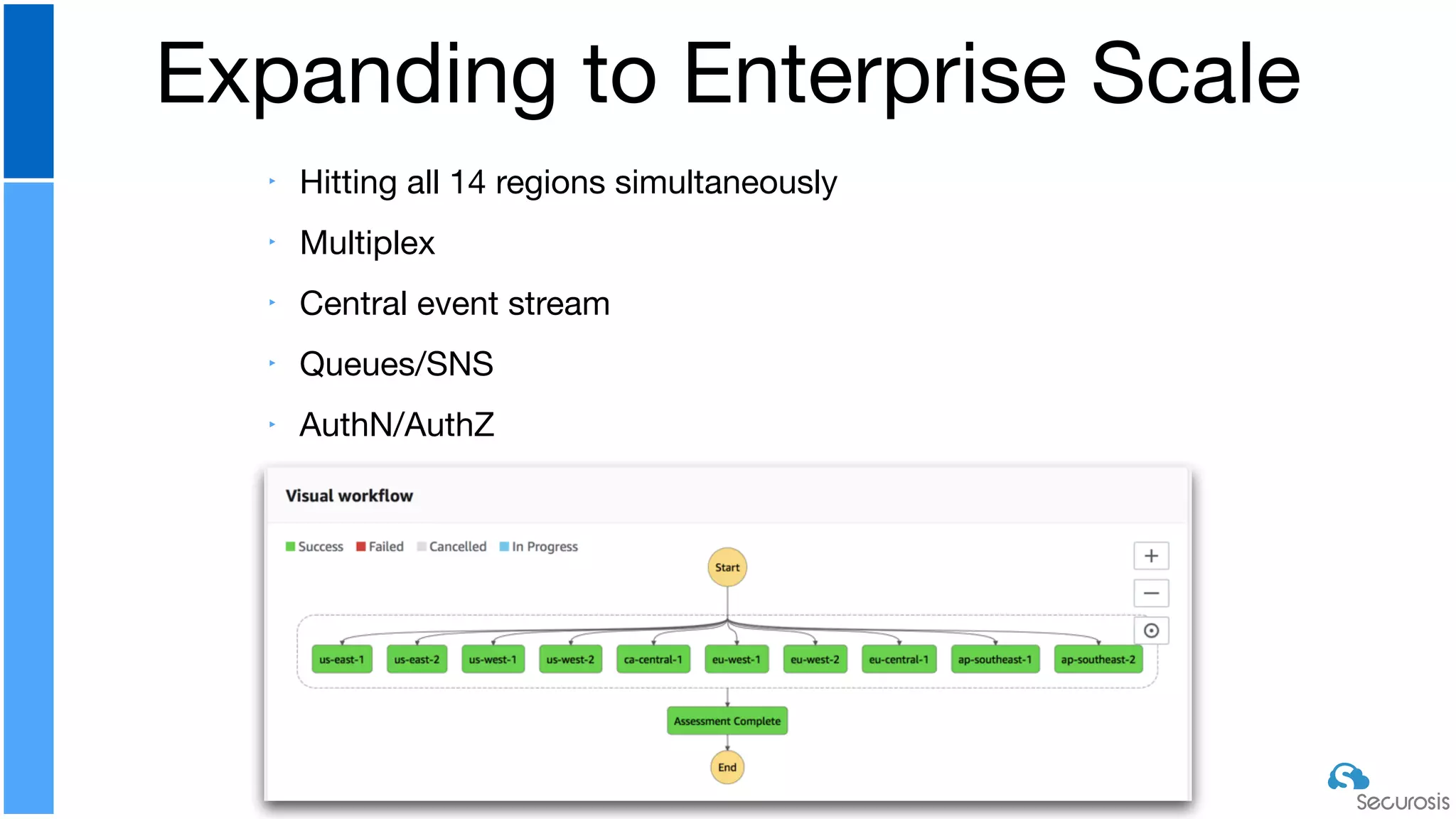
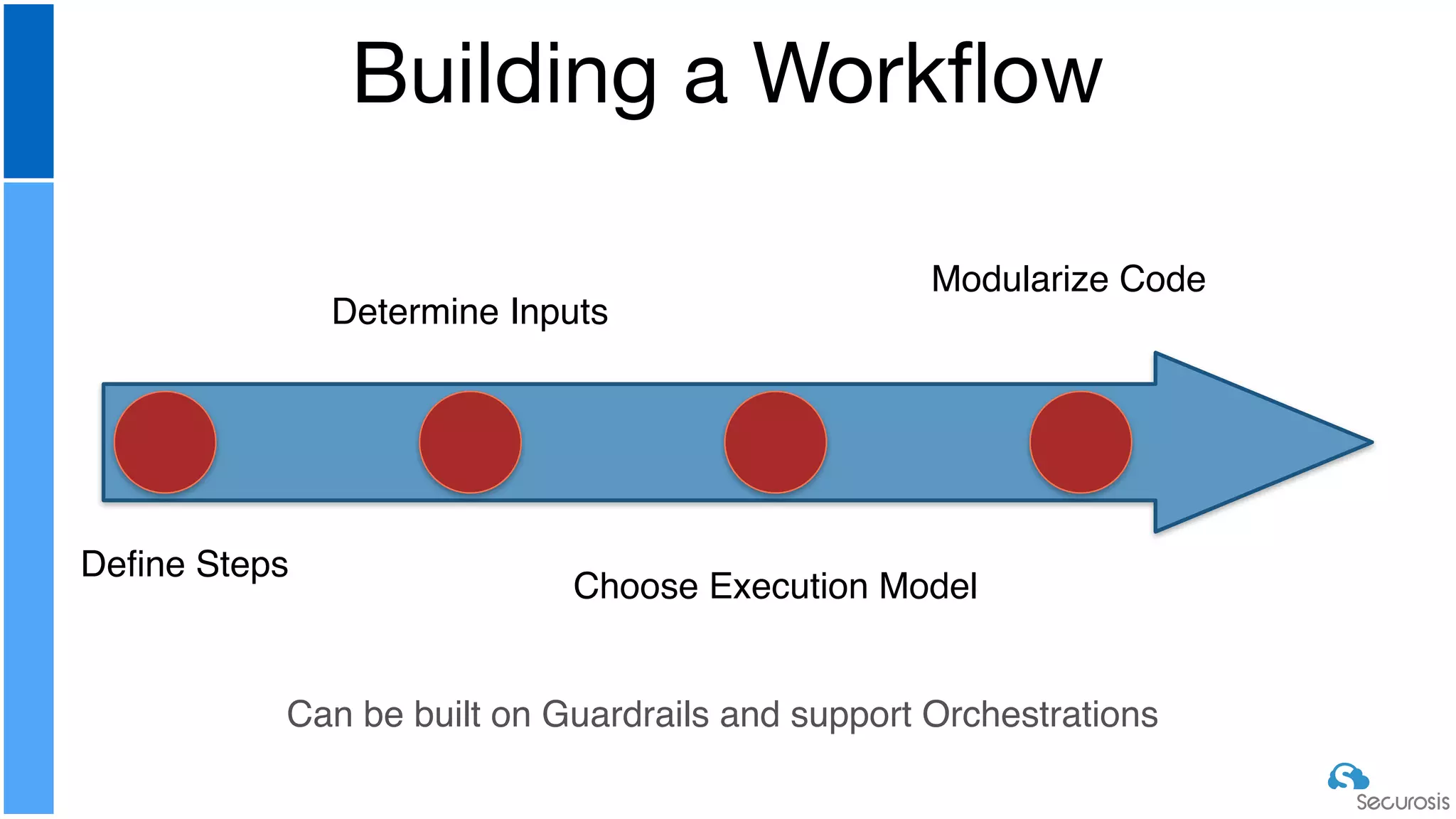
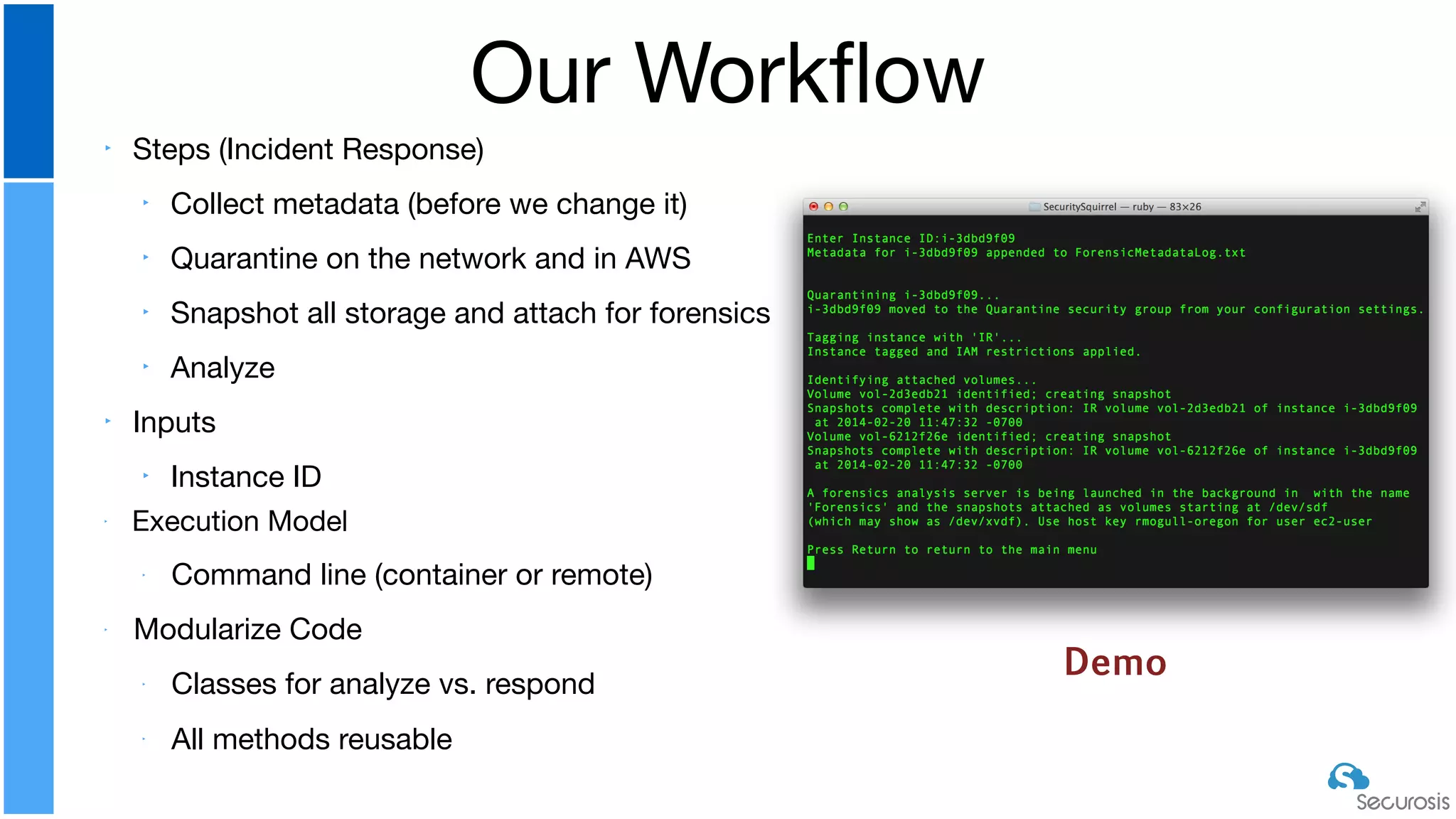
