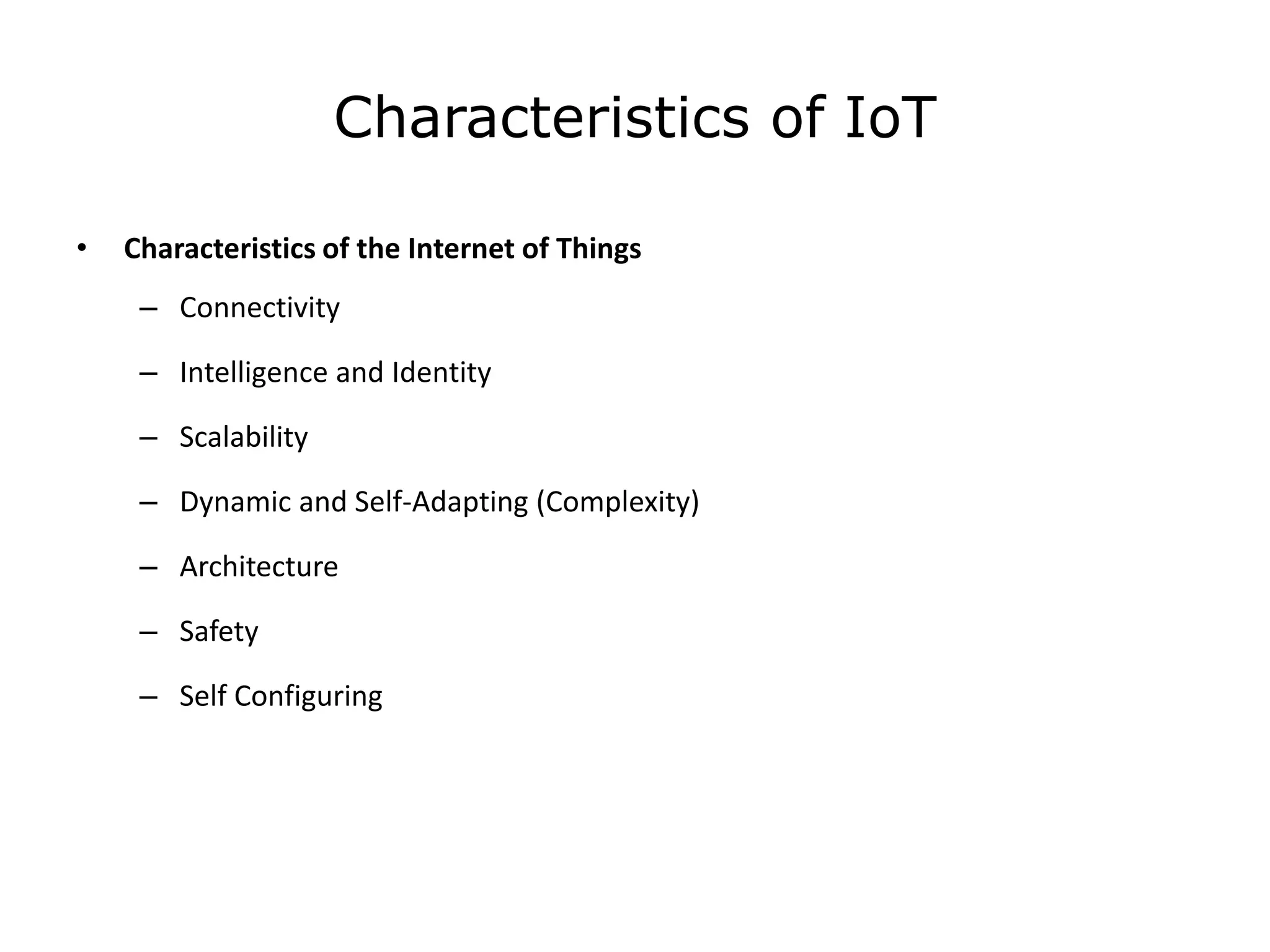
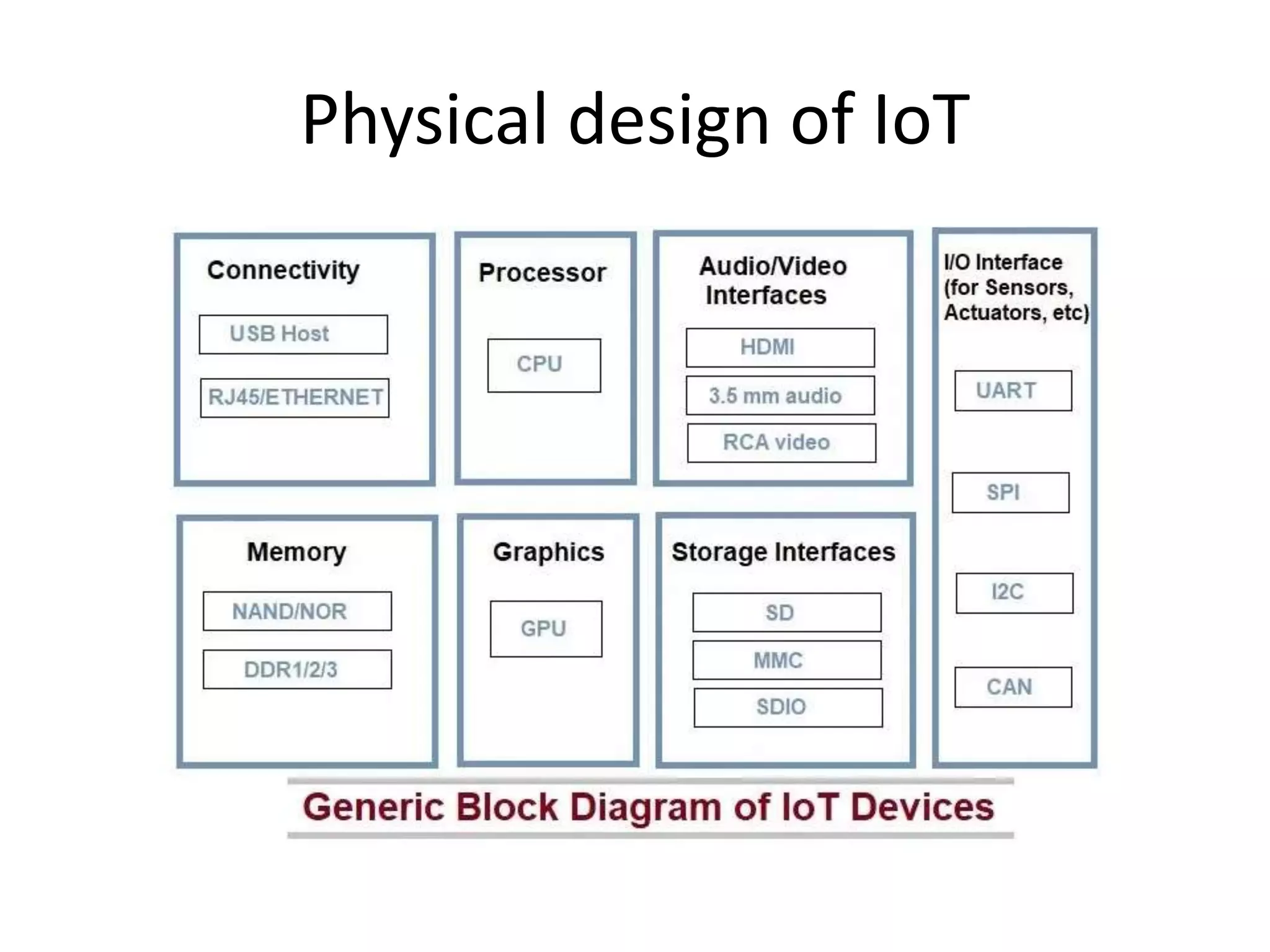
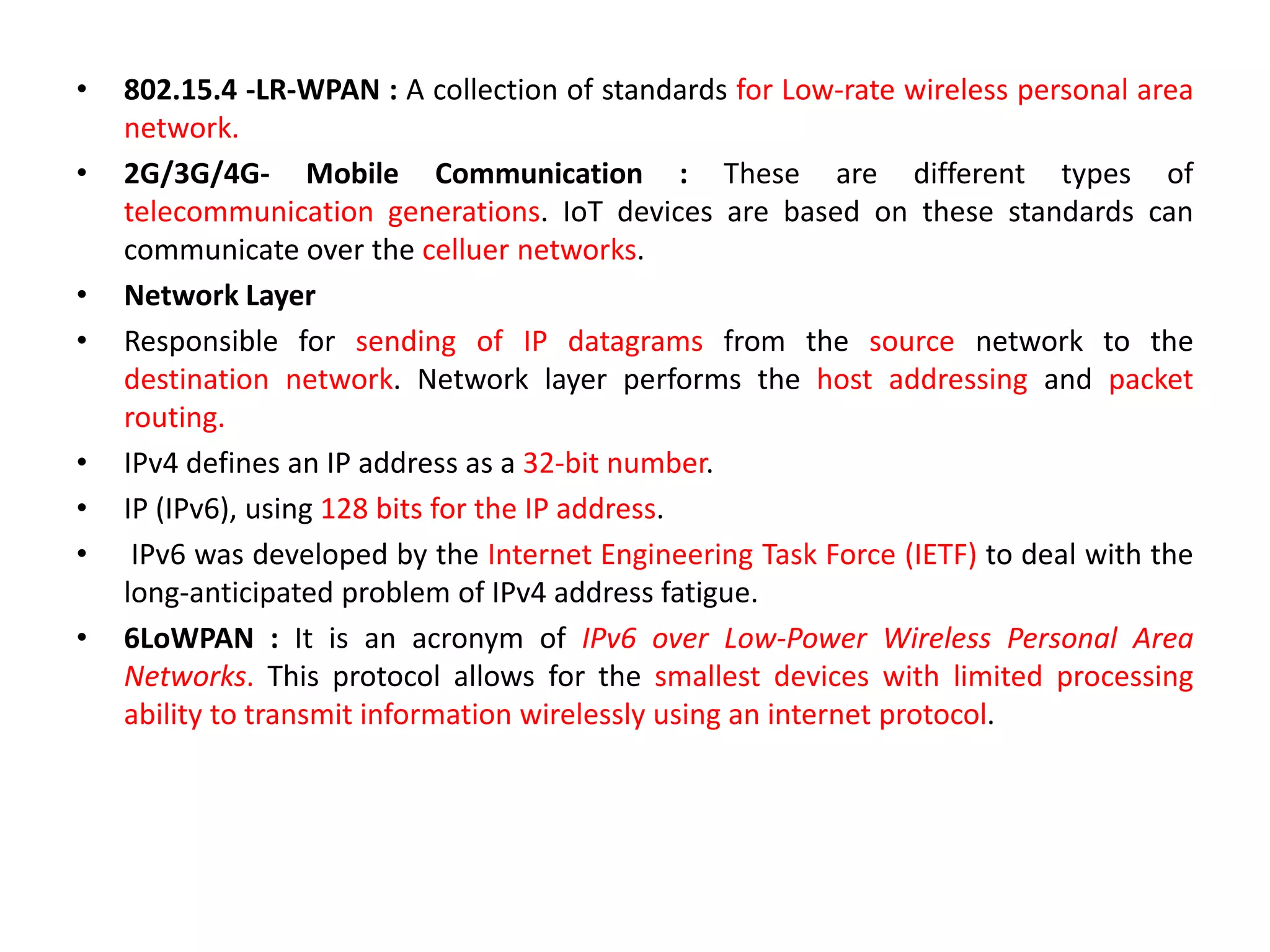
