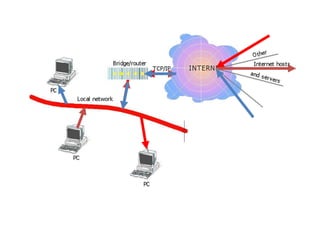
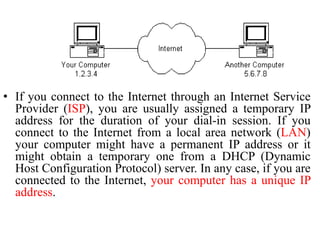
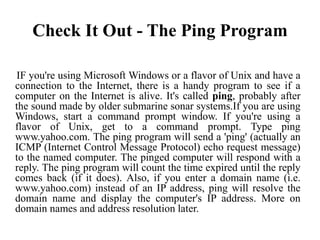
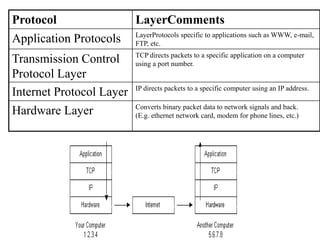
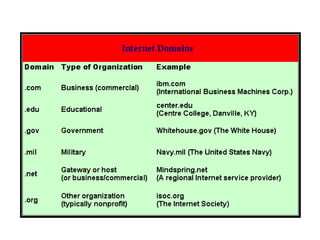
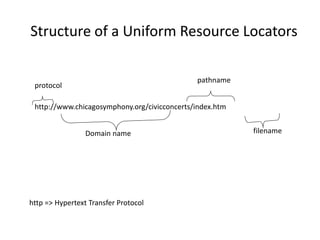
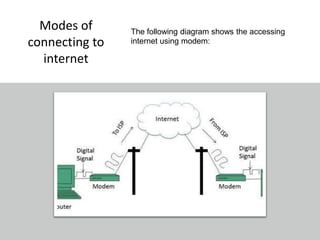
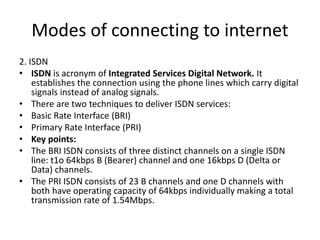
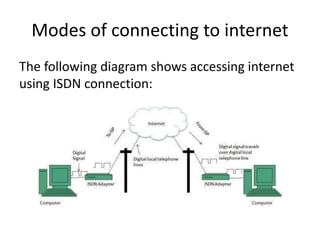
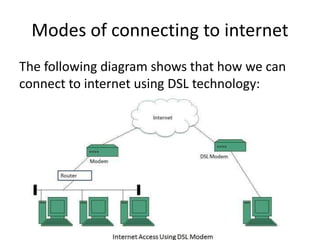
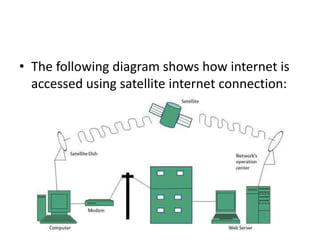
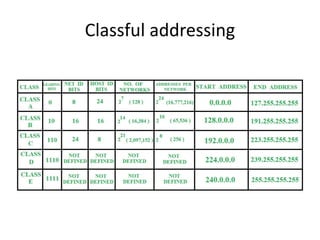
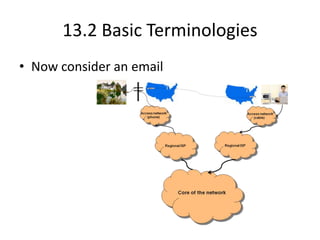
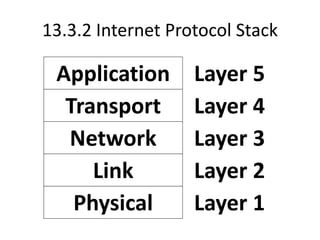
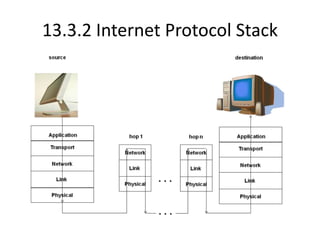
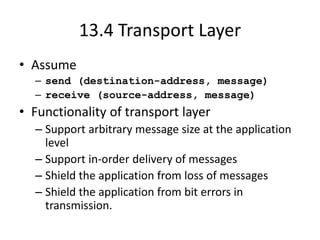
The document provides an overview of the internet, describing it as a vast network of interconnected networks that allows data exchange across the globe using protocols like TCP/IP. It details the structure and functionality of internet protocols, addressing schemes (IP addresses and domain names), and various methods of connecting to the internet such as dial-up, DSL, and satellite connections. Additionally, it explains the World Wide Web, highlighting how web browsers function with HTML documents and the process of searching for information online.