The document discusses Alan Turing and the origins of artificial intelligence. It covers:
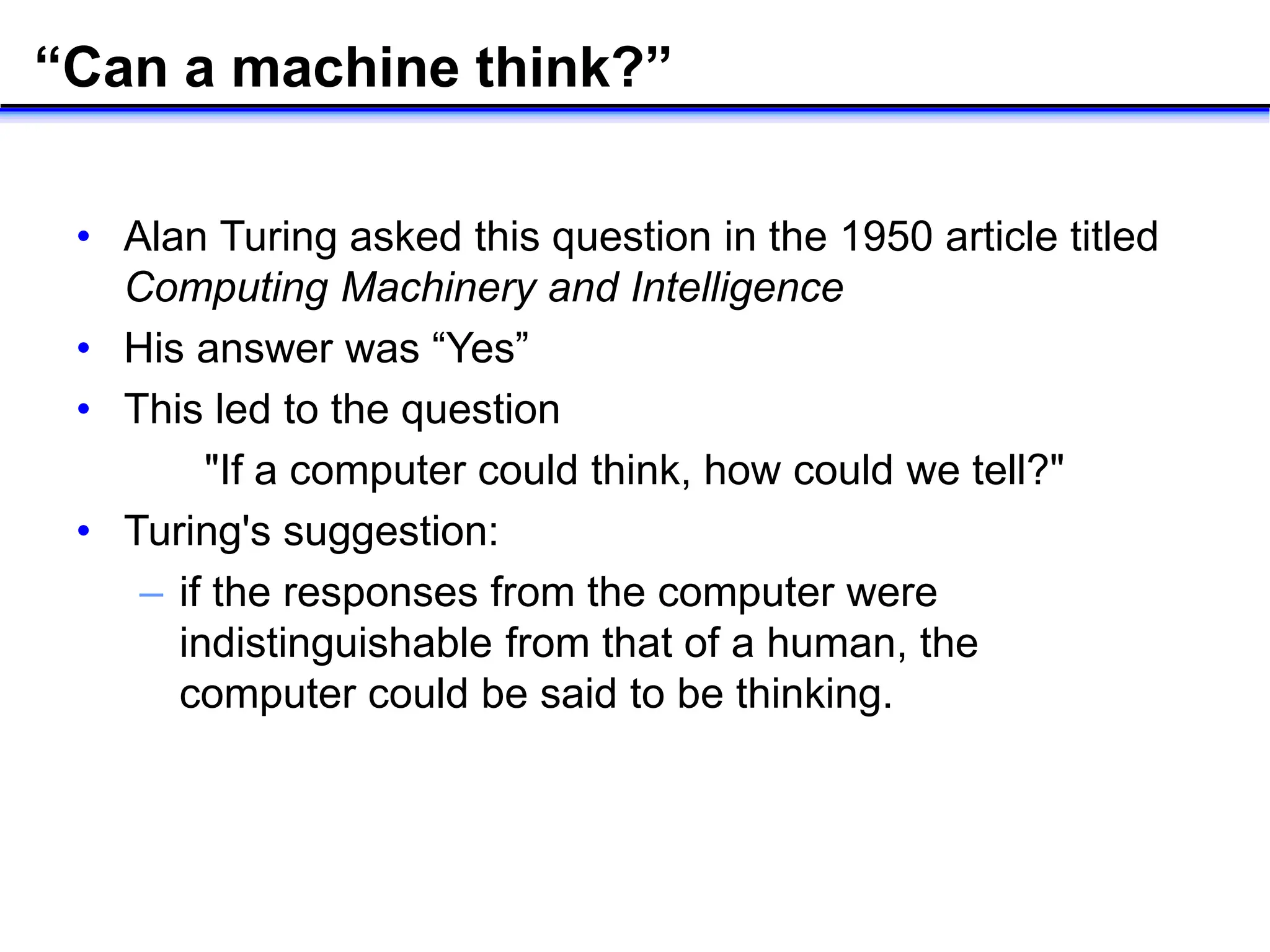
