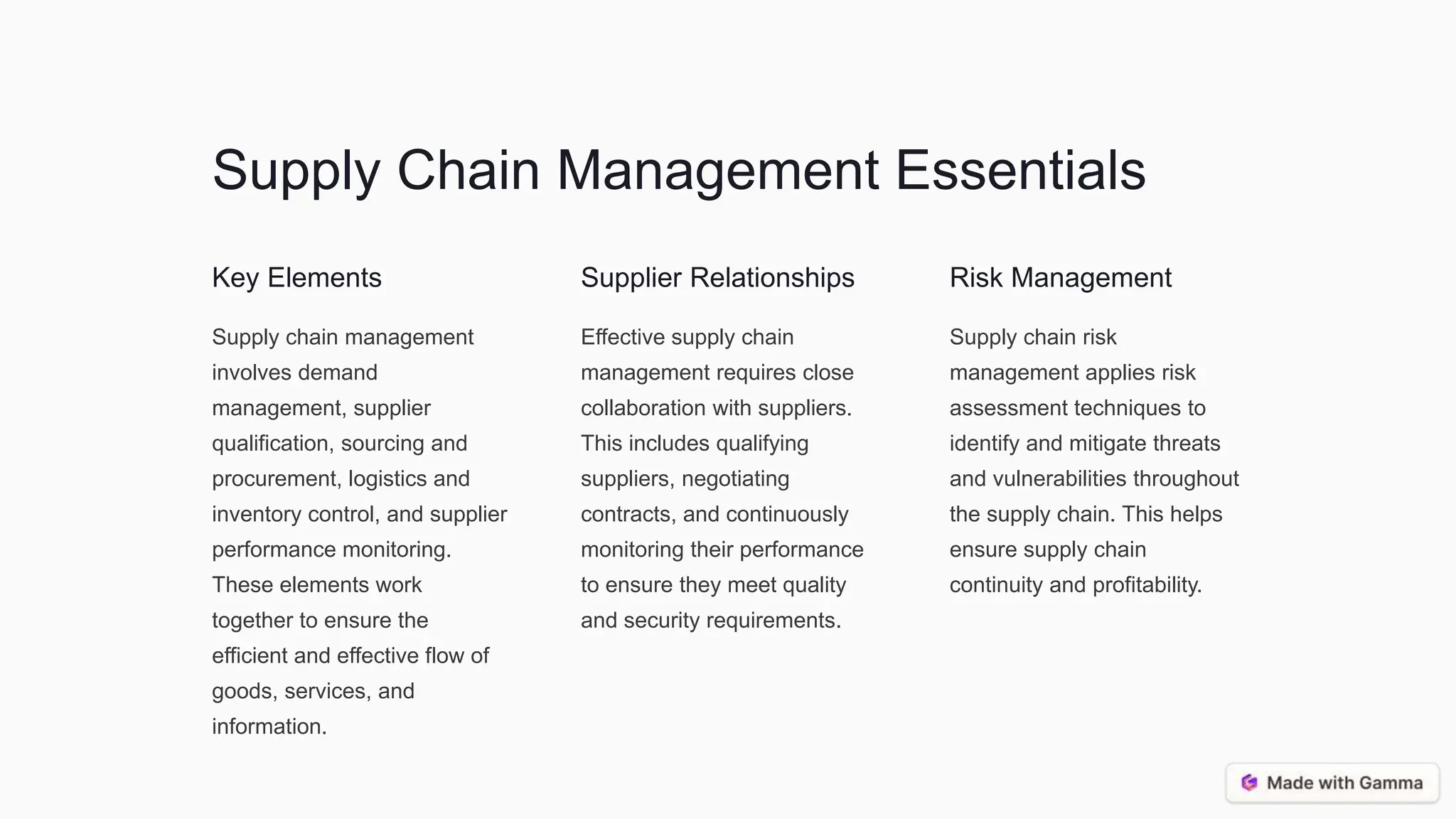
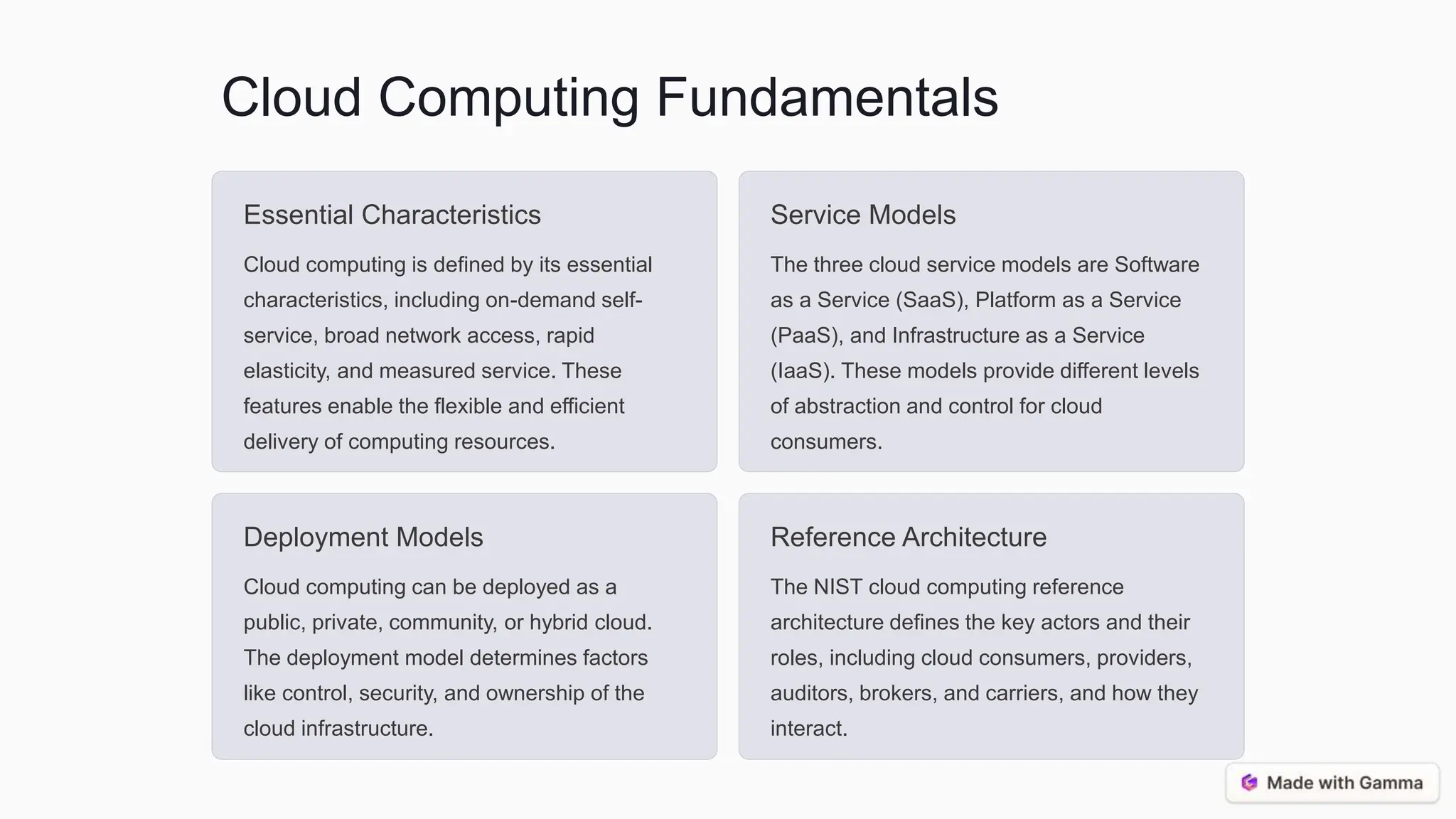
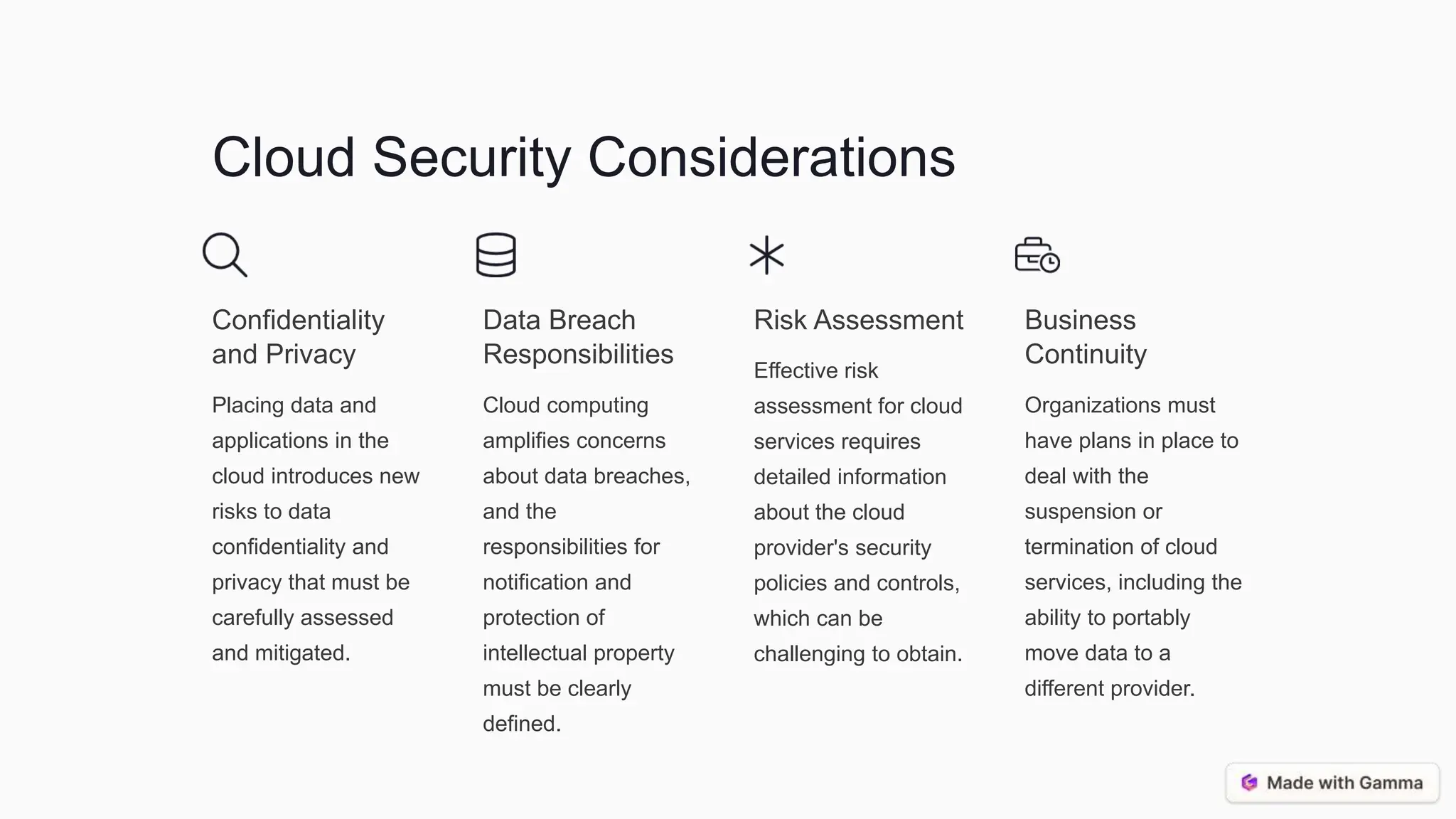
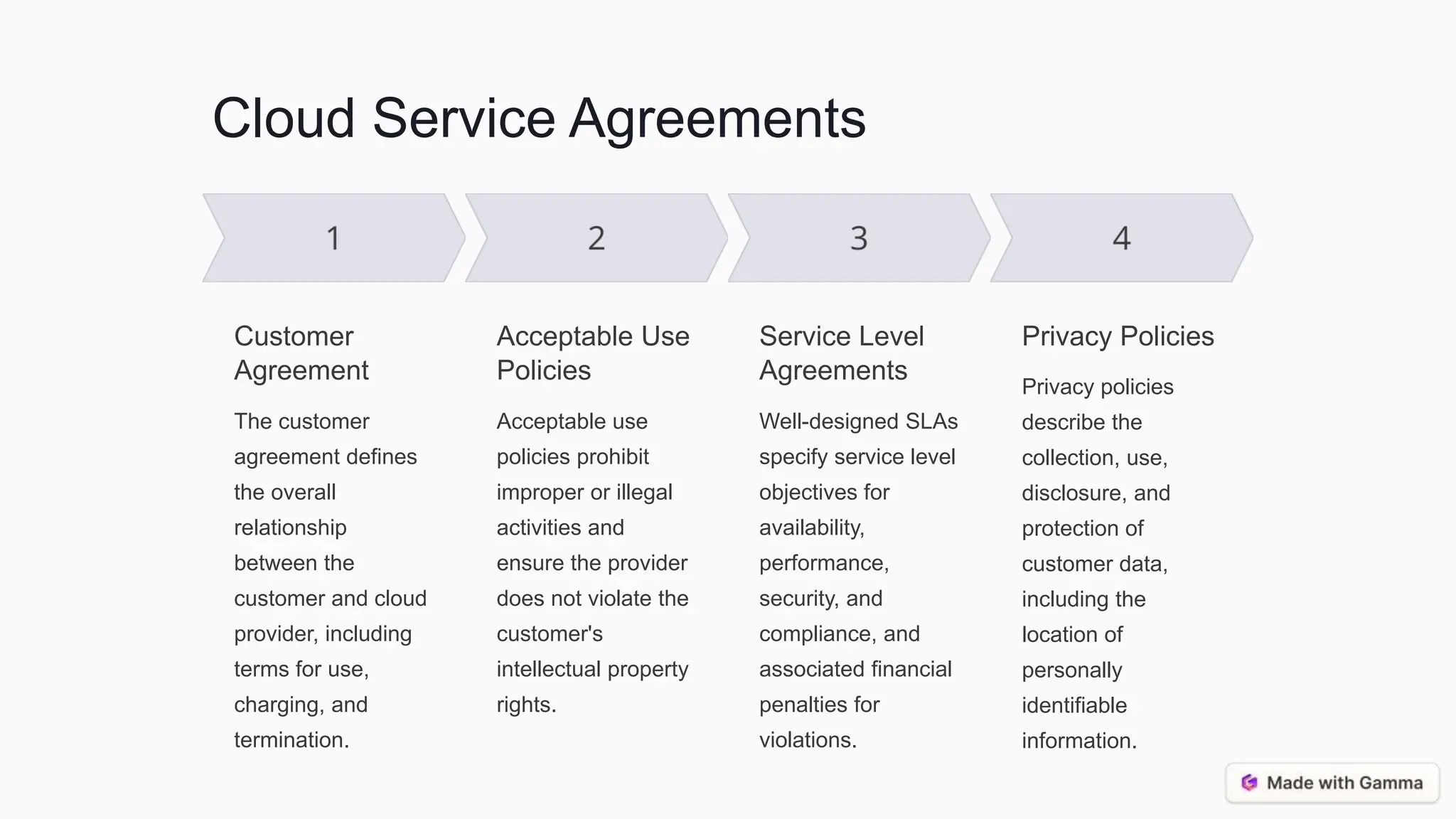