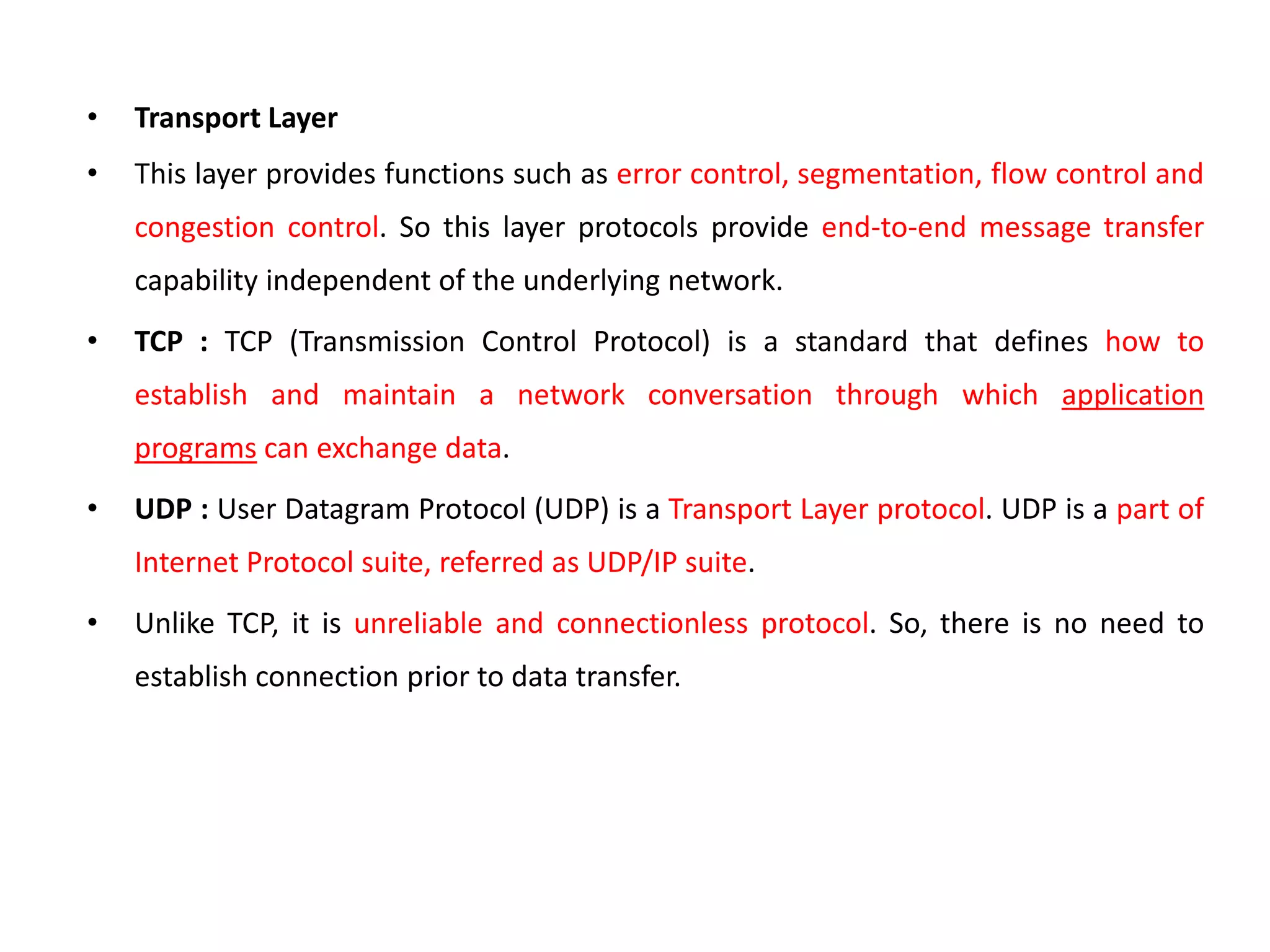
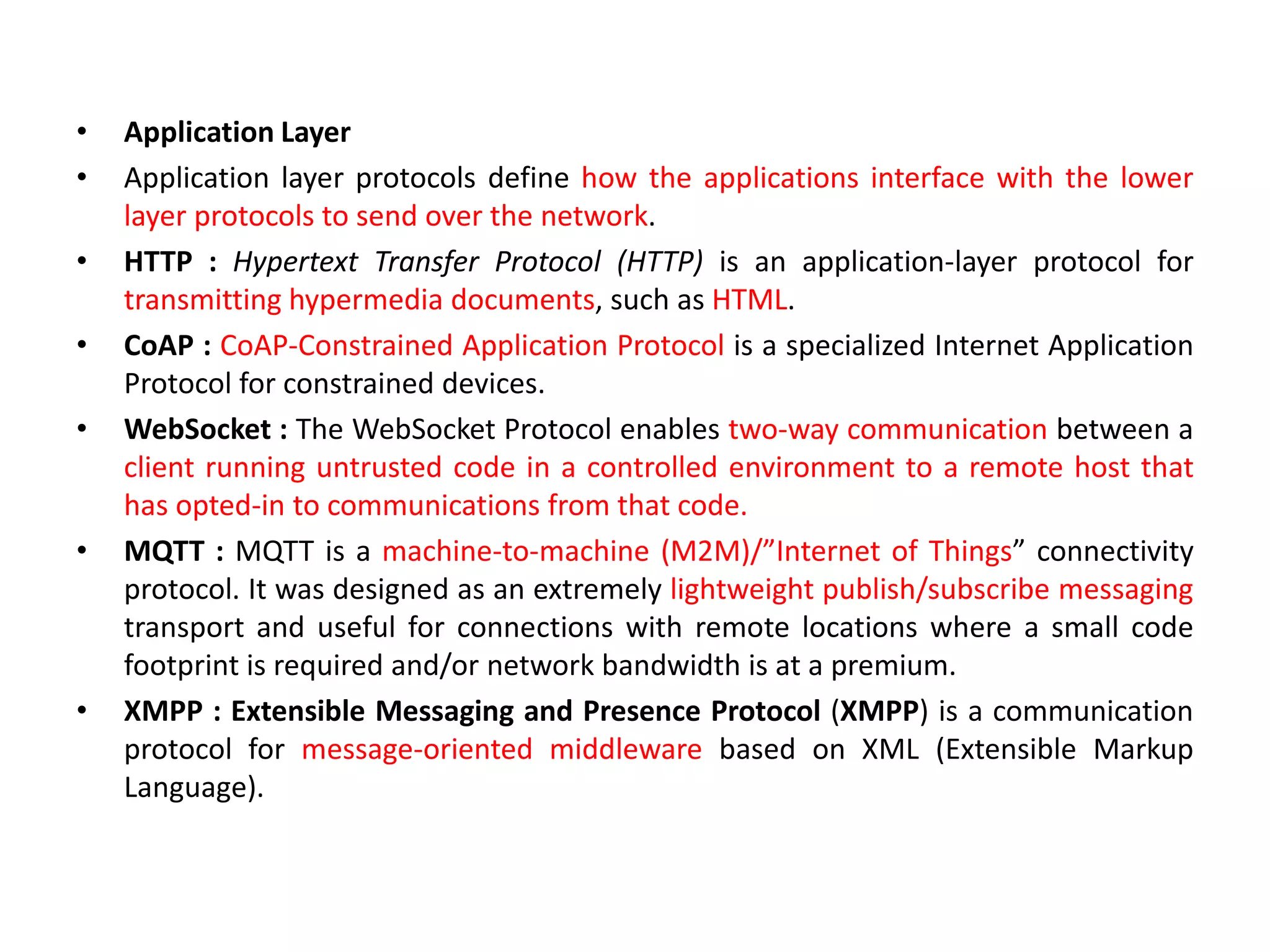
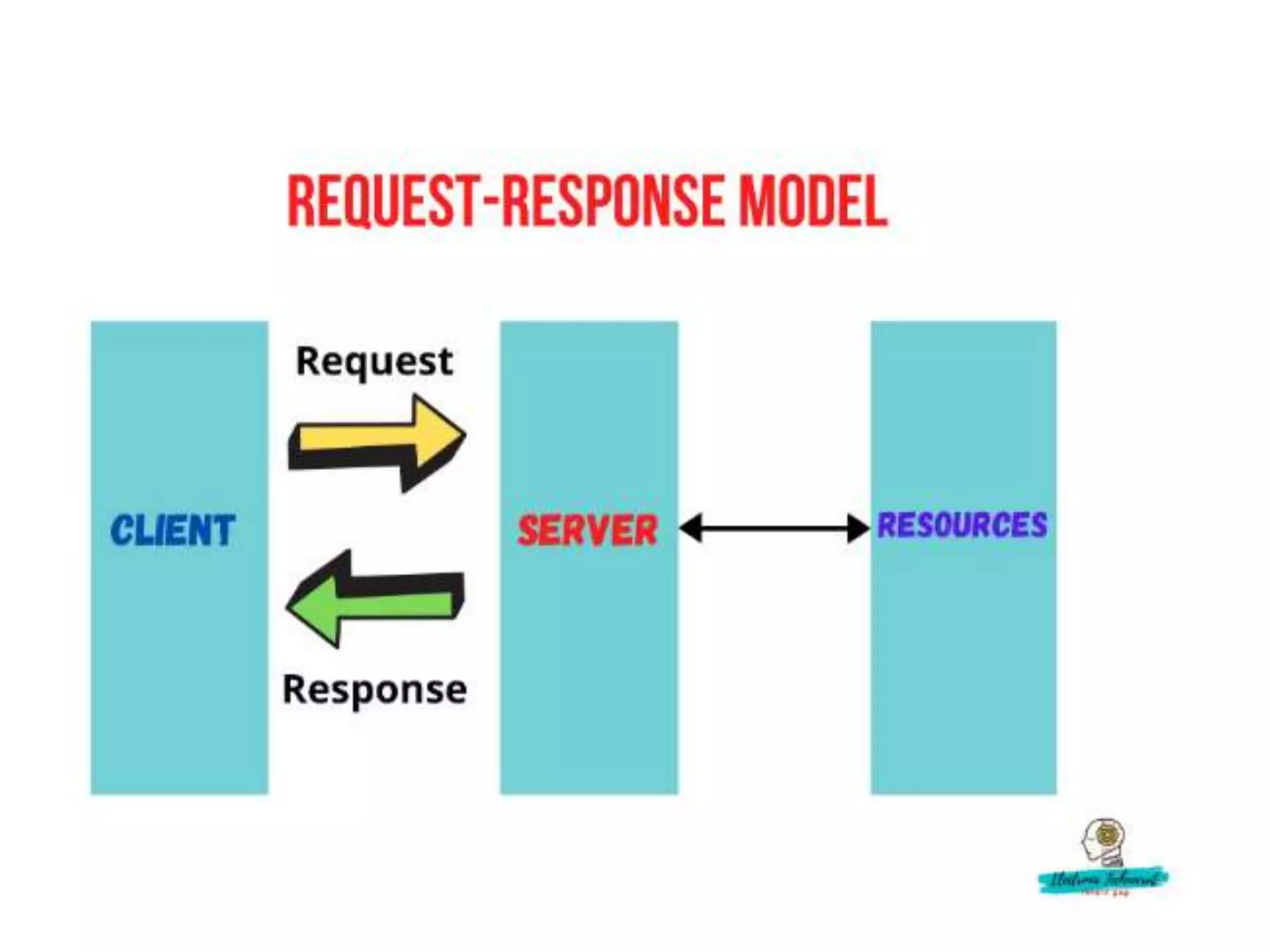
