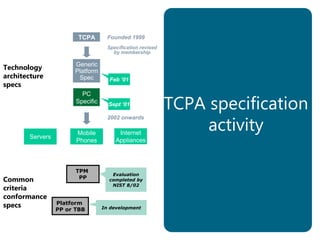
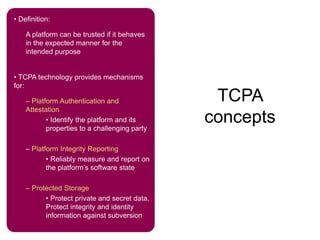
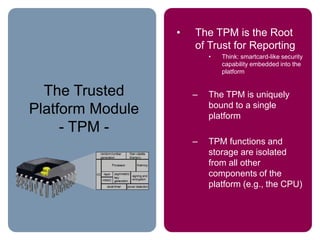
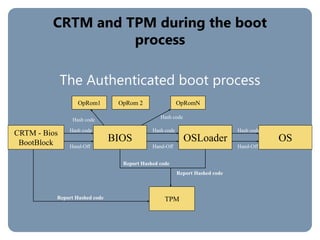
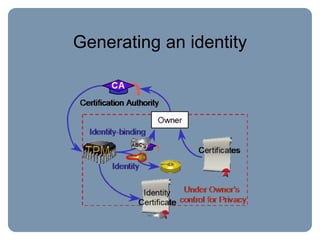
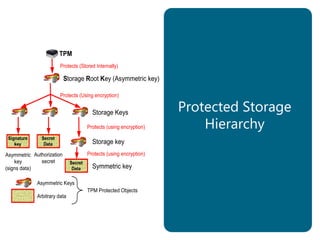
The document provides an overview of the Trusted Computing Platform Alliance (TCPA) and its technical specifications for trusted computing platforms. The TCPA aims to increase confidence in computing platforms through mechanisms like platform authentication, integrity reporting, and protected storage. This is achieved using a Trusted Platform Module (TPM) that acts as the root of trust and can reliably report the platform's software state. The TPM specifications define how platforms can prove their identity and properties to other entities while protecting users' privacy.