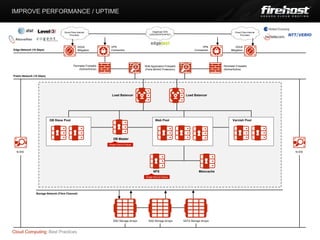
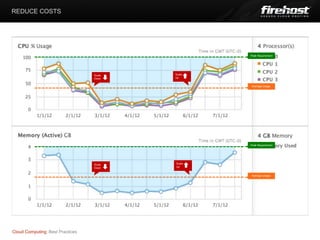
The document provides best practices for cloud computing around performance/uptime, cost reduction, and security maximization. It discusses improving performance through scaling out servers rather than up, reducing costs by adjusting server capacity to match usage levels, and maximizing security by focusing on people, processes, partners, and hosting environment controls. The presentation was given by Jamie Kephalas on behalf of Chris Drake to discuss findings and applications for various environments.