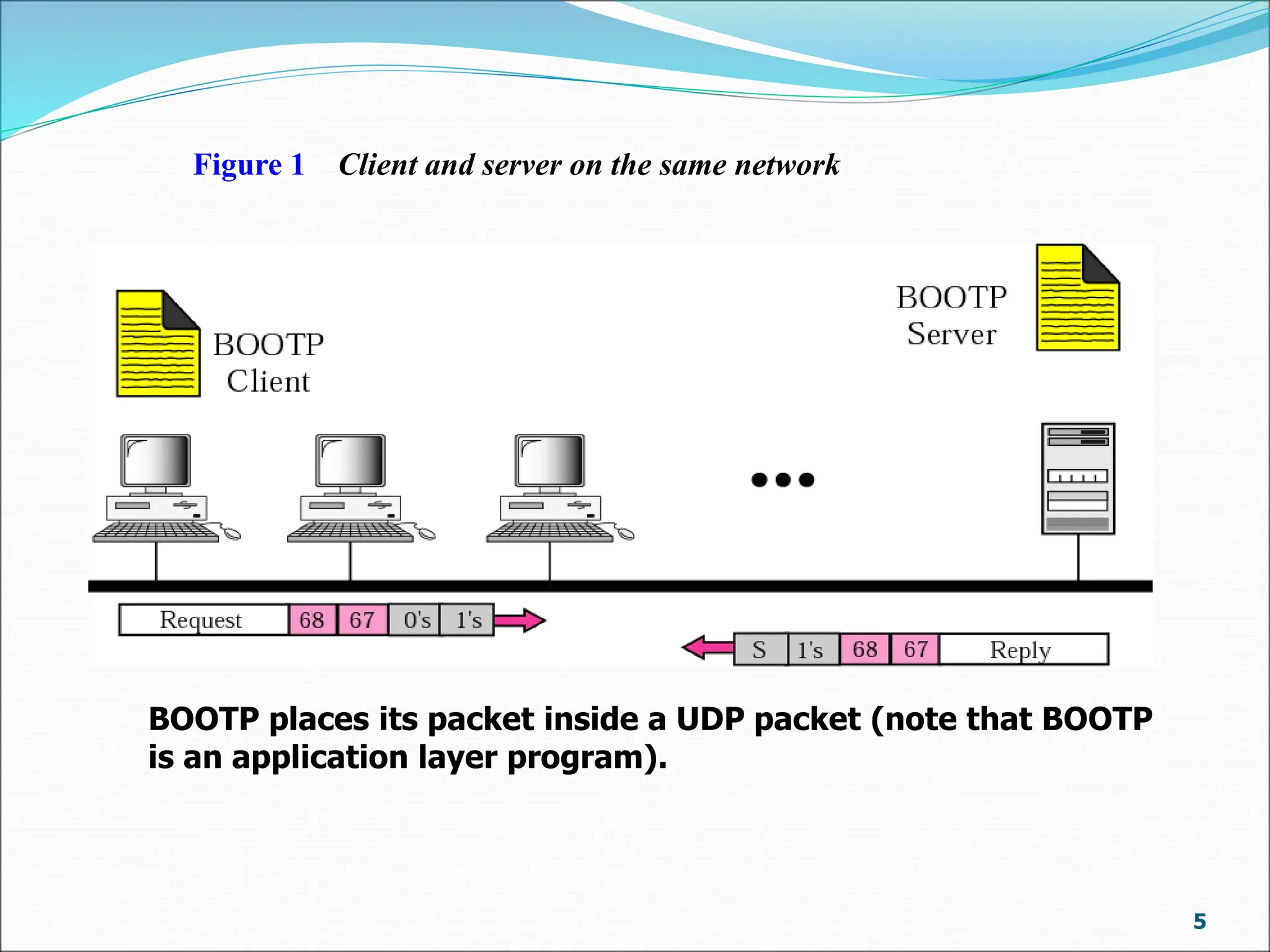
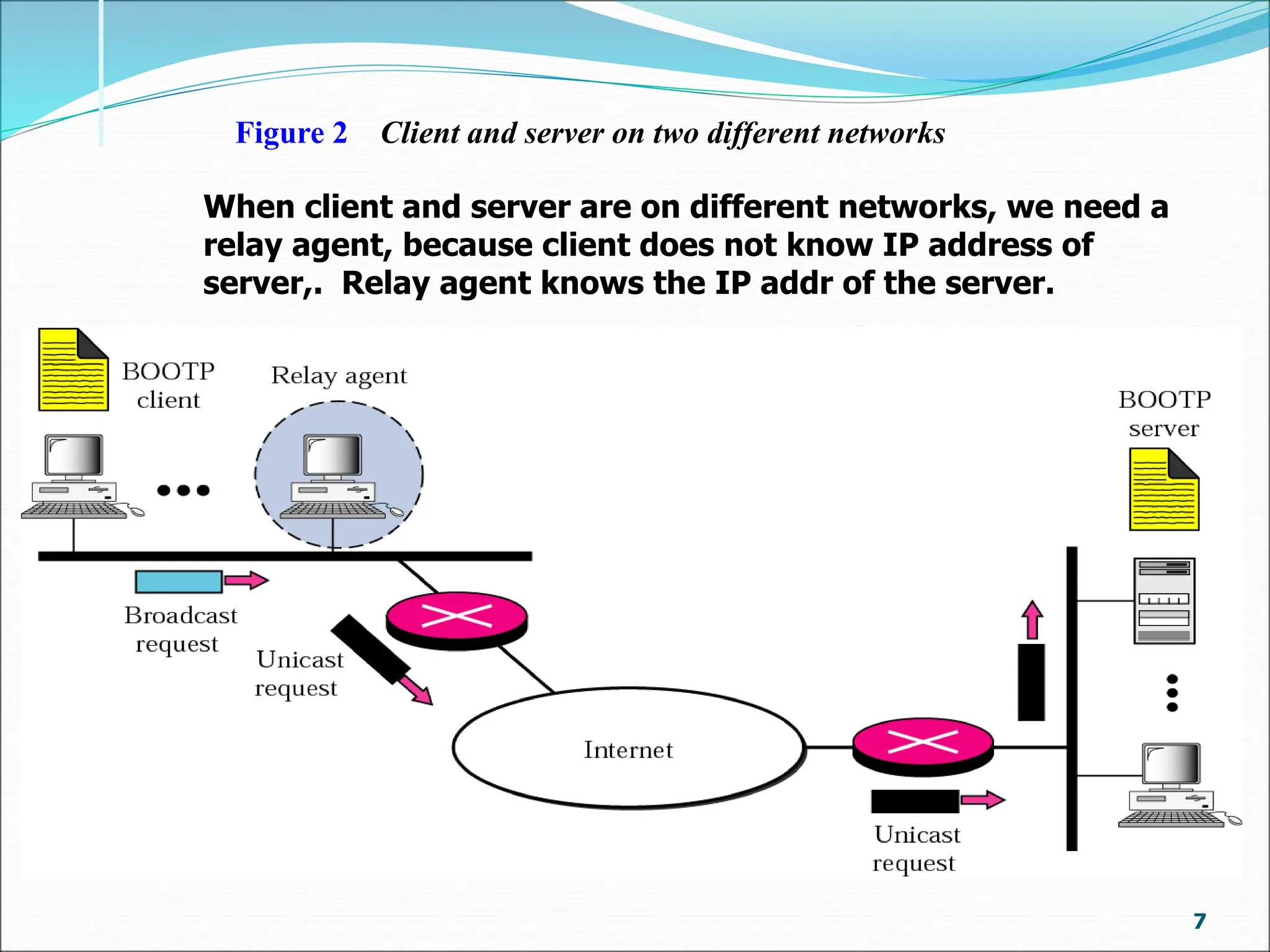
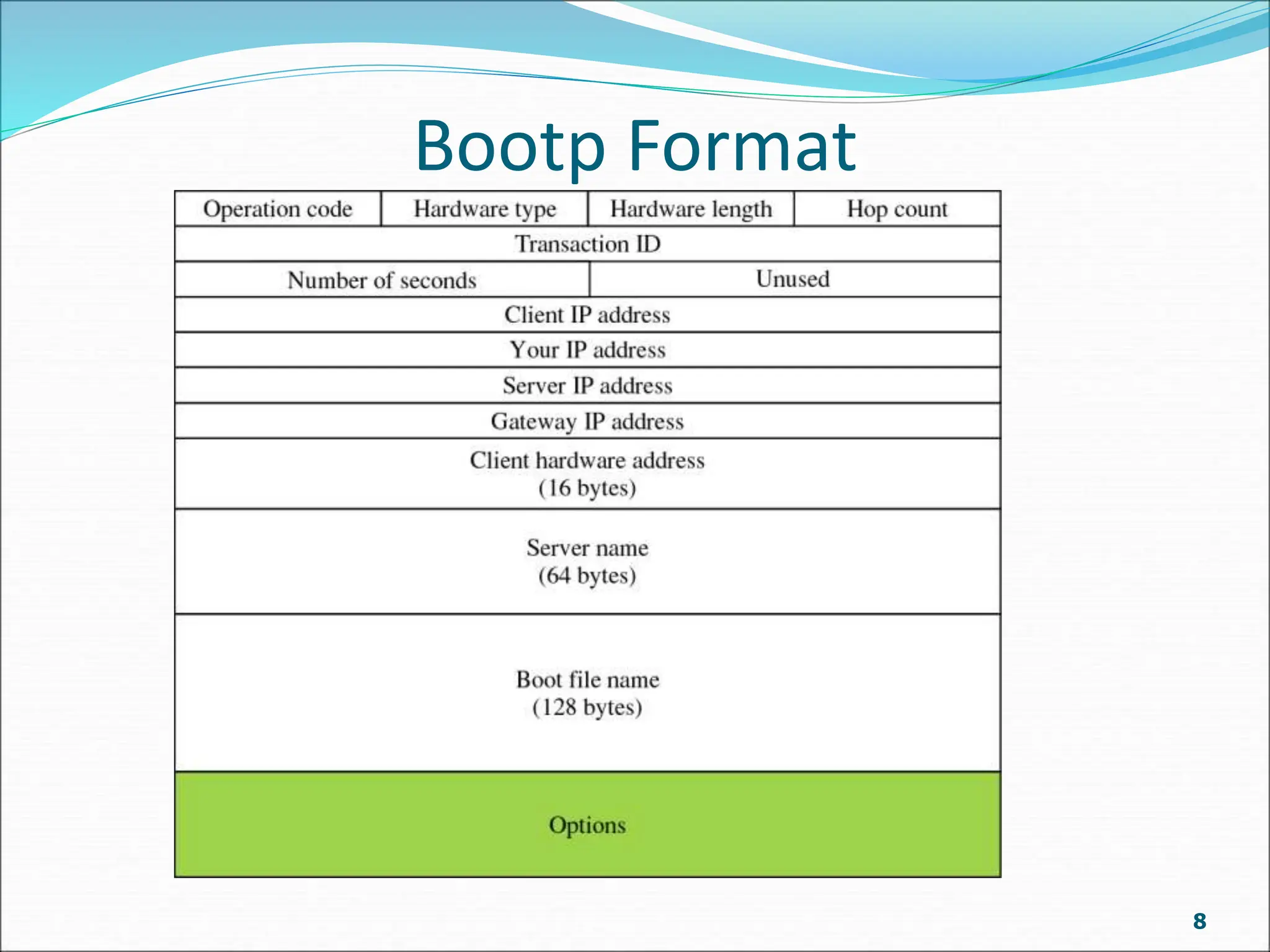
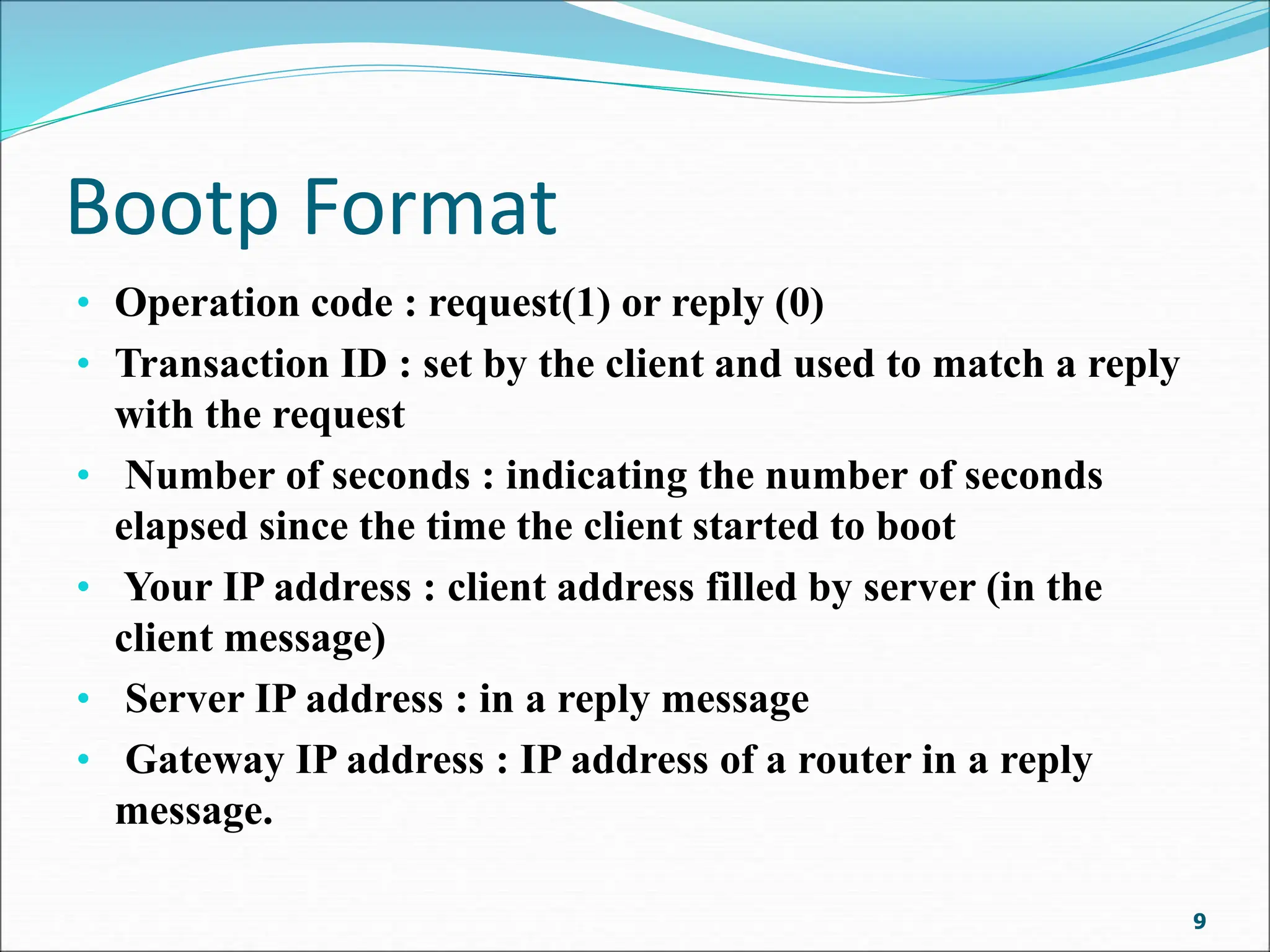
