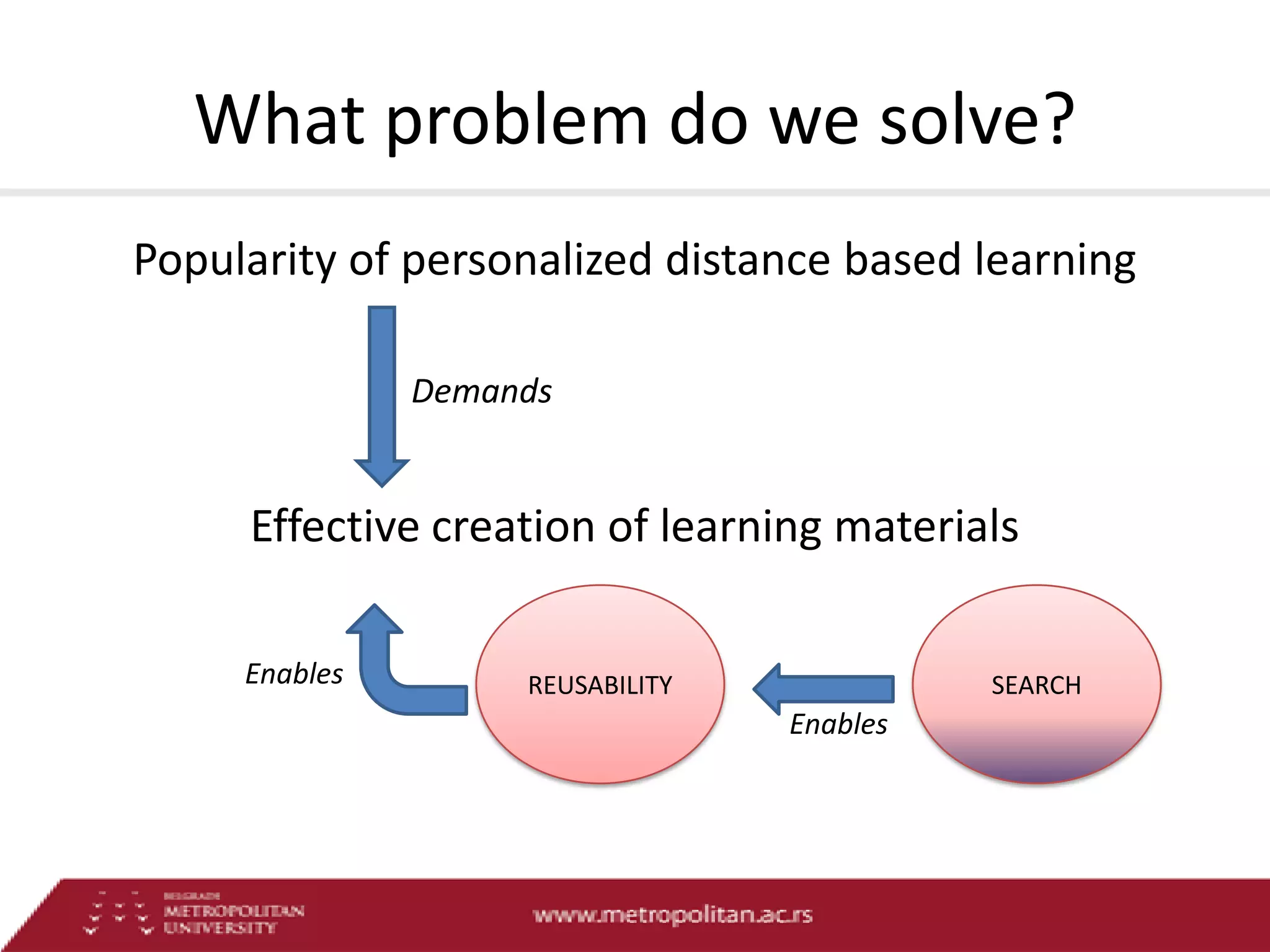
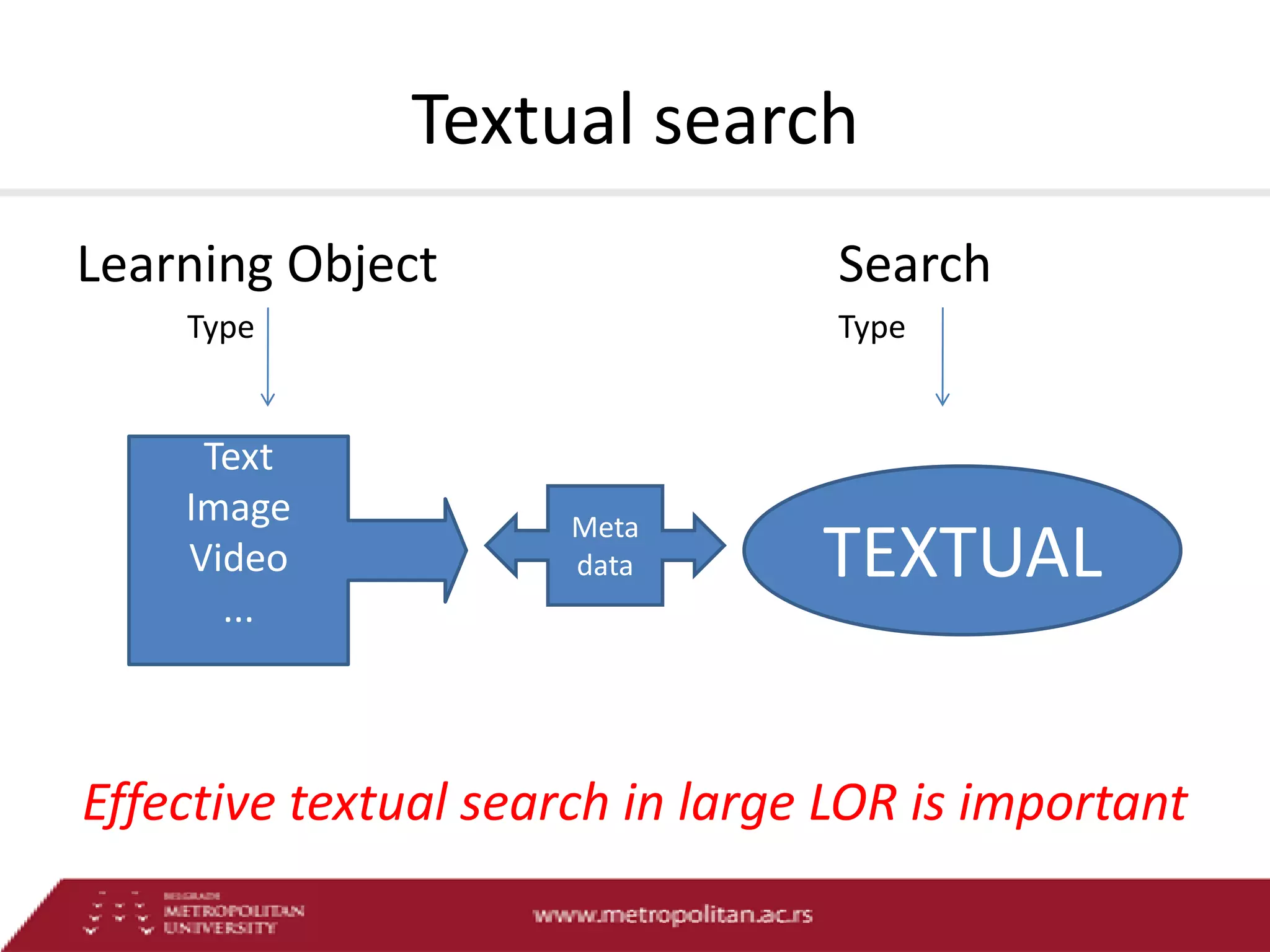
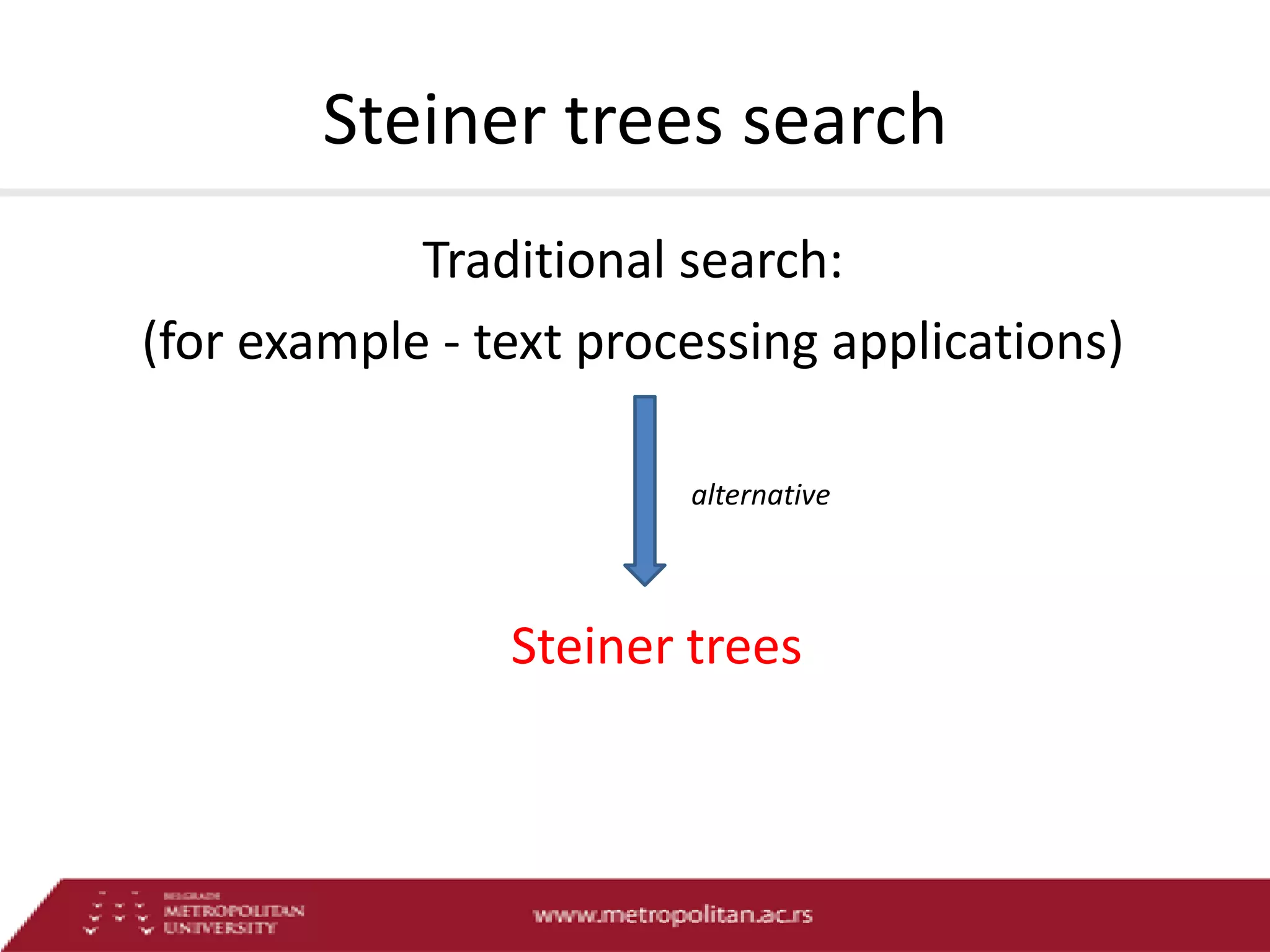
