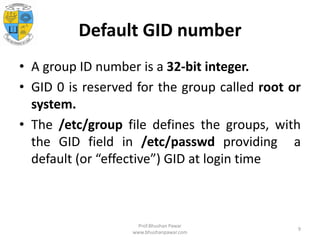
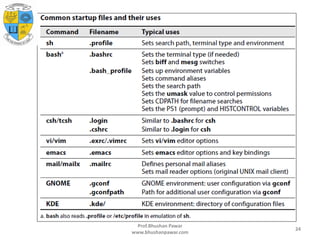
This document discusses how to add new users and storage on a Linux system. It covers editing the /etc/passwd and /etc/shadow files to define a new user account, setting an initial password, creating the user's home directory, installing startup files, and setting permissions. The key steps are using a command like useradd to edit the password and shadow files, setting the password with passwd, creating the home directory, copying default startup files, and setting ownership of the home directory to the new user.