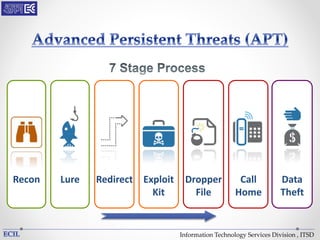
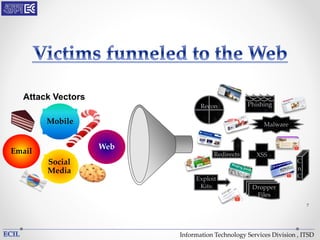
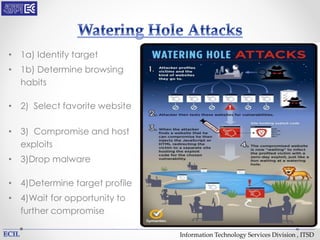
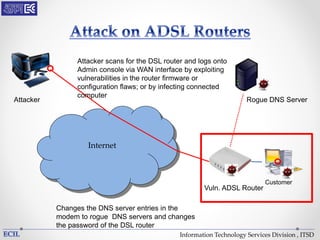
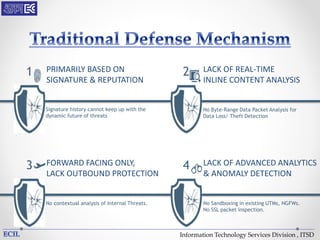
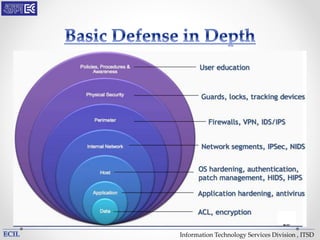
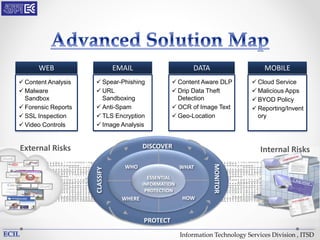
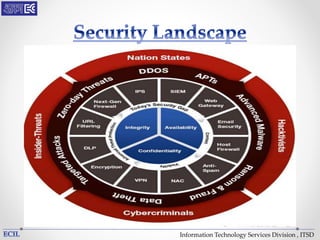
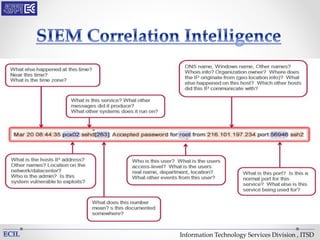
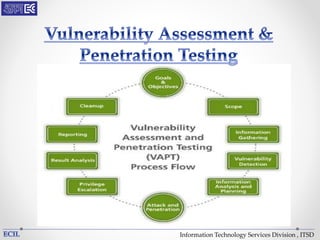
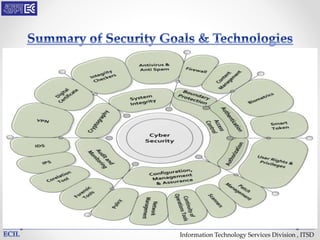
The document outlines various threats to information technology, including advanced persistent threats, zero-day attacks, and ransomware. It emphasizes the importance of protective measures like malware sandboxing, behavior-based classification, and real-time threat intelligence analysis. Additionally, it highlights vulnerabilities related to social media and web-based attacks, as well as strategies for enhancing system security and user awareness.