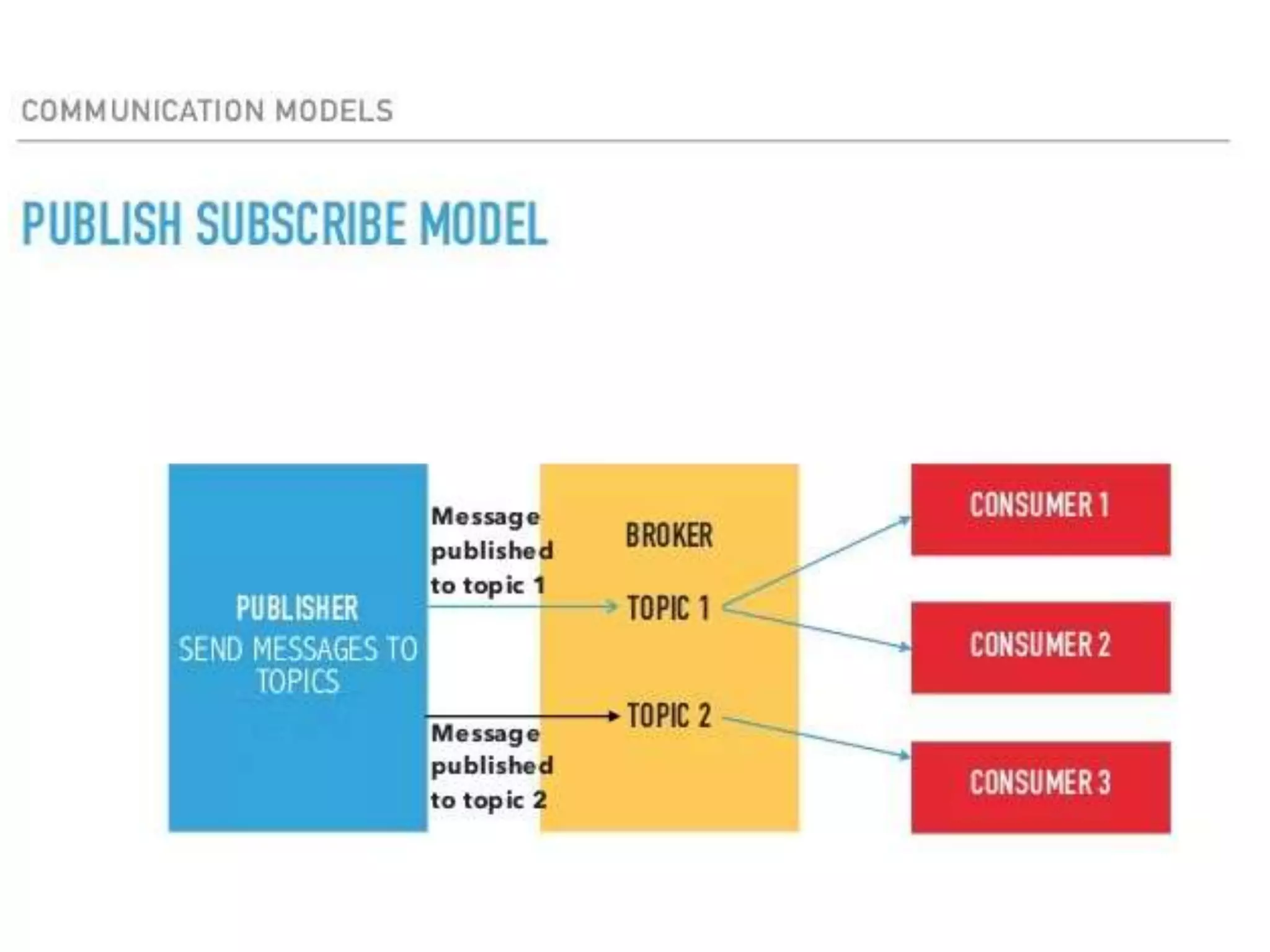
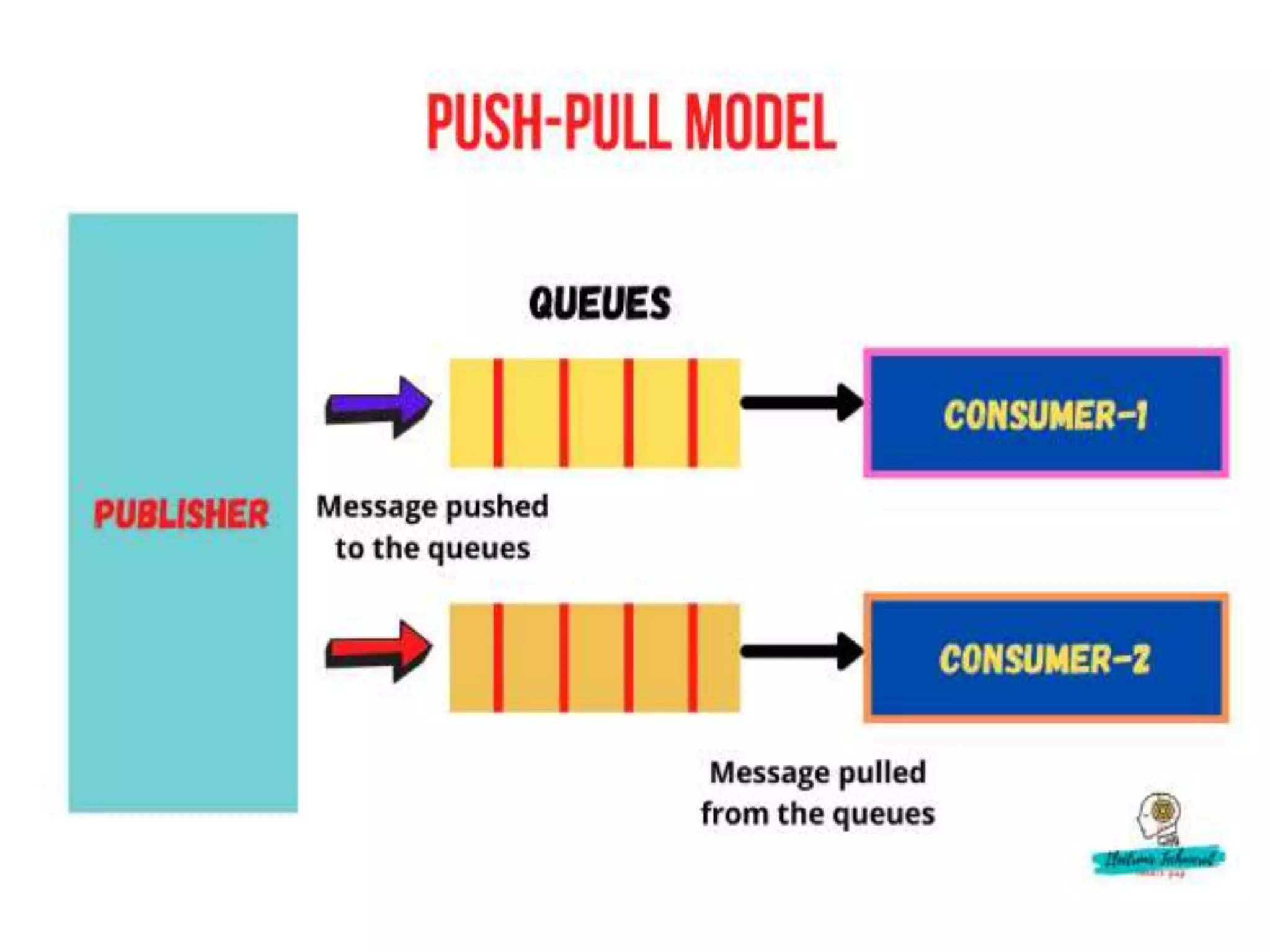
