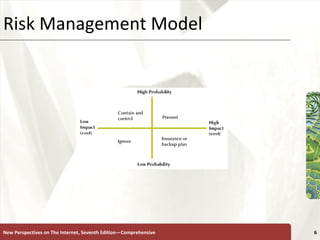
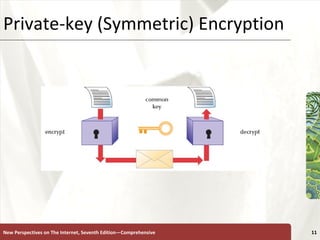
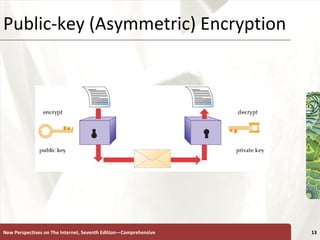
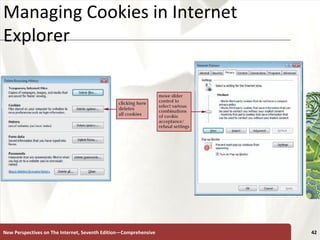
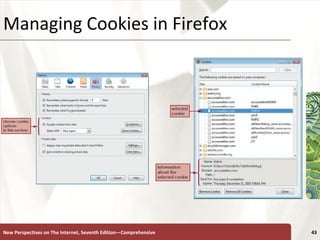
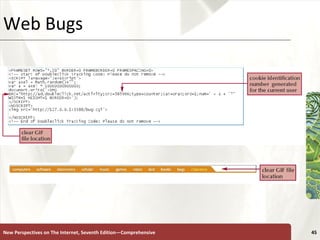
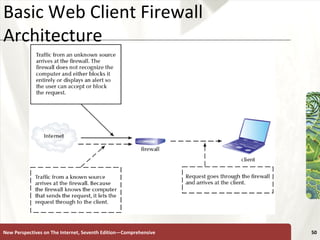
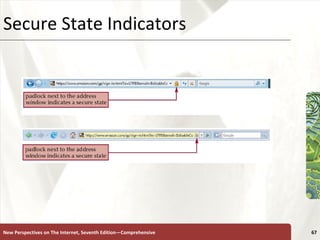
The document discusses various topics related to internet security, including secrecy, integrity, necessity, threats like hackers, viruses, denial of service attacks, and online crimes. It also covers ways to protect against these threats, such as encryption, antivirus software, firewalls, and managing cookies and active content.