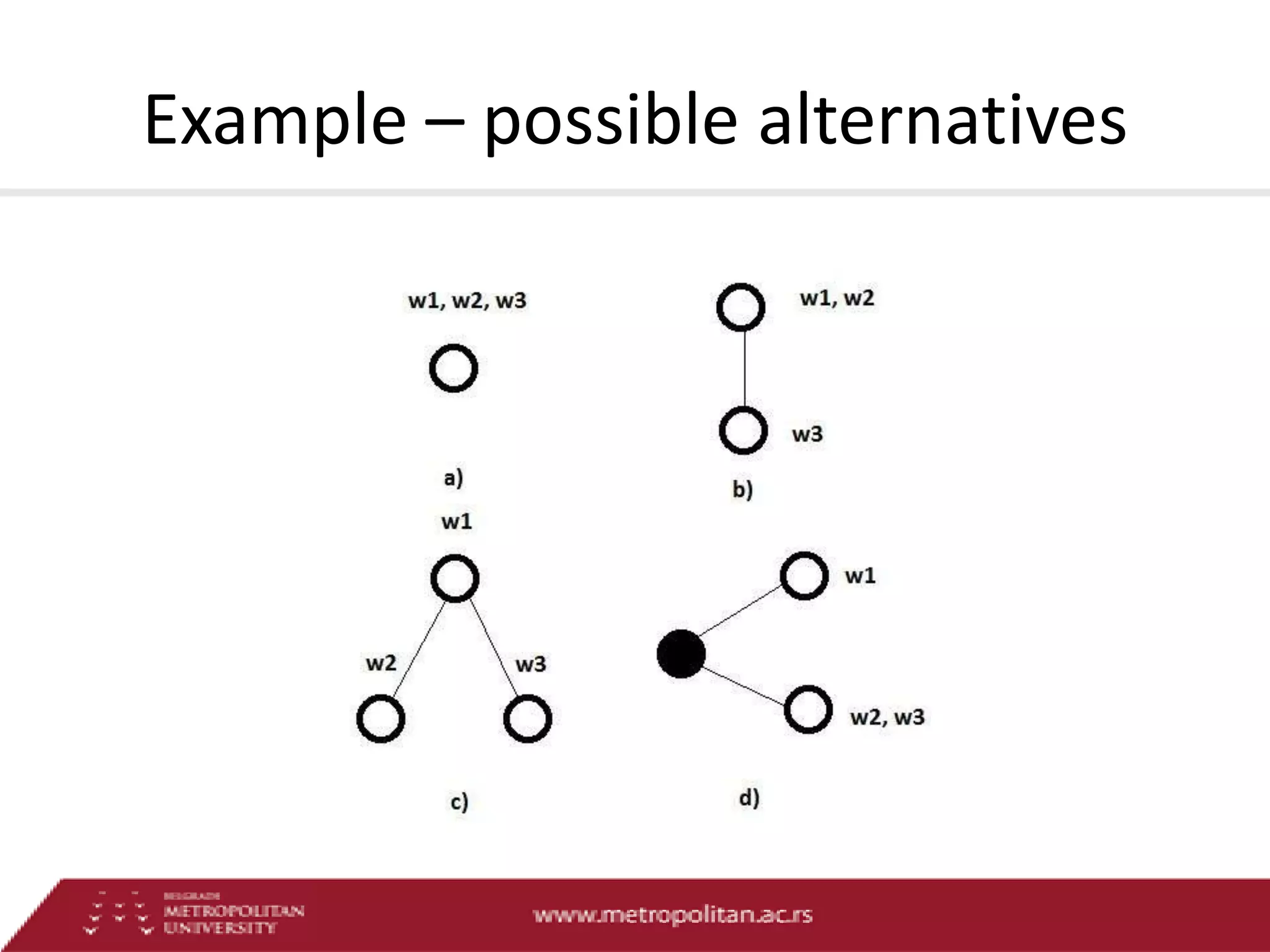
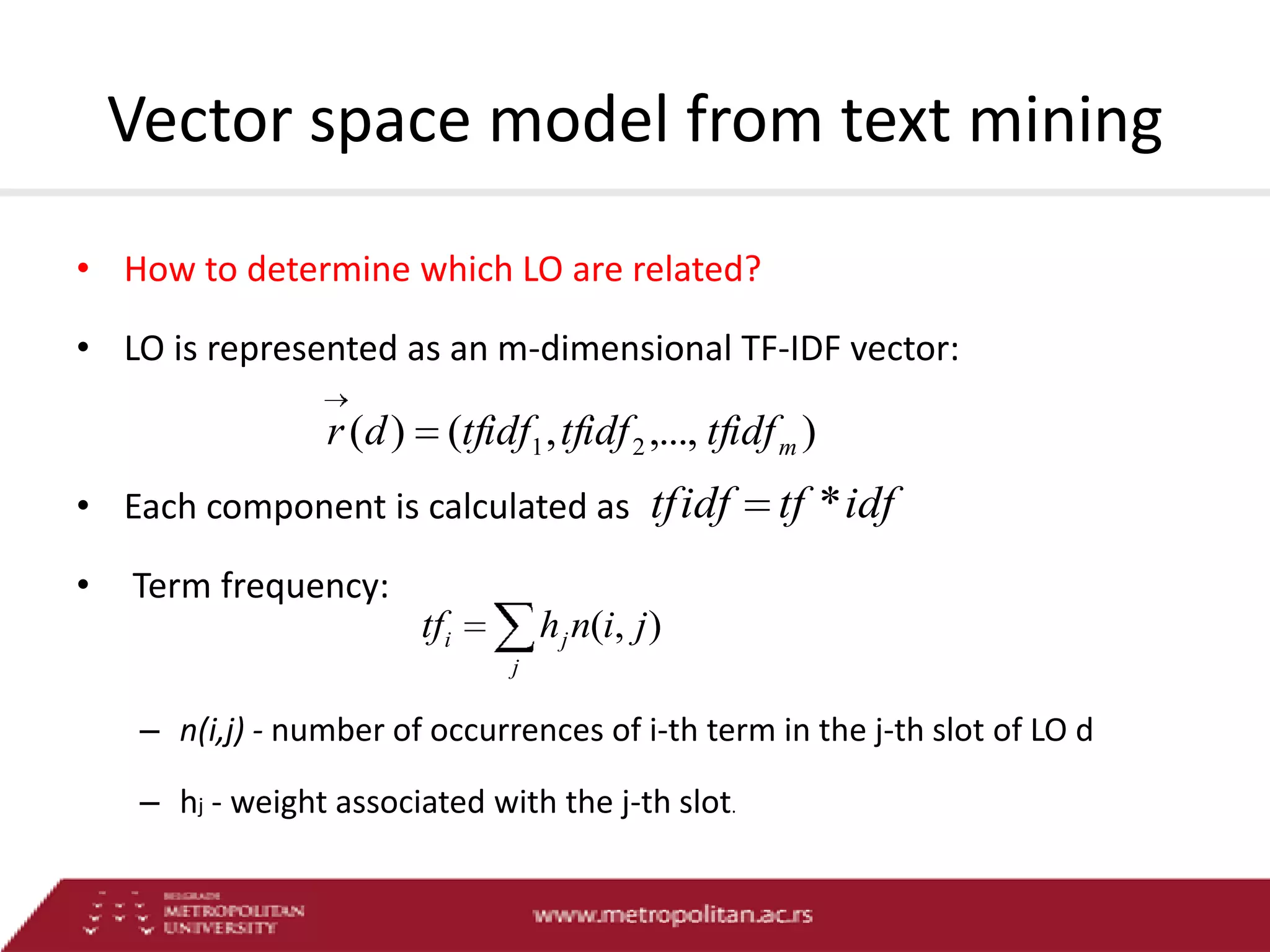
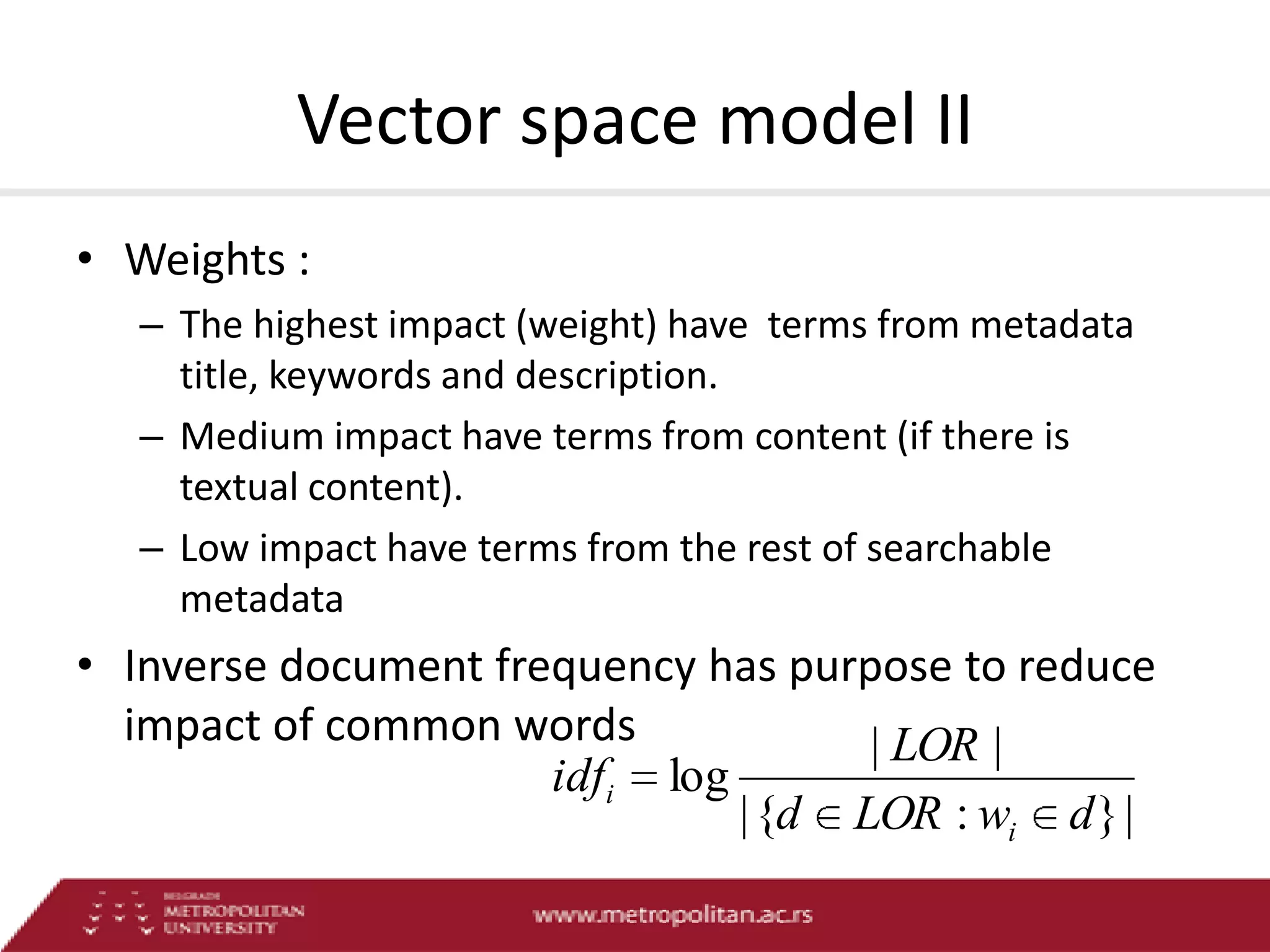
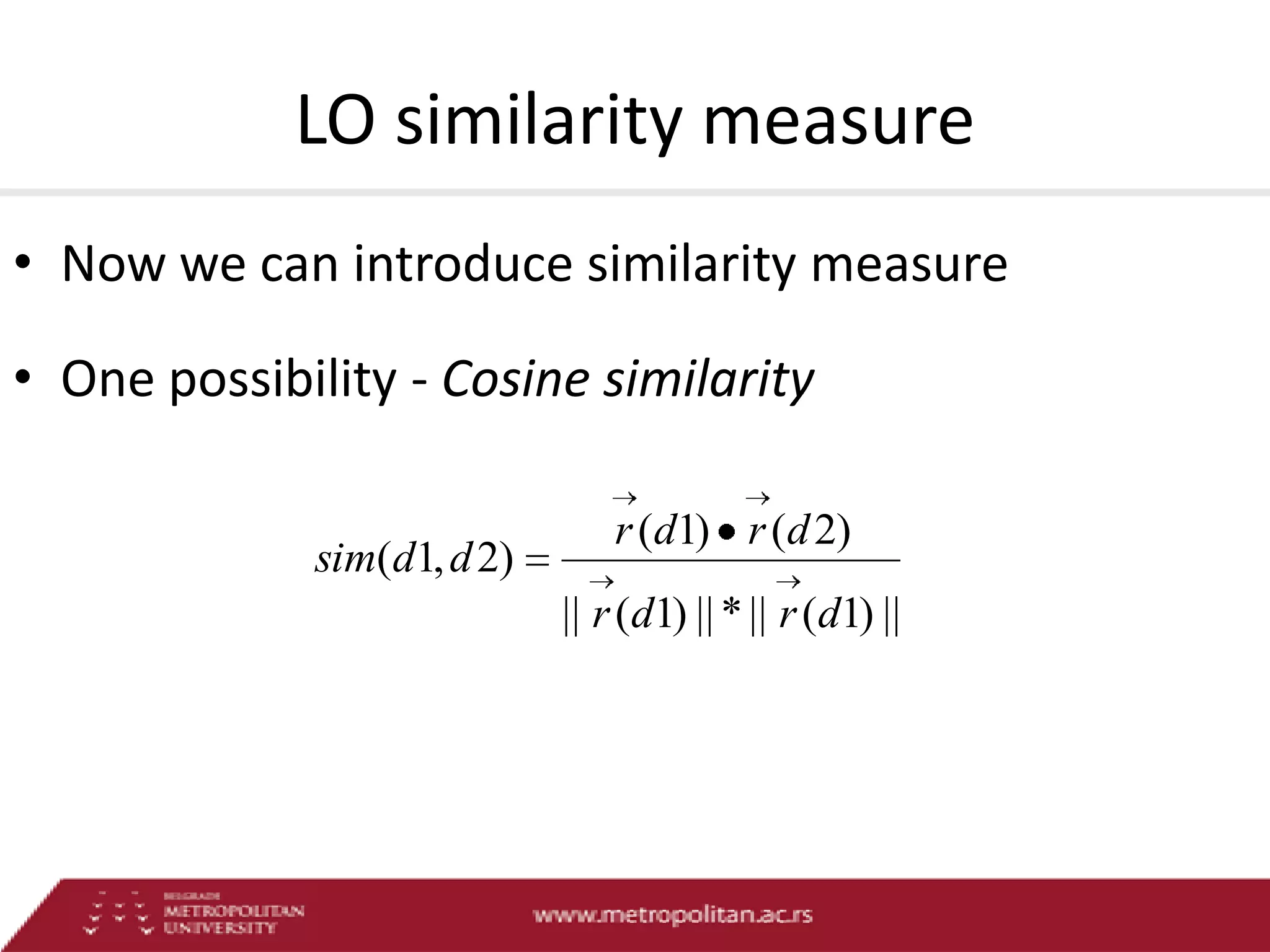