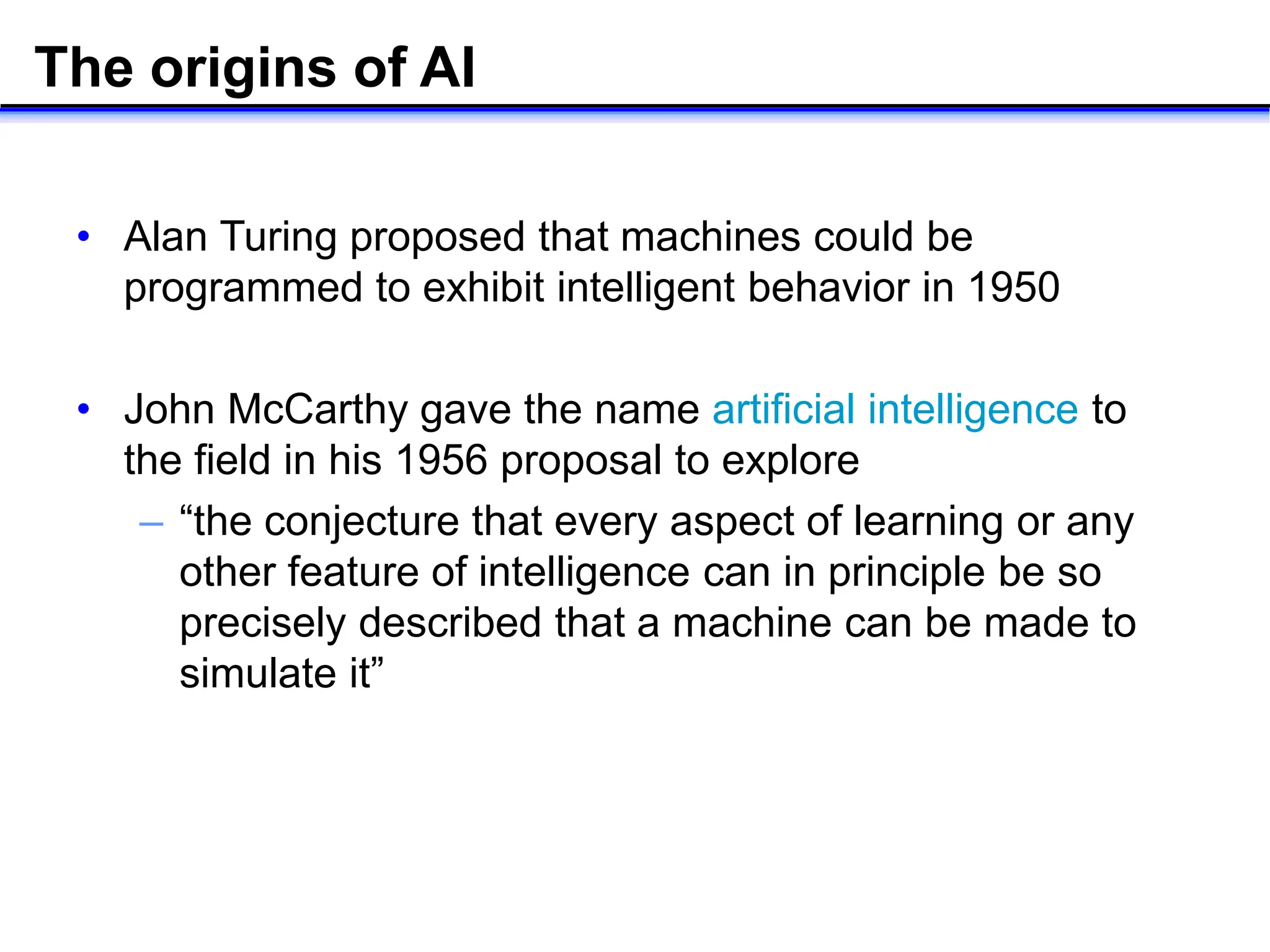
- Turing's 1950 proposal of the Turing test to