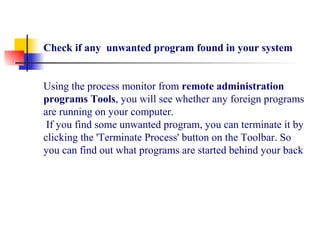
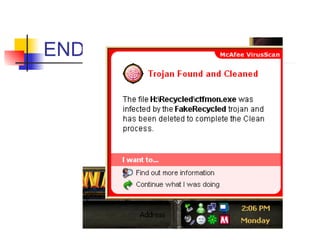
This document discusses Trojan horse programs and remote administration tools. It defines Trojan horses as programs that appear harmless but have malicious code. Trojan horses can give intruders access to computers by installing backdoors. Remote administration tools also allow unauthorized access and control of victim's computers. The document provides examples of common Trojan horses and remote access programs like Back Orifice and describes how to detect and remove such threats.





















![Actions:
Remote Access / AOL Trojan
Can register under 40 different HKEYs.
Versions:
1.0, 1.1, 2.0, 2.1, 5.3,
Registers:
HLMSOFTWAREMicrosoftWindowsCurrentVersionRun
HLMSOFTWAREMicrosoftWindowsCurrentVersion RunServices
and some 38 other entries !!!
Notes:
Works on Windows 95, 98, ME and Unix [Linux and FreeBSD]. RAT
server 1.1 has IRC support added. Send.tgz is Unix client. ˆ Source code
is available.
Country:
N/A
Program:
Written in Visual Basic 5.](https://image.slidesharecdn.com/trojanbackdoors-130505035019-phpapp01/85/Trojan-backdoors-25-320.jpg)