This document discusses how to implement DevSecOps on AWS for startups. It covers:
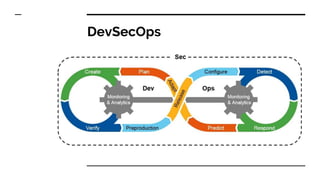
- Key principles of DevSecOps like everyone being responsible for security and shifting security left
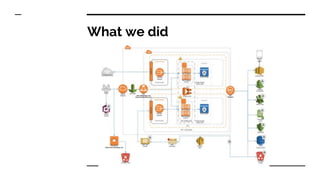
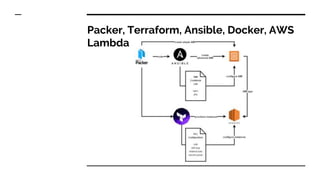
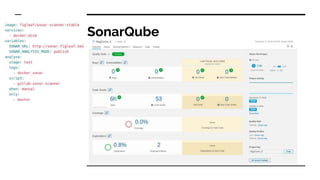
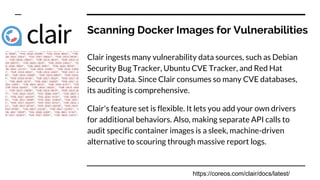
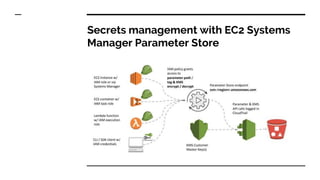
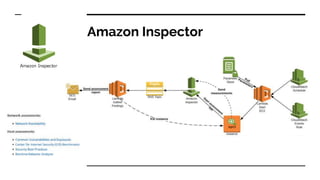
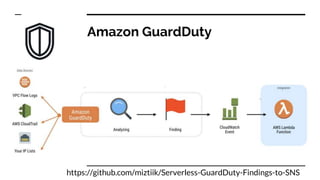
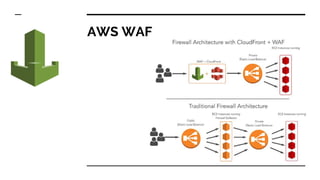
- The tools and services used in their pipeline including Packer, Terraform, Ansible, SonarQube, AWS Inspector, GuardDuty, and WAF
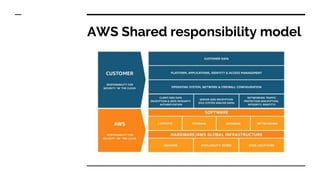
- How they established policies, used a multi-account approach, implemented access management, and focused on security culture and monitoring
- Their plans to further improve using AWS Config, perform penetration testing, and meet standards like OWASP and PCI DSS