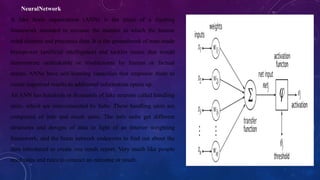
This document presents a novel approach to cyber threat detection utilizing artificial neural networks (ANNs) and event profiles to improve cybersecurity by identifying anomalies indicative of cyber threats. The primary objective is to develop a machine learning-based system for the early detection and mitigation of deception attacks in cyber-physical systems, emphasizing real-time adaptability and enhanced accuracy through various algorithms. The proposed system aims to address the limitations of existing detection methods by combining advanced machine learning techniques with comprehensive event analysis for effective threat assessment.