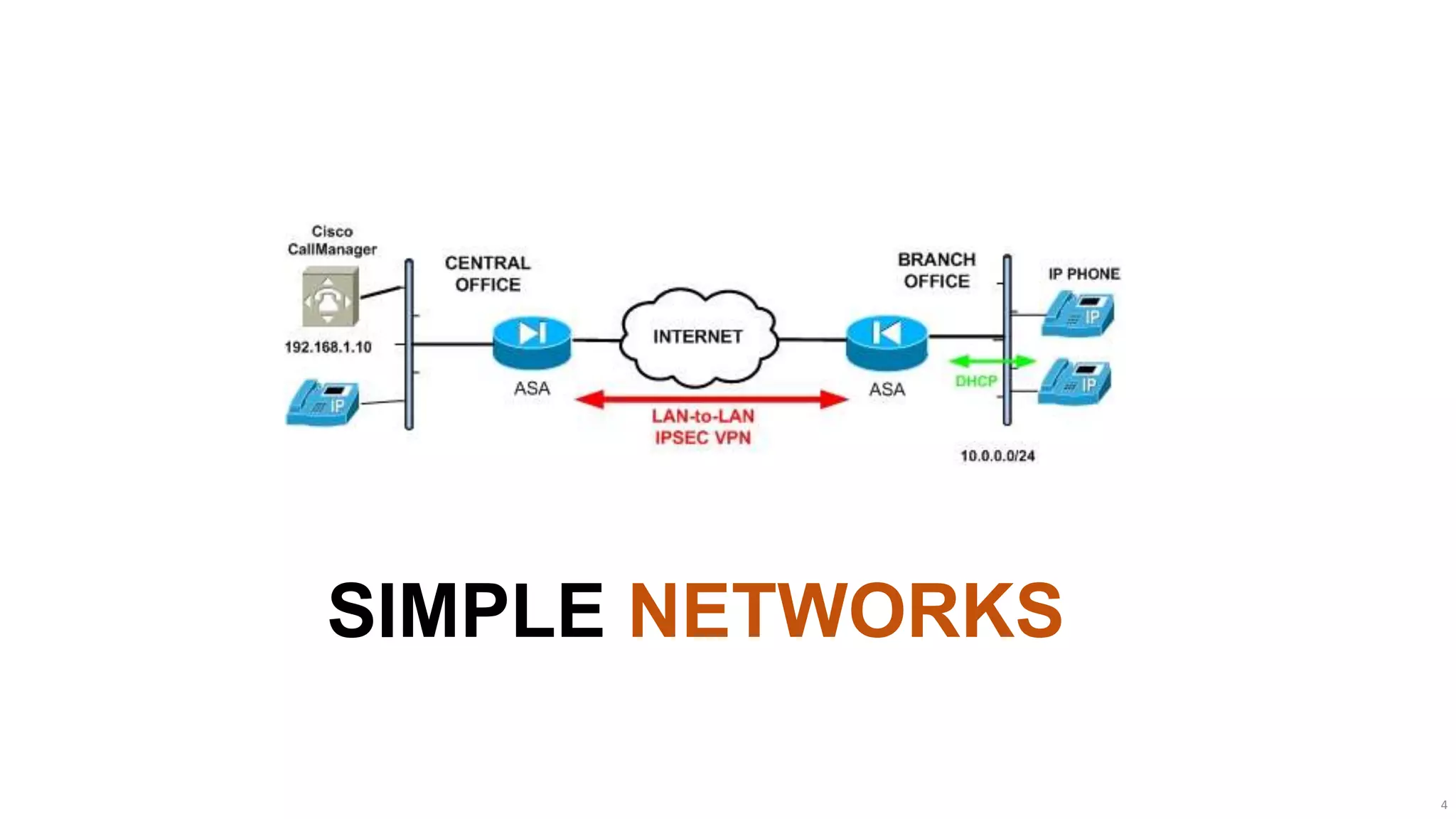
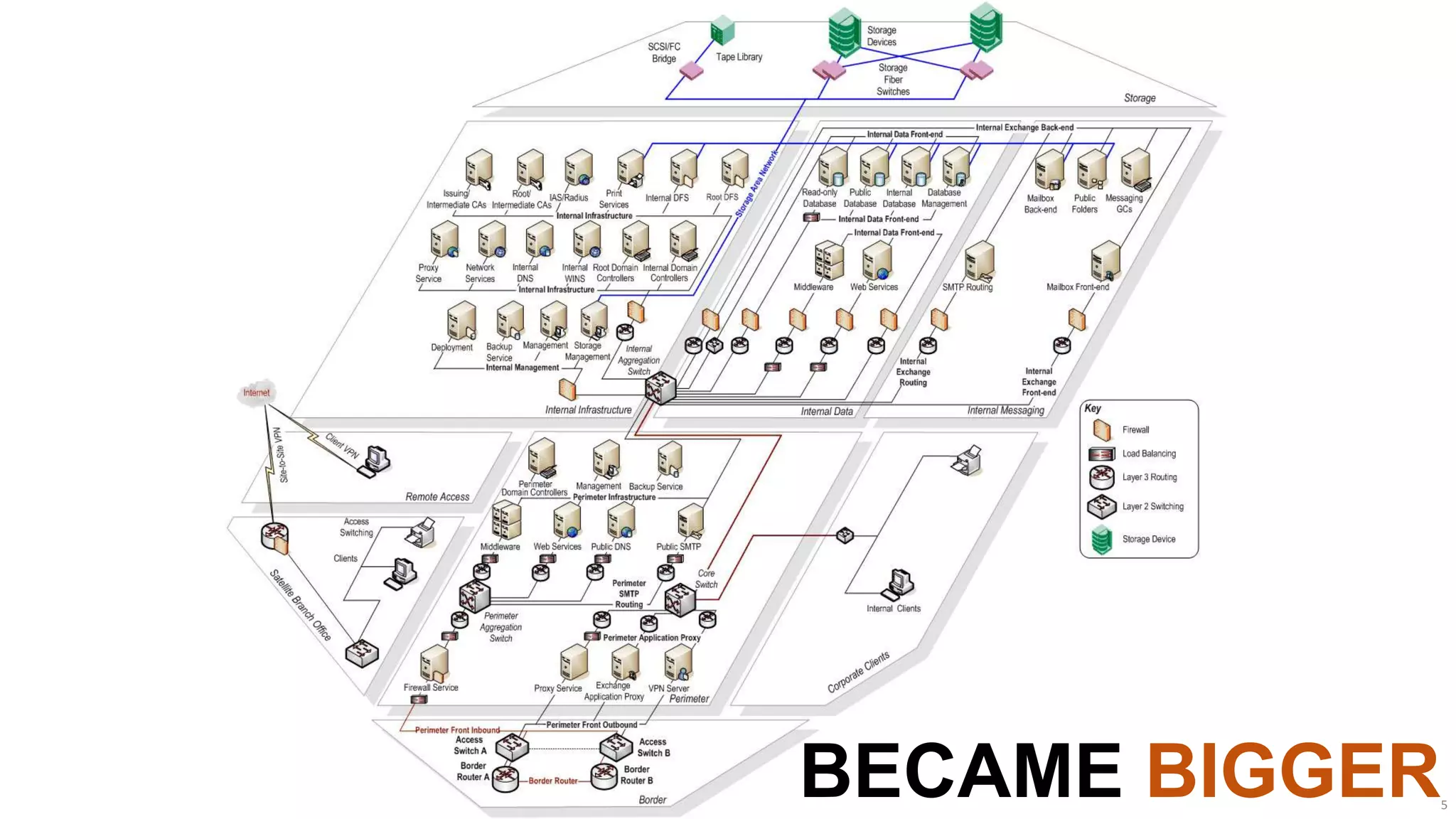
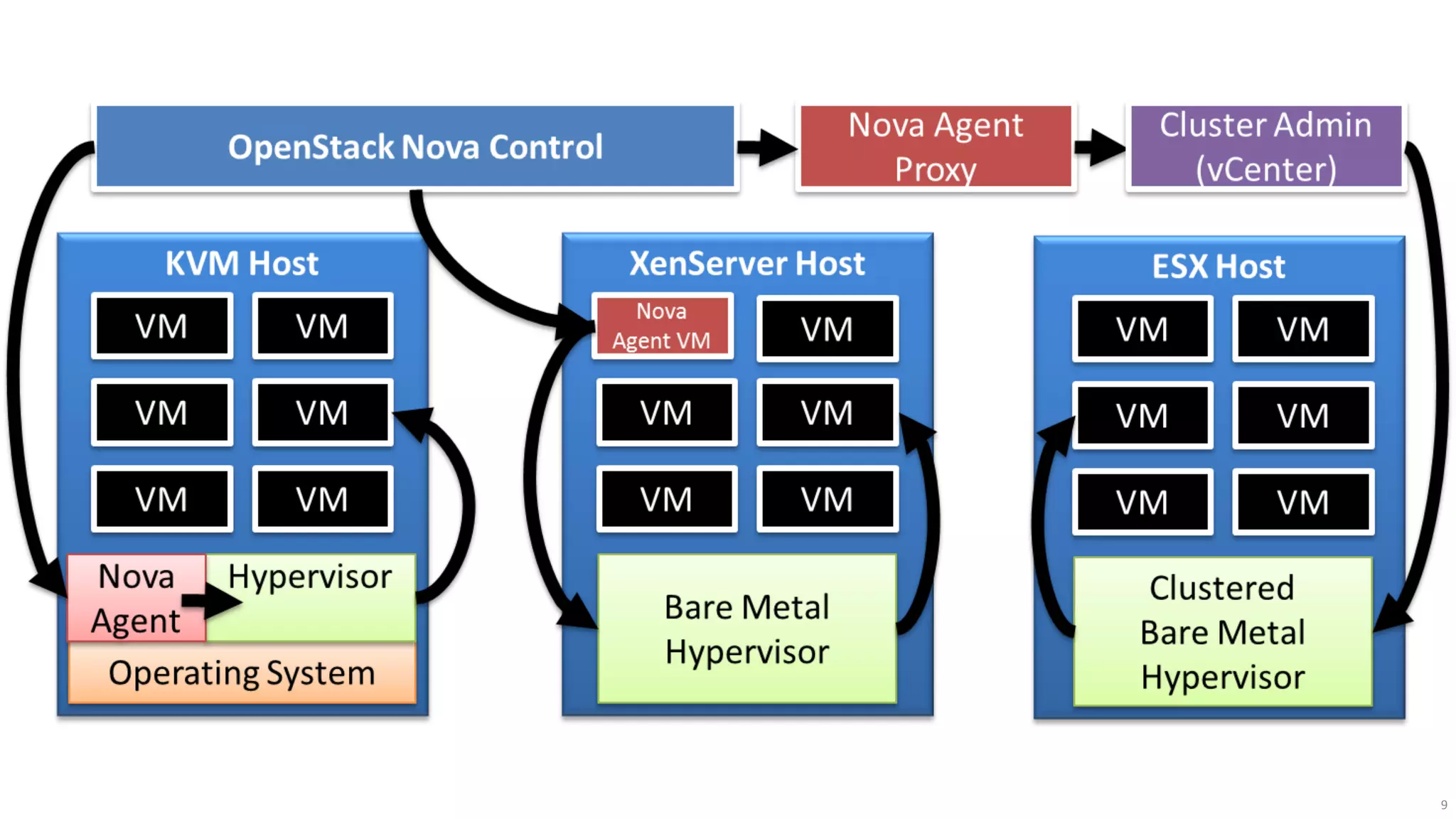
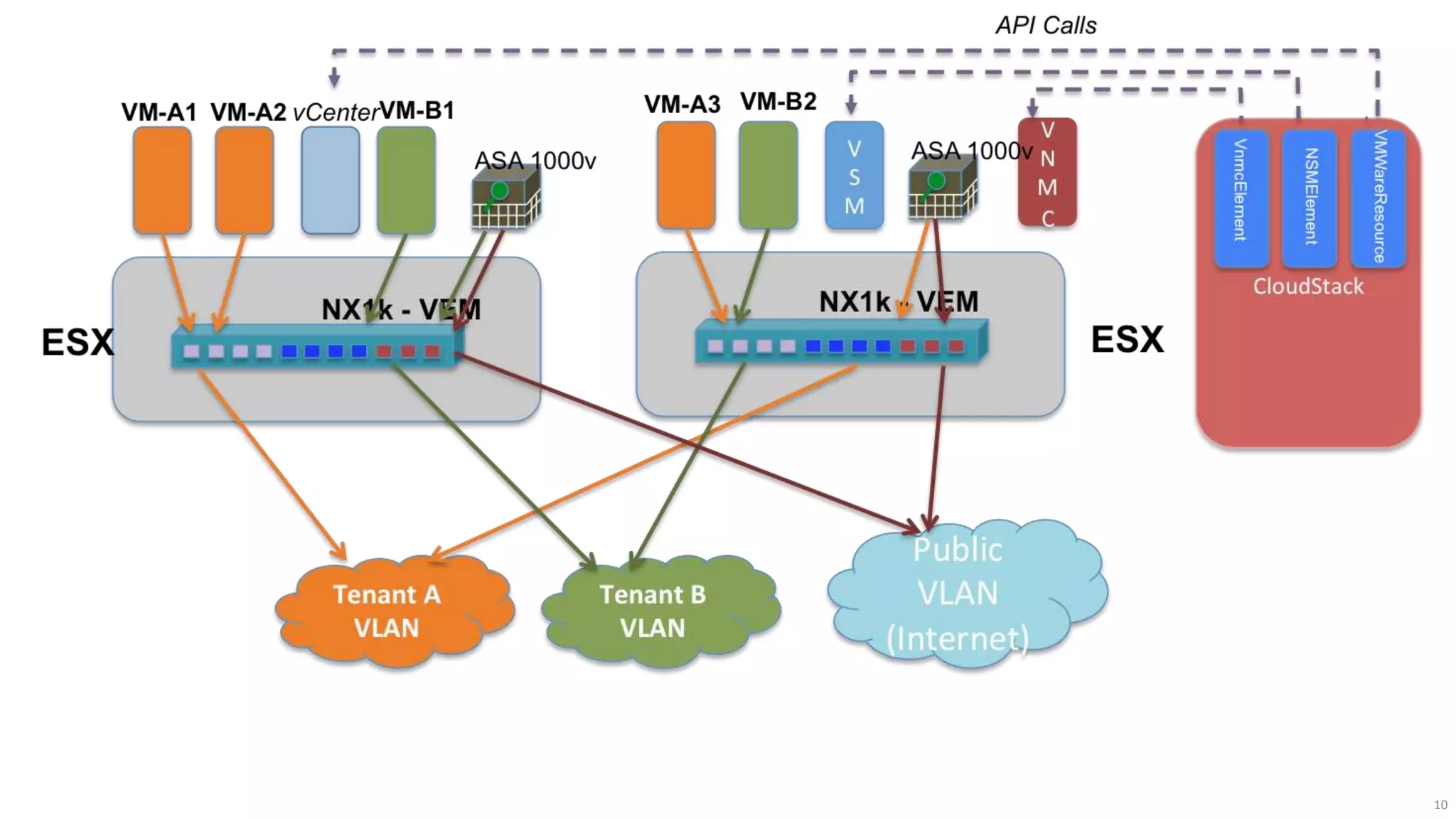