determine if a machine can think
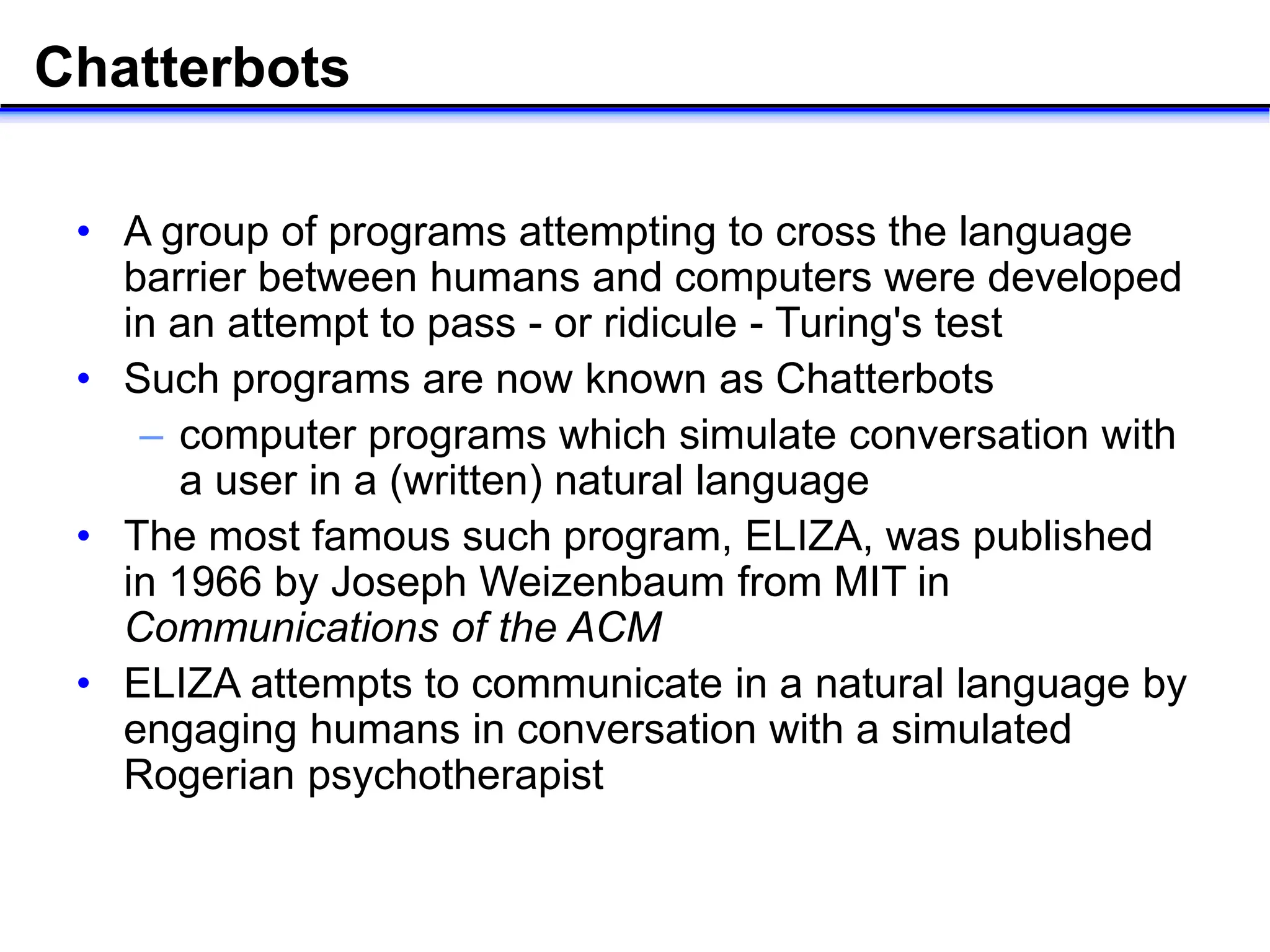
- Early chatbots like ELIZA that aimed