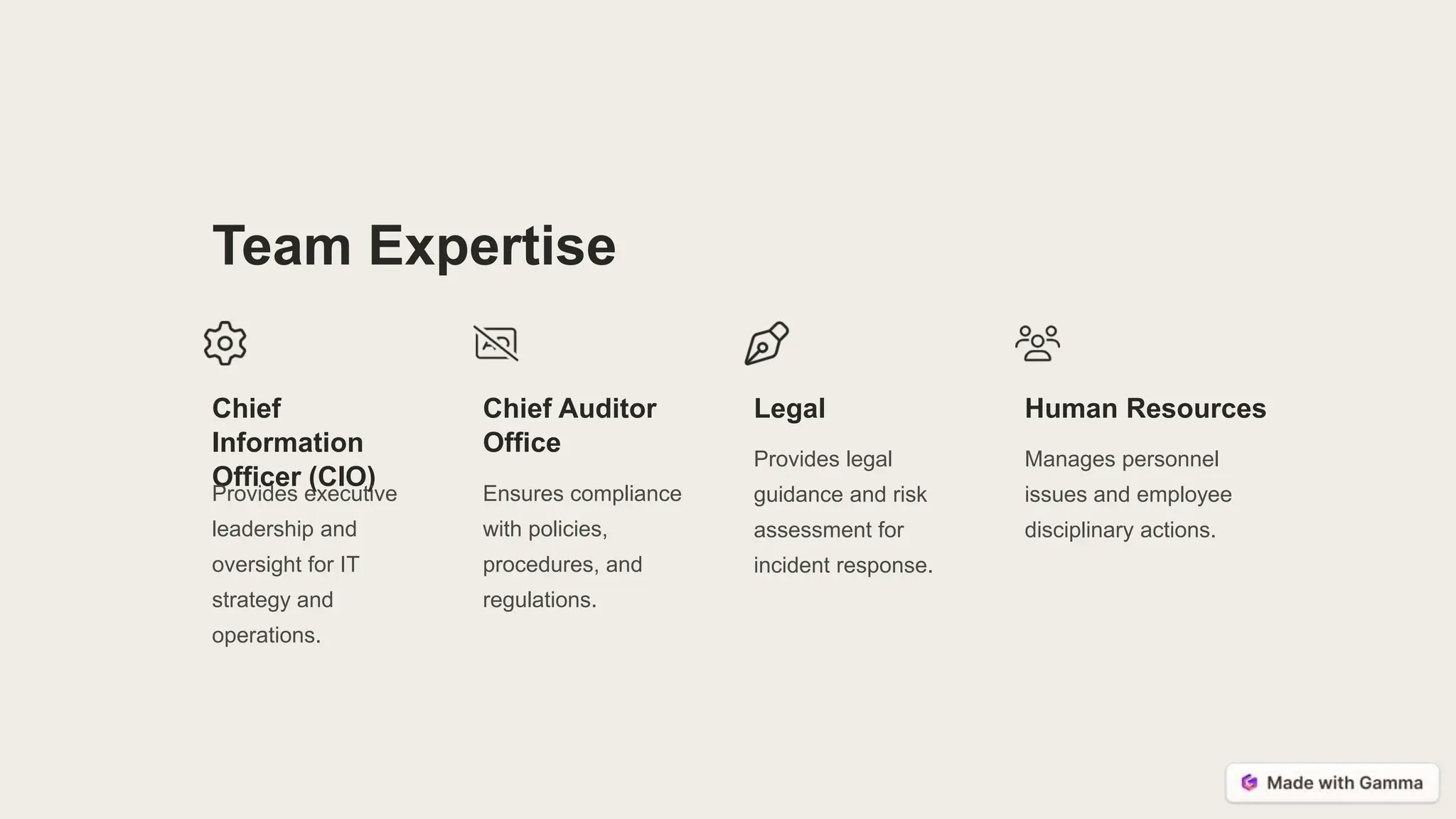
The document discusses incident response at a university fusion center. It outlines common security incidents like phishing, ransomware attacks, and lost/stolen devices. Effective response requires clear policies, a well-coordinated incident response team (CSIRT), and standardized procedures. The CSIRT is led by a CISO and includes experts from IT, legal, auditing, and HR. The CSIRT's key responsibilities are identifying, mitigating, reviewing, and reporting security incidents to preserve data confidentiality, integrity and system availability.