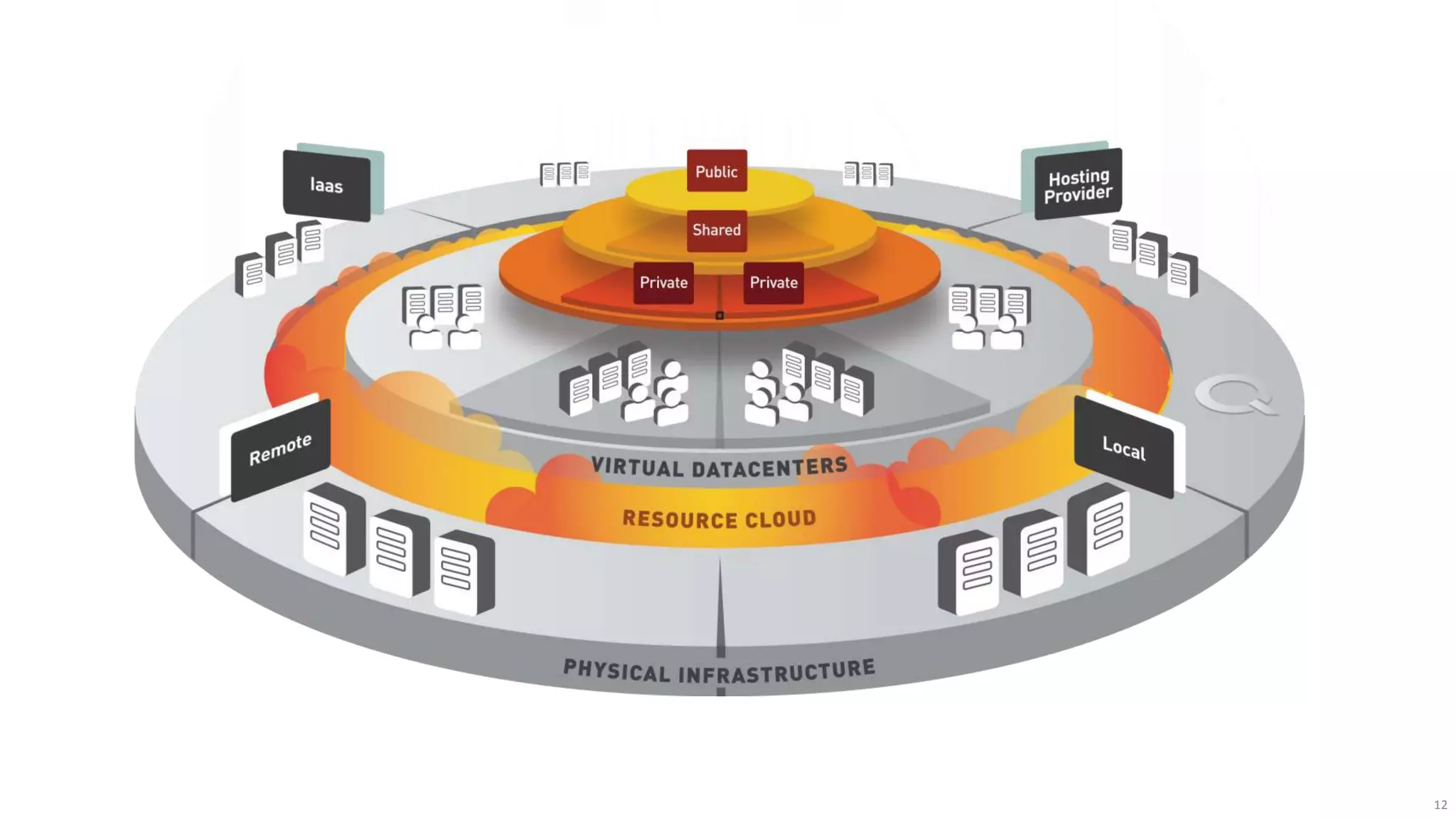
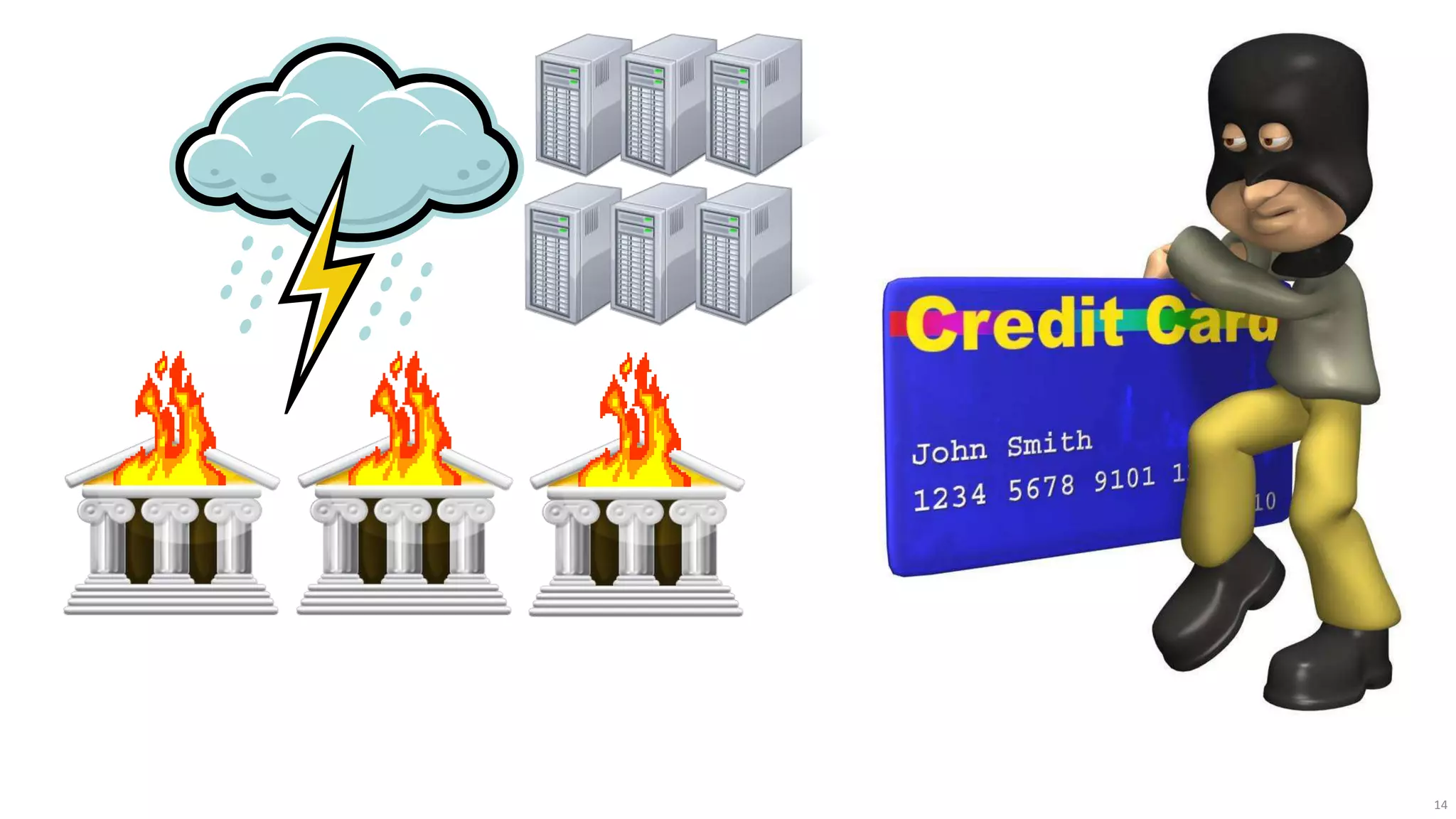
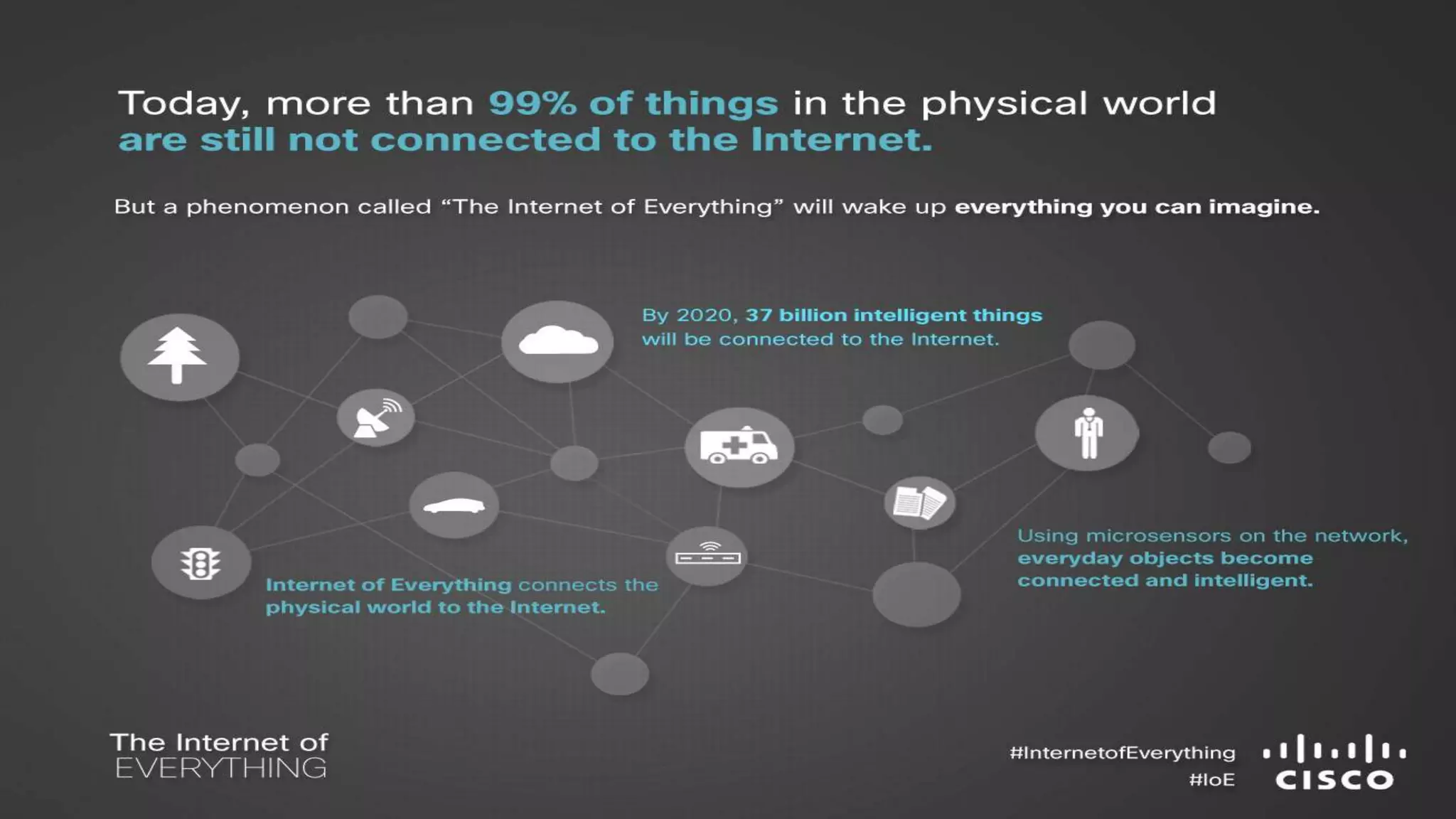
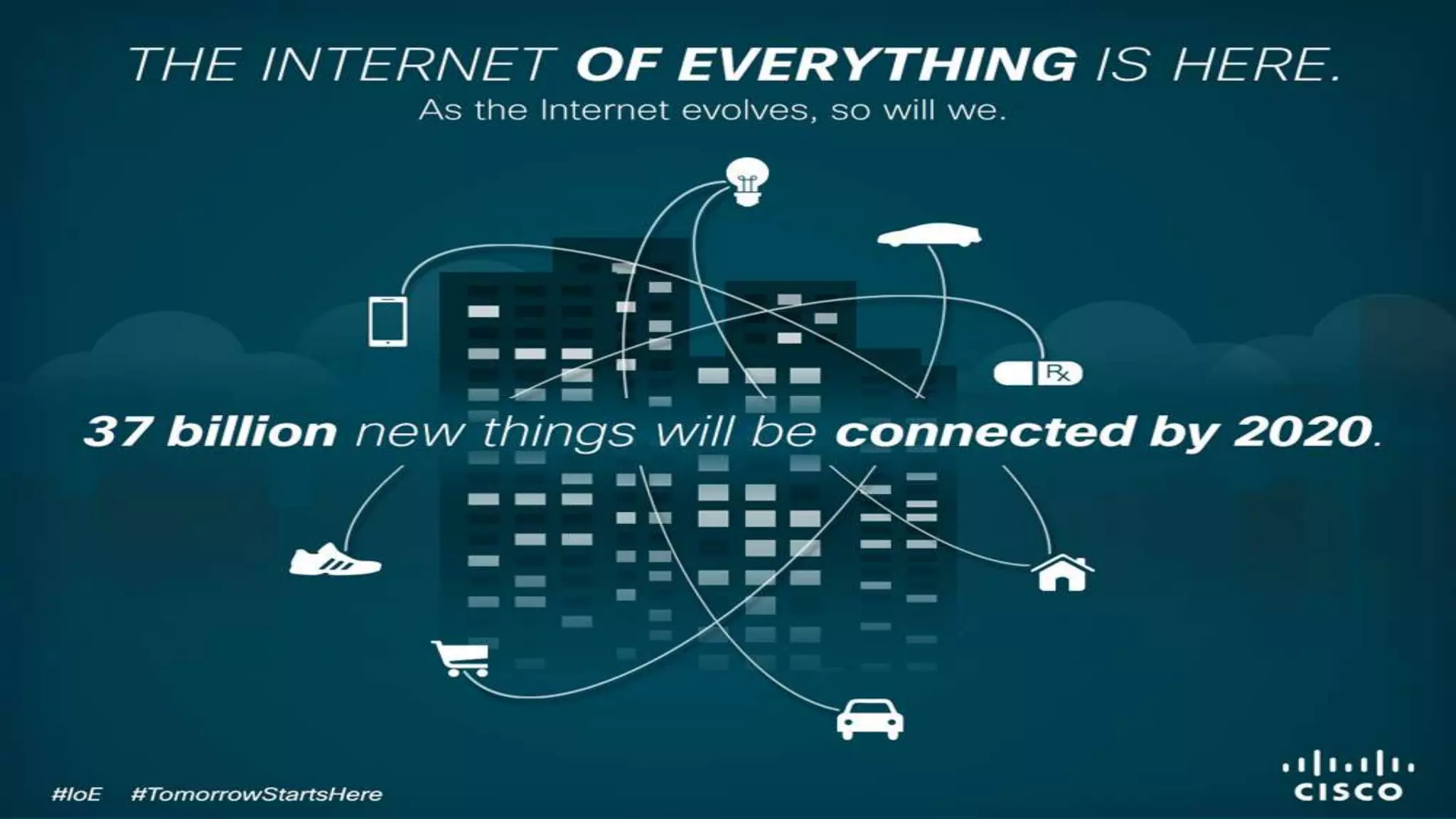
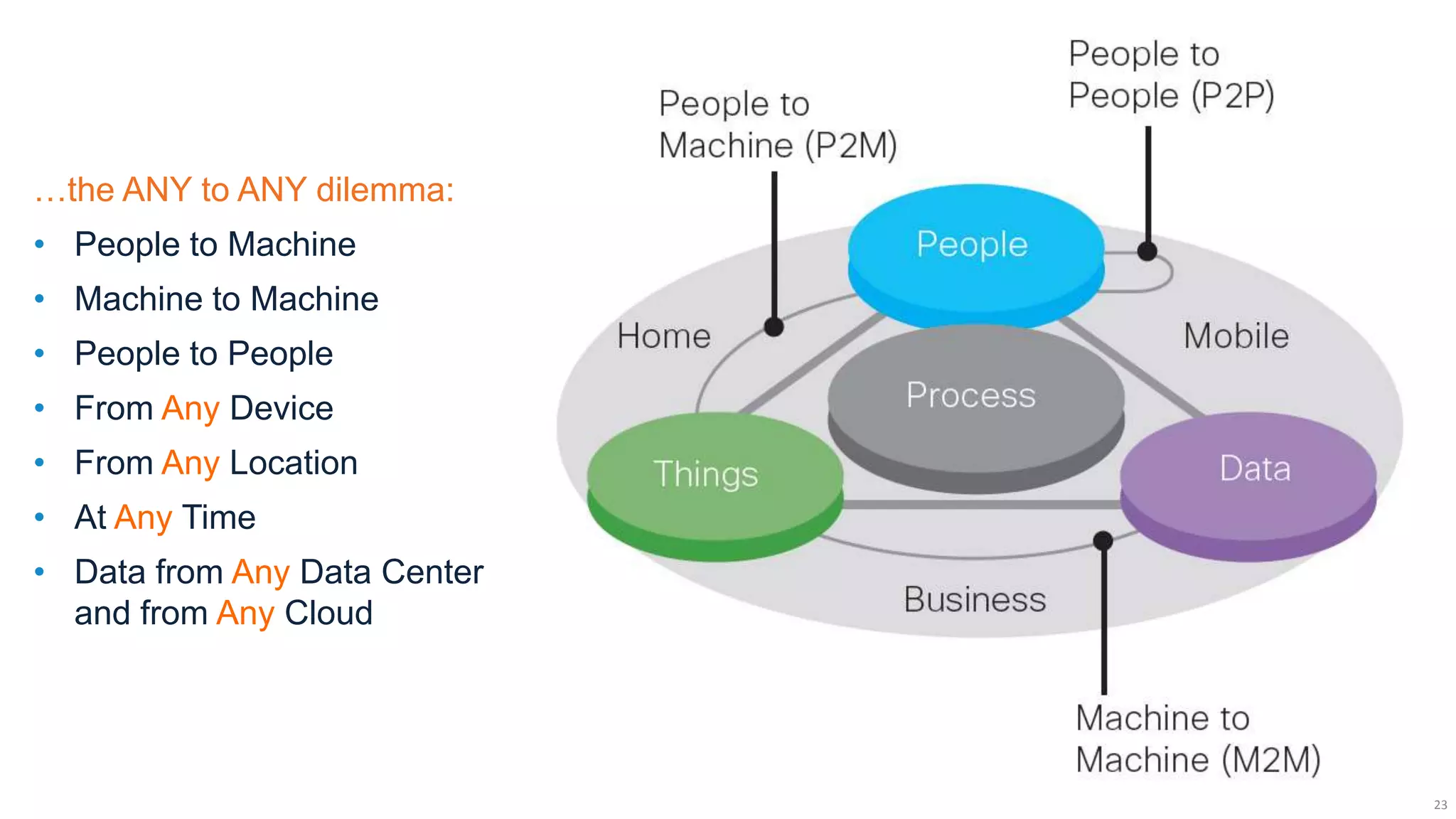