to pass the Turing test by simulating conversation
- The annual Loebner Prize competition that awards the chatbot deemed most human-like
- Debates around the validity of the Turing test and what truly constitutes intelligence
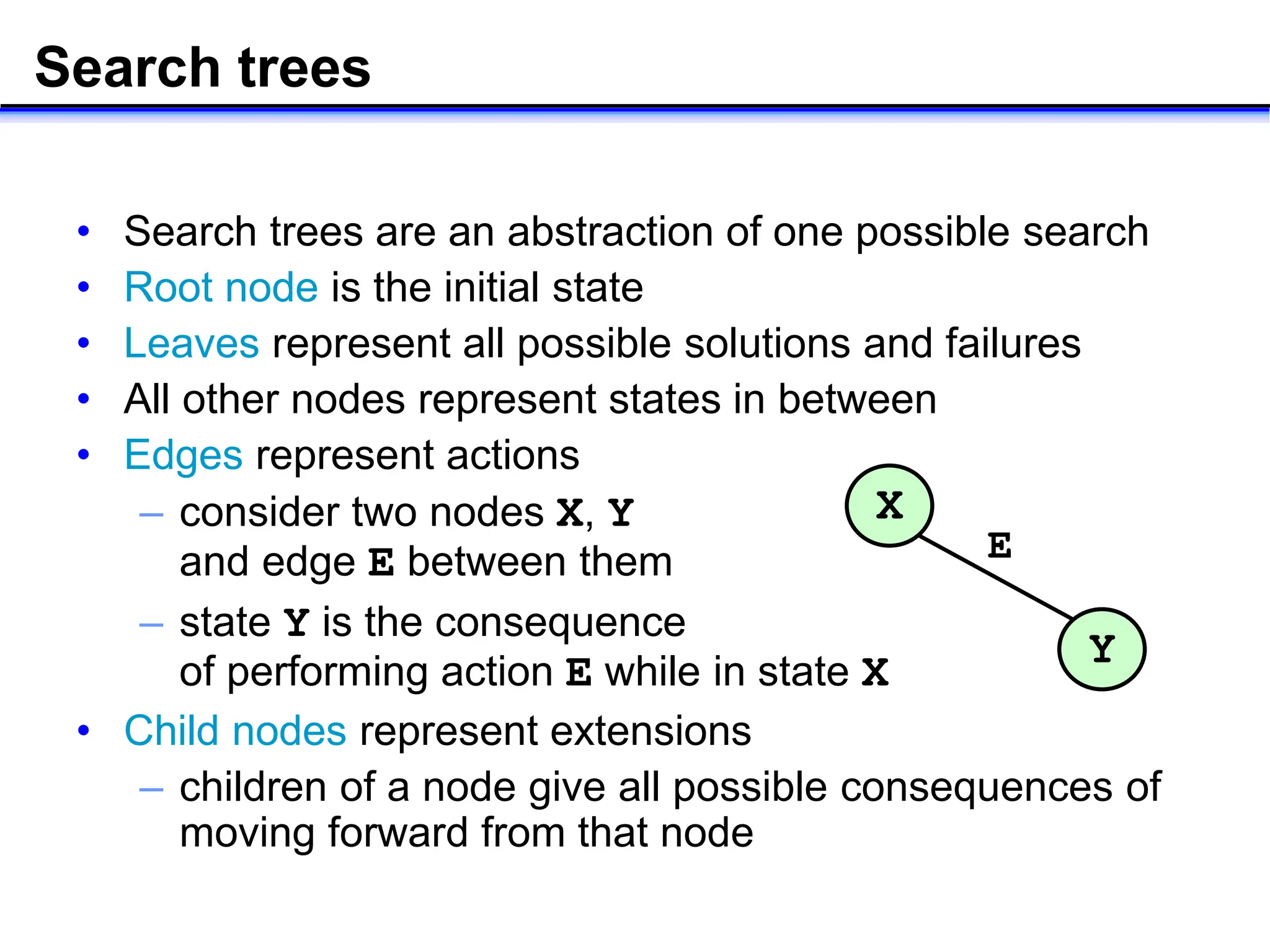
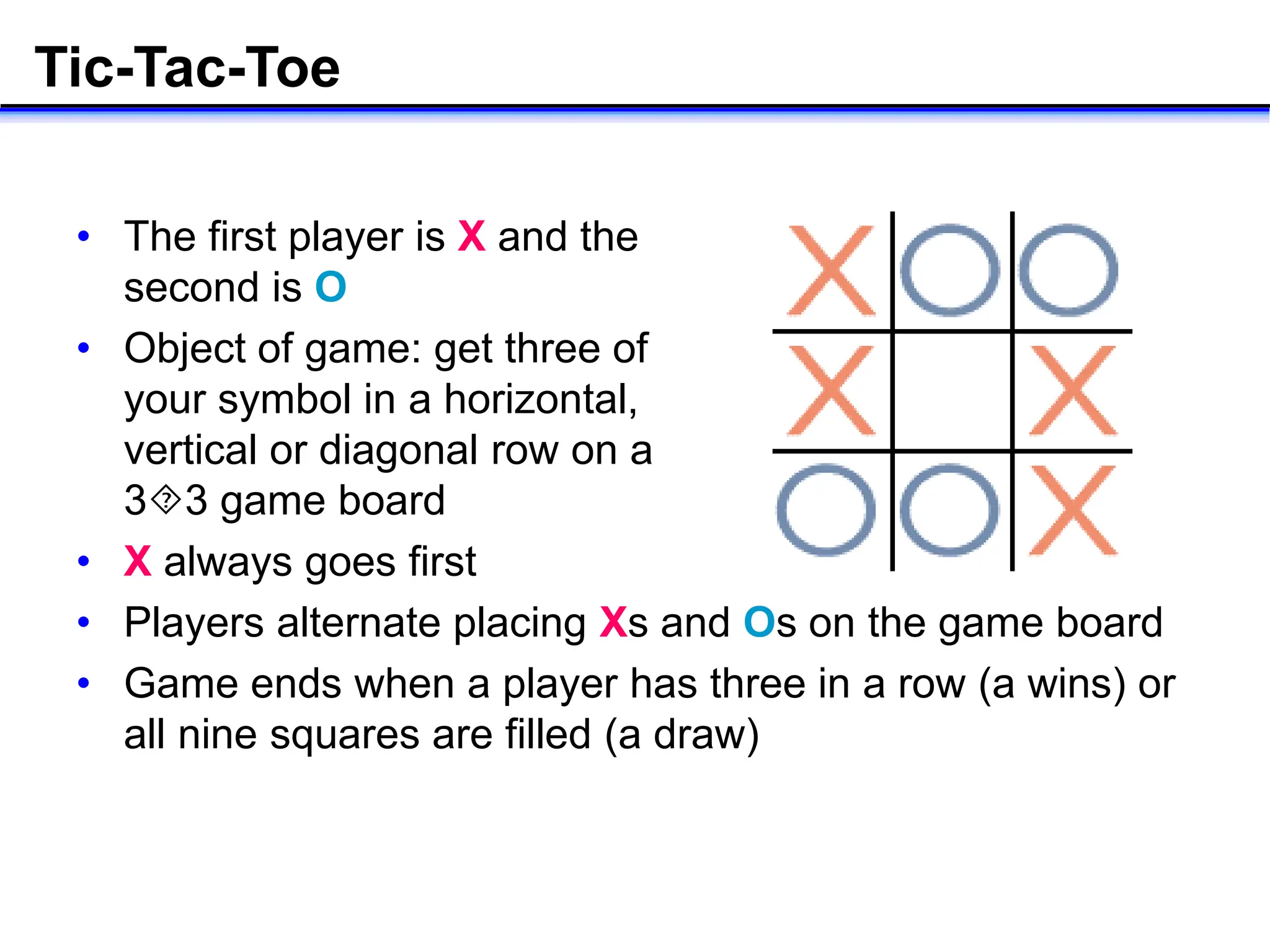
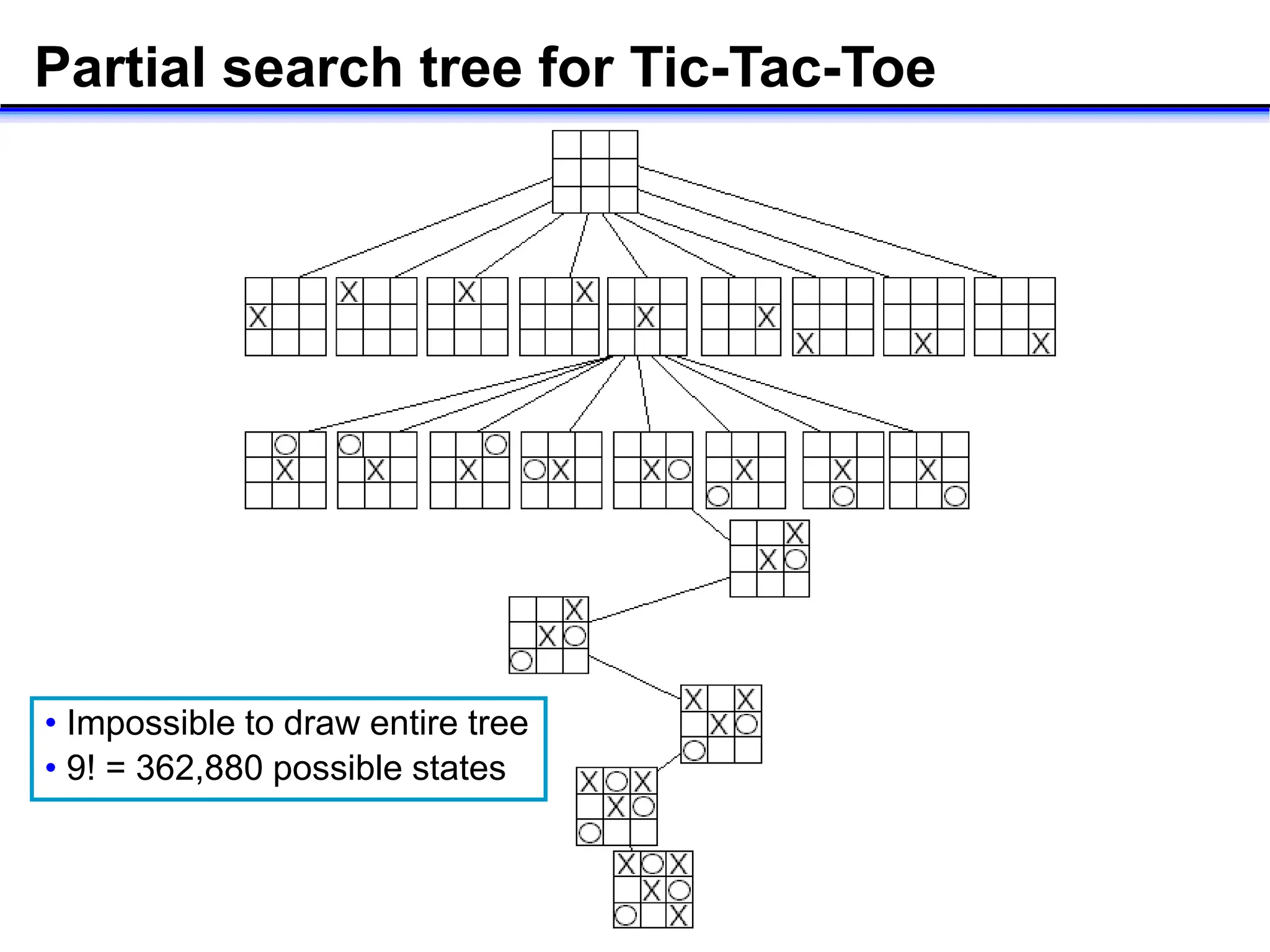