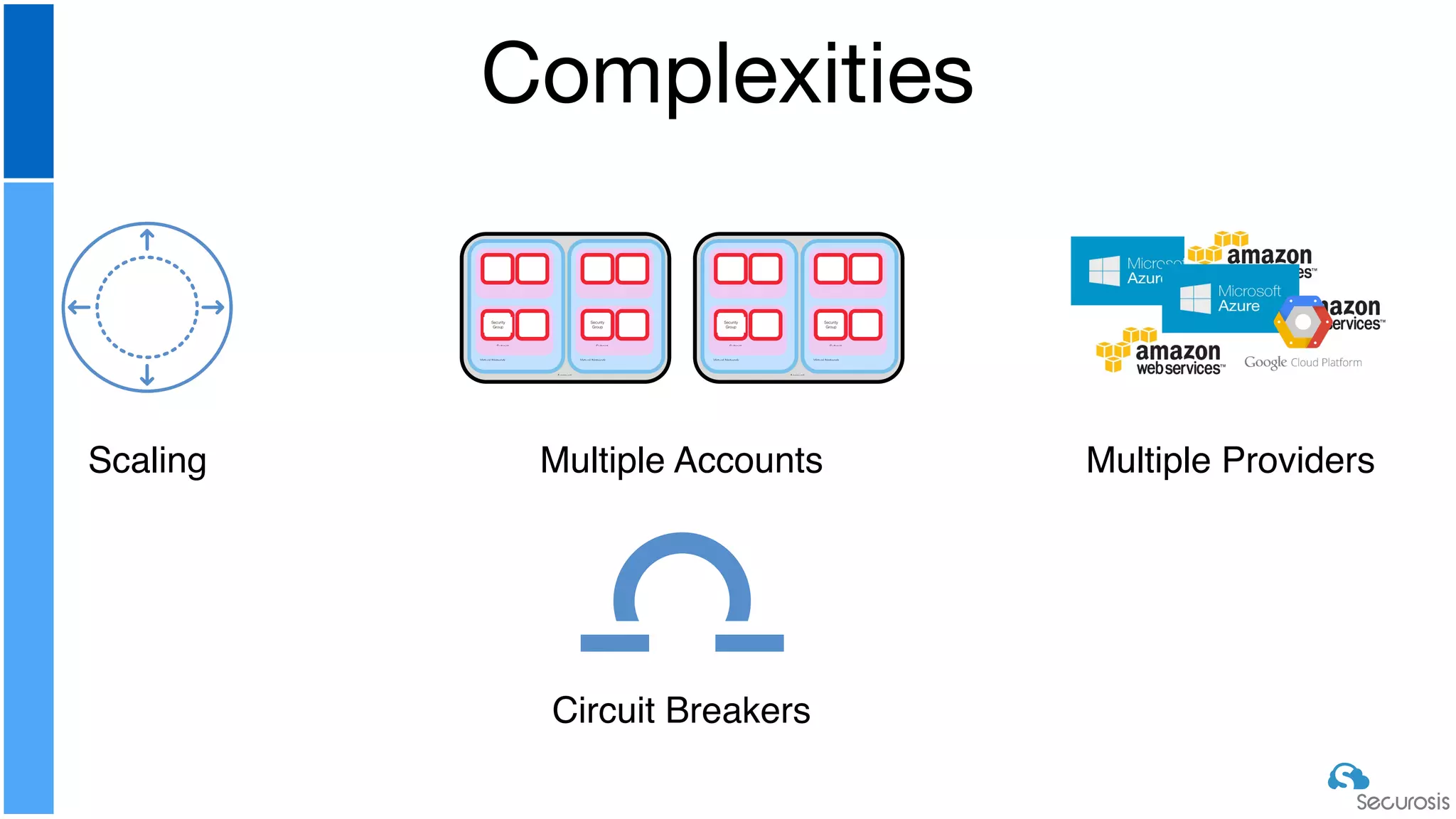
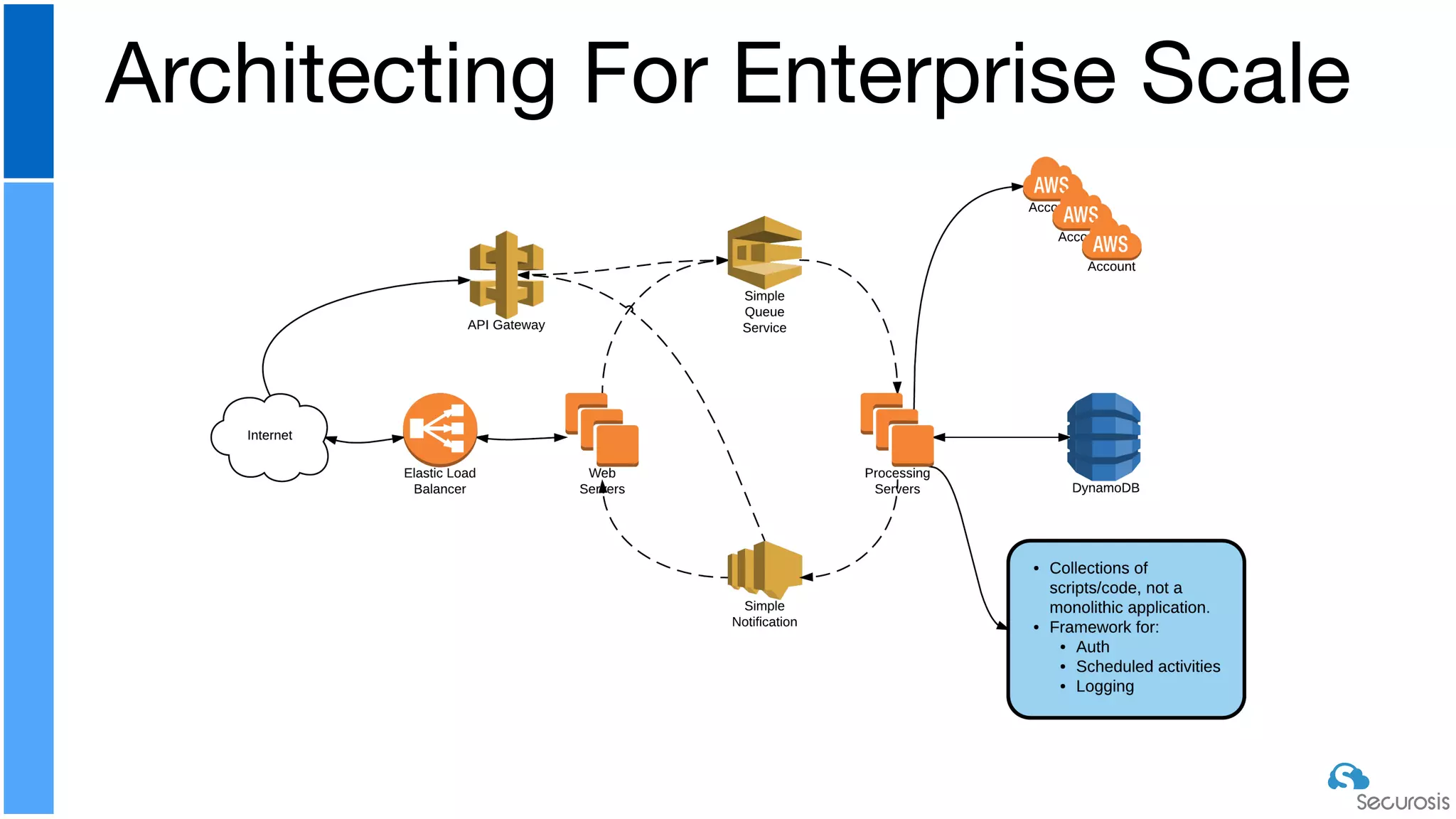