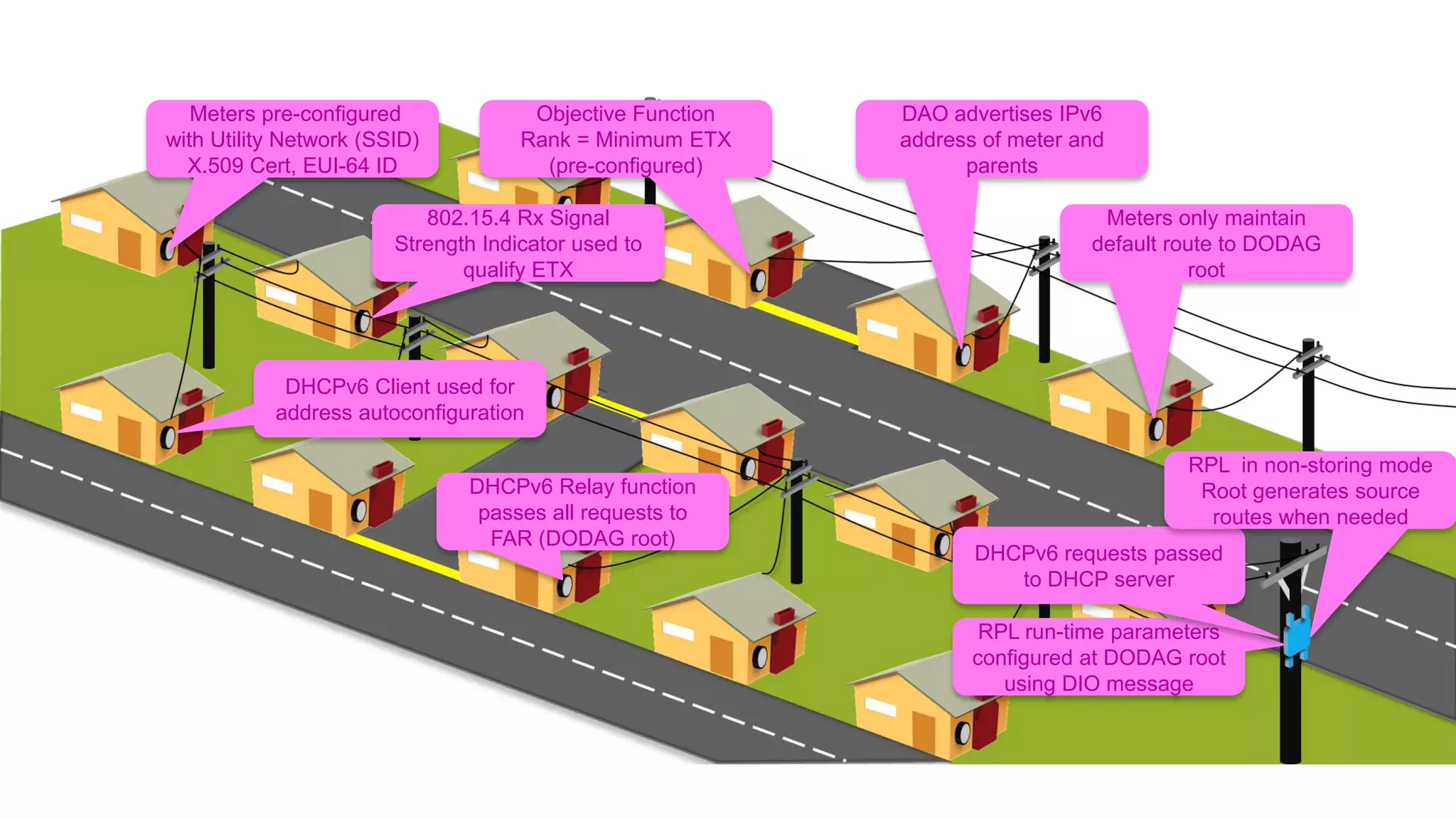
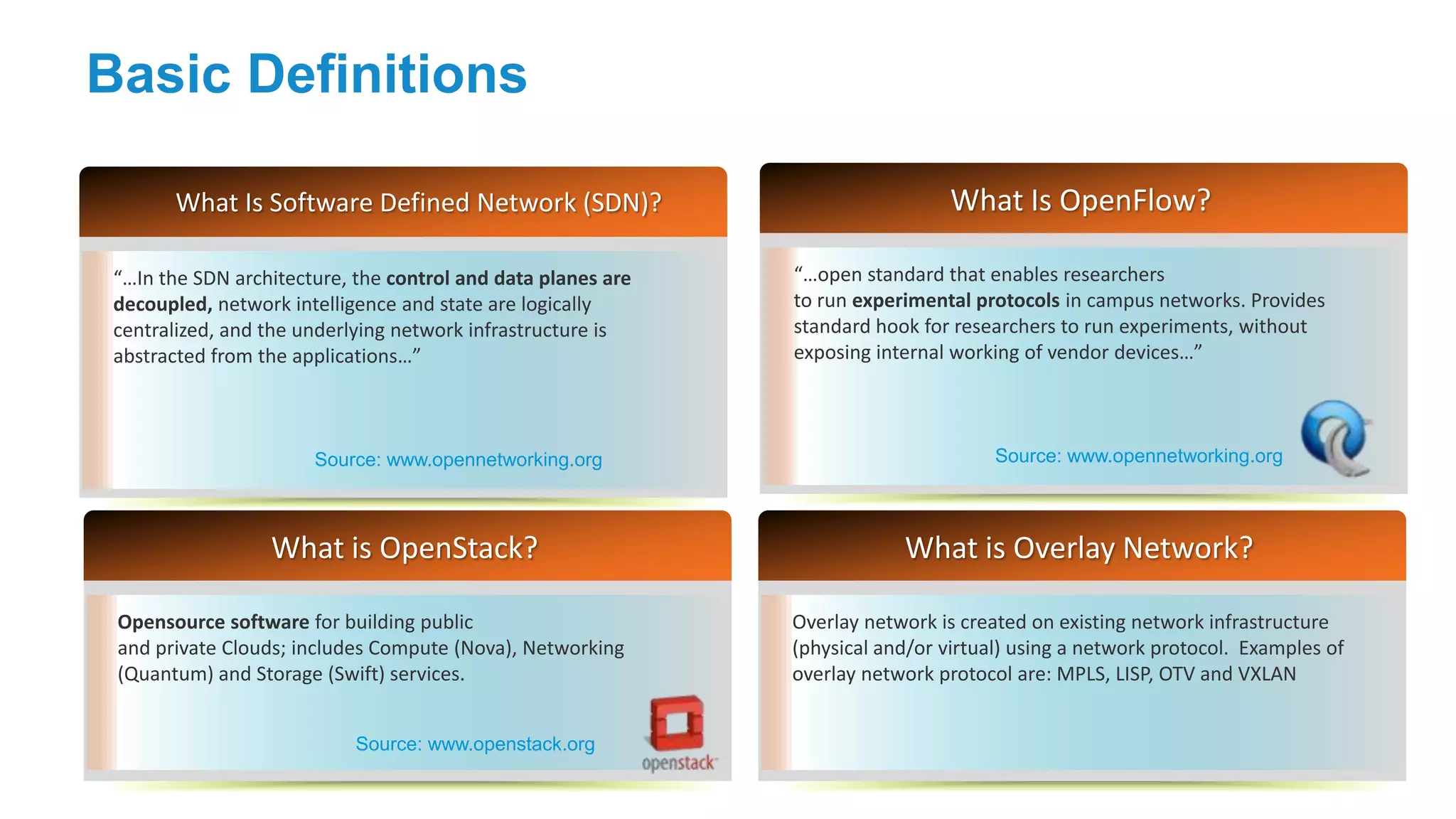
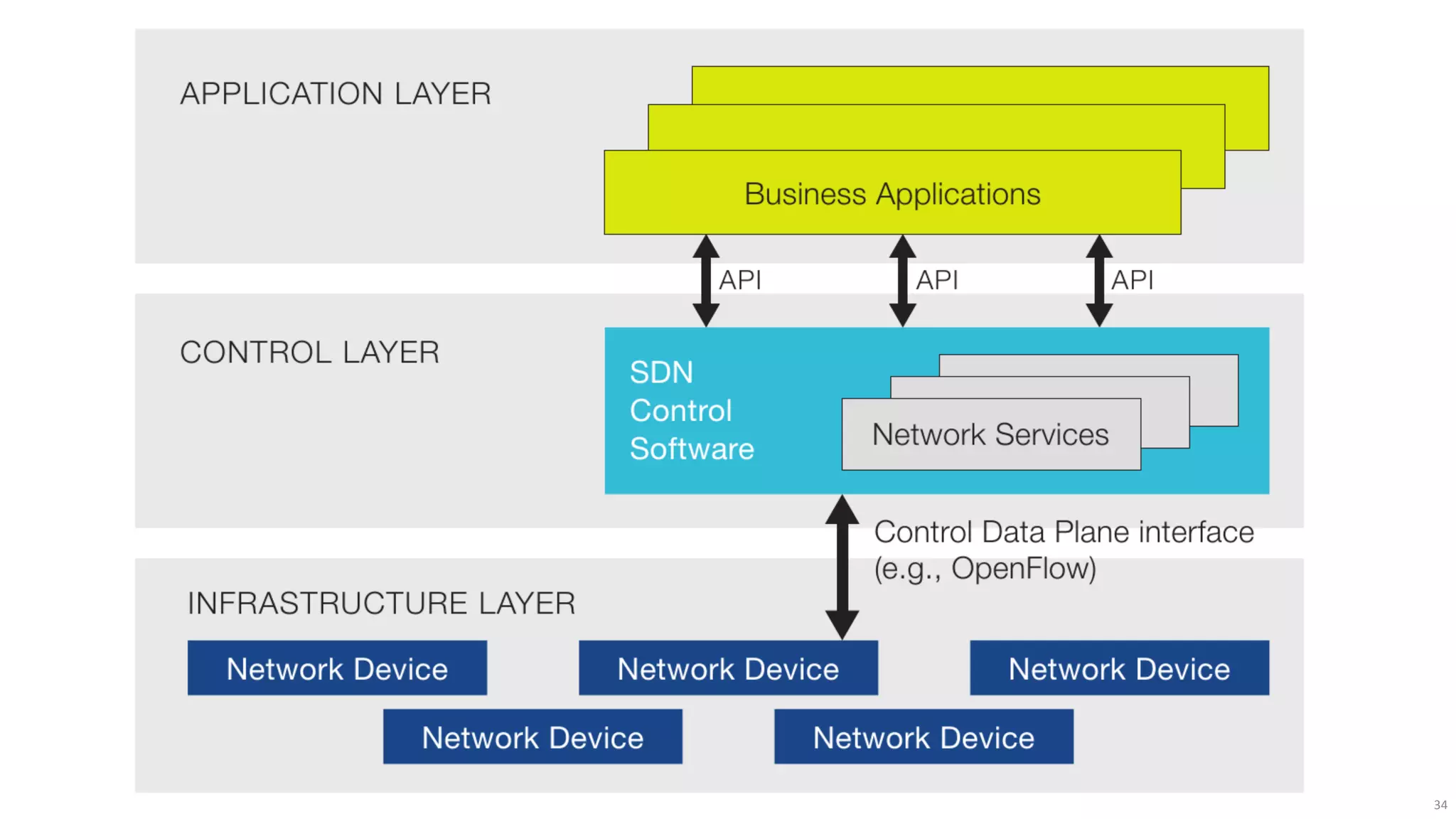
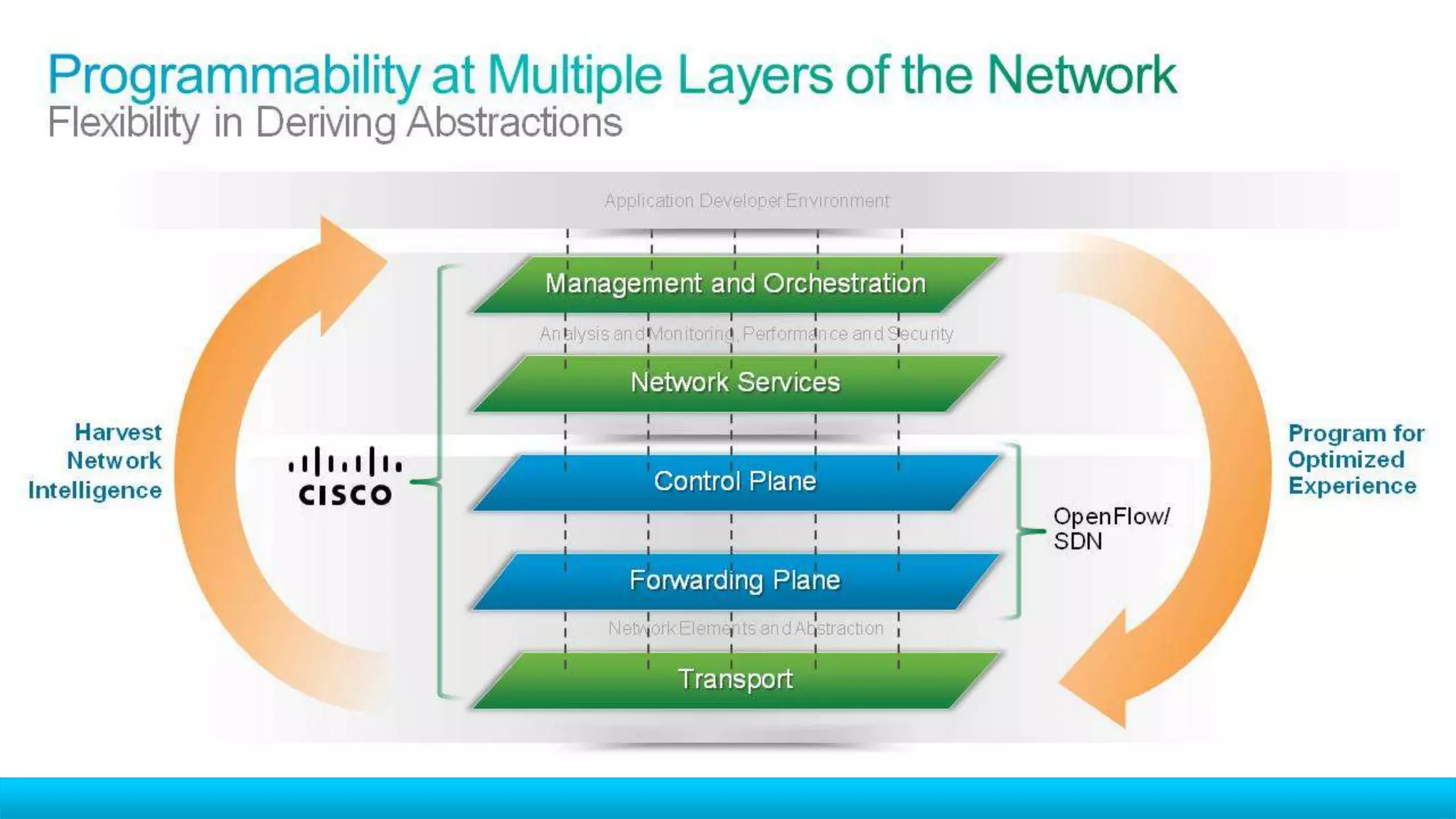