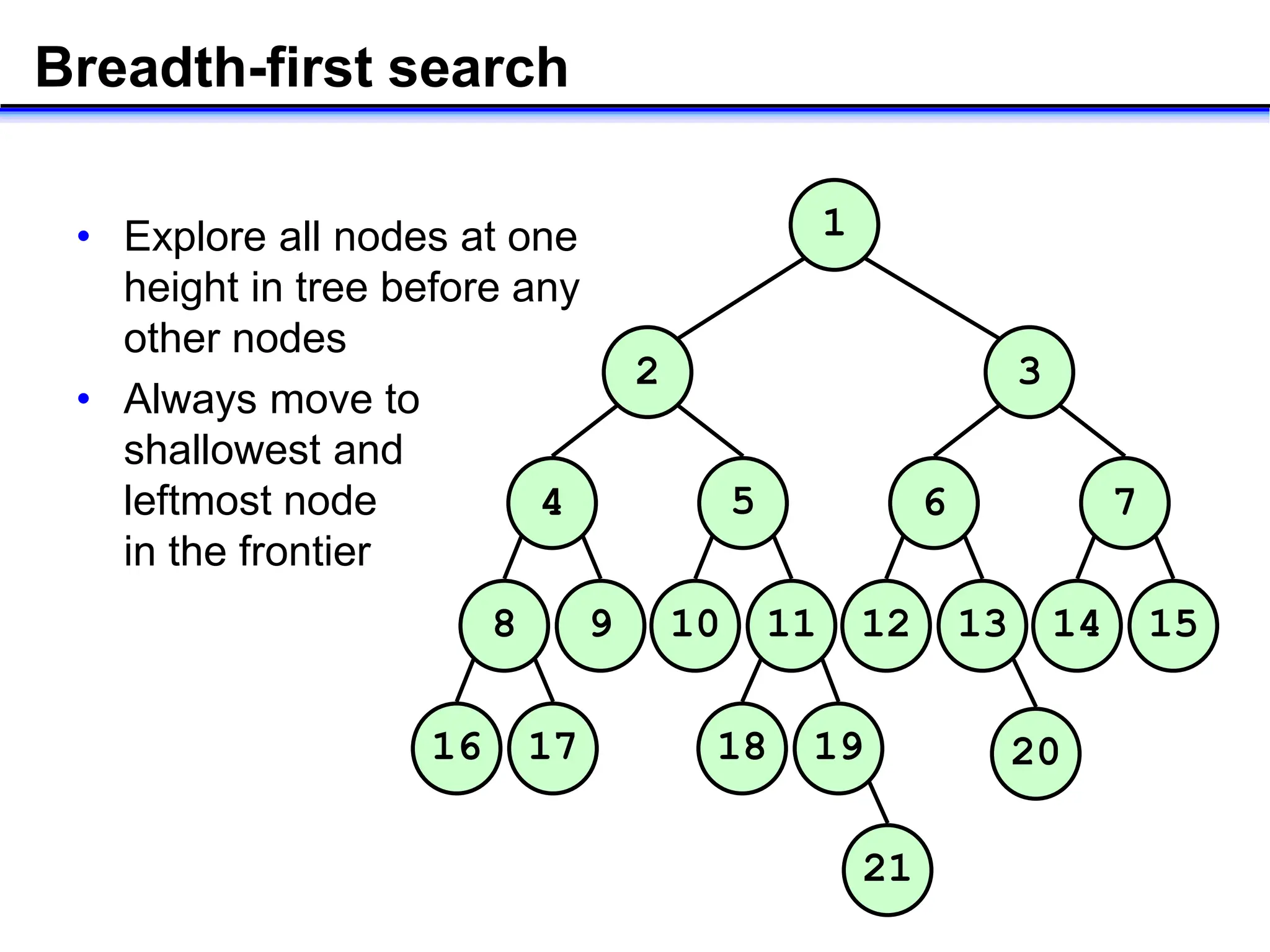
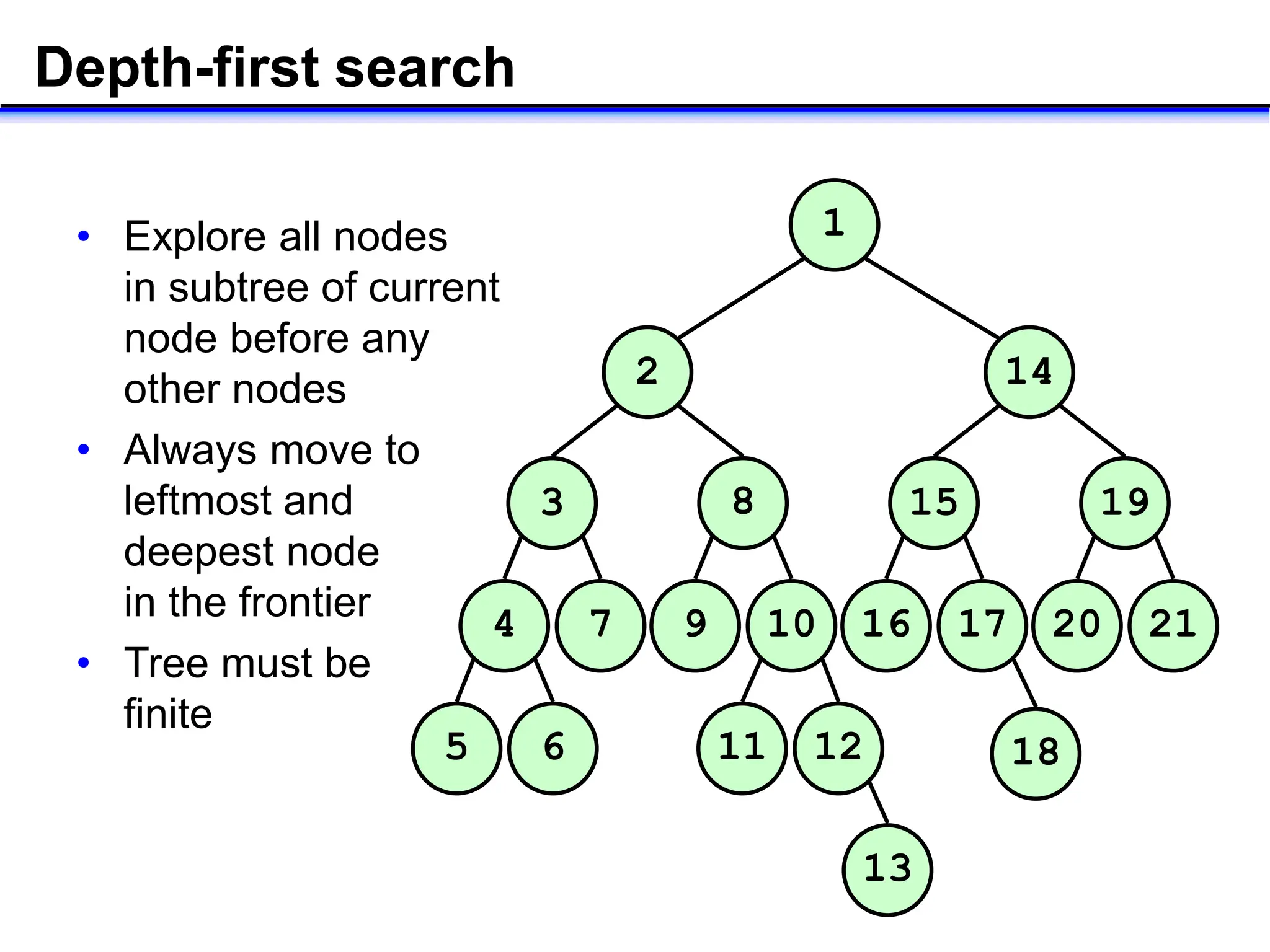