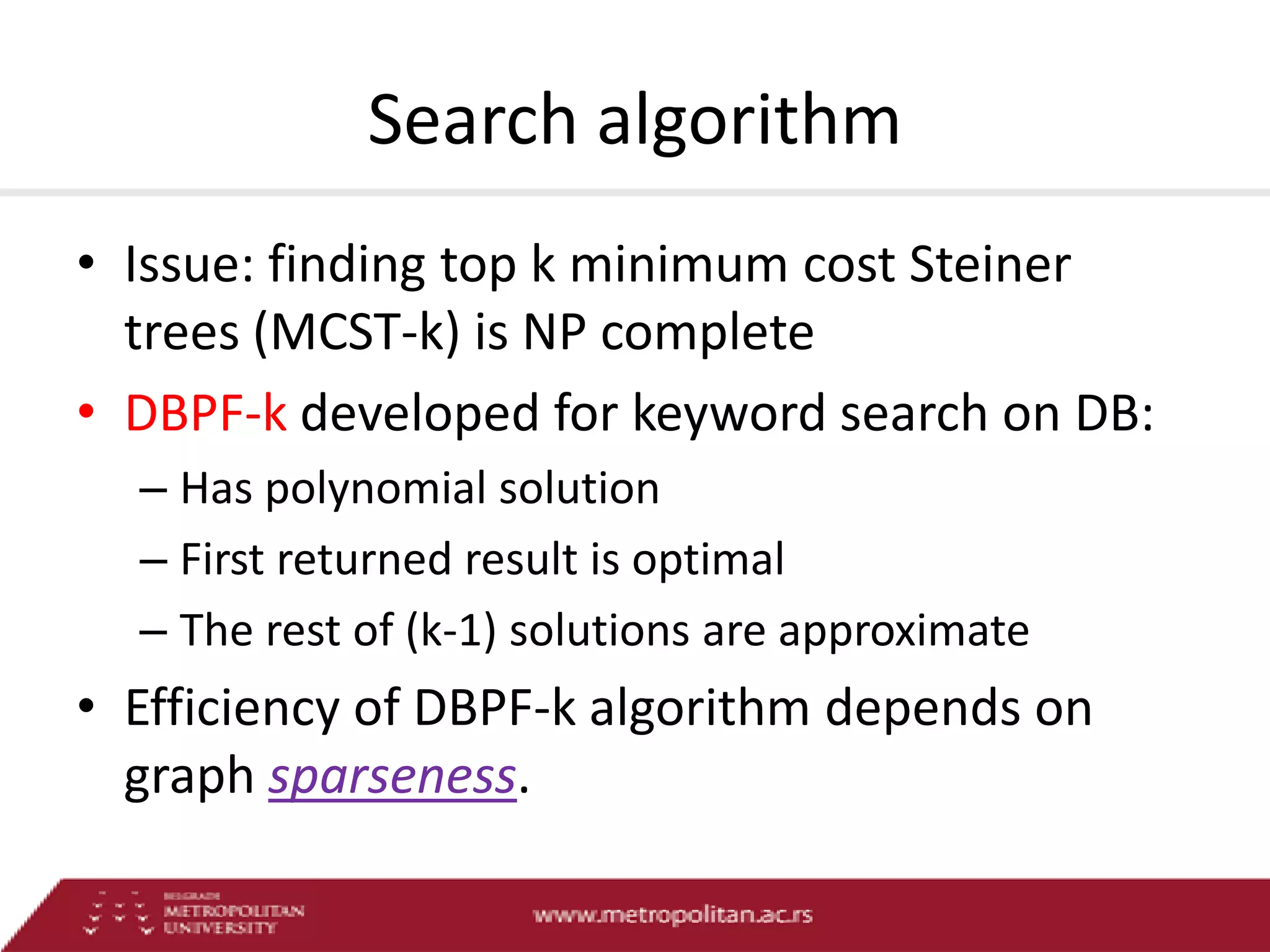
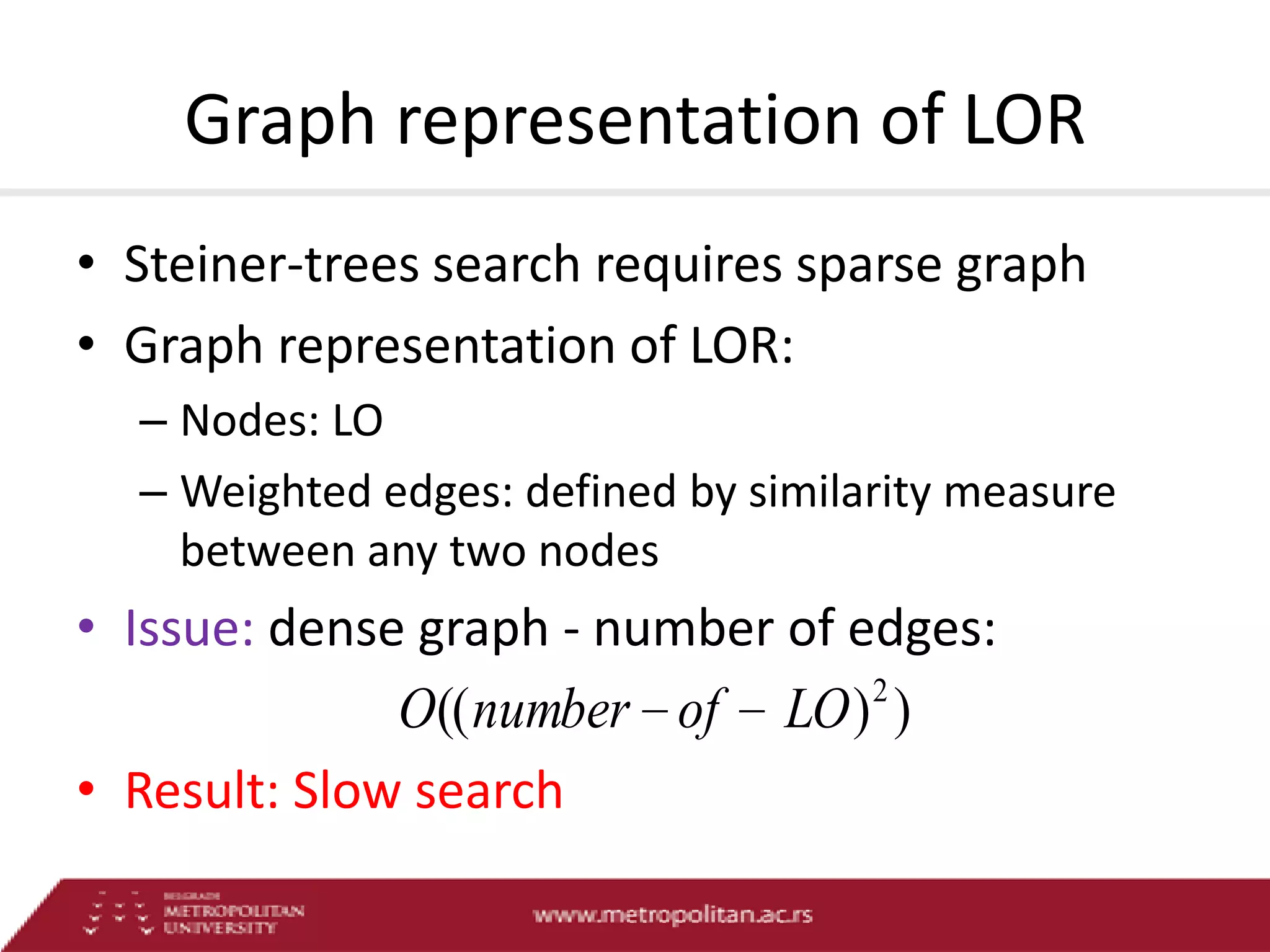
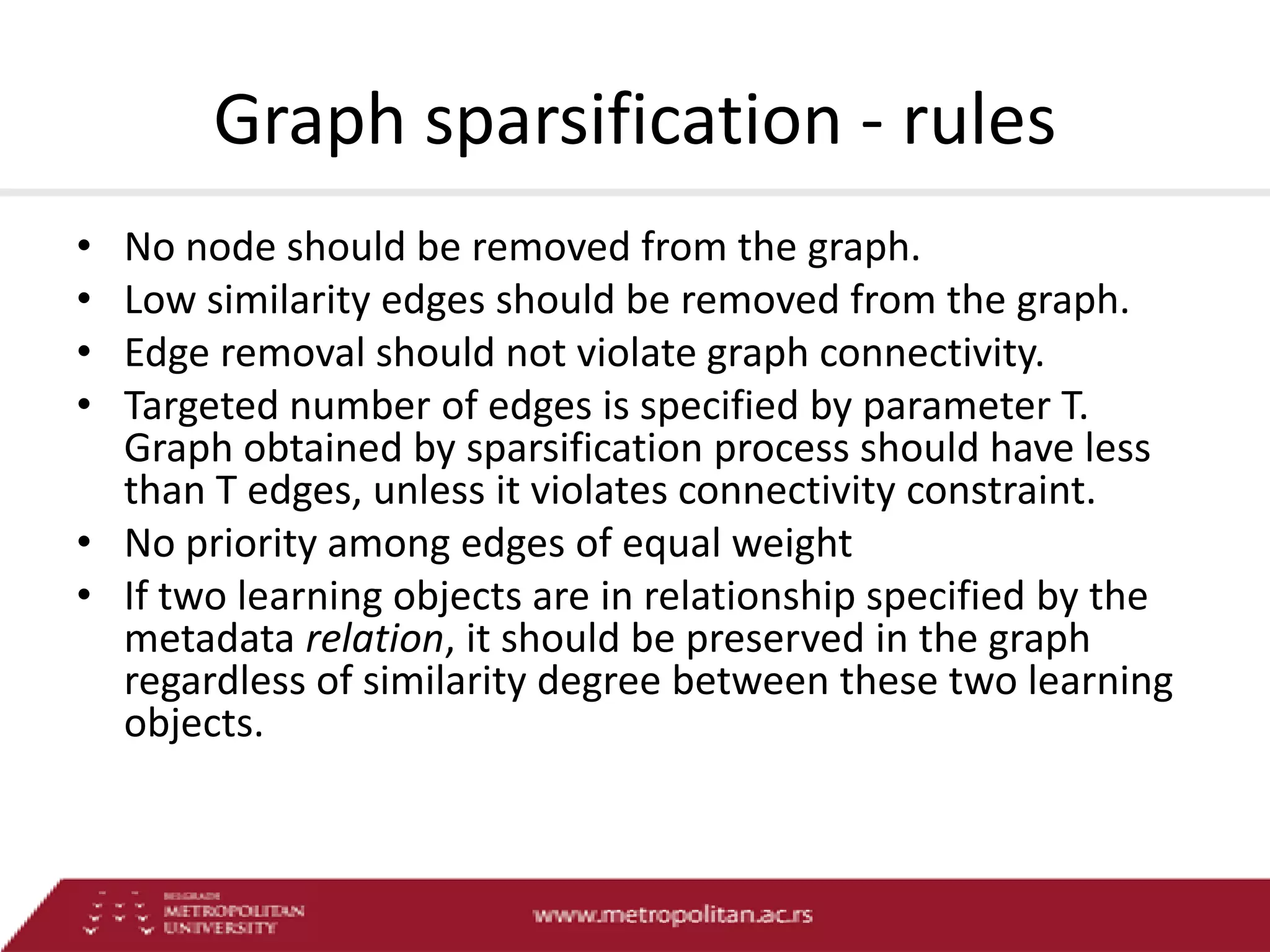