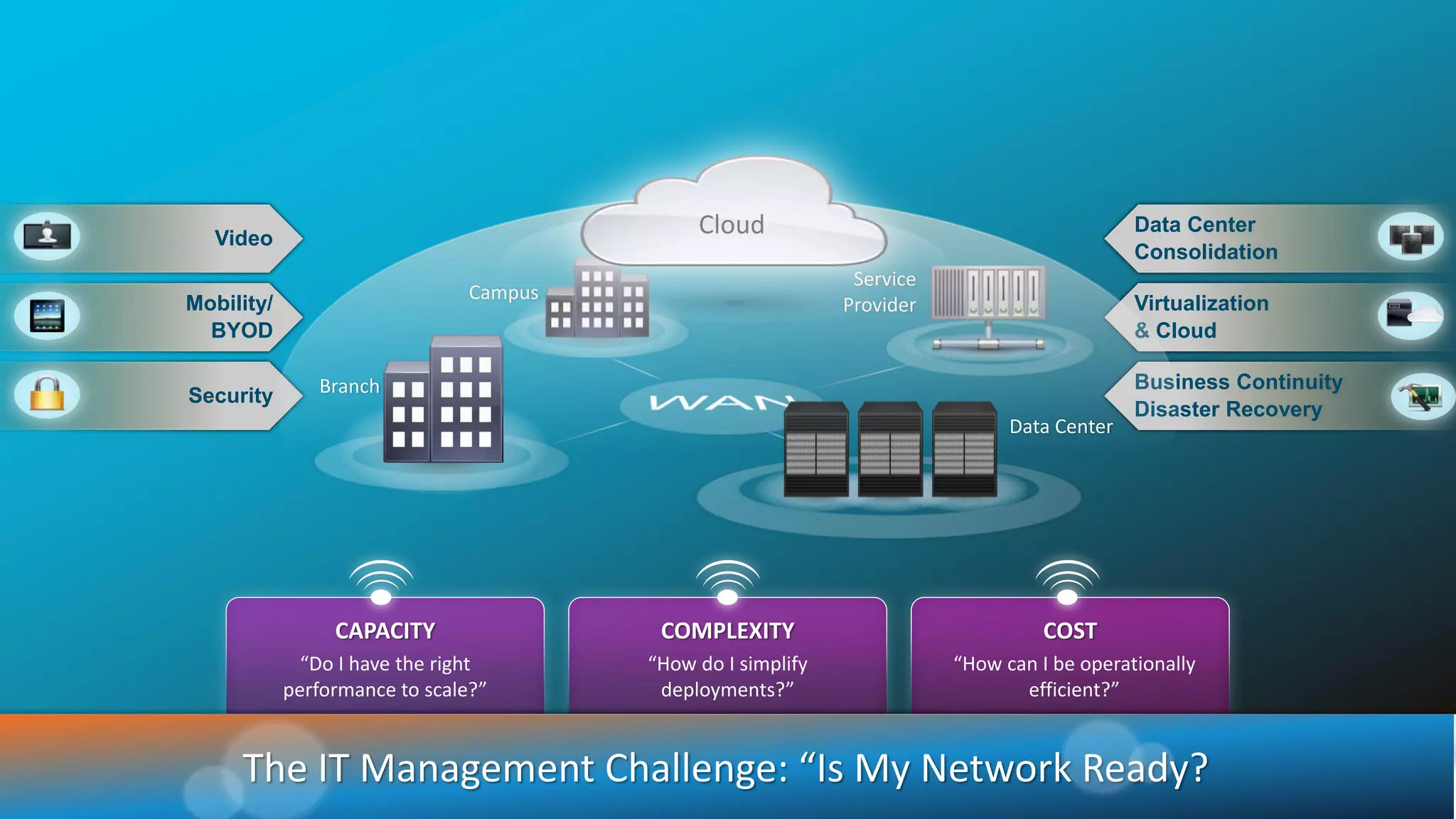
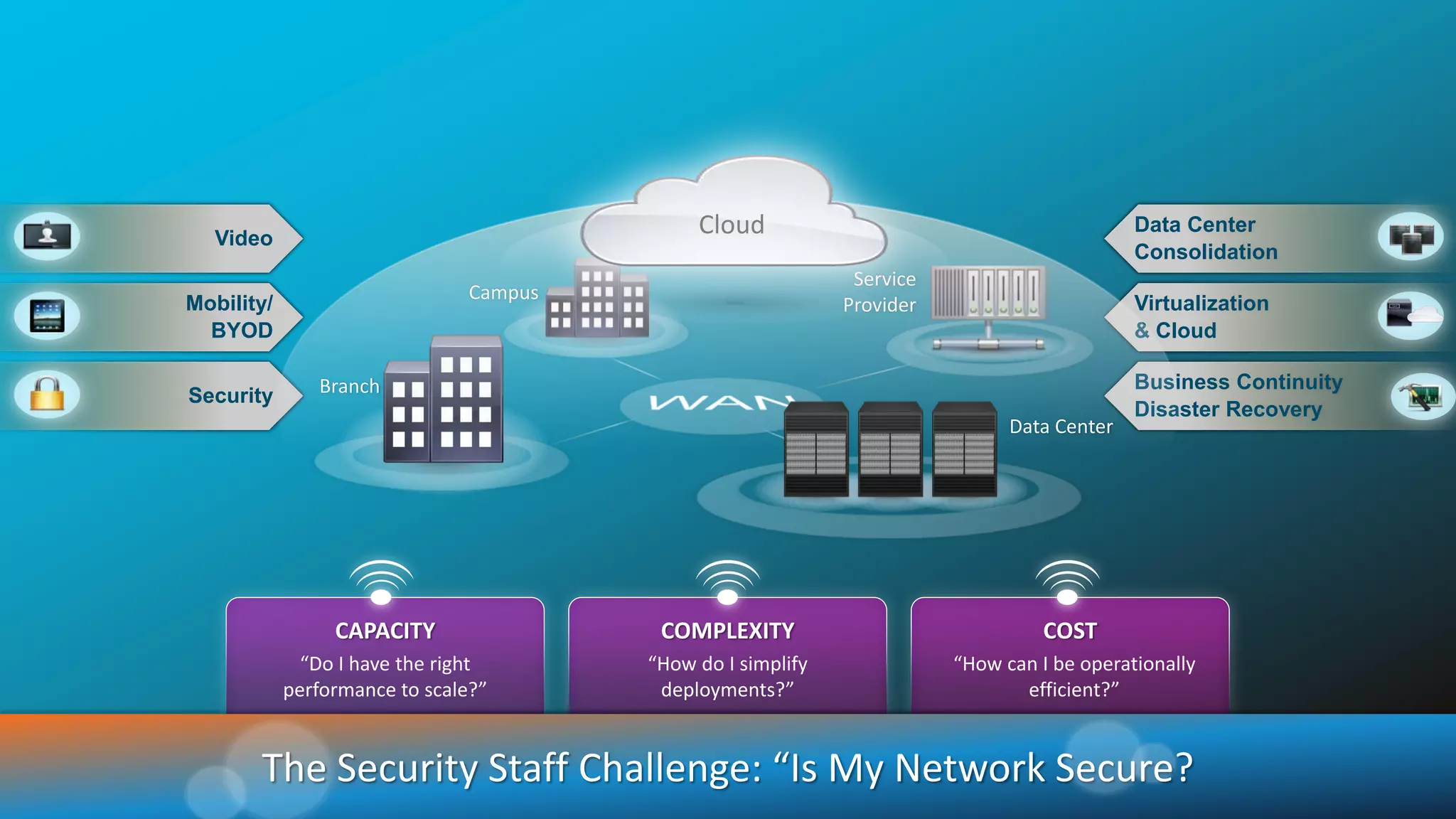
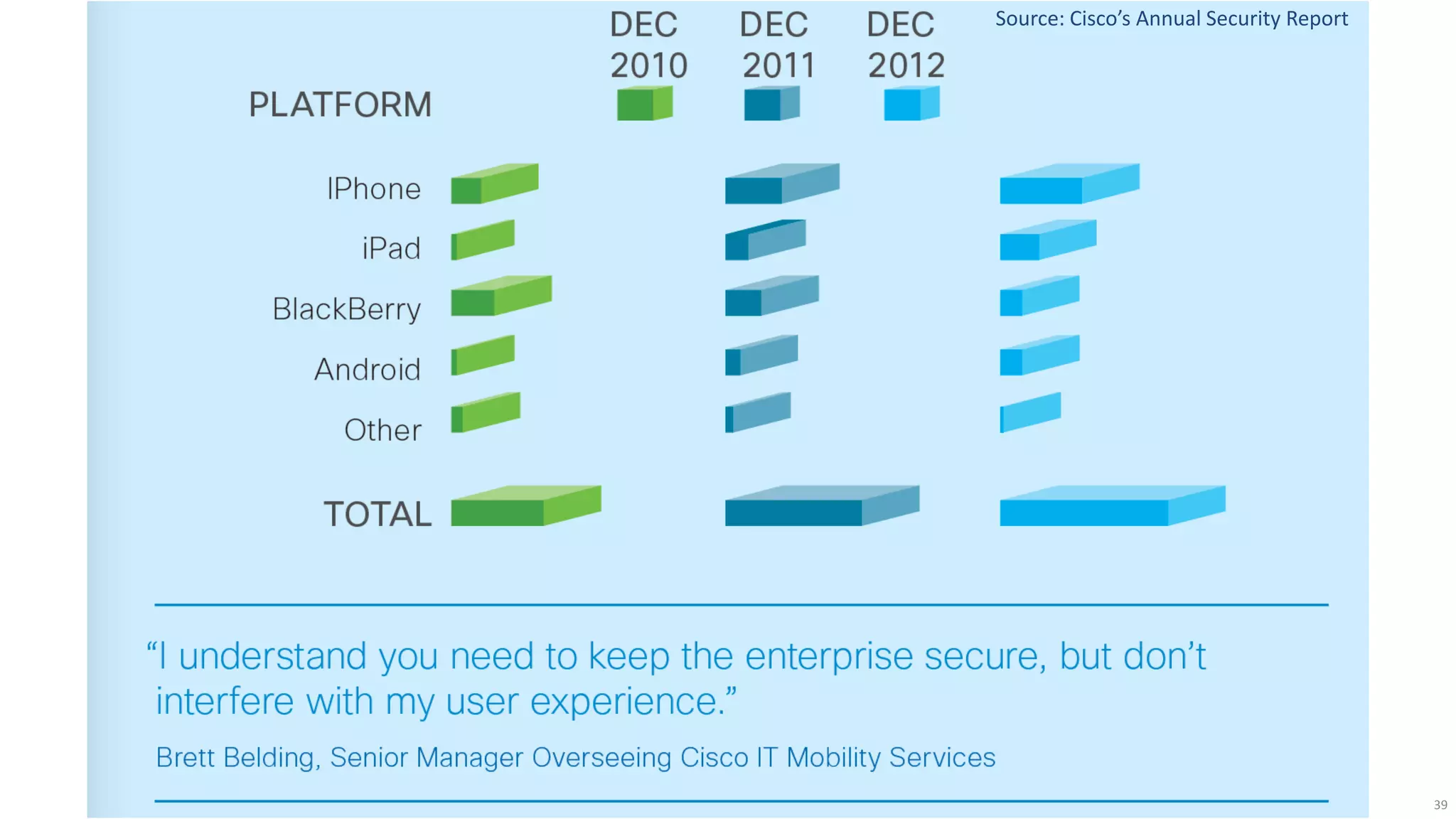
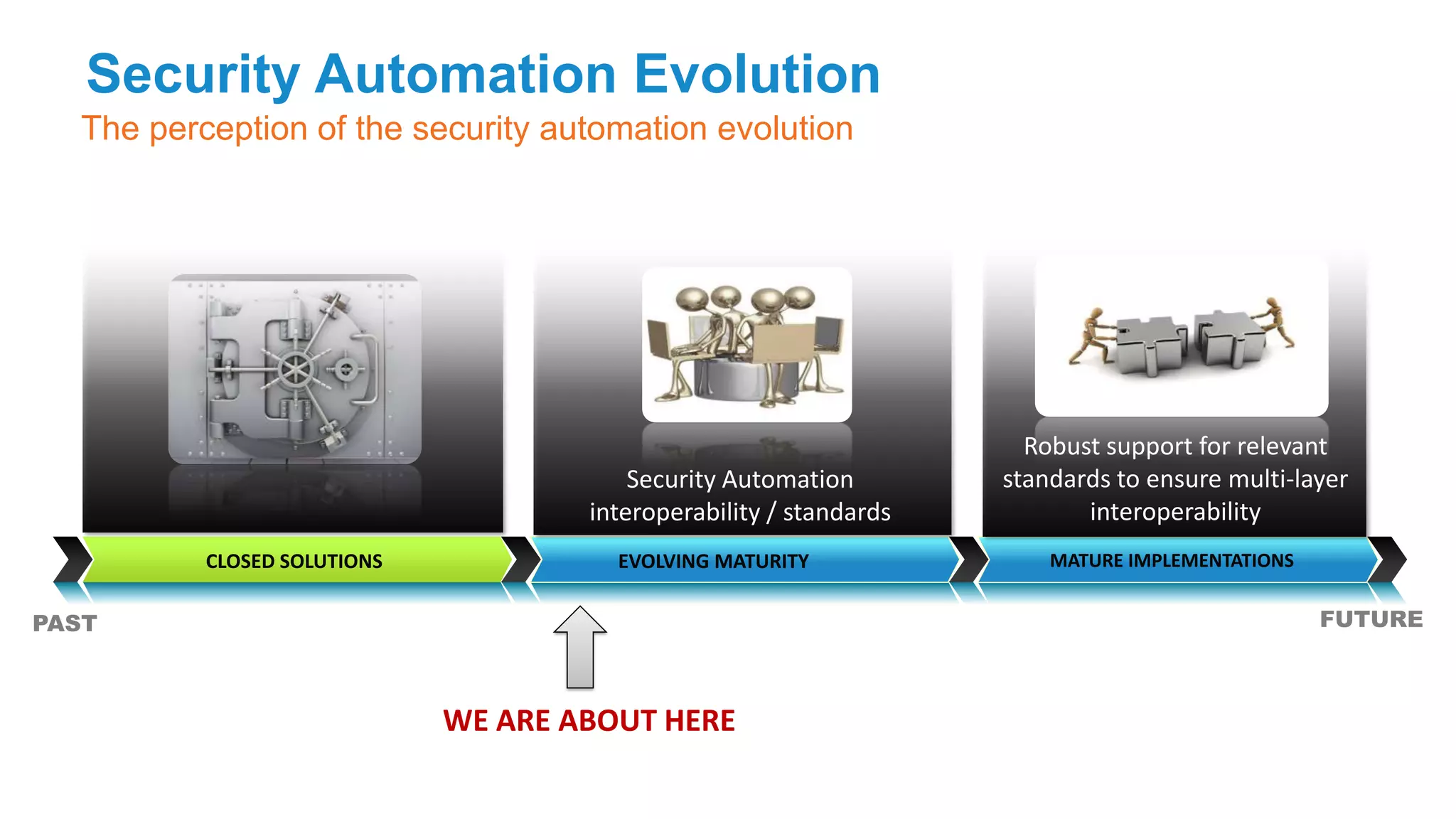