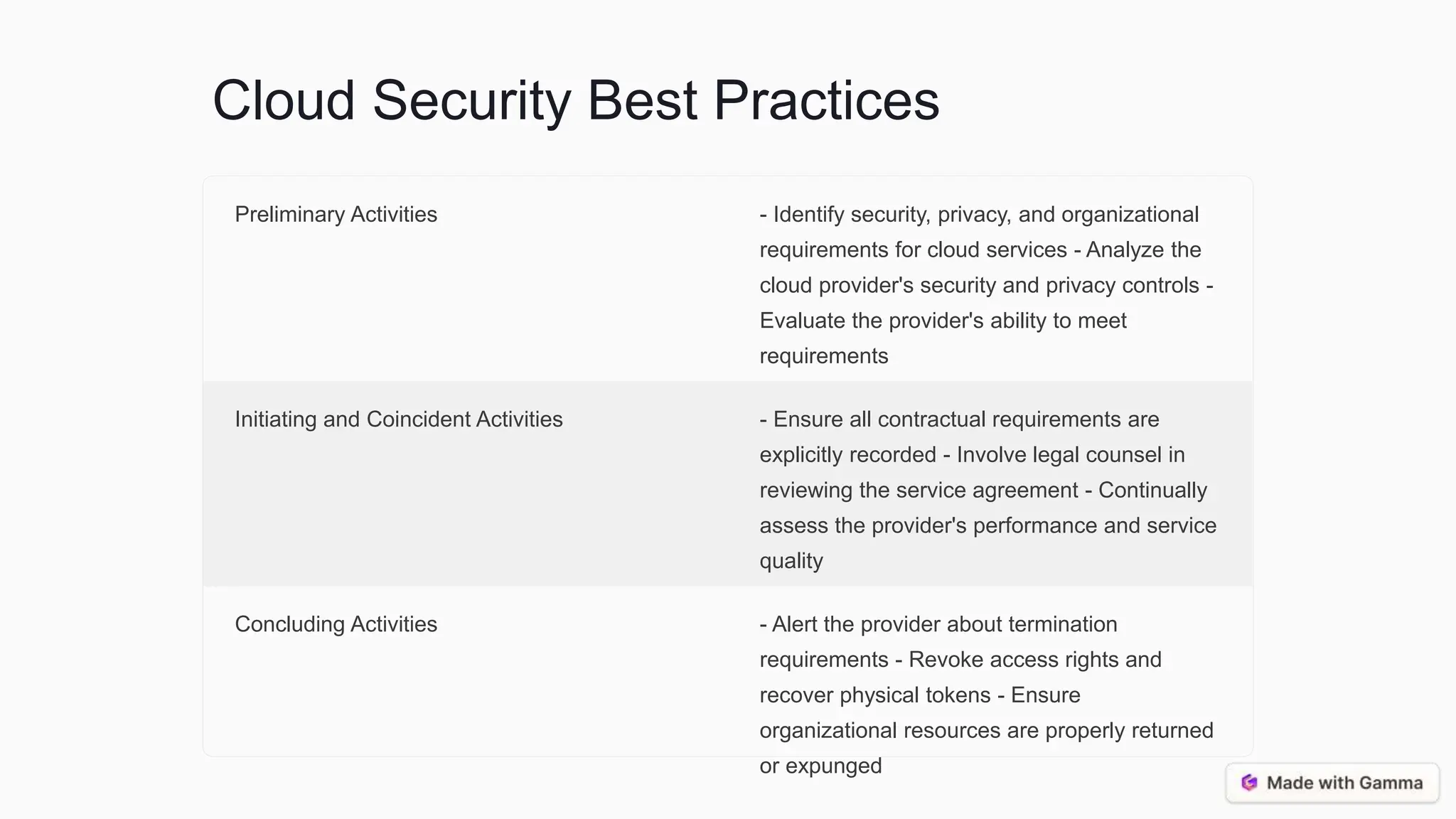
This document discusses supply chain management, cloud computing, and best practices for security. It covers the traditional and ICT supply chains, key supply chain elements like risk management, and assessing supply chain risks through threat analysis and vulnerability assessment. It also discusses cloud computing models and security considerations, as well as best practices for vendor selection, risk mitigation, information management, and the cloud service lifecycle. The conclusion emphasizes an integrated, continuous monitoring approach and the importance of collaboration and transparency between organizations and their suppliers/cloud providers.