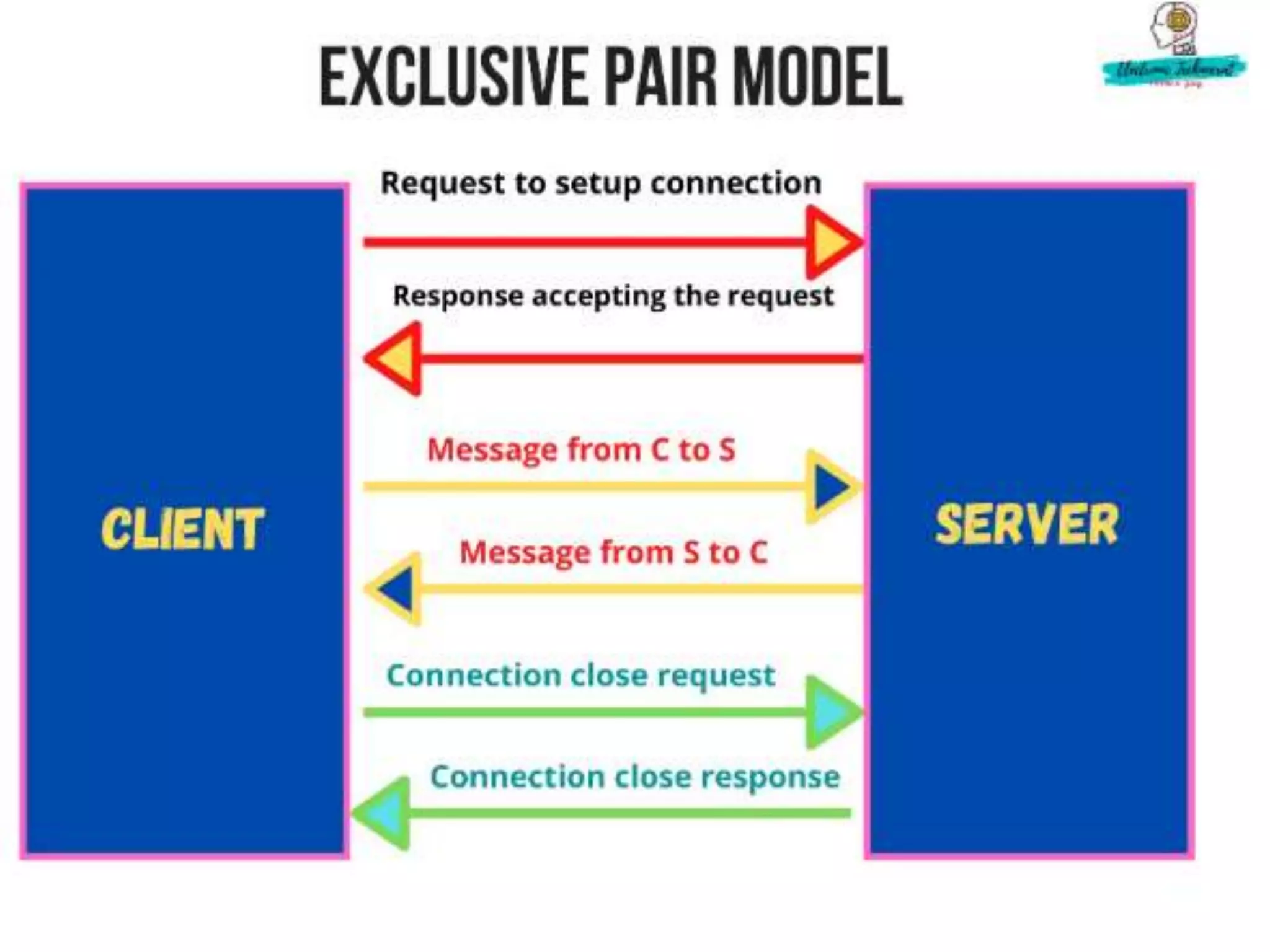
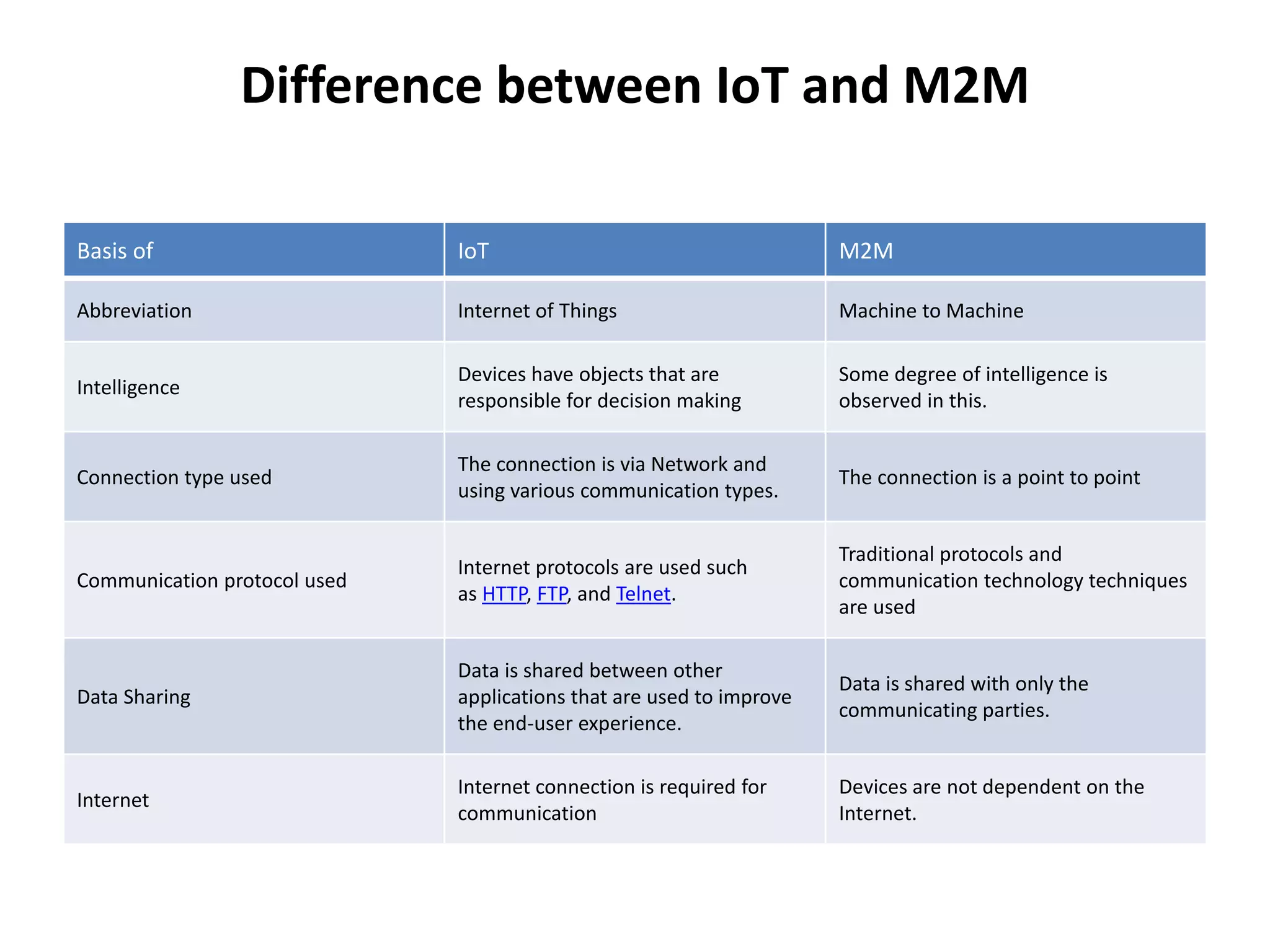
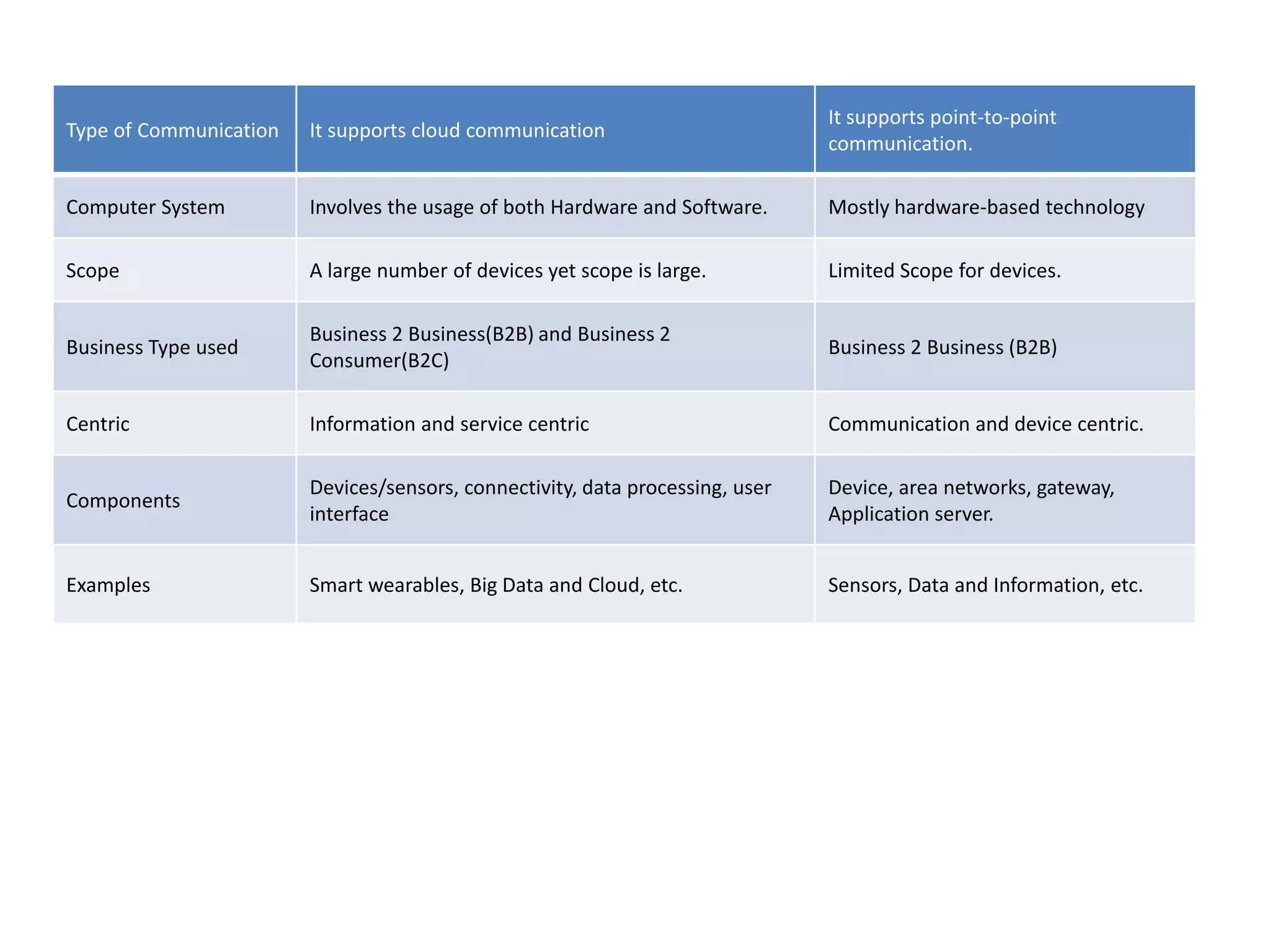
This document provides an overview of the course "18BME18 INTERNET OF THINGS FOR BIOMEDICAL ENGINEERS". The course aims to discuss IoT concepts, interpret wireless sensor network protocols, illustrate IoT applications in healthcare using tools and embedded systems. The document outlines the various units that will be covered, including IoT and M2M communication models, functional blocks, and protocols. It also compares IoT with M2M and describes software-defined networking.