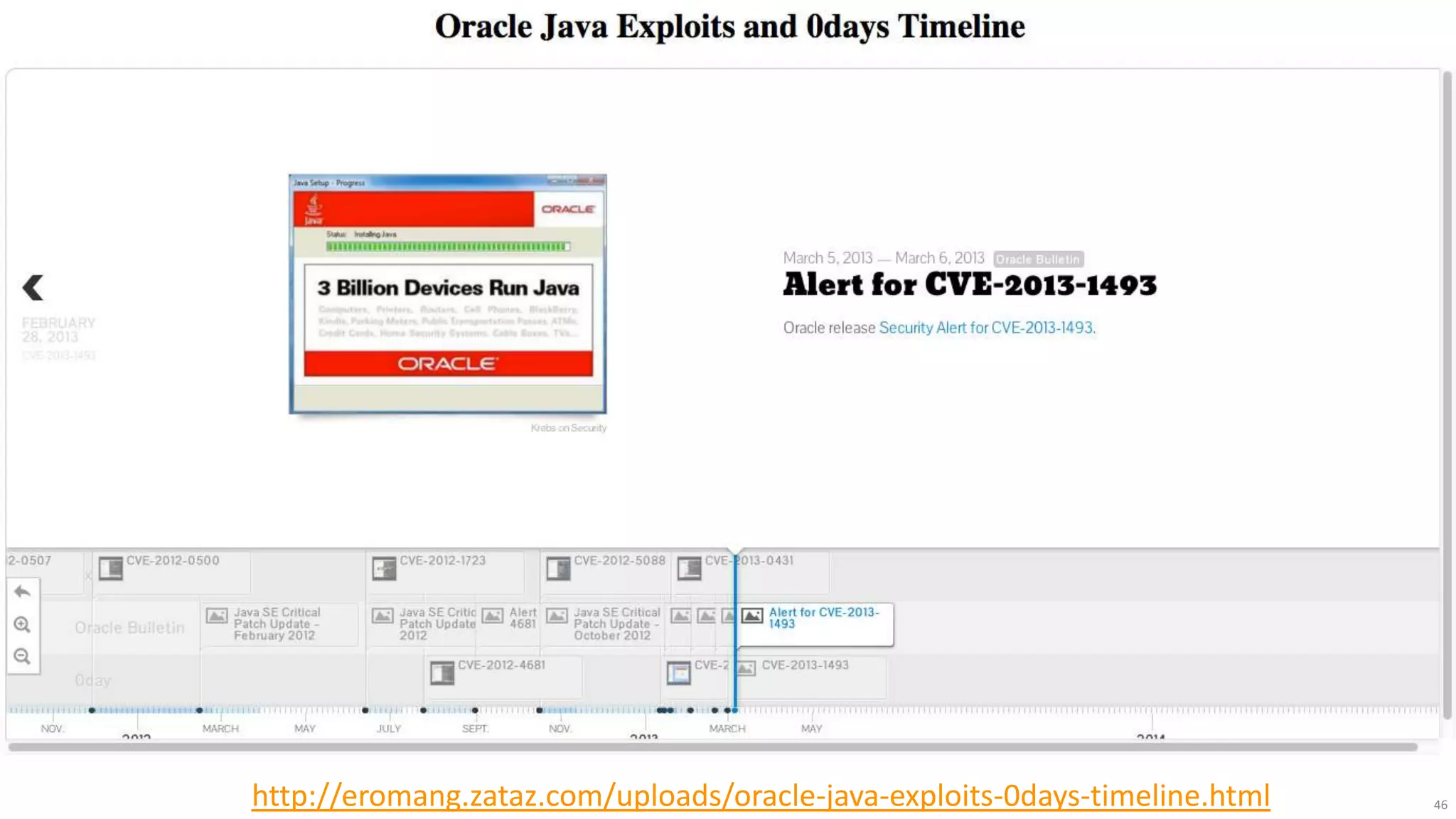
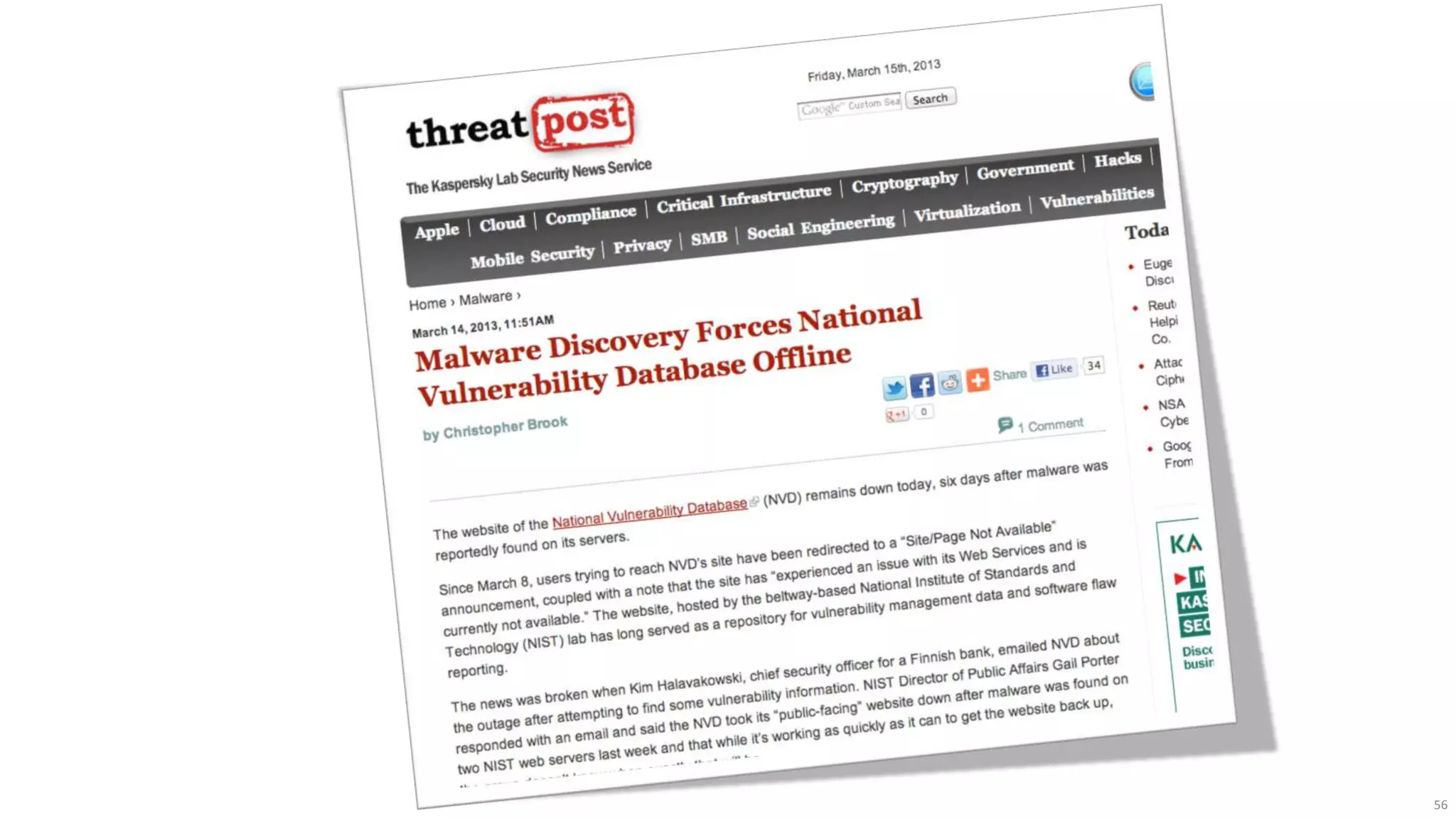
The document discusses the evolution of network security over time as networks have become more complex and connected. It describes how early networks were simpler but grew larger and became virtualized and located in multiple cloud environments. This trend of increased connectivity between all kinds of devices and systems from any location creates new security challenges. The document advocates for increased security automation through standards and highlights some recent cyber attacks to demonstrate ongoing threats. It suggests collaboratively sharing ideas and brainstorming as ways to improve network security defenses.