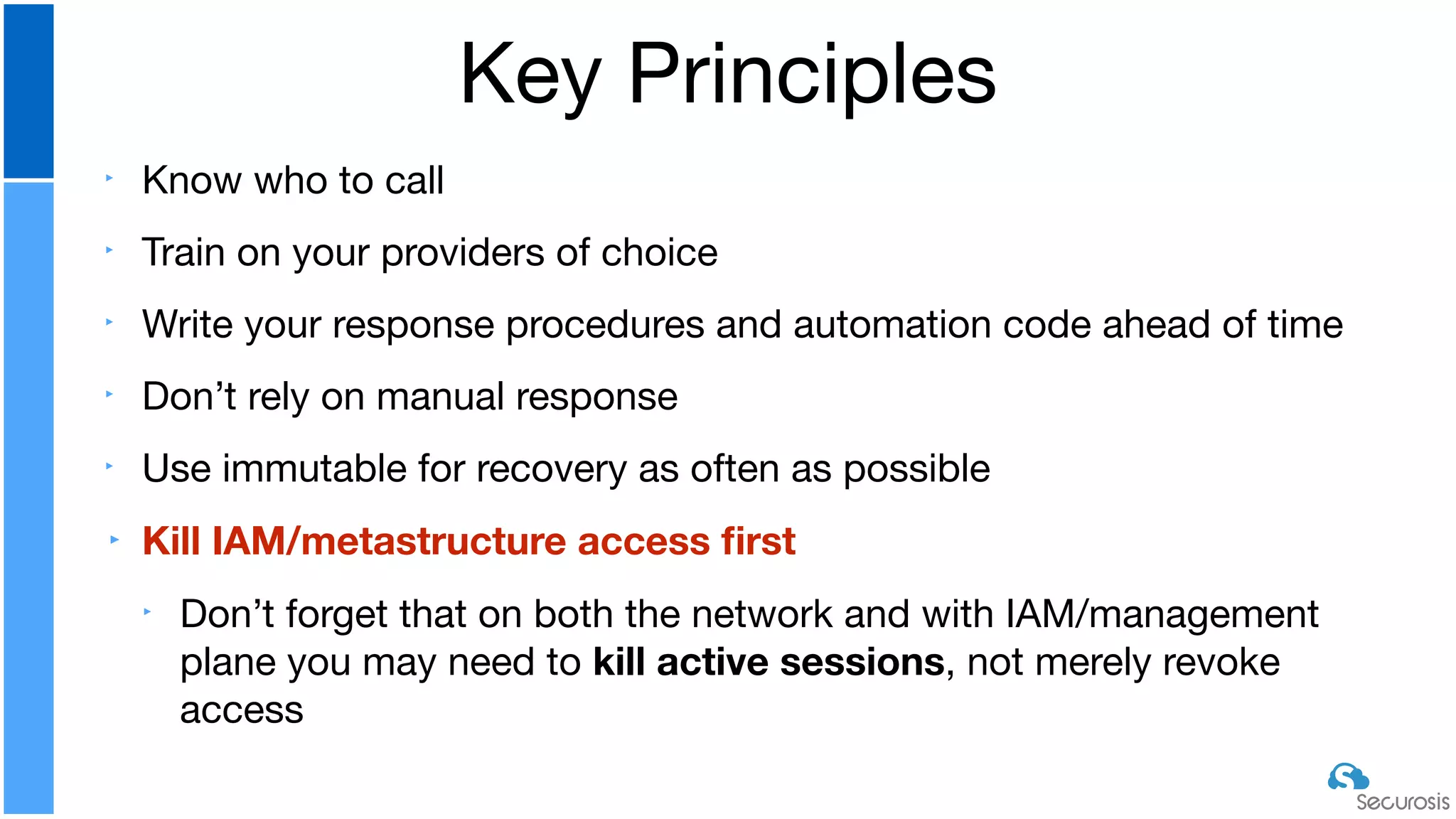
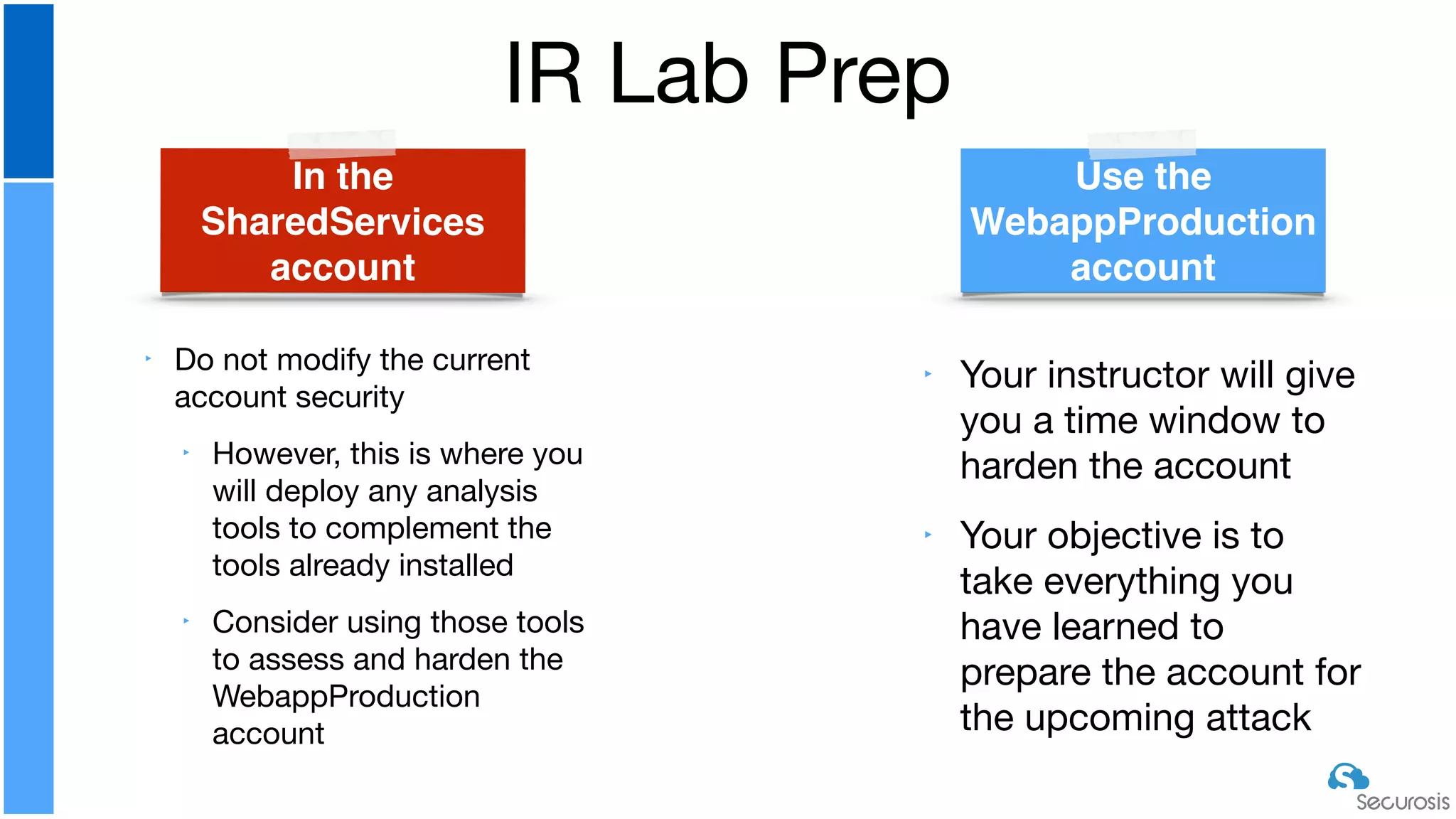
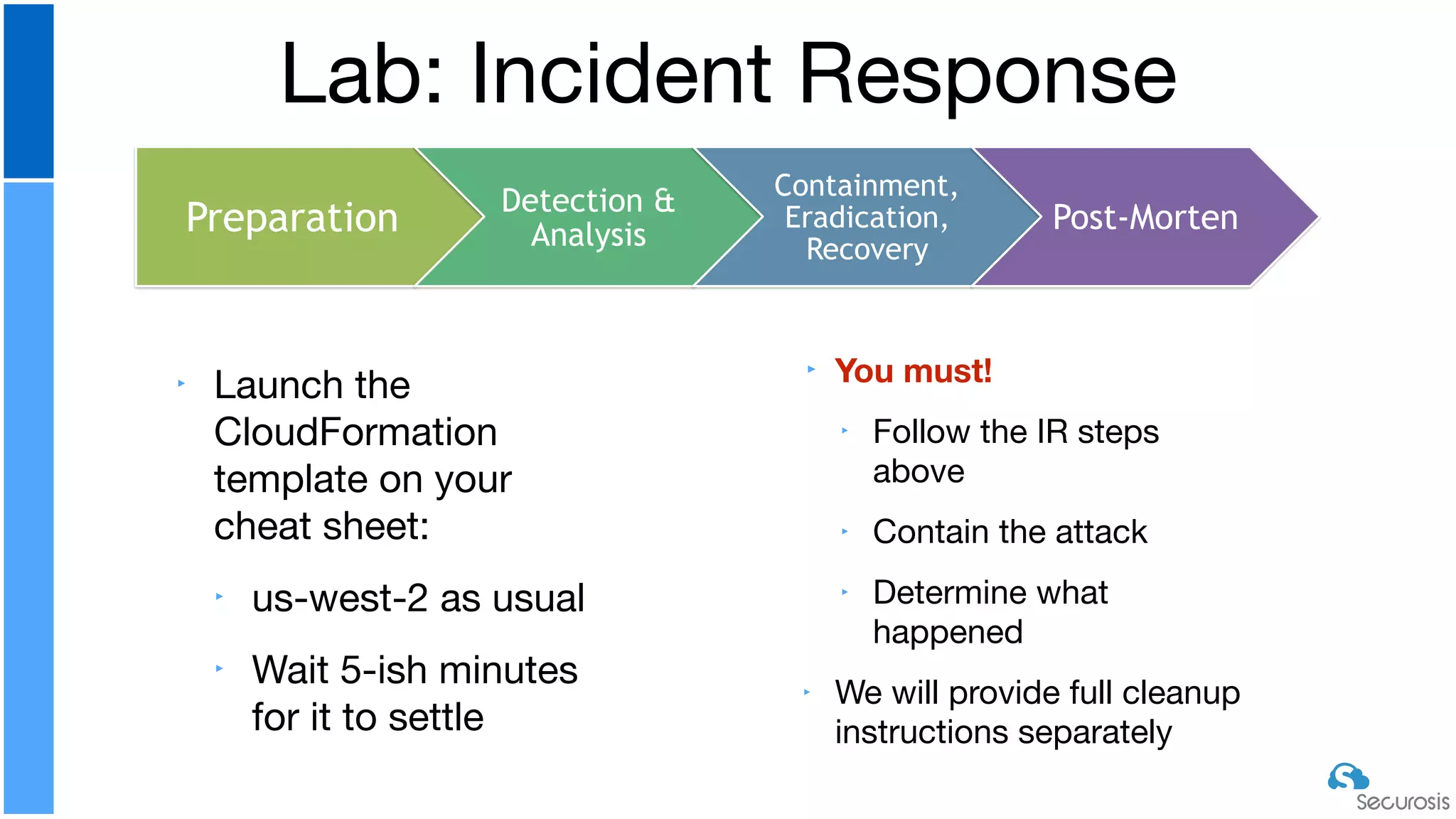