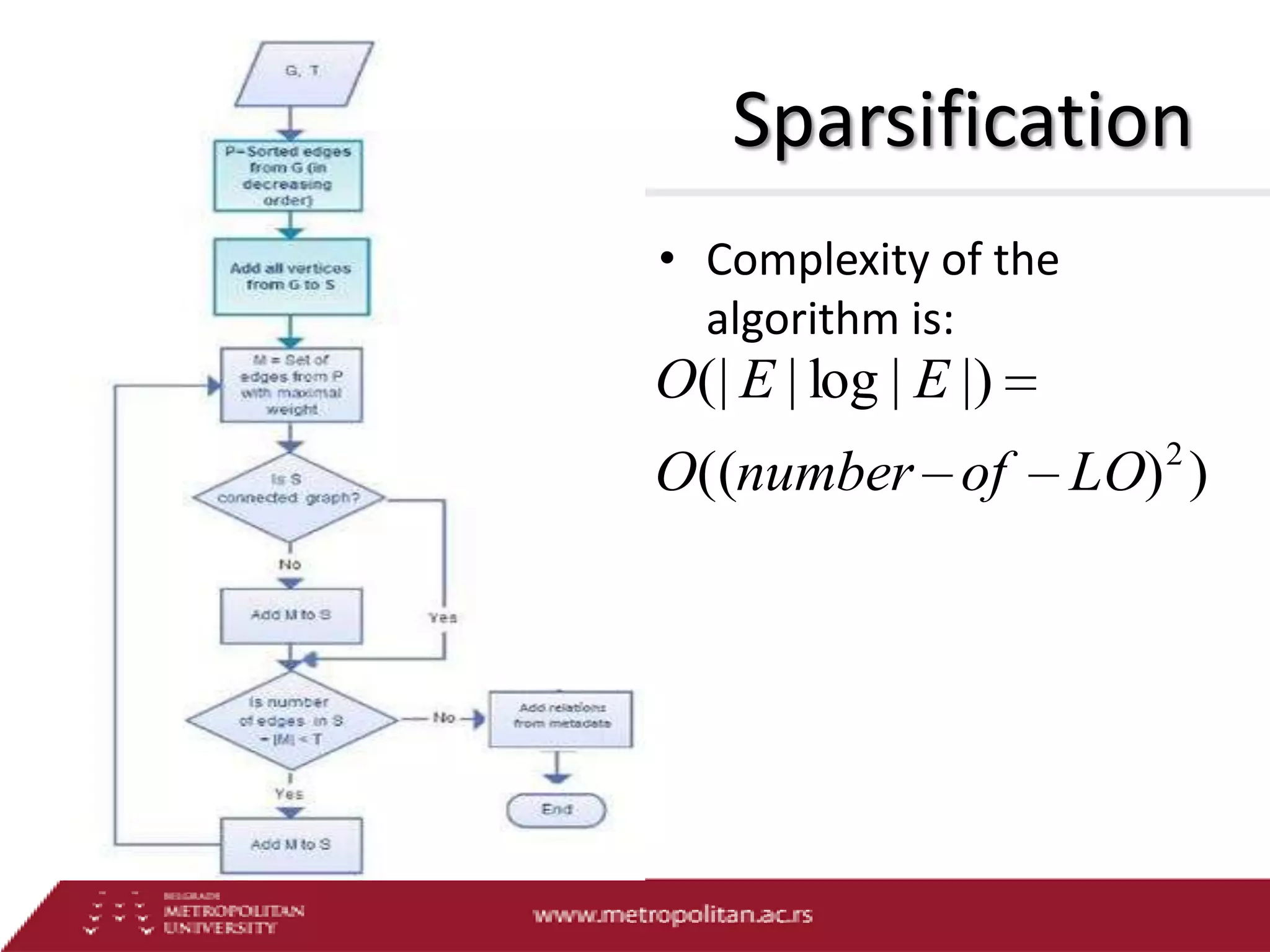
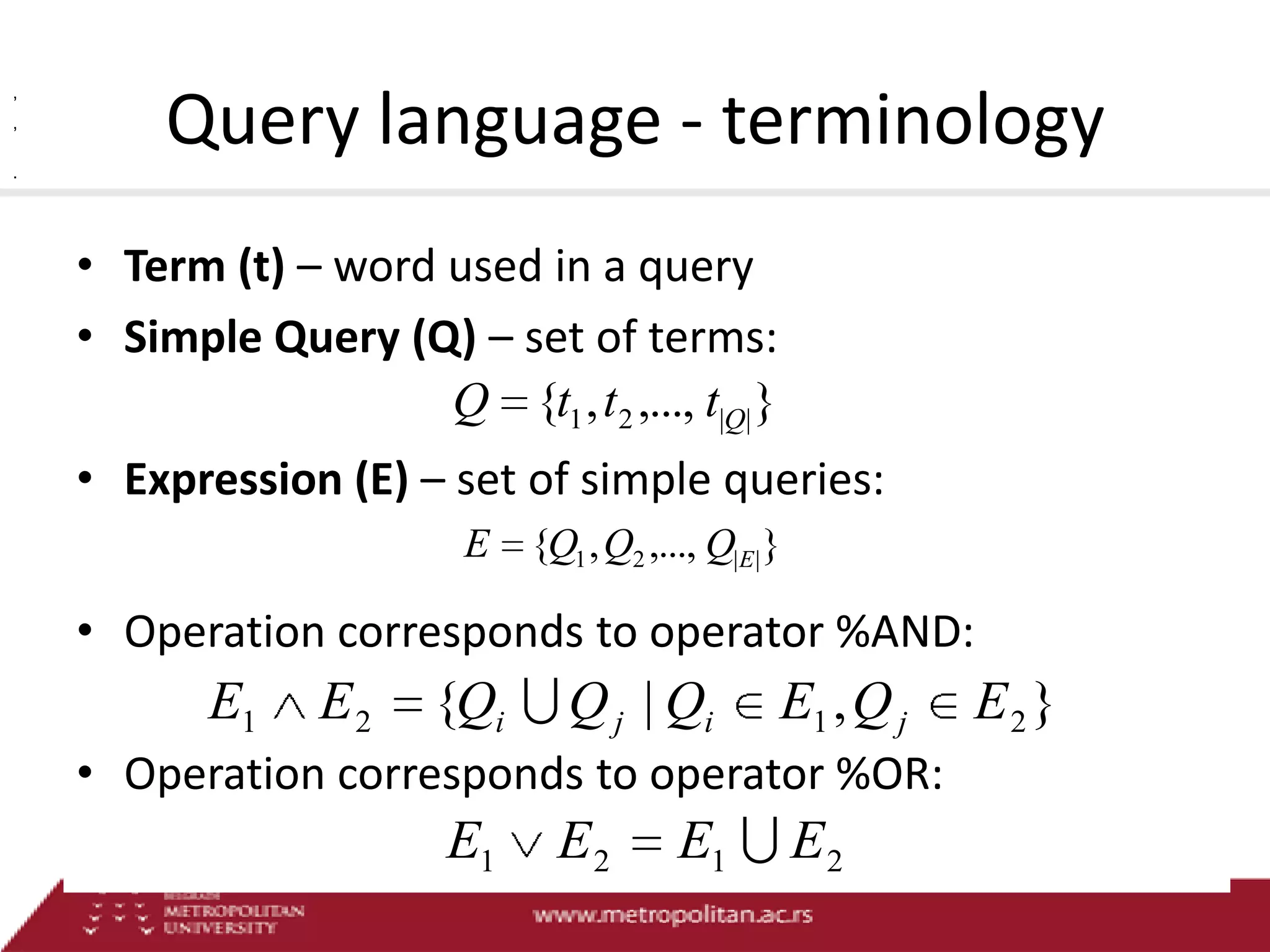
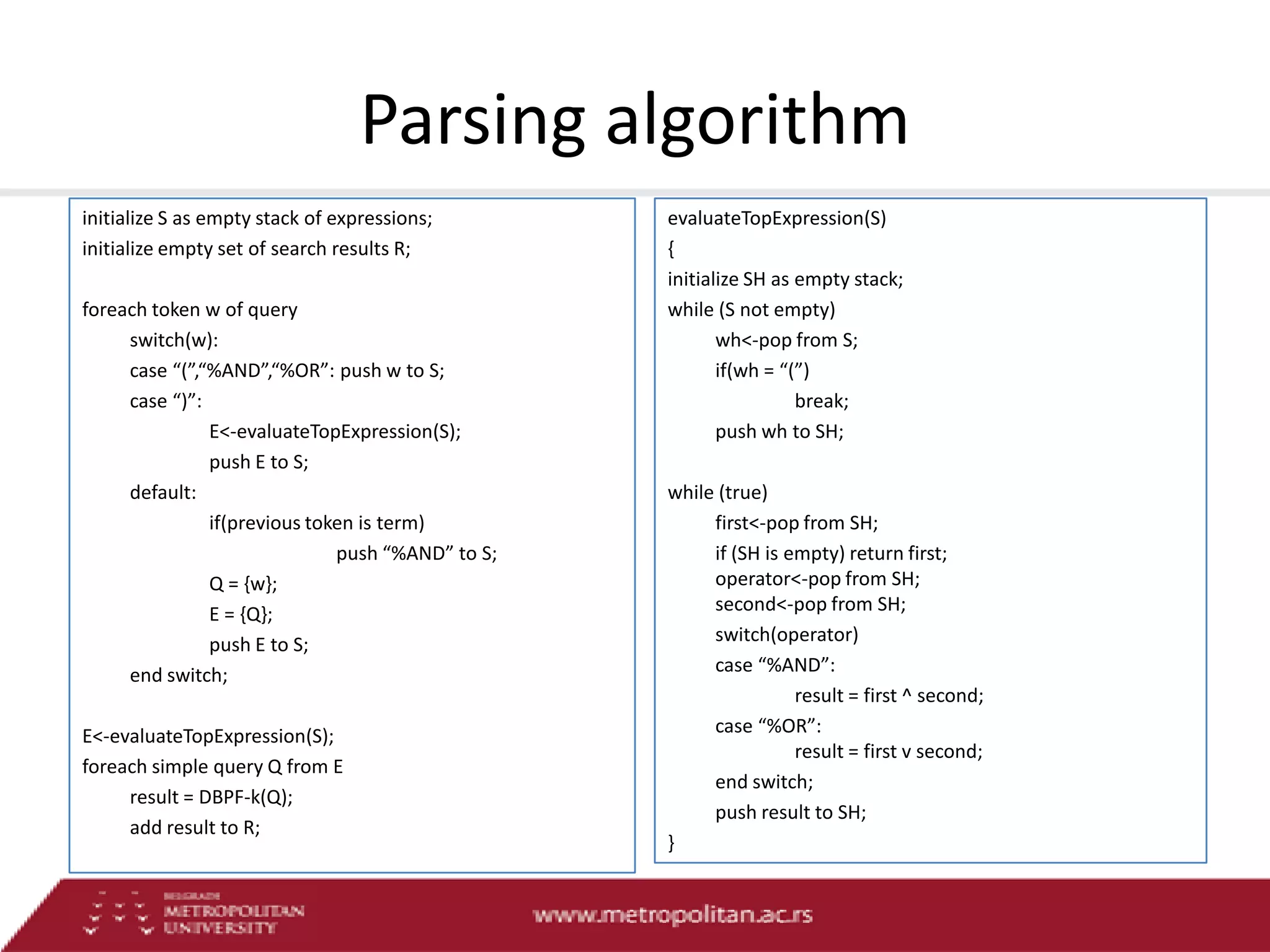
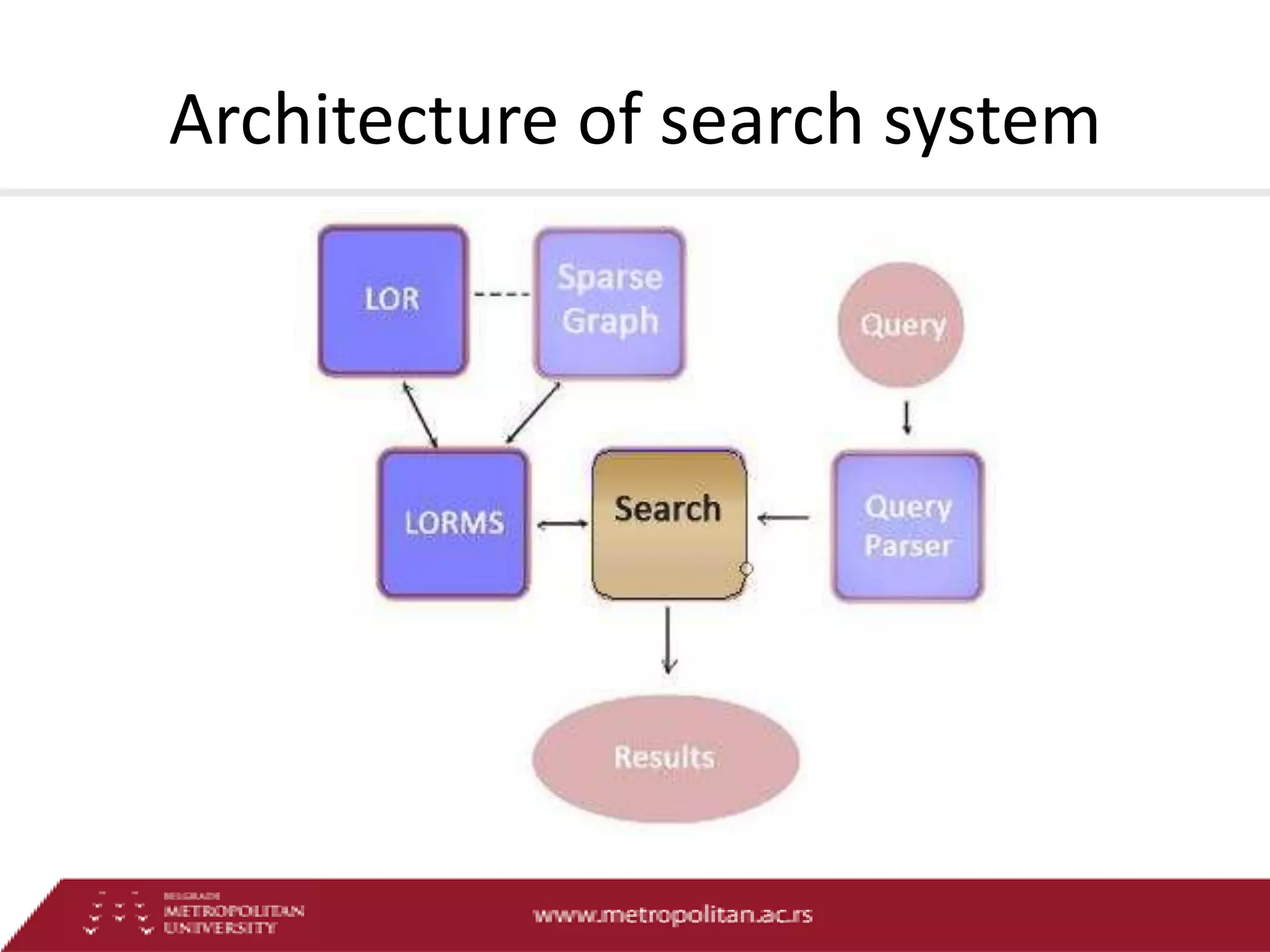