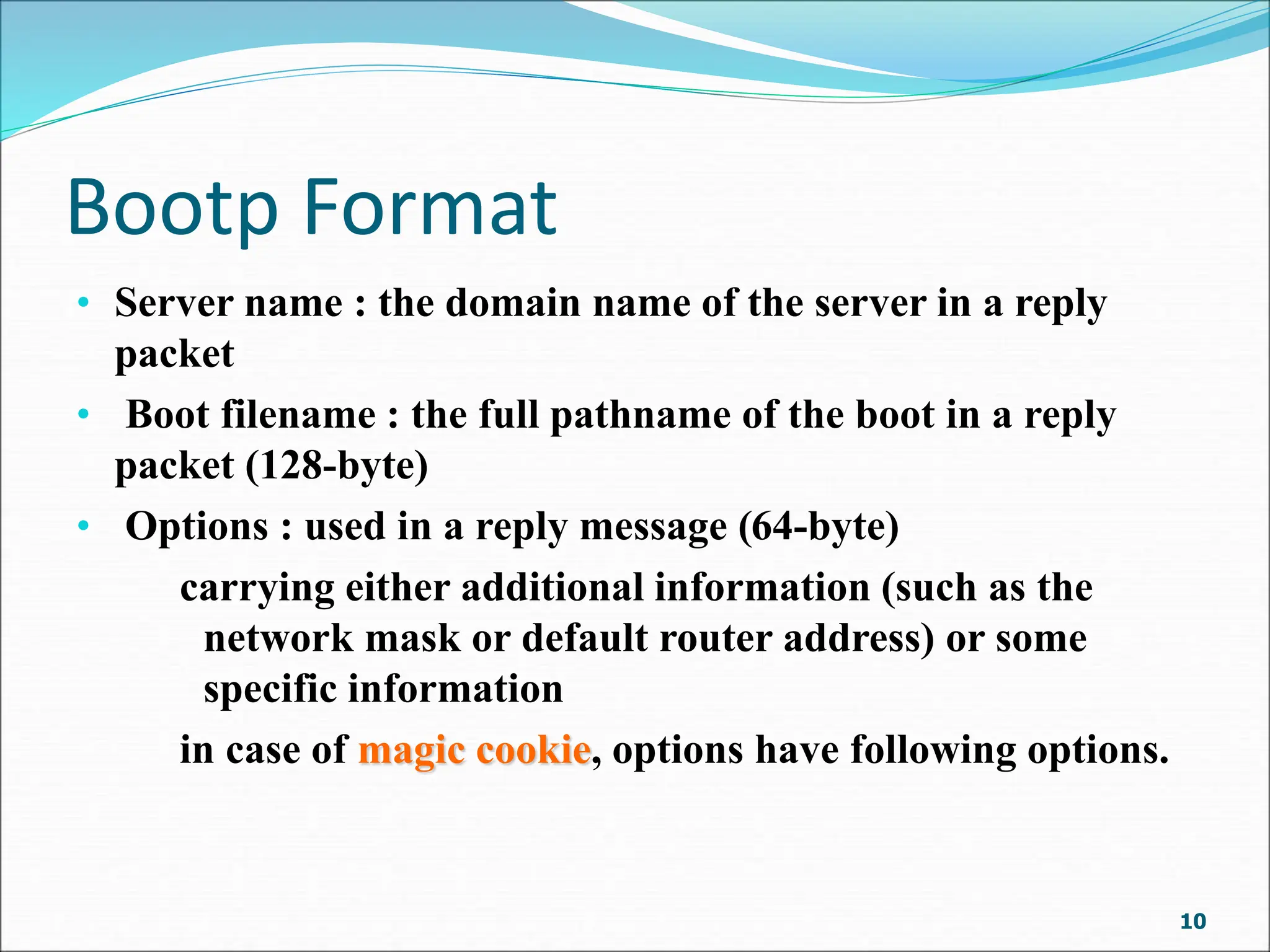
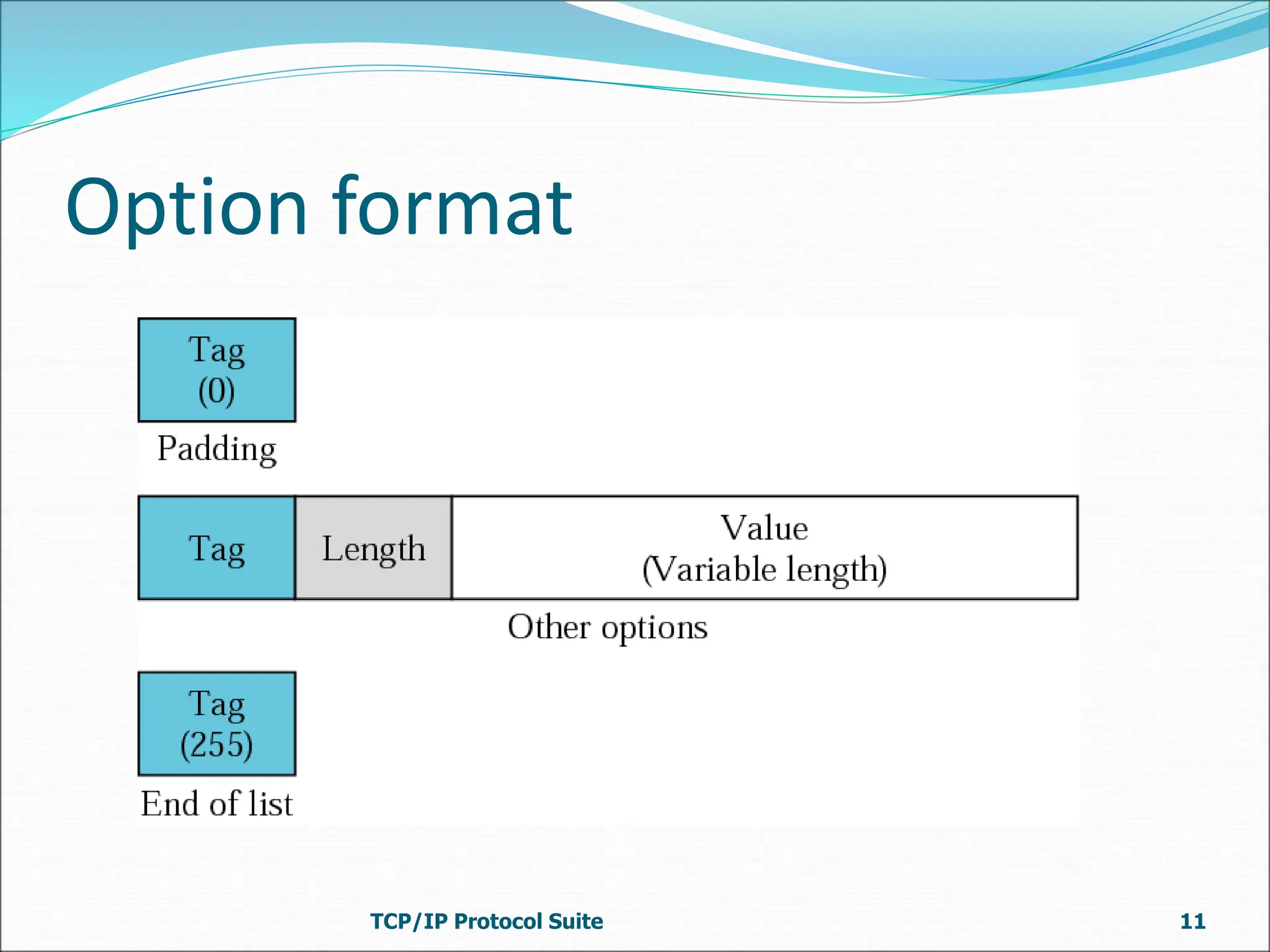
Bootp is a client-server protocol that provides TCP/IP configuration information to diskless or newly booted computers. It allows a client computer to retrieve its IP address, subnet mask, default gateway, and name server address from a Bootp server. When a client requests this information, the Bootp server responds with a fixed configuration from its table. The Bootp protocol uses UDP with the client on port 68 and server on port 67. It supports broadcasting for multiple clients on the same network or using a relay agent for clients on different networks from the server. The Bootp packet format includes fields for operation code, transaction ID, time elapsed, client/server IP addresses, boot file name, and options.