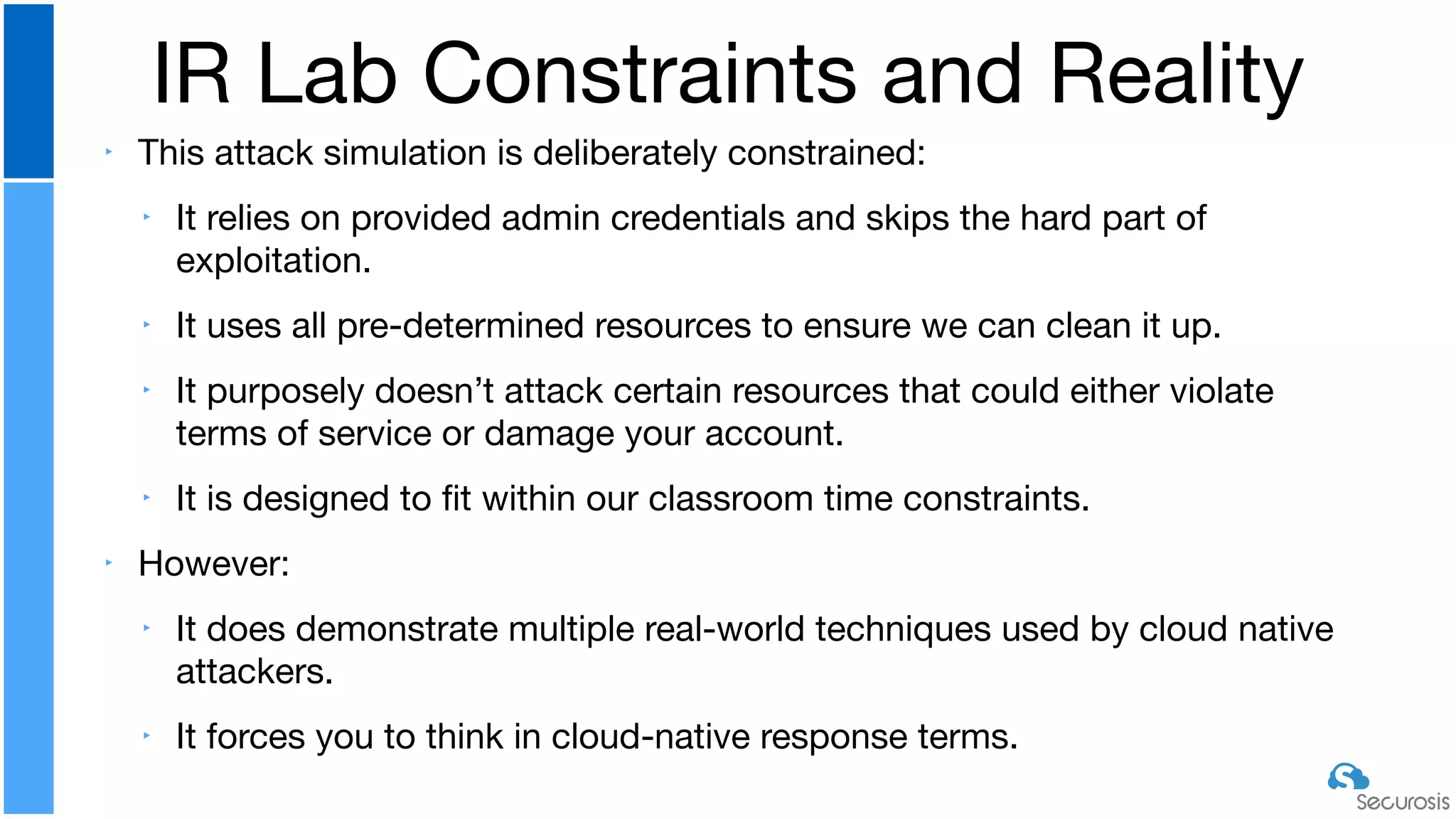
The document discusses cloud security automation, emphasizing the need for cloud-native security management and automation techniques like guardrails and workflows. It outlines essential capabilities for incident response, including monitoring, event-driven approaches, and orchestration for effective remediation of security issues. Additionally, it highlights practical labs for implementing security features and incident response strategies within cloud environments.