Embed presentation
Downloaded 412 times





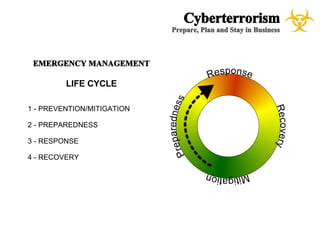


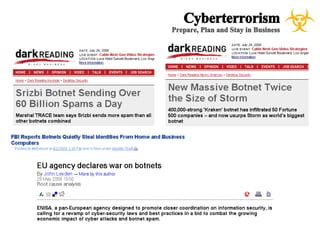






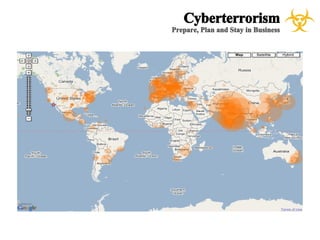
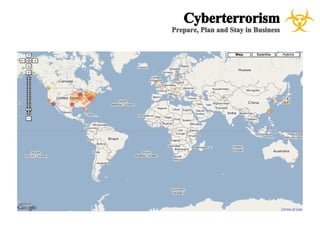
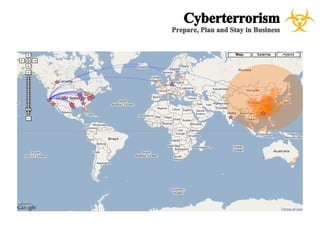
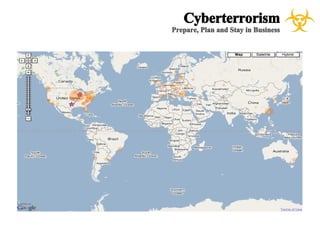
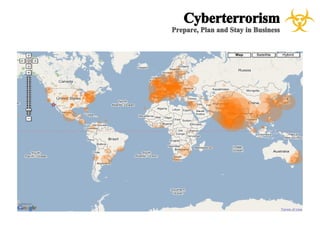
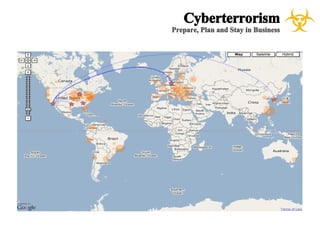
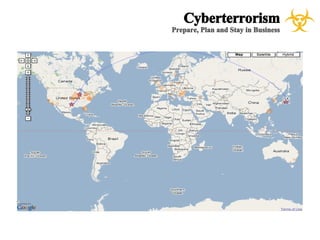
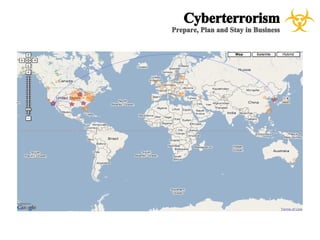


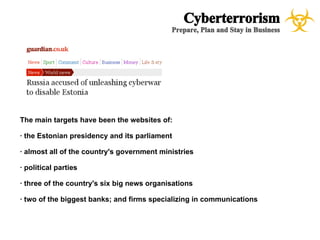

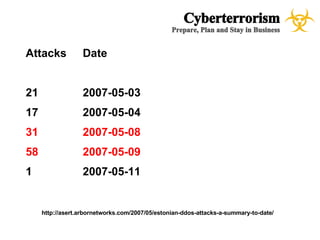

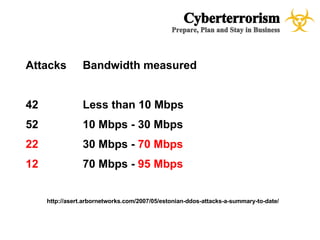

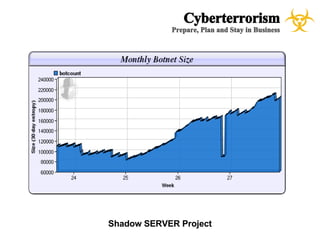
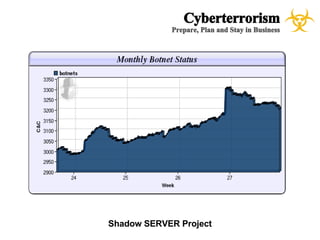



The document presents a case study on cyberterrorism within emergency management, defining cyberterrorism and outlining its implications, including the use of botnets and denial-of-service attacks. It emphasizes the importance of preparedness and response strategies, including compliance with security standards and coordination among agencies. The document also references specific real-life attacks, particularly targeting Estonian government and financial institutions.




































