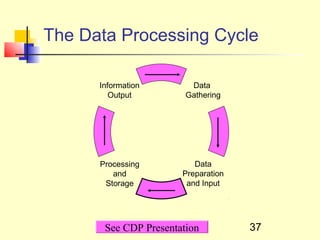
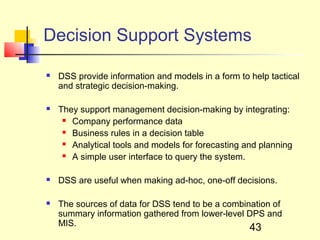
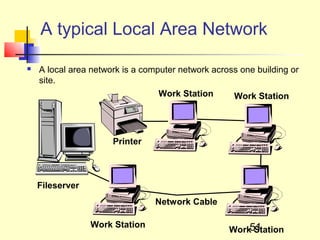
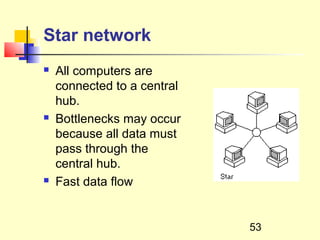
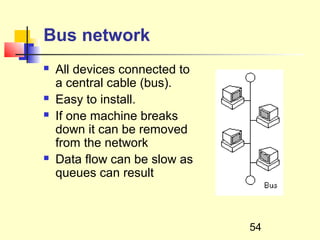
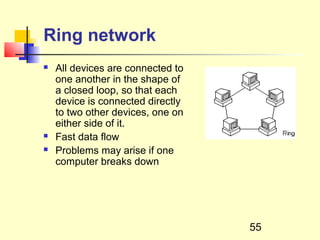
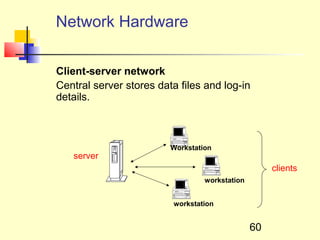
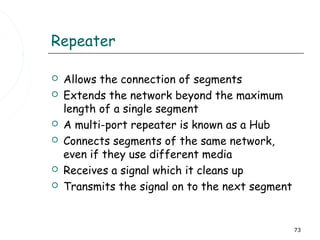
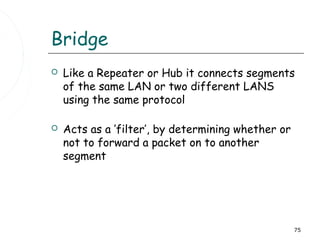
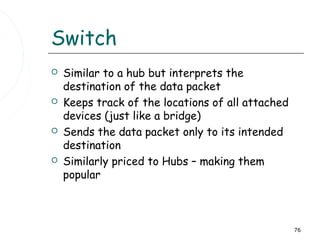
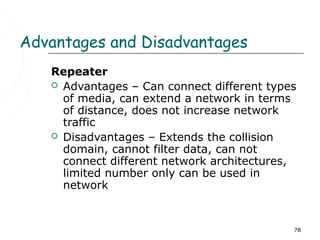
This document discusses information systems and concepts related to organizational management. It begins by defining an information system and distinguishing between data and information. It then covers topics such as the categorization and characteristics of information, including source, nature, levels of use, time, frequency, and form. The document also discusses different types of information systems used at various organizational levels, including data processing systems, management information systems, decision support systems, and executive information systems. Finally, it covers concepts like the speed of processing systems and value versus cost of information.