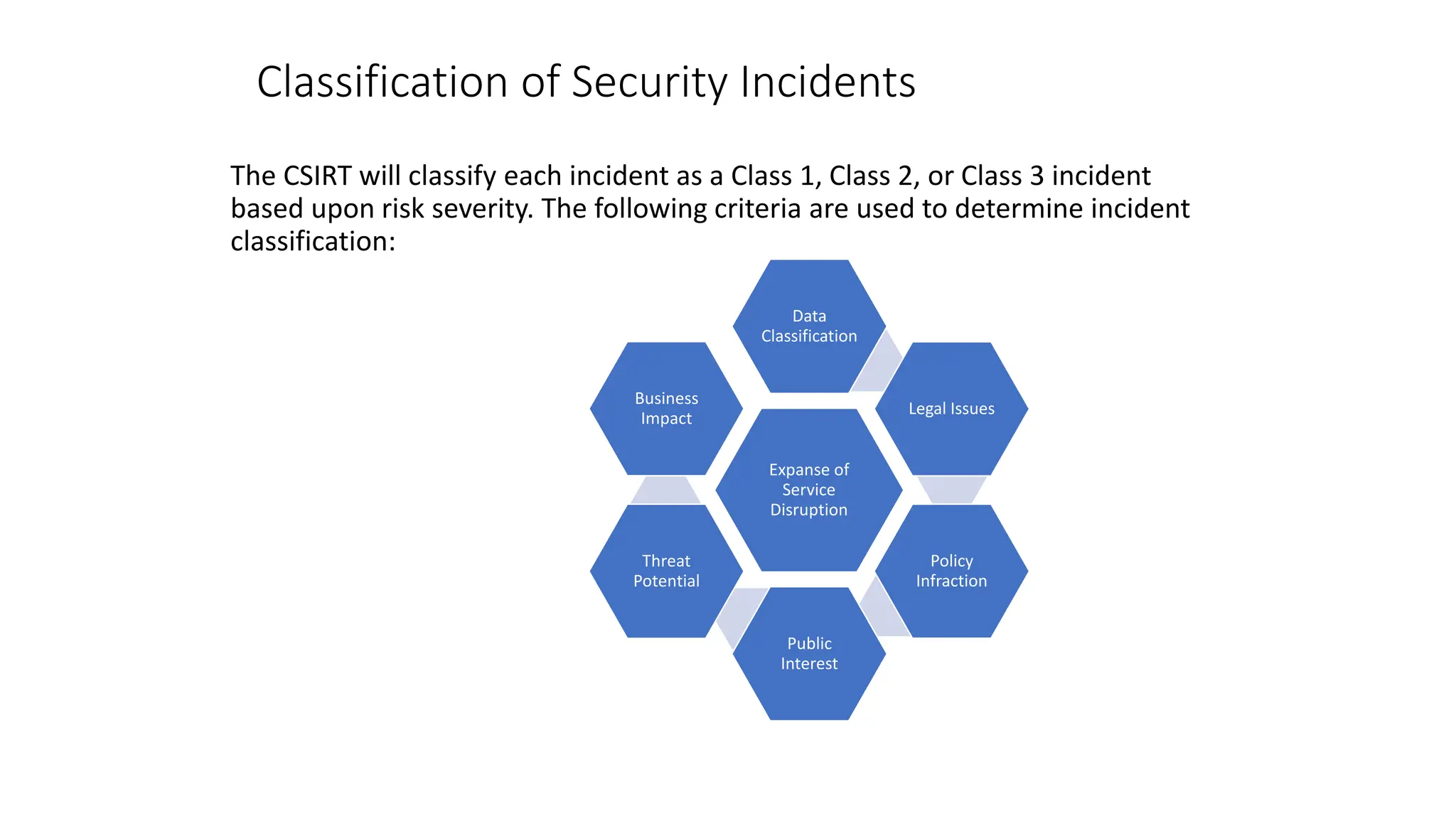
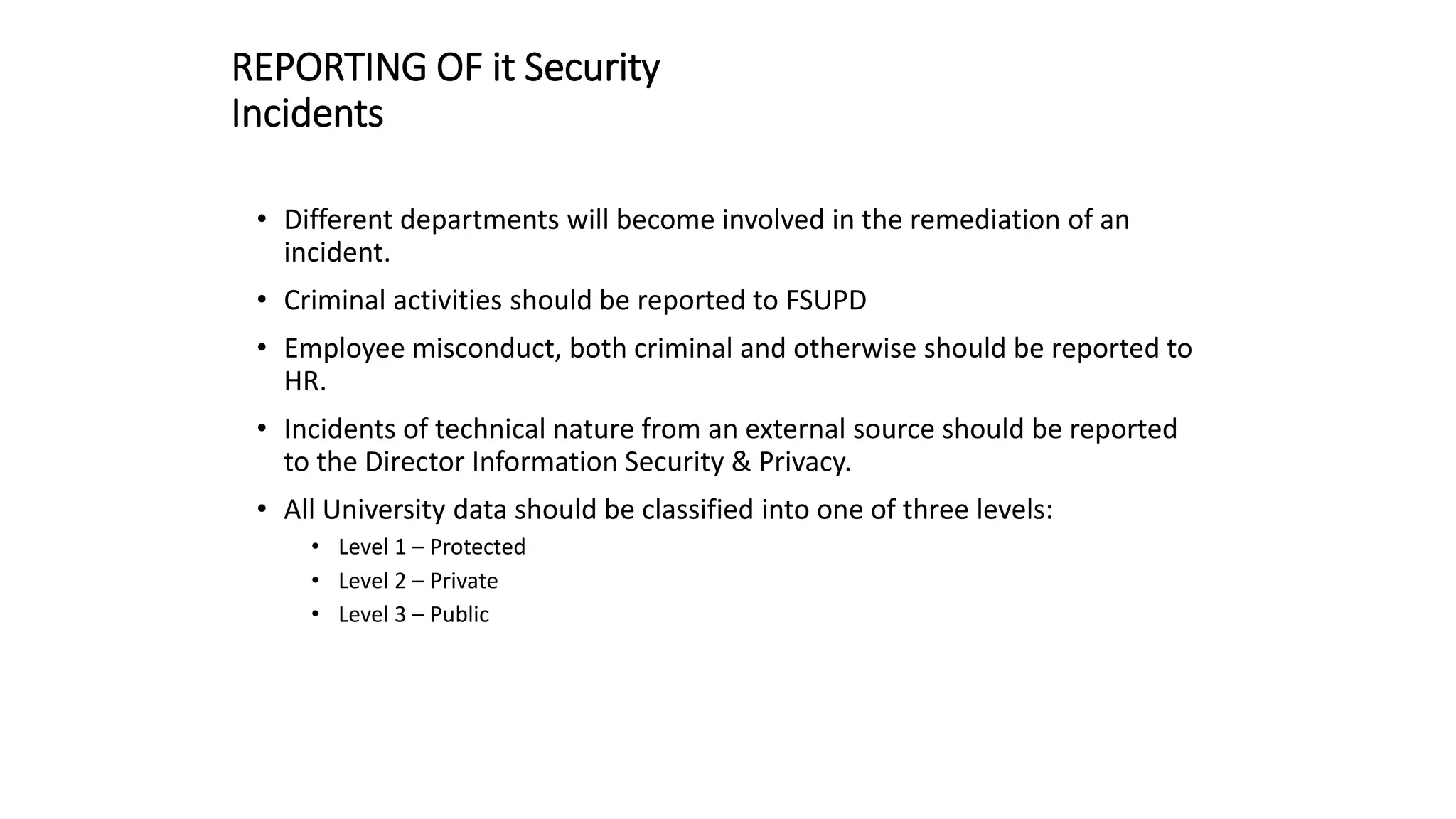
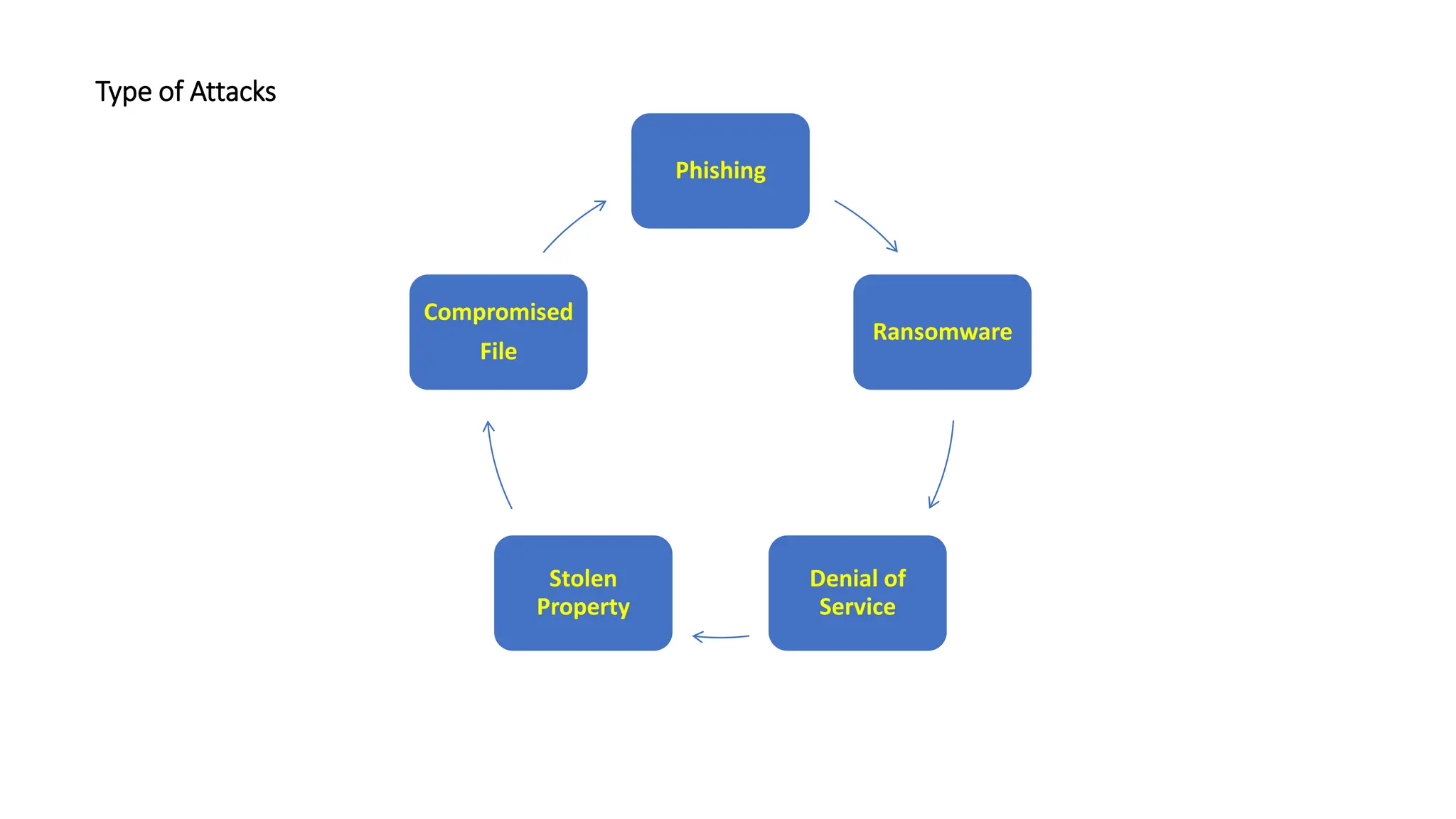
The document outlines the responsibilities and procedures of a Computer Security Incident Response Team (CSIRT). The CSIRT is responsible for classifying, assessing, responding to, and documenting security incidents. Incidents are classified based on their severity as Class 1 (low), Class 2 (moderate), or Class 3 (high). For more severe Class 2 and 3 incidents, the CSIRT leader reports details of the incident including findings, conclusions, and recommendations. The document also describes general procedures for reporting different types of incidents to relevant departments such as IT security, police, or human resources.