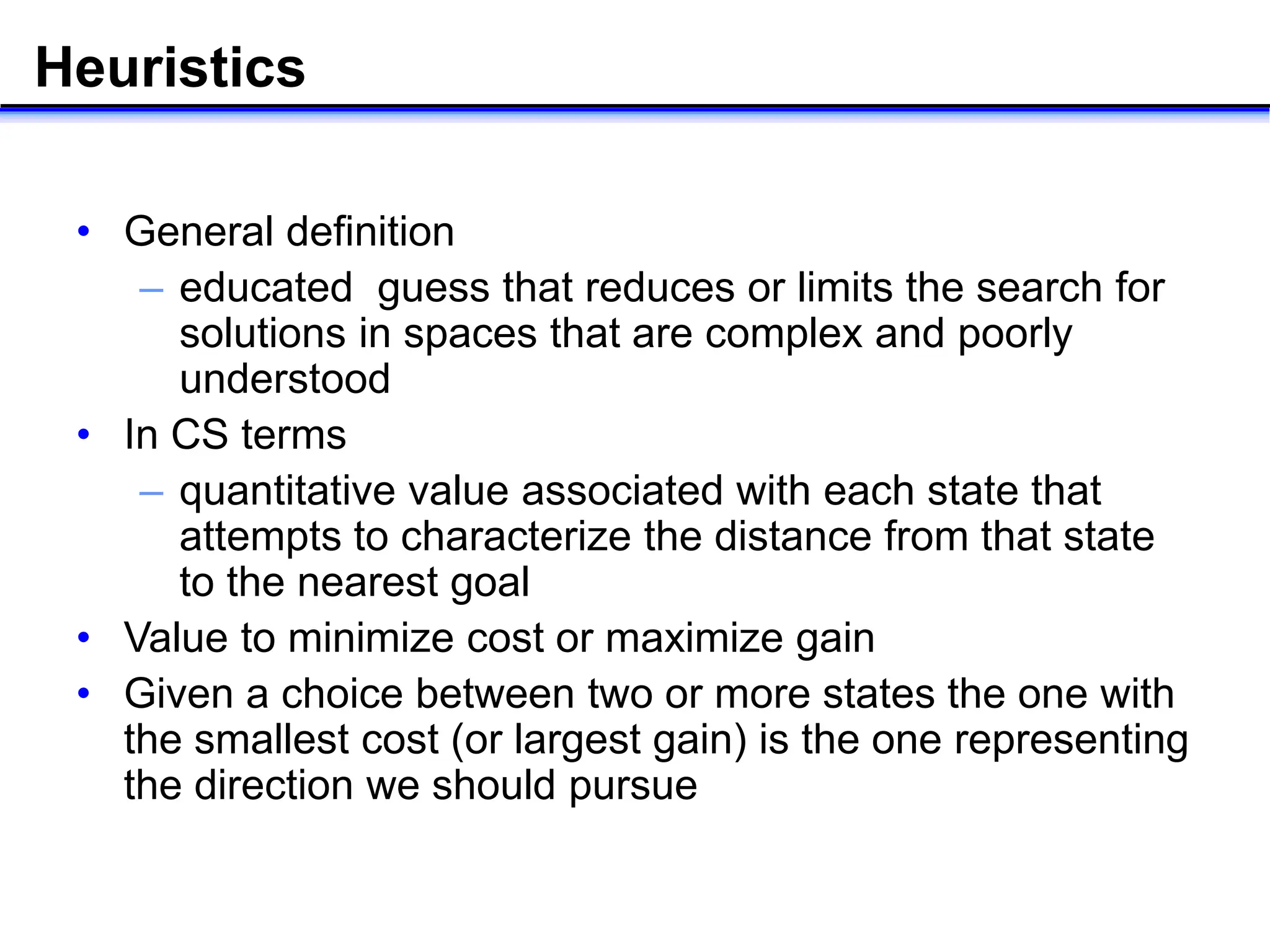
- Key concepts in AI like search, reasoning, and different search algorithms used