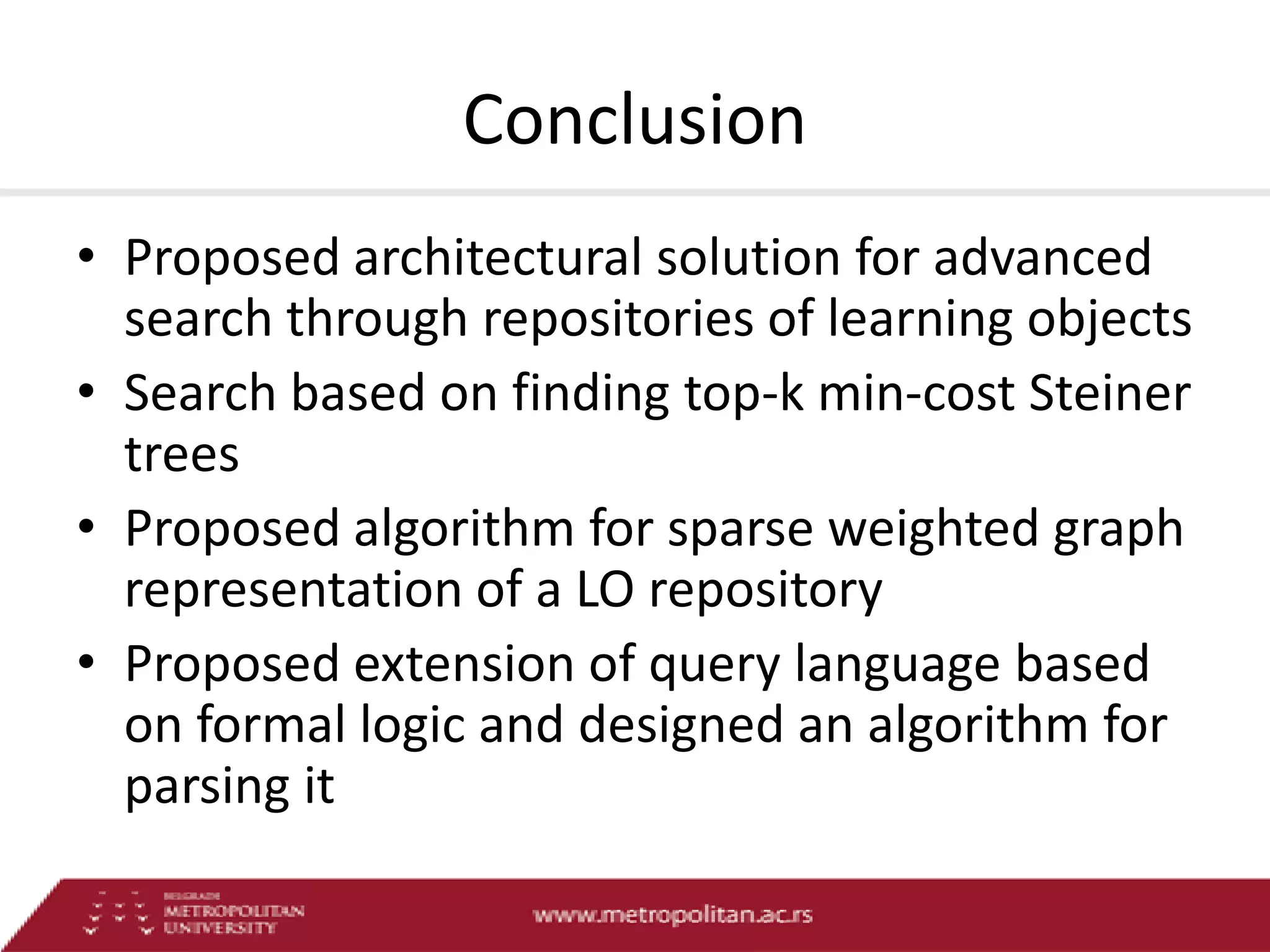
This document proposes an advanced search system for learning object repositories. It uses a Steiner trees approach to retrieve groups of related learning objects that satisfy a query, even if no single object matches all query terms. It represents the repository as a sparse weighted graph based on learning object similarities. It also extends the query language with AND and OR operators and presents an algorithm for parsing complex queries. The system aims to enable effective search and reuse of learning materials.